
News: Apple Working on AR Shopping App for iOS 14, Report Says
Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.


Apple's first AR wearable might not arrive until 2022, but we may have an early preview of what it will be like to wear a pair of its smartglasses via iOS 14.
Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.
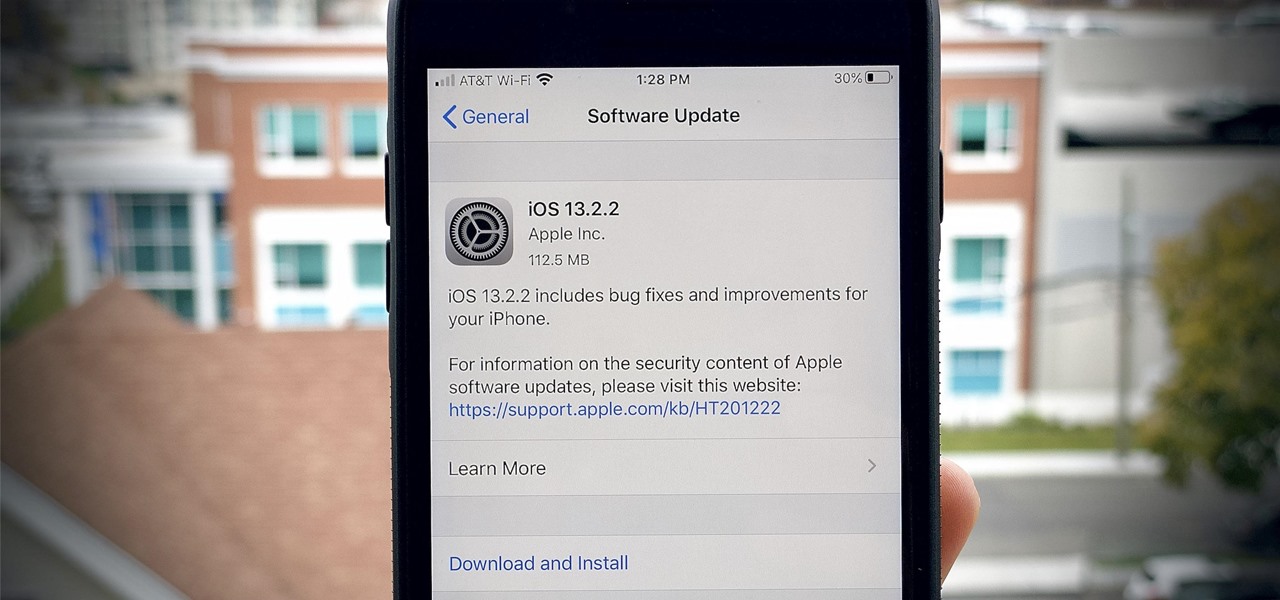
If you're a beta tester, you know Apple released iOS 13.3 this week, bringing with it stability for multitasking as well as minor changes throughout the OS. It seems Apple doesn't want the rest of us to go without this critical patch, as the company releases iOS 13.2.2 today, Thursday, Nov. 7.

Apple might be a secretive company, but it's showing its hand these past few weeks. The release of iOS 13 was met with much excitement for its hundreds of new features but also frustration over the numerous bugs. Apple soon released iOS 13.1, then iOS 13.1.1, as a patch for some of those bugs, but clearly they weren't enough. How do we know? The company just released iOS 13.1.2 today, Monday, Sept. 30.
Apps can collect a lot of data. Even if they don't have permission to access your GPS or camera, they can still read other sensors and learn a lot more than you'd think. Your gyroscope could be used as a keylogger. The light sensor could read your visited links. But if you're on Android 10, you don't need to worry about this.
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

While the next-generation HoloLens does not have a launch date yet, we now have a better idea of how big a leap the device will take in terms of depth sensor performance.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.
