How To: Your Android Device Can Help Save Lives While You Sleep: Here's How to Help Out
"Millions of us have smartphones with the power to speed up research that will benefit billions of people around the world." - Professor Francois Grey


"Millions of us have smartphones with the power to speed up research that will benefit billions of people around the world." - Professor Francois Grey

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

The lockout feature in iOS 7, which securely locks your device after a few incorrect passcode entries, can be a real pain in the ass sometimes.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

As if you needed another reason to lock down your Facebook profile, the company's sketchy new partnership with data mining firm Datalogix is geared towards giving advertisers more information on what you're doing—even when you're not online. It's just not enough that they can target ads based on your preferences, now they want to know how those ads are influencing your buying habits in the real world.

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...
In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drives. Choose any letter you want from the drop down menu, then click next to the "reconnect on logon" text. Click on the finish button, then open your newly mapped network drive from your computer. You can do this for any s...

Have you always thought of Excel's grid system as kind of limited? Too small for what you need? Well, now in Excel 2008 for Mac, its grid might be too big for its own good! It's huge with plenty of room for all your data. The Microsoft Office for Mac team shows you just how to explore the bigger grid in this how-to video.
Great news! — Excel isn't just for Windows anymore. Okay, so it's been available on the Mac for awhile now, but if you haven't used it yet, why not start now? Getting started with Excel 2008 for Mac is easy, and this video overview will show beginners or even the most seasoned professional spreadsheet worker a thing or two. The Microsoft Office for Mac team shows you just how to get started in this how-to video.
Excel 2008 for Mac makes it easy to create formulas for cells. You could always do it before, but now with the new Formula Builder feature, building formulas just got one step closer to simple. The Microsoft Office for Mac team shows you just how to build formulas by using the new Formula Builder in this how-to video.
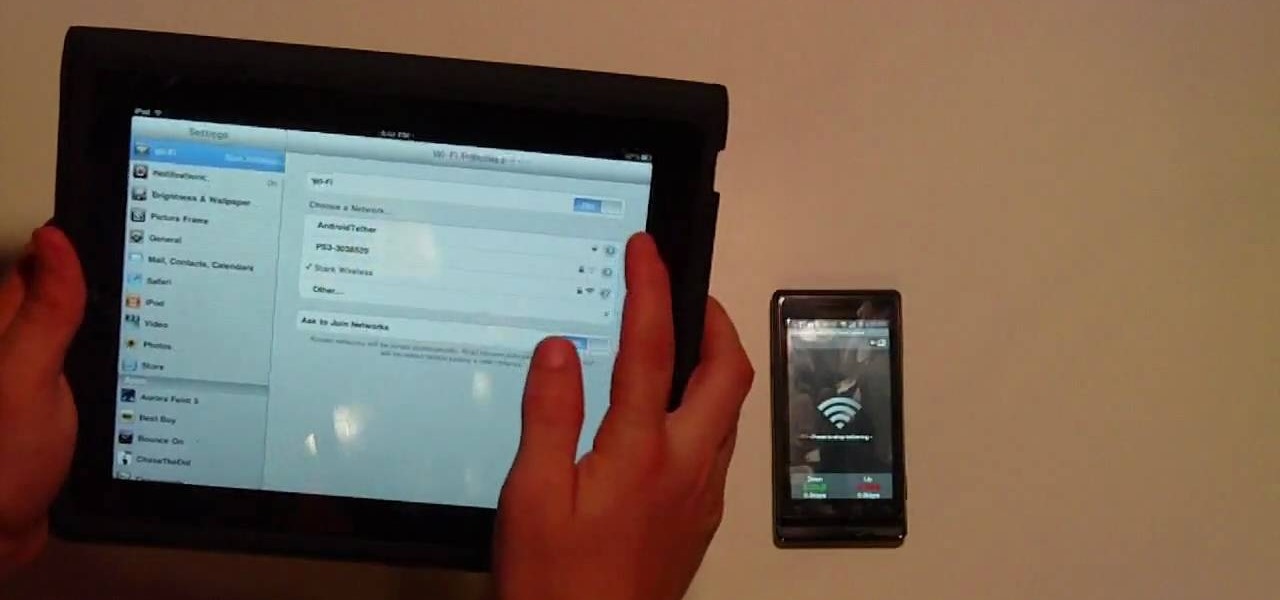
In this Electronics video tutorial you will learn how to tether a laptop to a Droid Smartphone for free Wi-Fi. For this you will need the android wifi tether application. Download the version for your device from here and install it. Then launch the app and press the icon to start tethering. In your laptop, go to settings and then to wi-fi. You will see a new network called android tether. Connect to the network and you will see that it works. As with any other network, you can change the nam...

