
News: Next iPhone Could Be Li-Fi Compatible, Up to 100 Times Faster Than Wi-Fi
A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.


A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

Hello friends. This is actually my first how to.
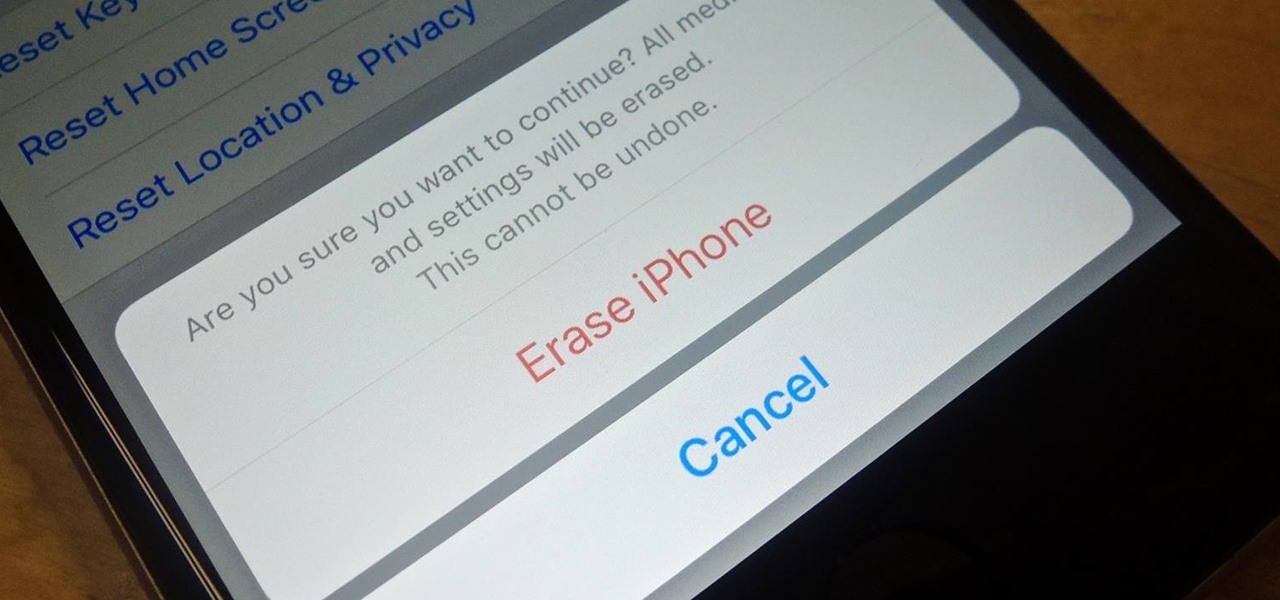
Before you sell your old iPad, iPhone, or iPod touch to a buddy or a company like Gazelle, it's vital that you wipe the entire device of all its content; including sensitive material like contacts, messages, pictures, and videos. There are two easy ways to wipe your iOS device, so let's show you how to do it using iTunes or directly from the device itself.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Why did I write this when they're tons of scanning tools available.
Well, this is my first article so if it sucks tell me...lol!! Story Time

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.