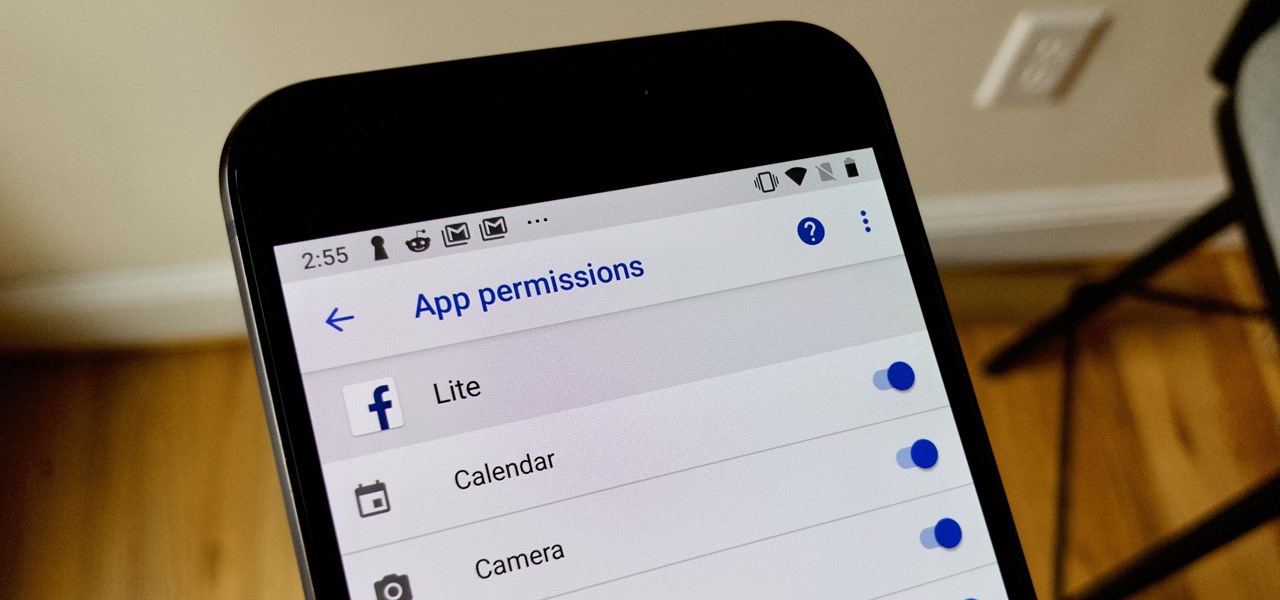
The Android world exploded when it was discovered that Facebook was logging the call and text histories of many of its users, although the company claims those users had explicitly given Facebook permission to log that data. The case remains that many users were unaware of this activity, which occurs on both Messenger and Facebook Lite. Luckily, it's very easy to disable.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.
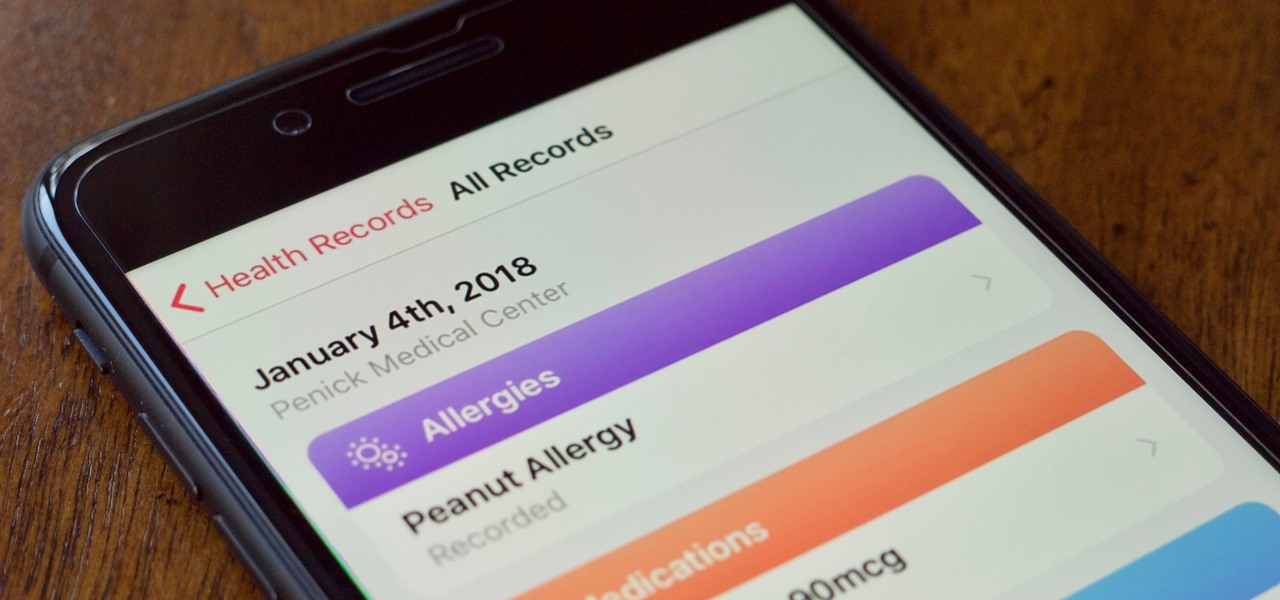
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

