
Market Reality: Vuzix Reports Sales Growth & Partners with Blackberry
As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.


As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

The primary method of activating Siri is done by pressing and holding either the Home or Side button, depending on the iPhone model, but there's a much better way to ask a question to Siri or command it to do something — and you don't need to touch your iPhone at all to do it.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Last week, T-Mobile CEO John Legere got salty. He announced ever so cheerily T-Mobile's intentions to release the first true 5G network in coming years, all while gaily smacking AT&T around for their bogus "5G Evolution" reveal. But could Legere be wrong to say T-Mobile will be the nation's first 5G carrier? It looks as though that title may have to be shared with Sprint ...

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Uh oh. With millions of devices already sold, Apple's latest blunder is bound to upset the owners of some of their brand new iPhone 7 Plus phones.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught unaware.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Android Debug Bridge, or ADB for short, is a very powerful utility that can remotely execute commands on your Android device. This remote terminal interface, however, is not very "remote" at all. You have to be tied down to your computer to use it, since a USB cable is normally required.

This tutorial video will show you how to connect a wifi network in your Samsung Galaxy S5. This is very easy to employ. So please watch the video. Follow all the steps to do it yourself in your Samsung Galaxy S5 phone and enjoy a wifi environment.
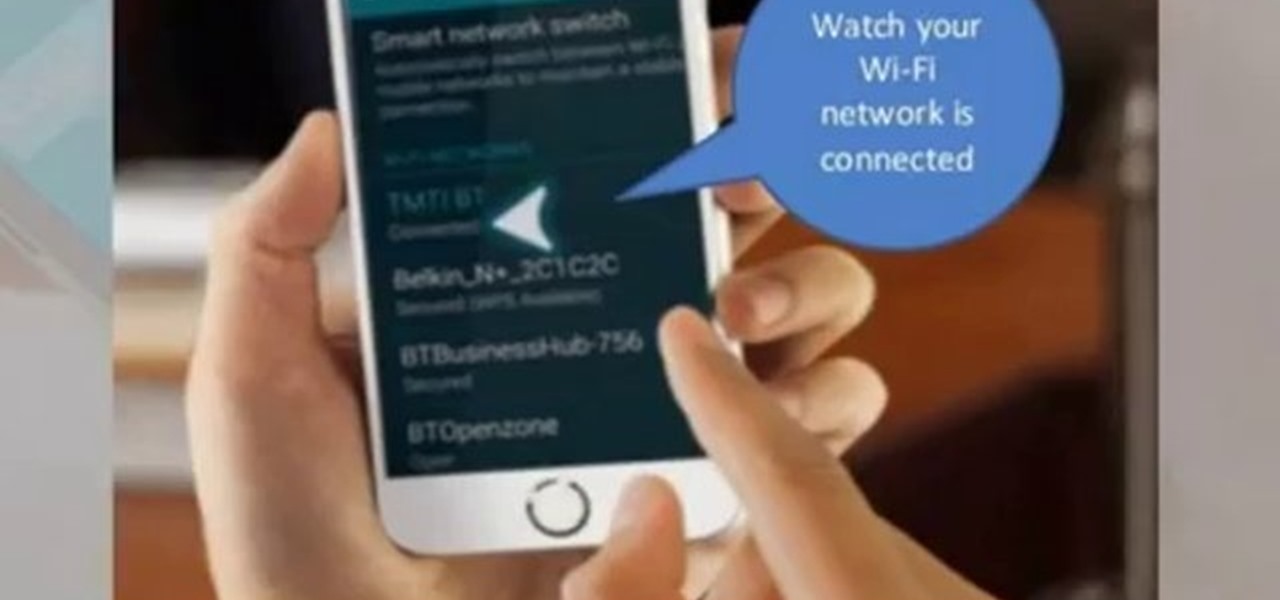
This video will show you how to set up a connection with wifi network in your Samsung Galaxy S5. So please watch the video and follow all the steps carefully. Employ the technique in your Samsung Galaxy S5 phone and enjoy a wifi environment.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