This video shows you how to fix a Windows "Blue Screen of Death". You should know what to look for when you get the BSOD. You should look for the error code first and then the stock code. You should hit the F8 button upon start up to go to the last known good configuration and it will boot your computer to the last time it booted correctly. You can also start in safe mode. You will need to do a system restore. If that doesn't work do a Google search for the file name that is causing the probl...
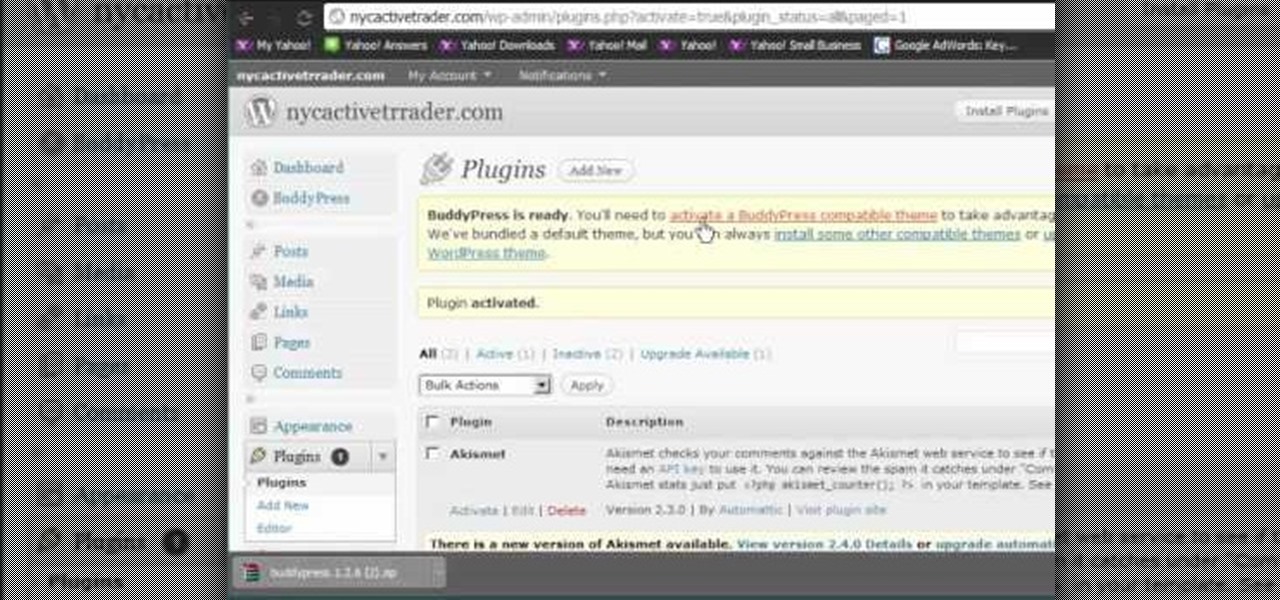
Like Facebook so much that you want to make your own version of a social network, just for you and your friends? It's totally possible, thanks to BuddyPress, a DIY social network for a tight community with the power of WordPress. This video will show you the steps to installing it and setting up your own social network.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...
