
News: 'The Purge' Invades Your Safe Home via Mobile AR App
Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.


Have you ever wondered what it would be like to try to survive The Purge as depicted in the popular movie series? Well, thanks to augmented reality, now you can.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Just weeks after being acquired by comedian turned producer Byron Allen for $300 million, The Weather Channel has tapped augmented reality studio The Future Group to integrate immersive augmented reality experiences into its broadcast content.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
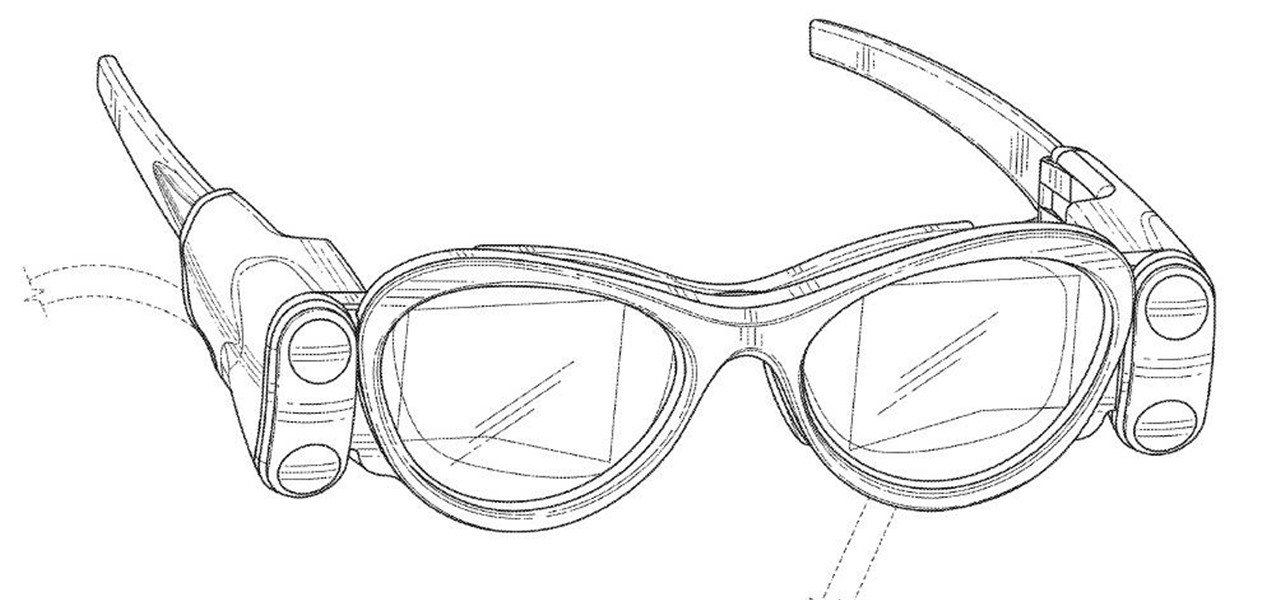
In June at the eMerge Americas investors conference, Magic Leap founder (and NR50 member) Rony Abovitz proclaimed that the launch of their flagship product was "not far away."
Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...
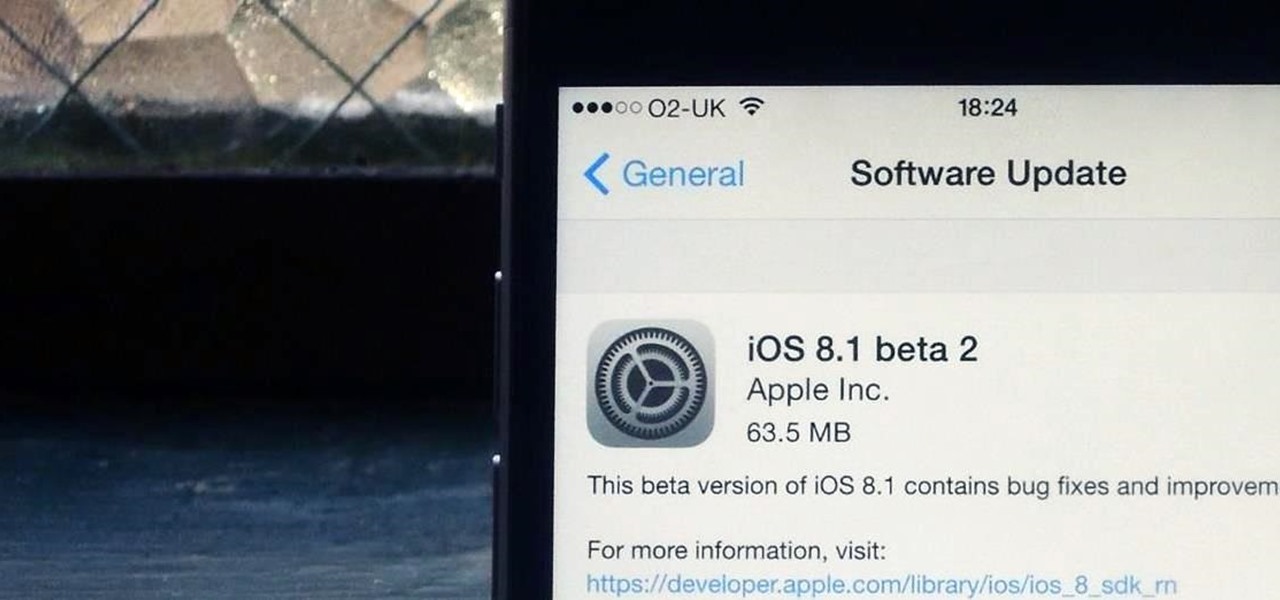
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