When it comes to Hi-Fi music streaming services, Jay-Z's Tidal is one of your only choices. But as you can imagine, true High Fidelity audio requires faster download speeds than your average music service. So the question becomes, how do you listen to Hi-Fi tracks on Tidal when a speedy internet connection isn't available? Offline music is the answer.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.
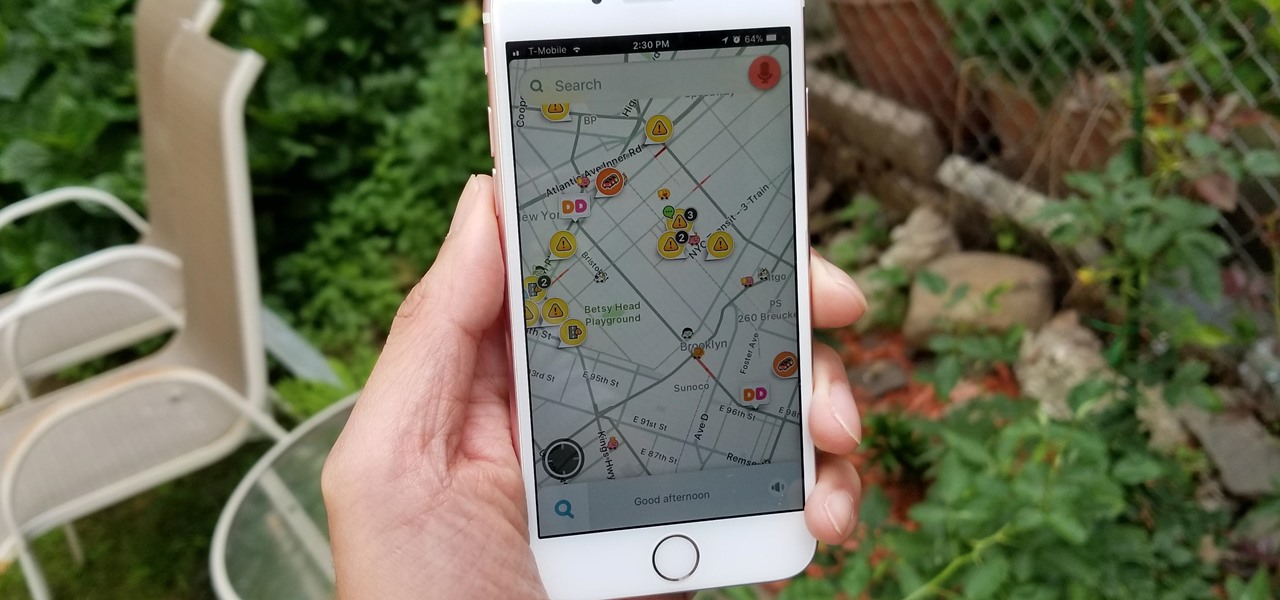
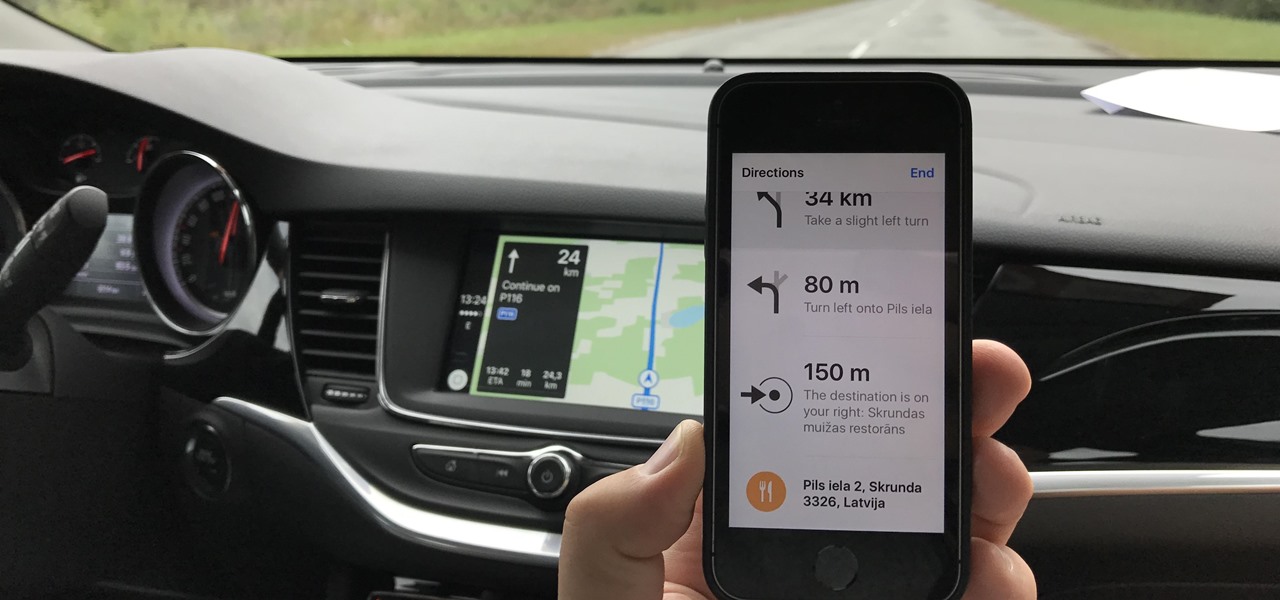
Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.
According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