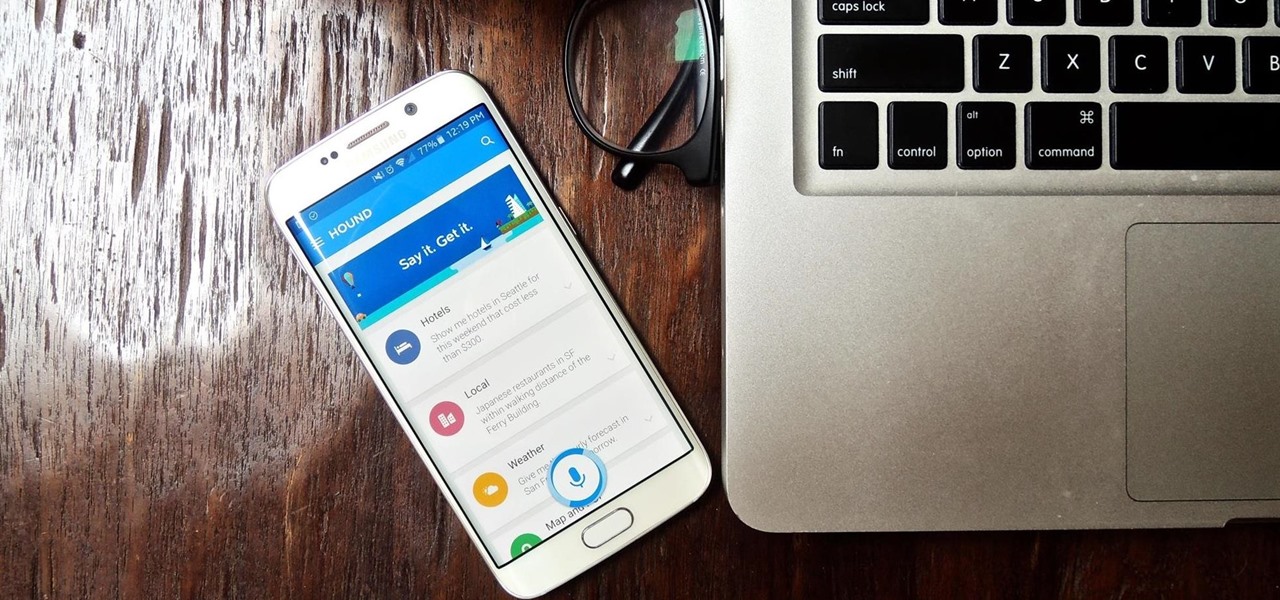
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).
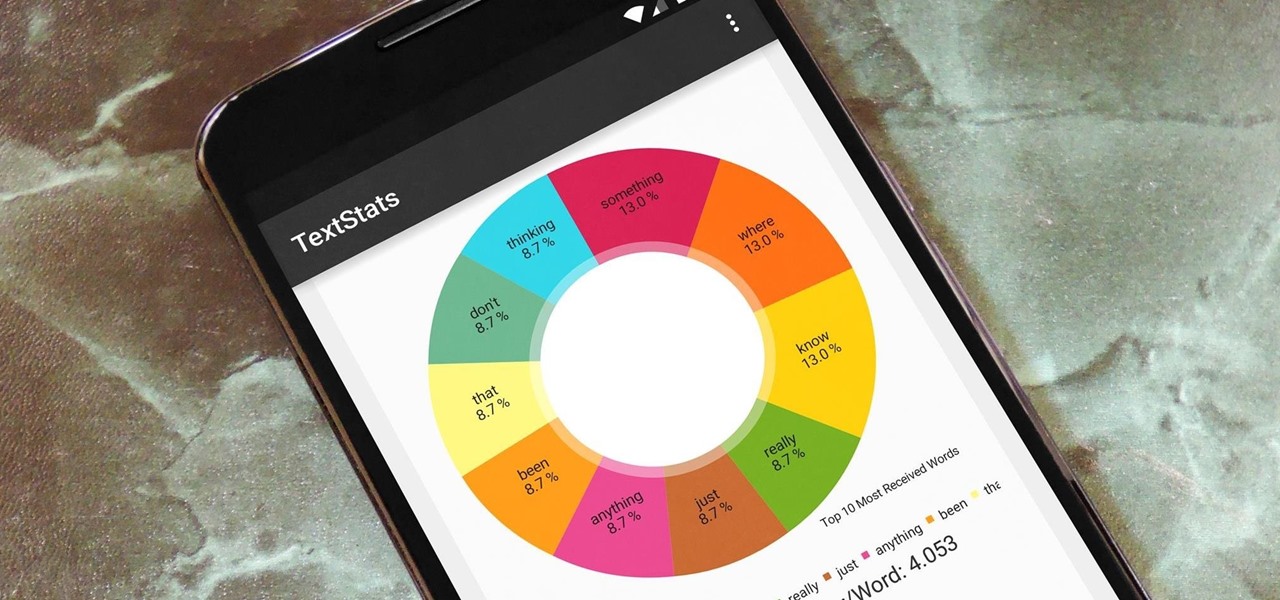
With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the nature of the beast.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

Android automatically clears entries in your call log after 30 days. While this might be fine in most cases, sometimes you need to find a number that called you more than a month ago. Or perhaps you want to keep detailed records for business purposes, and 30 days just isn't long enough.