If you're not much for office computers, and like using your own powerful PC at your workstation, then chances are, you're going to have to login to the network. Microsoft shows you how to quickly login and join a Domain or Workgroup in an office network.
In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...
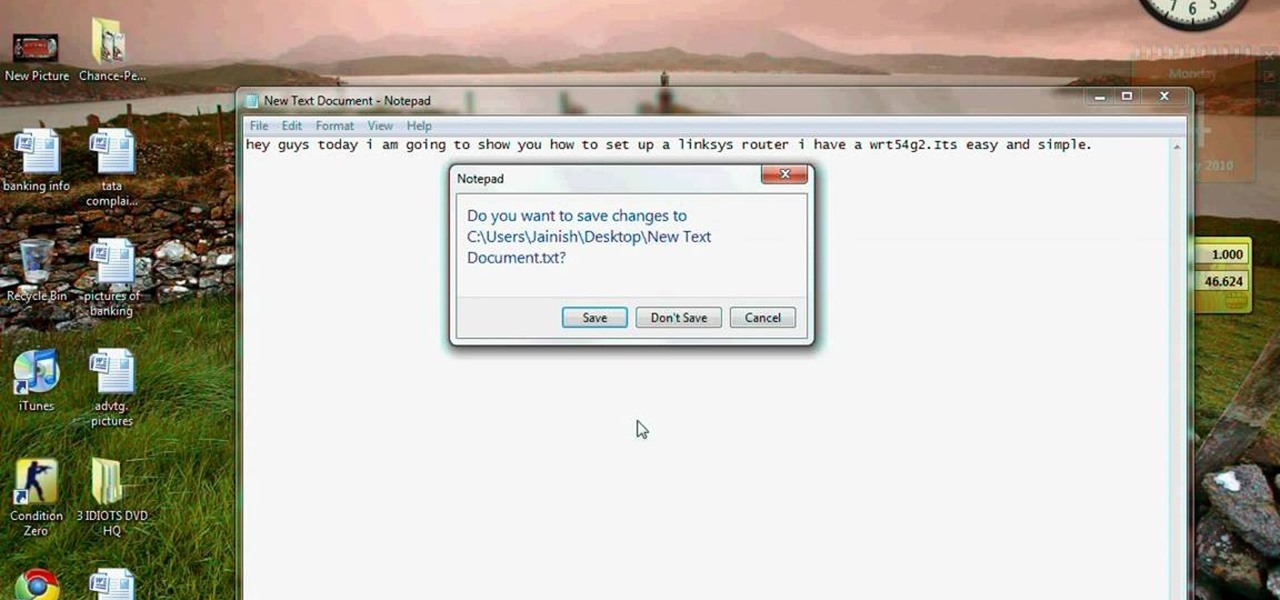
This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

In this video tutorial, viewers learn how to fix the Wi-Fi problem on an iPod Touch or iPhone. Begin by clicking on Settings and select General. Then scroll down to click on General and select Reset Network Settings. When a confirmation window pops up, click on "Reset Network Settings". The iPod device will then reboot. Now click on Settings and select Wi-Fi. Then select a network to connect to. This video will benefit those viewers who have an iPhone or iPod Touch, and would like to learn ho...