This video will show you how to enable or disable USB port in your PC. If you disable USB port nobody could insert a USB device on your computer and could not copy your data. You could enable the port whenever you needed. Watch the video and follow all the steps.
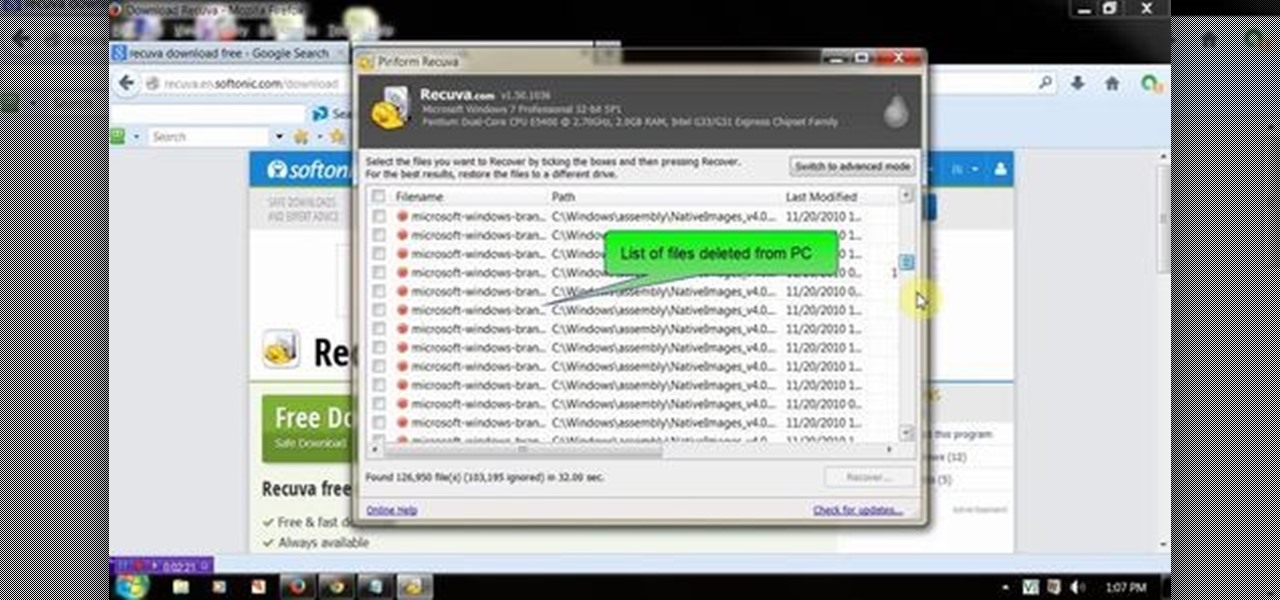
This video will show you how to recover permanently deleted file which you have deleted from recycle bin. But if any new file allocated to those positions then the files could not be recovered with this tool. Watch the video from the installation to execution of the tool to recover deleted data.