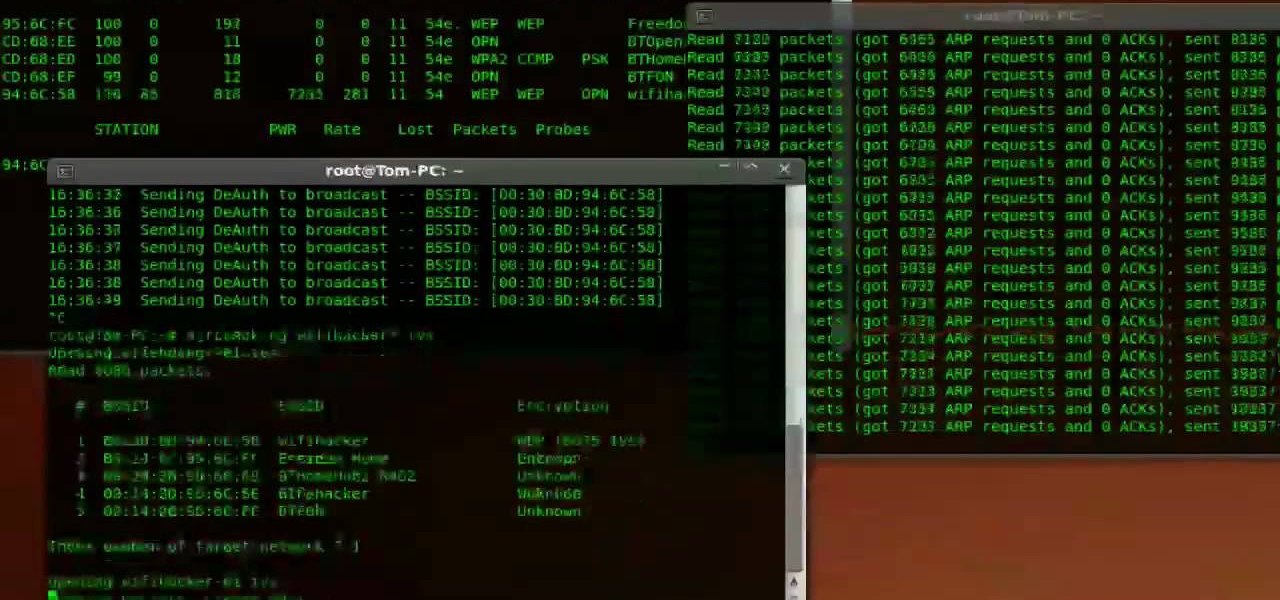
Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.
Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