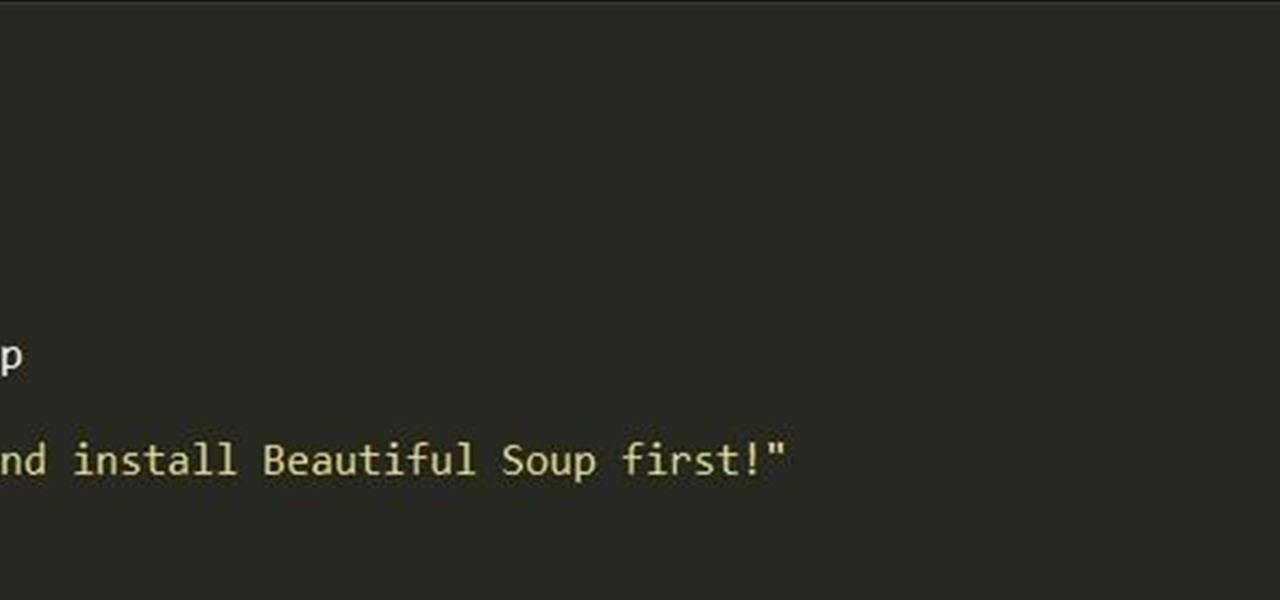
Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.
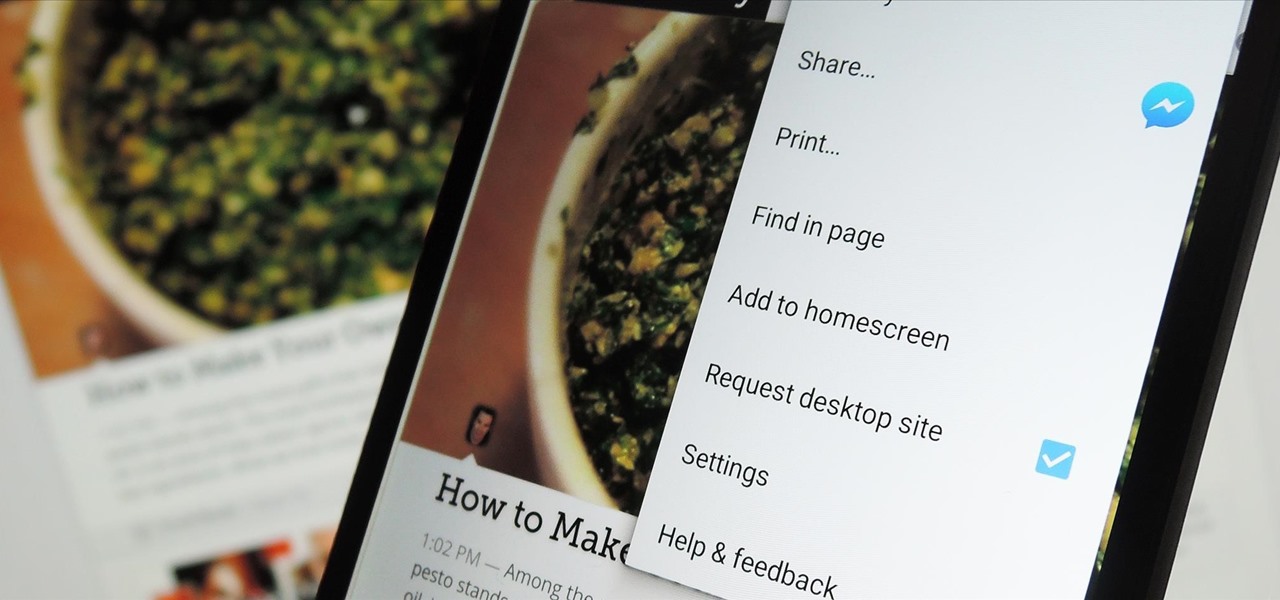
The majority of Android web browsers carry a "desktop mode" feature that makes mobile websites look like normal computer versions. Mobile versions are designed to work faster and more efficiently on smartphones, but sometimes the desktop version looks better on large displays or has additional features not included in the mobile one.