As if being pregnant did not come with enough worry, a new study found that certain antibiotics are linked to an increased risk of spontaneous abortion, or miscarriage — a terrifying finding for any expectant mother.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.
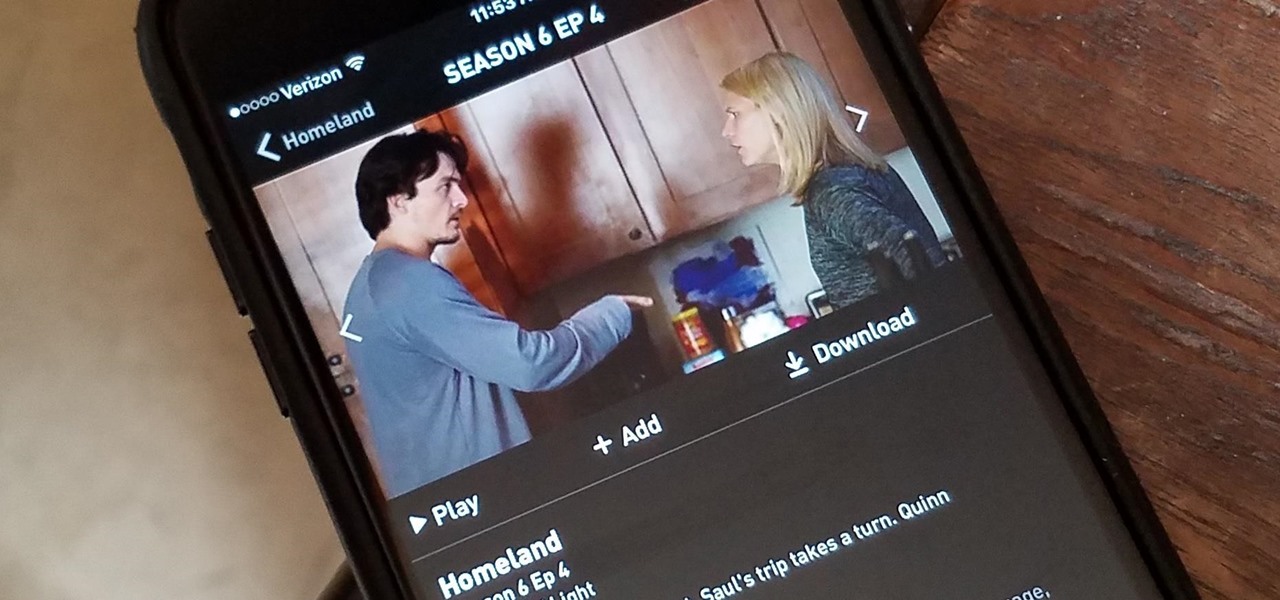
Have you ever wanted to catch up on Homeland or Shameless, but are out and about and don't want to use up your data? Those problems are for days of old now, as Showtime has announced their mobile app will allow titles to be downloaded and viewed without an internet connection.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.