Hey all, in this video tutorial I explain 3ds Max Network Rendering, and queuing multiple scenes for rendering.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Several people have been reporting Wi-Fi problems after updating to iOS 6 on both iPads and iPhones. The connection might work sometimes, but it usually cuts out or takes forever to connect to anything, only to time out shortly after.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...
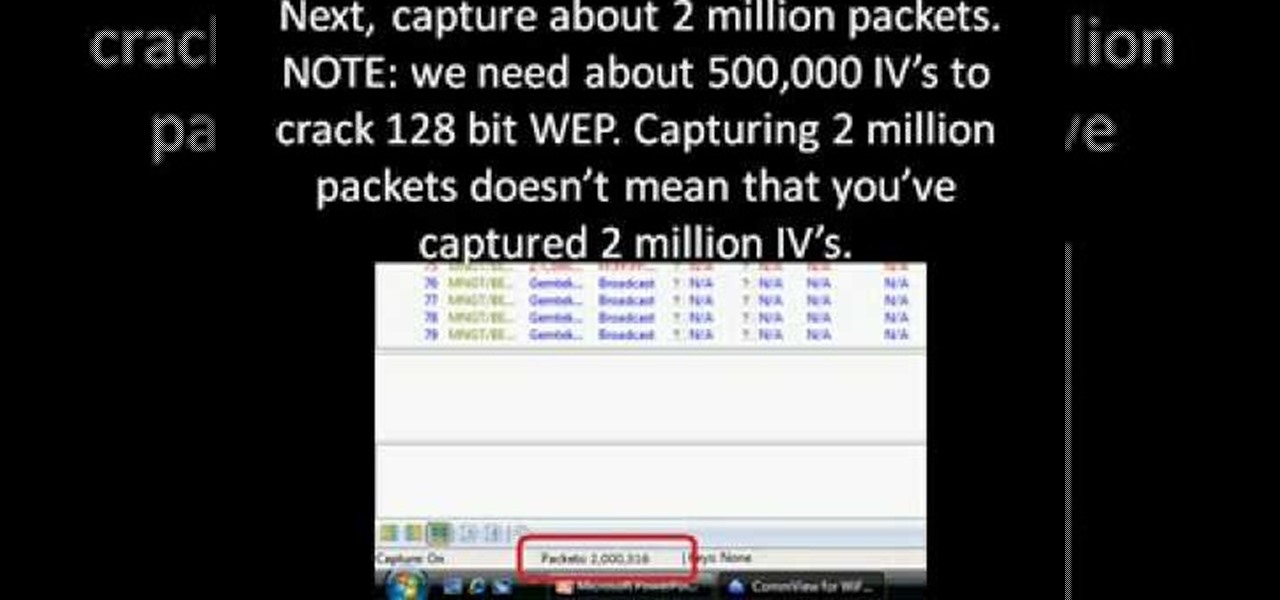
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.
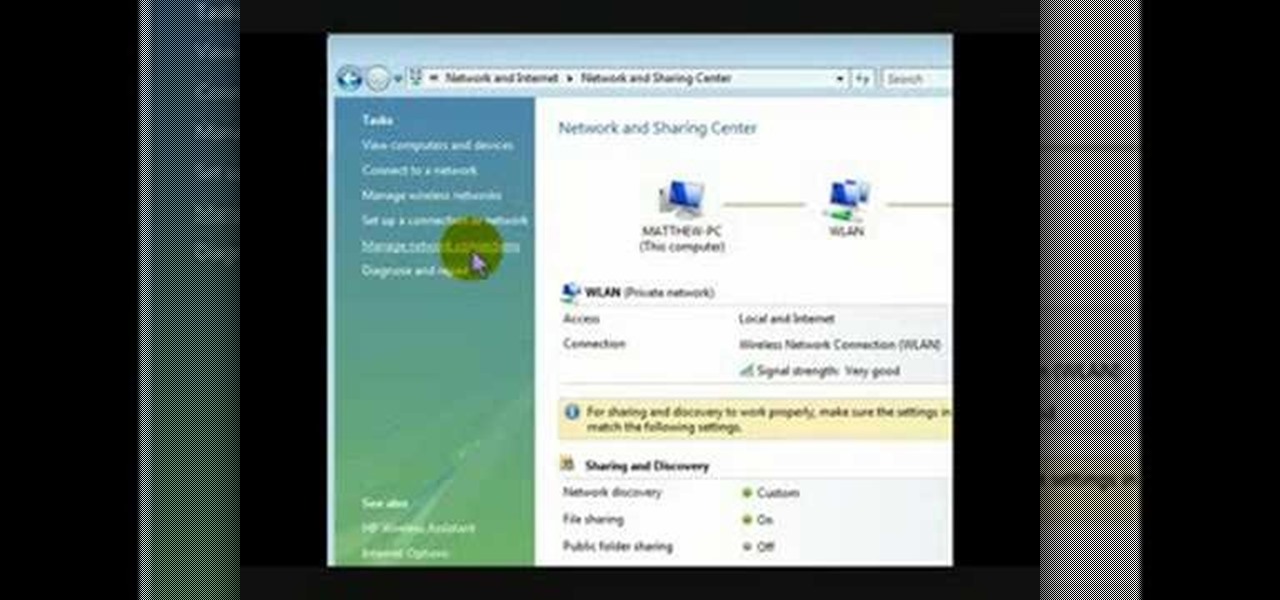
This is a video that is describing how to connect your xbox360 to the internet using a laptop. First what their showing is going to the start menu, and then to the right of it, click on control panels. A little page will pop up, and you click on network and internet. It takes you to another page and then you click network and sharing. It will take you to another page, where you see three computers, and to the very left of that page there it says "tasks" look in the columns under tasks and cli...