Android 5.0 "Lollipop" has only existed for a few months, but a leaked version of Samsung's take on the firmware has already been spotted in the wild. This update came straight from Samsung, and brings with it a plethora of new features, including greatly improved performance and a revamped TouchWiz UI.
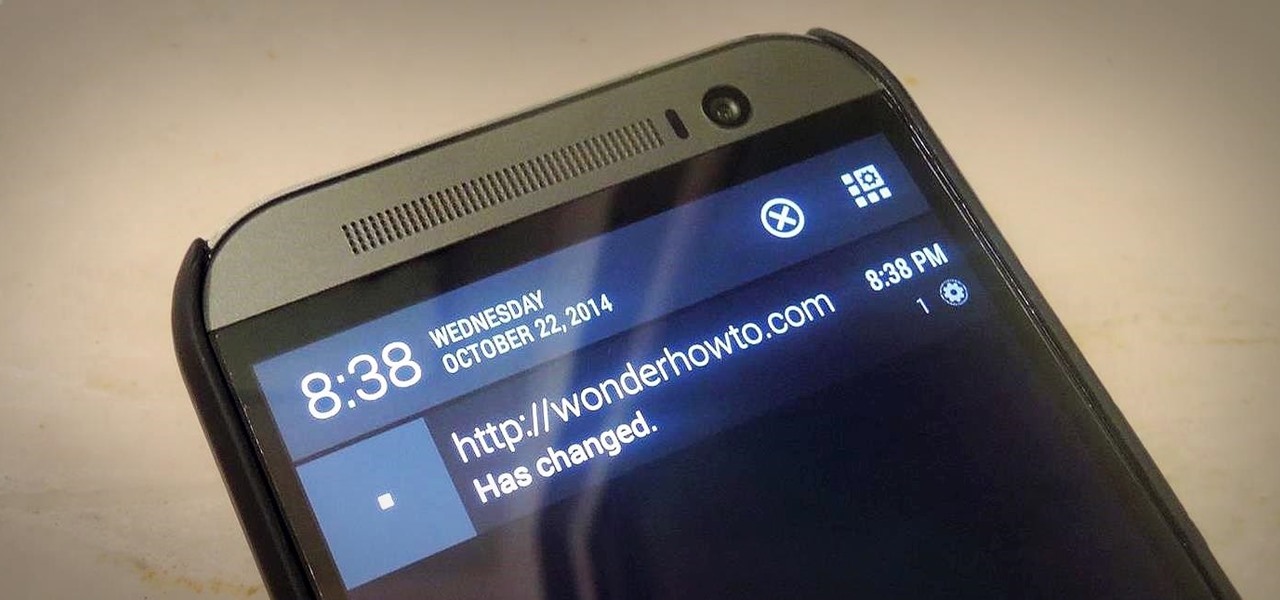
The problem with striving to be on the bleeding edge of what's new for your smartphone, or really anything else in life, is having to constantly check websites and forums for new content. And with lots of that browsing happening on our phones, the aimless page loading and refreshing is not just annoying when there isn't new content, but can lead to wasted data usage, not to mention time.

With developments from tech giants Apple and Samsung being shared throughout the interwebs, the term smartwatch has become increasingly popular over the last year. That being said, smartwatches have been around for a while.