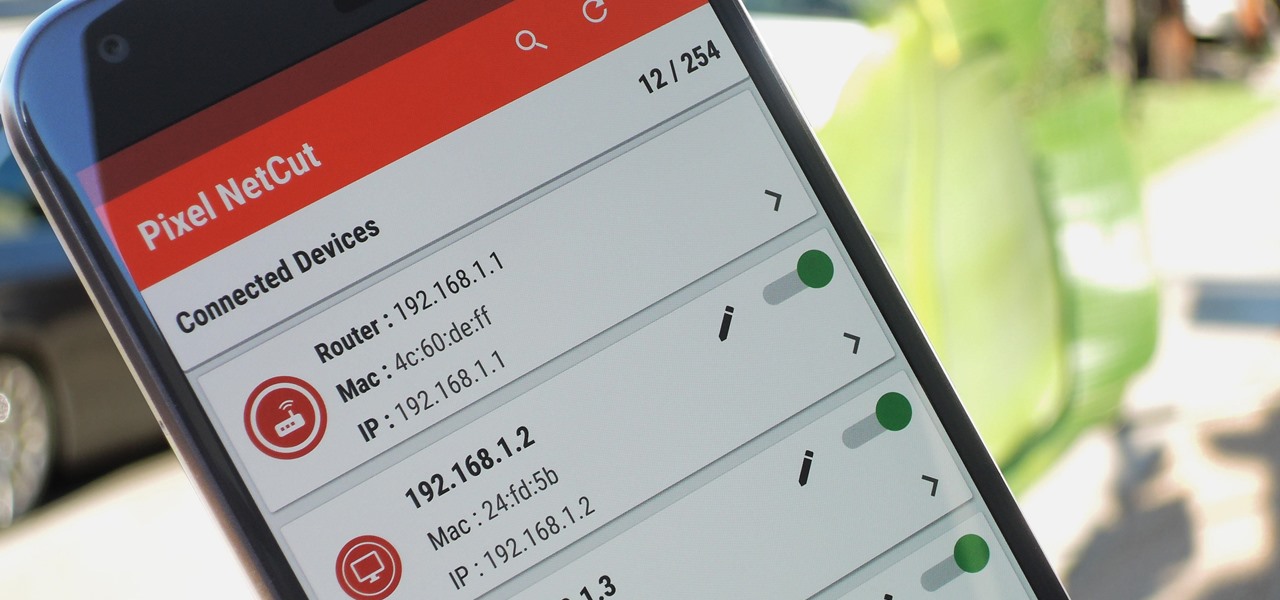
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Lenovo announced at Tech World '16 a slew of new products, and one of them aims to upend the smartphone accessory ecosystem: Moto Mods. Moto Mods are proprietary modular add-ons developed for two new Motorola phones that were also announced in the keynote, the Moto Z and Moto Z Force. Sixteen magnetic nodes align the bottom back of the phones that connect and hold accessories, forming a case appearance. The nodes transfer both data and power at high speeds, a fact that Lenovo hammered home wi...

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.