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.
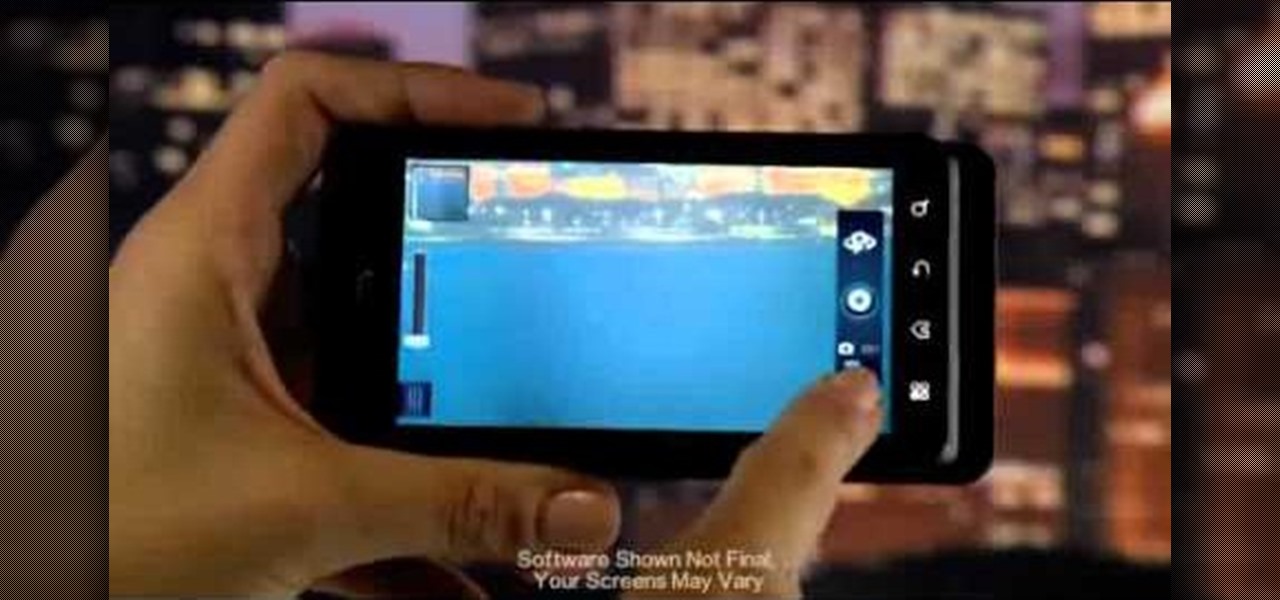
The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.
Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

With the economy as terrible as it is these days, obtaining any sort of job, from receptionist to screen writer, requires thorough networking.
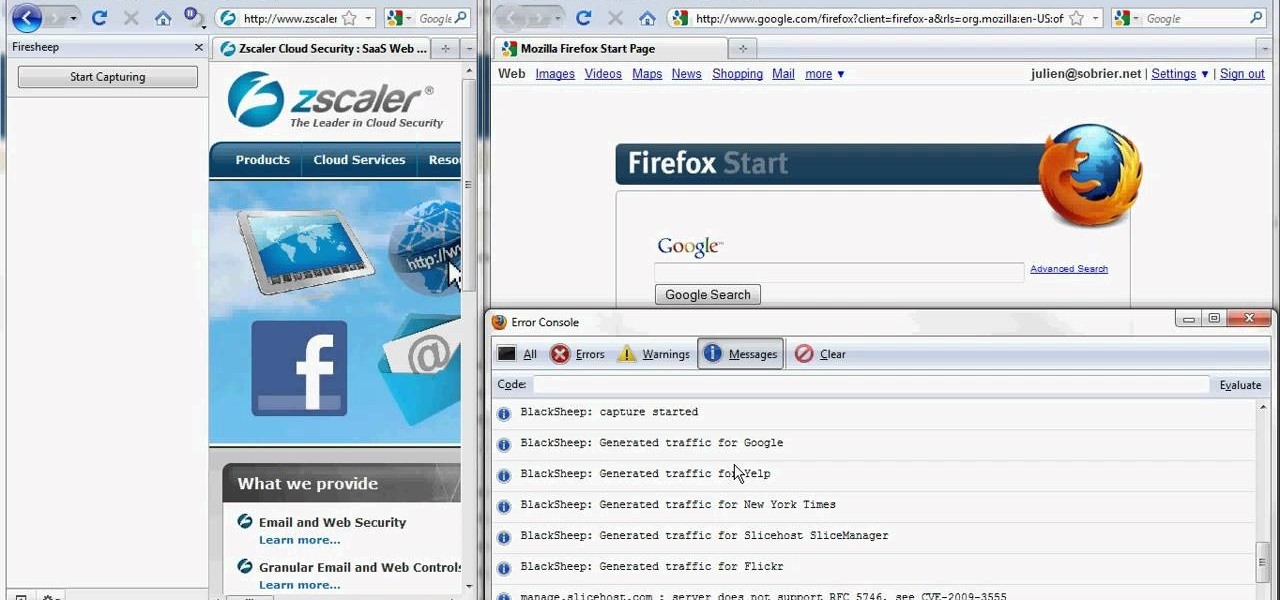
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.