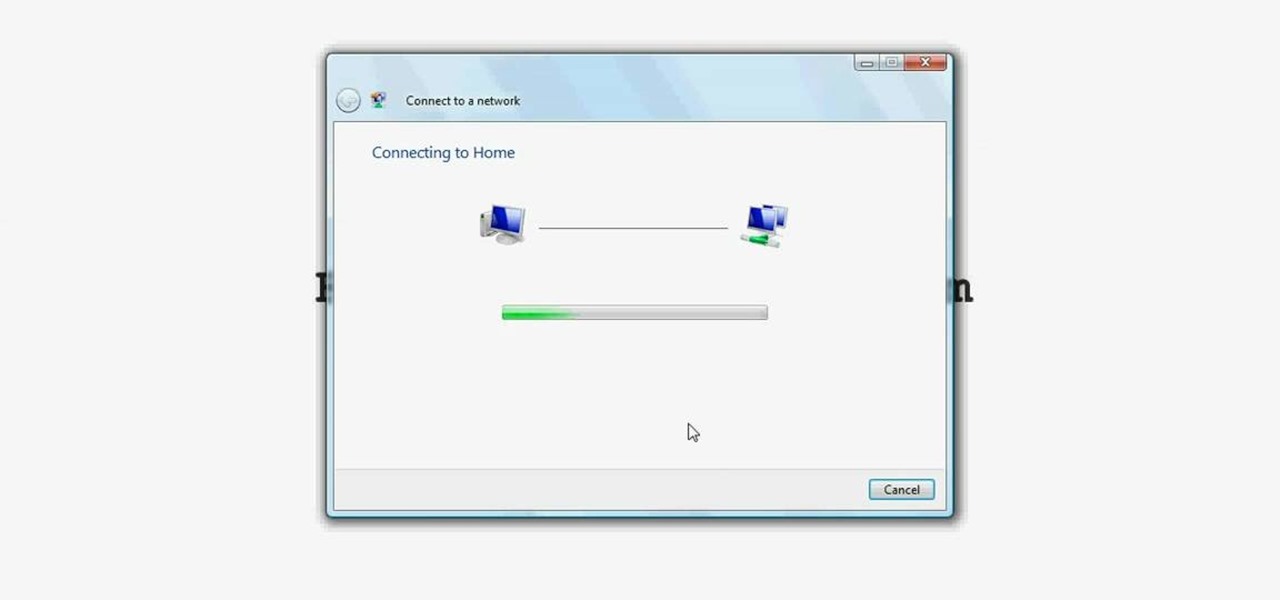
Wireless networks are really the only way to go these days. With WiFi you can access the world wide web from almost anywhere, at anytime, and not have to worry about annoying wires or cords. In this tutorial, learn how to set up a wireless connection in a Windows Vista based machine.
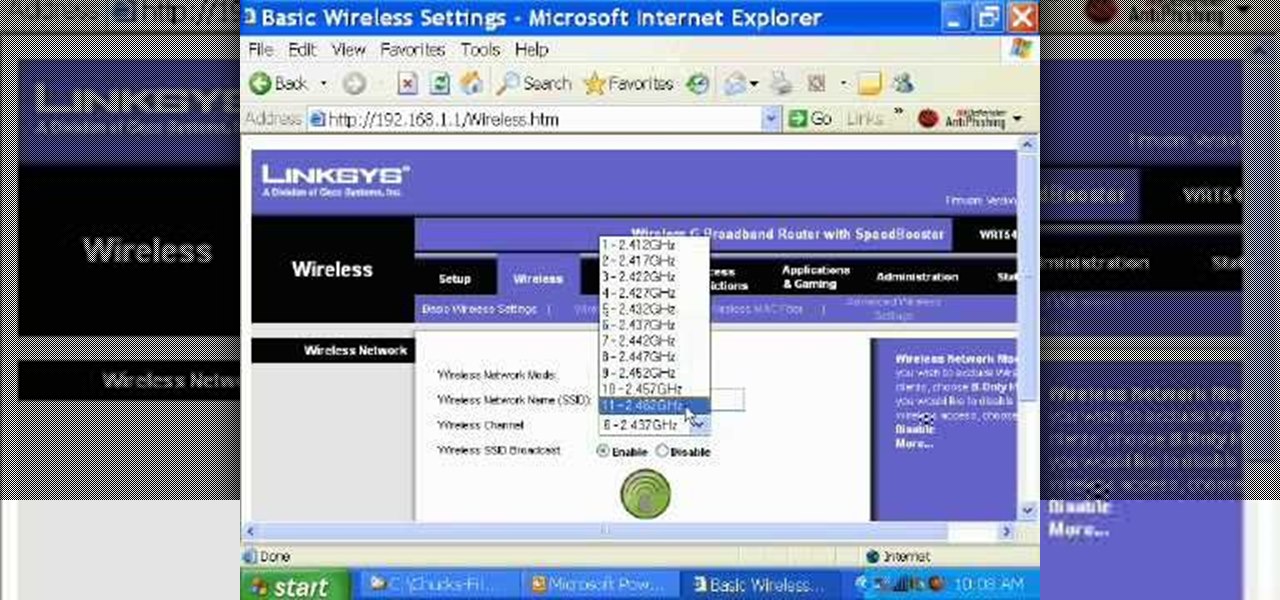
Ever had router trouble? Got router trouble? Well don,t worry the people over from quickcert.com have made this video to help! More specifically a linksys 802.11g router. All new routers come with a standard Ethernet cable, which must be plugged into one of the four ports on the router and connected to your computer as well. This is