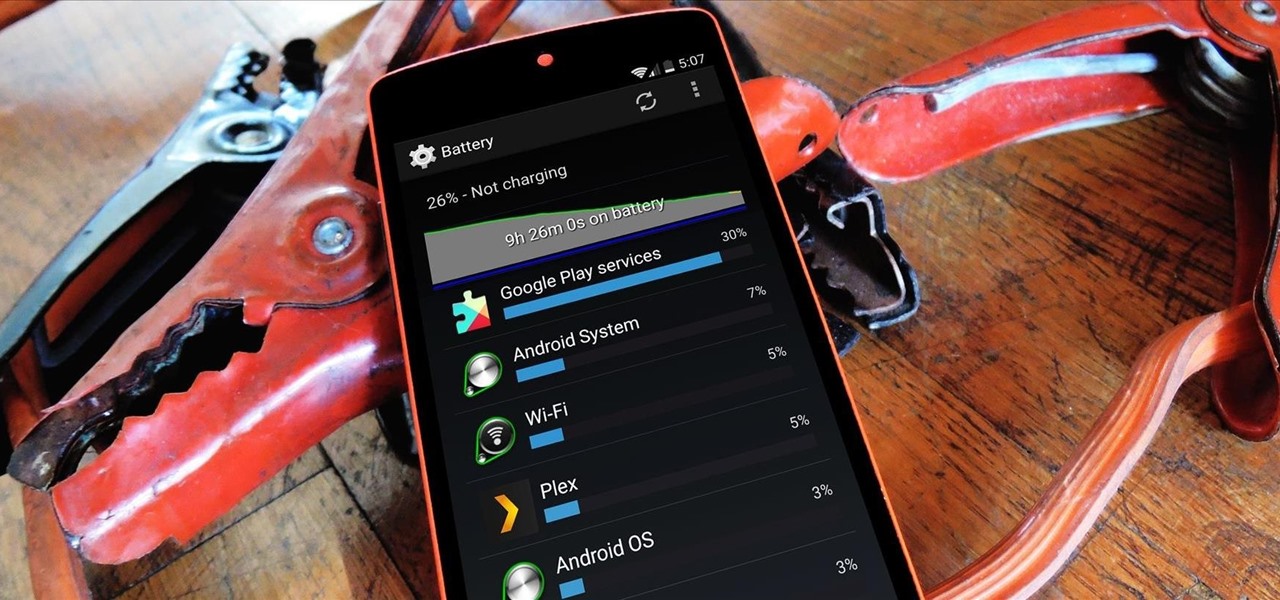
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.
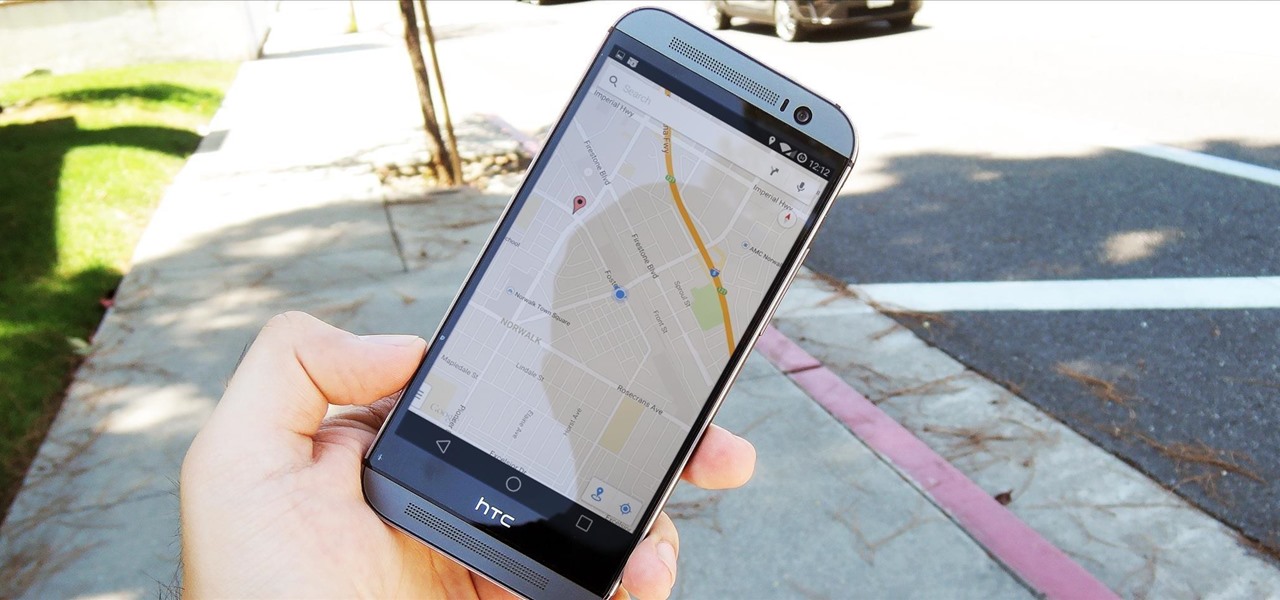
Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.