HTC's Sense 6 has been out for over a month now with the One M8, and most of you have probably played around with its better known features, like the new Camera app and Harman Kardon audio.
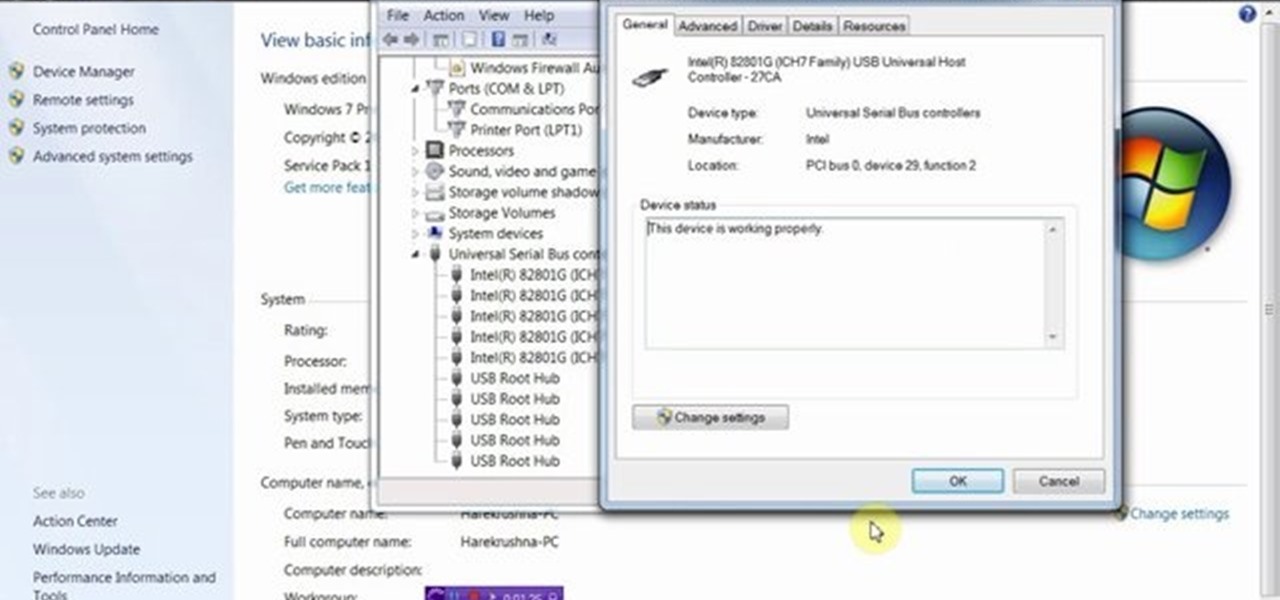
This video will provide an idea how to disable or enable the USB port on your PC. By disabling USB port will restrict people from copying your files into USB devices. This is a very effective trick to save your data. Watch the video and follow all the steps.
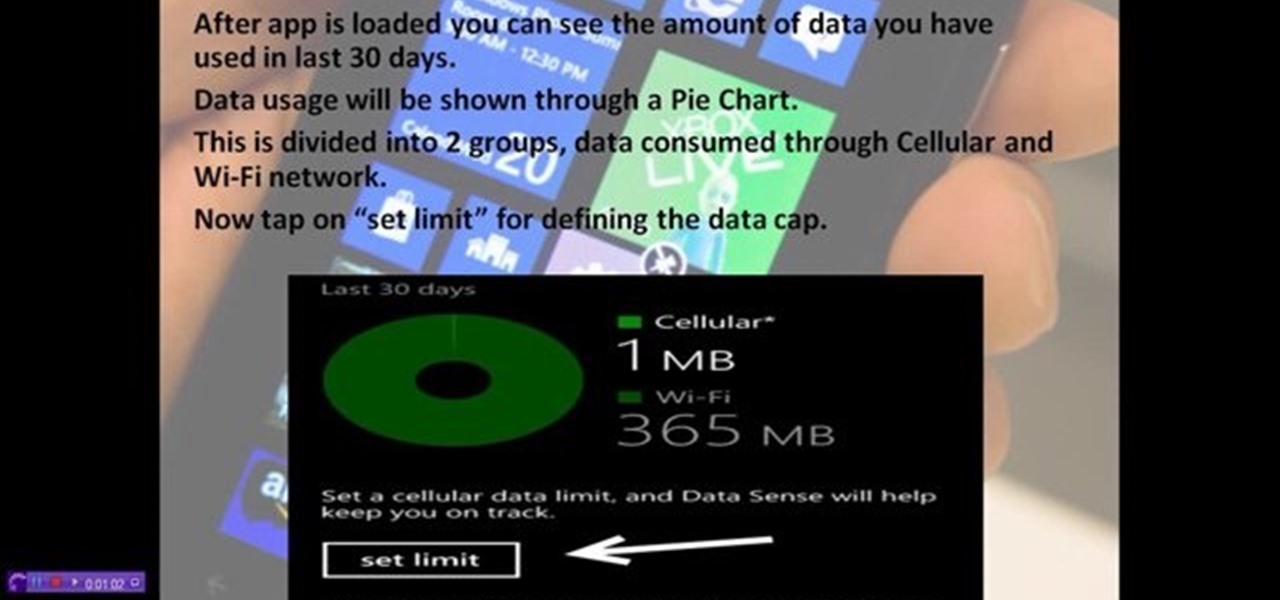
How to control and limit your internet usage in your windows 8 phone? You may want to restrict your internet usage and want to set limit for apps also. If you set your usage limit internet will stop automatically after reaching the limit. Follow the video to employ in your own phone.
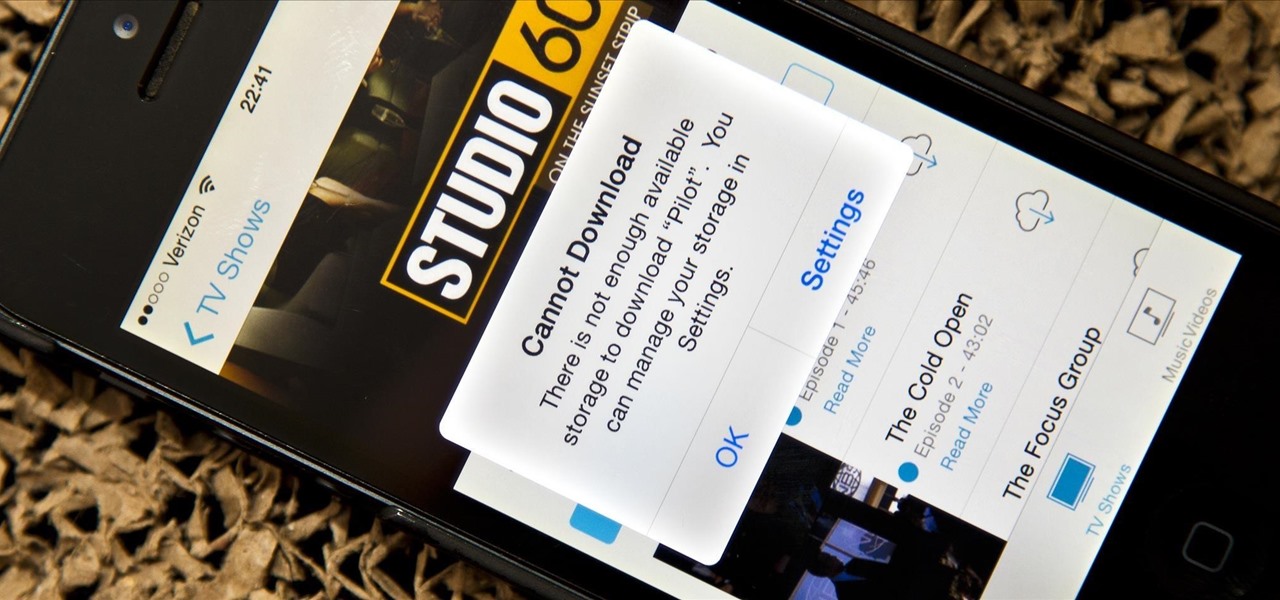
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back to its fresh-out-of-the-box state is a fairly simple process with the right tools.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Video: . this codes help

Want to breathe some life into your Macbook Pro? Get an SSD! But how to swap your data over? Here's how!

The new Samsung Galaxy S4 just received an update to Android 4.2.2, so why is it that my Galaxy Note 2 is still running an older version of Jelly Bean? It felt like yesterday that my device was finally updated to 4.1.2, but why even bother since 4.2 has been around since last November?

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected.

Self-restraint is one of the hardest thing to do. I'm a world-class procrastinator, and one of the biggest causes for my procrastination is my iPhone. Temple Run 2 was probably the best and worst thing that could have happened to me.