necessary to change settings, using Microsoft IE (internet explorer) when the routers IP is typed into the address bar. It is strong recommended to change the def...
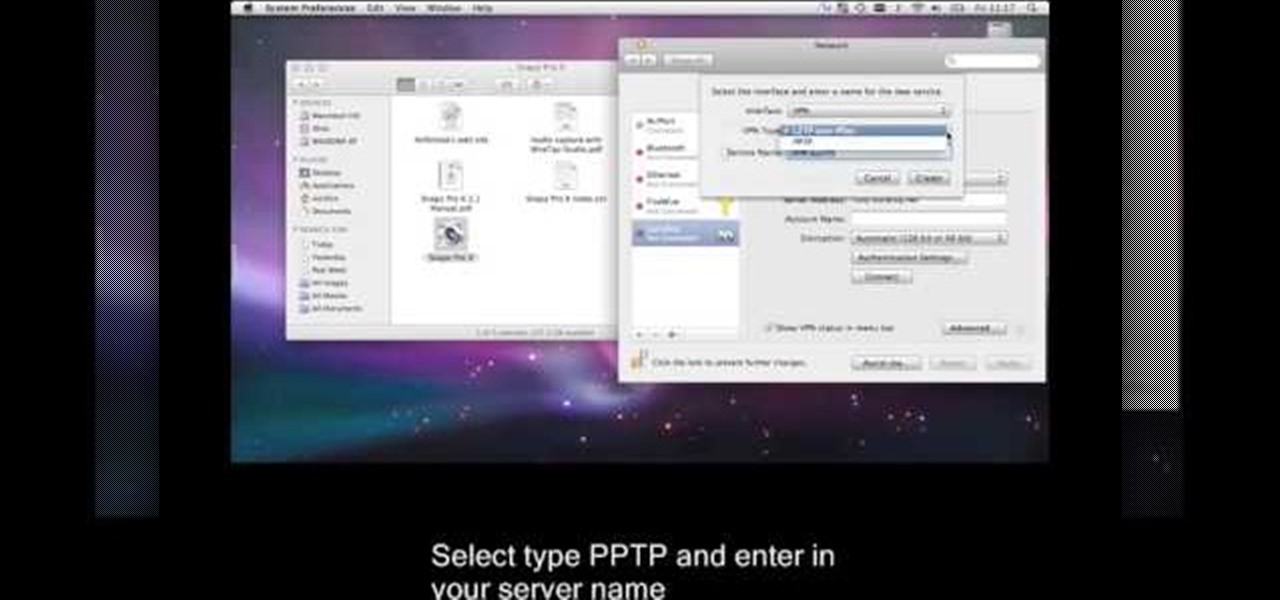
This is a video tutorial that is showing its audience how to set up your own VPN client on your Mac computer. The first step in setting up a VPN client is to go to your system preferences on your computer. Next select network and then select the plus button and type in that you will be making a VPN network. Next you should select the type PPTP and enter your server name. Then you can click on create and it will create a new network for you. Next you should enter your service address and your ...