Last week, I showed you a peek at the not-yet-released Galaxy S5 Active, the more rugged version of Samsung's current flagship. The man behind those leaks, TK Tech News, has now brought another goodie from the device, and it's one we can have on the Galaxy Note 3.

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.
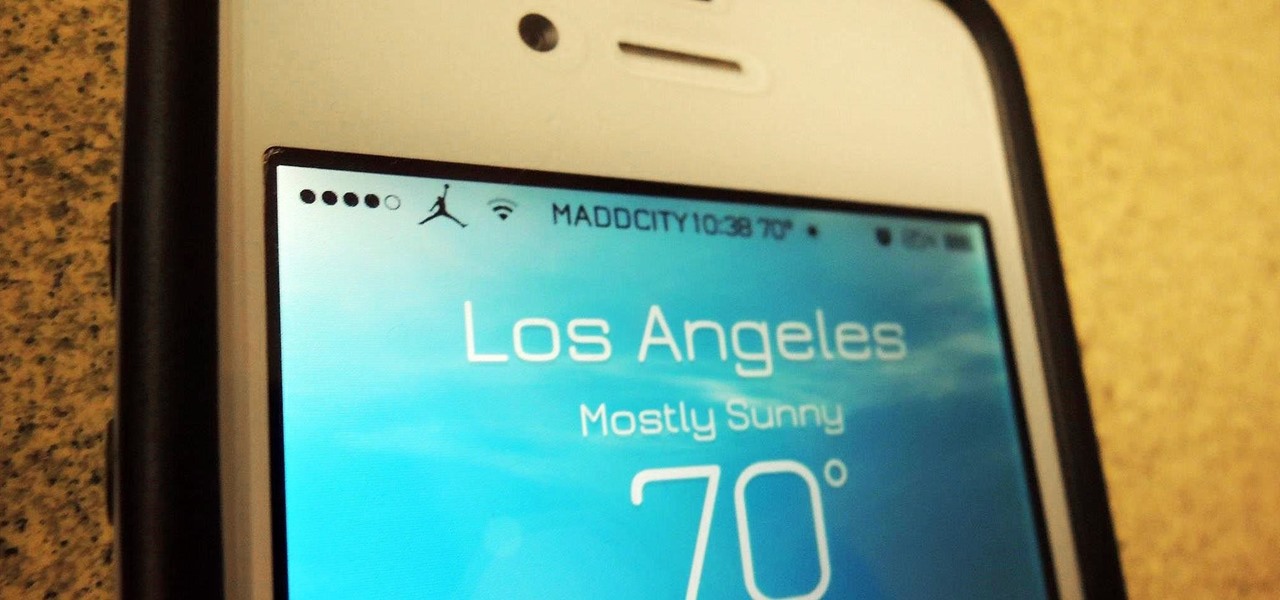
While it may not serve much of a purpose here in sunny Los Angeles, it's still a good idea to keep constant tabs on the weather forecast, because you don't want anything to rain on your parade.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless.

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.