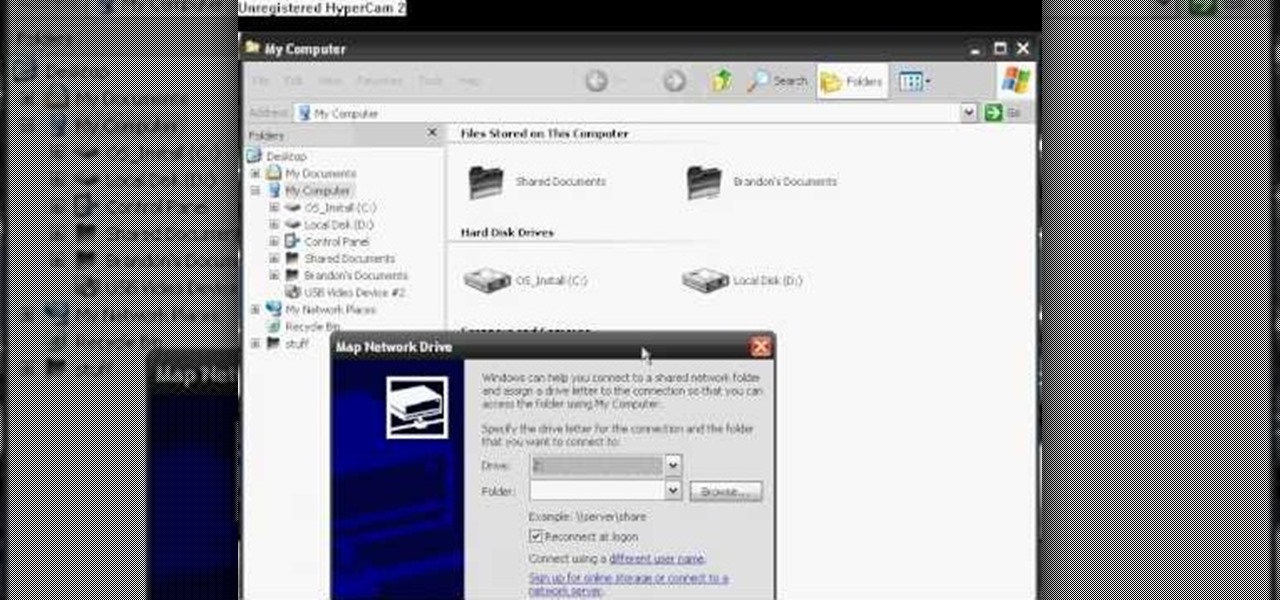
This tutorial will walk you through the steps you need to map a network drive for file access in Windows XP. By mapping your network drive you will be able to store and access files offsite and make computing easier all around.
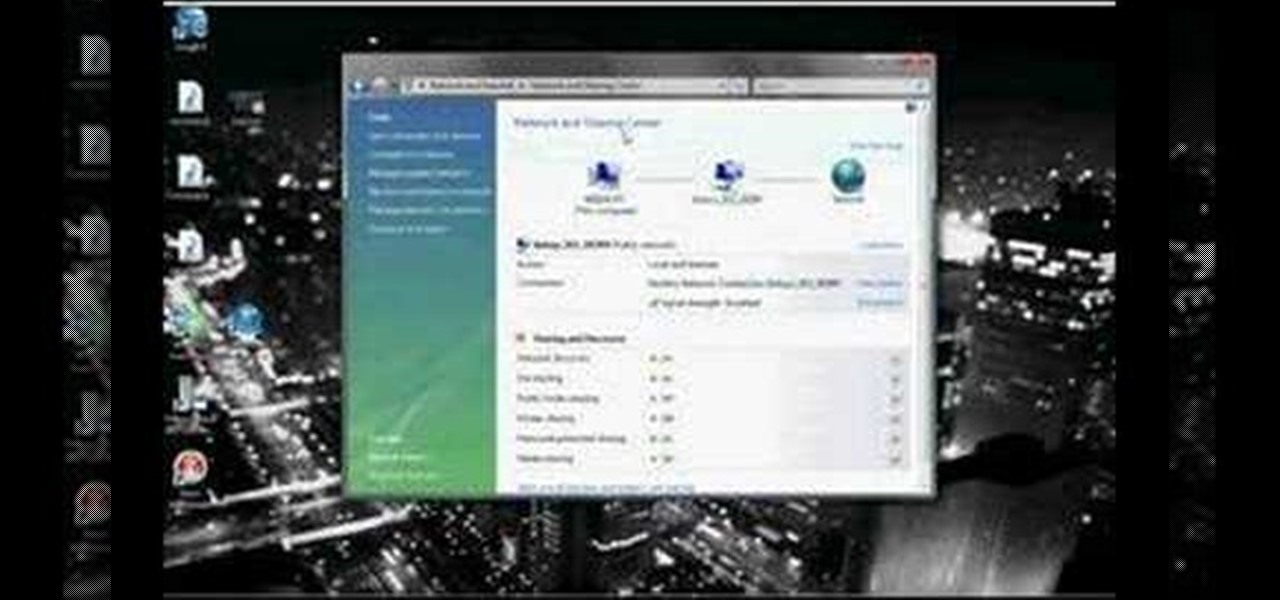
In this video tutorial, viewers learn how to connect an Xbox360 with wireless internet. Begin by connecting your computer to a wireless network. Click on the Start menu and select Control Panel. Go to Network and Internet, and select Network and Sharing Center. Under Tasks, click on Manage network connections and select your wireless connection. Right-click on the connection and select Properties. Go to the Sharing tab and check both the sharing options. Now click OK. This video will benefit ...
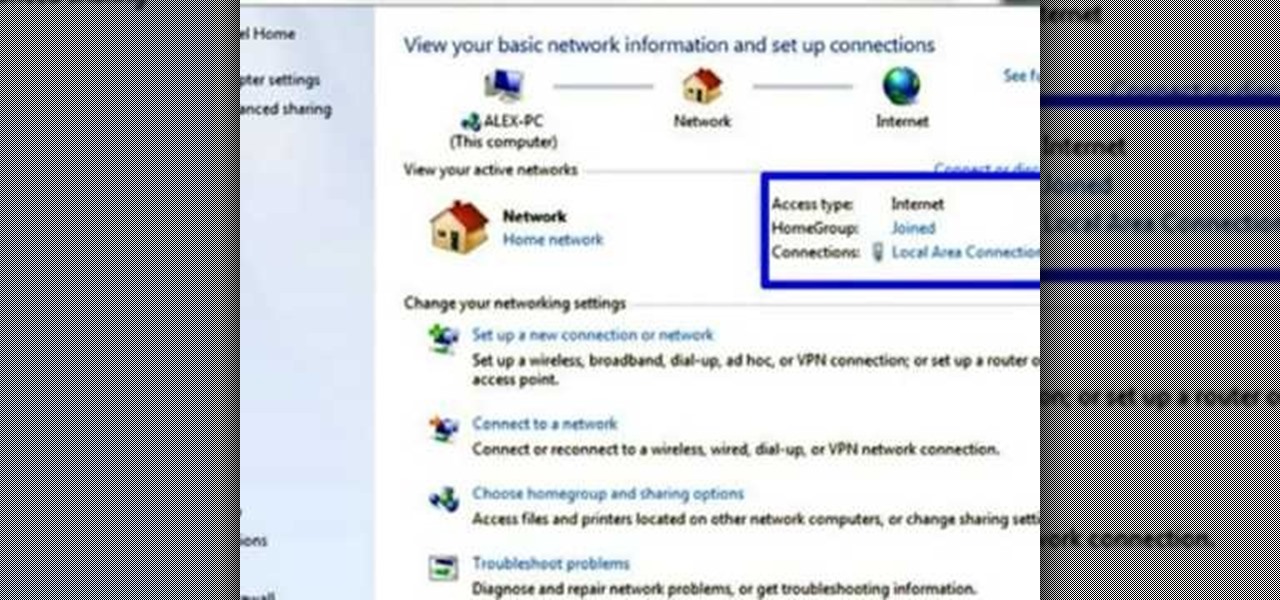
Want to access files from multiple computers at work or home? An expert from PC Remedies explains how to set up a Home Group network on Windows 7 systems. Includes a how-to of setting up your location, and managing the set-up wizard. Finally maximize your current resources by networking your work and entertainment files, as well as hardware such as printers. The excellent video gives you an exact snapshot of what you can expect to see on your own Windows 7 system. Includes advice on setting u...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

If you can't access your iCloud data such as emails, contacts, calendars, photos, notes, reminders, files, and other documents via a web browser on untrusted devices, like one at a library or friend's house, there's an easy way to regain access.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.
When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.
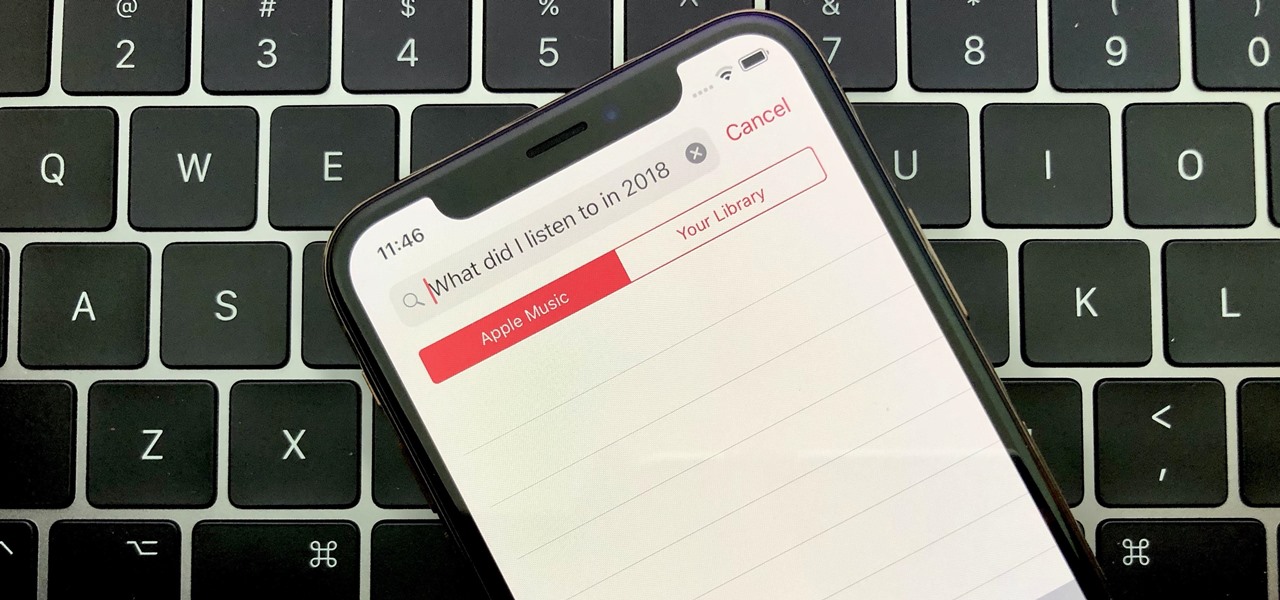
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.