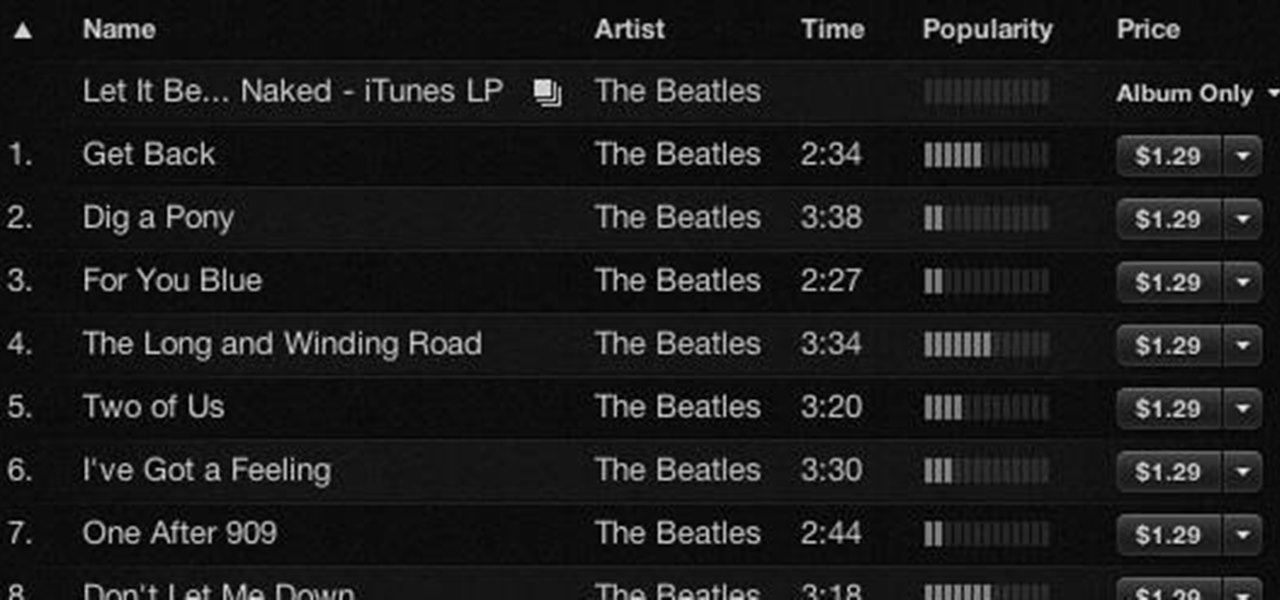
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.
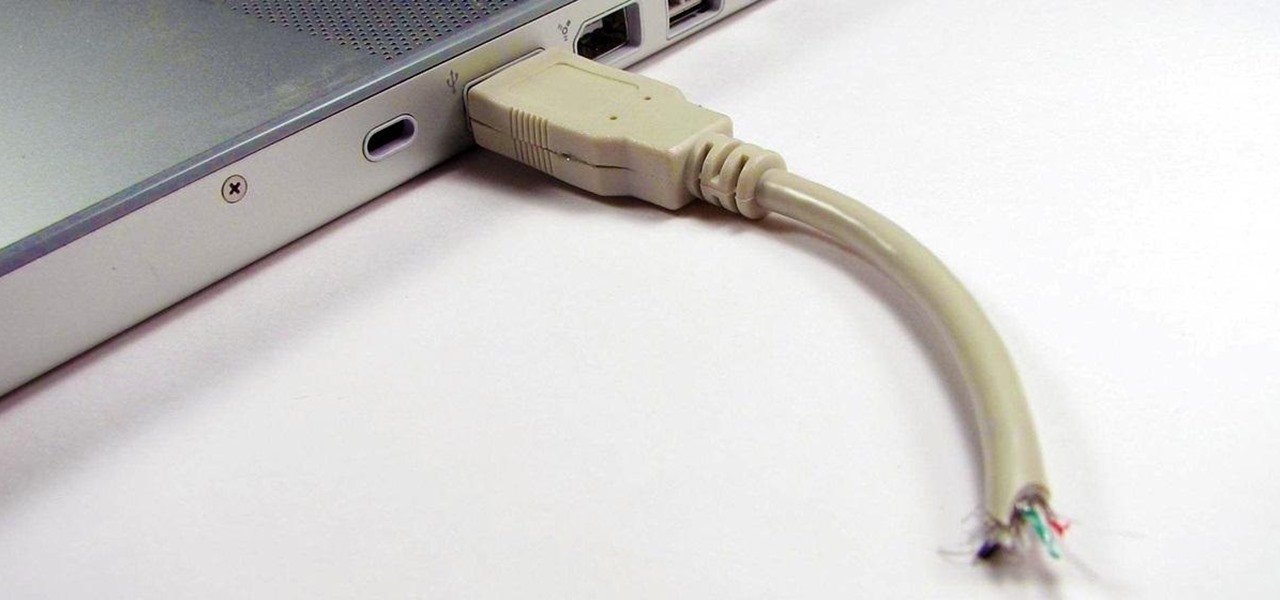
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
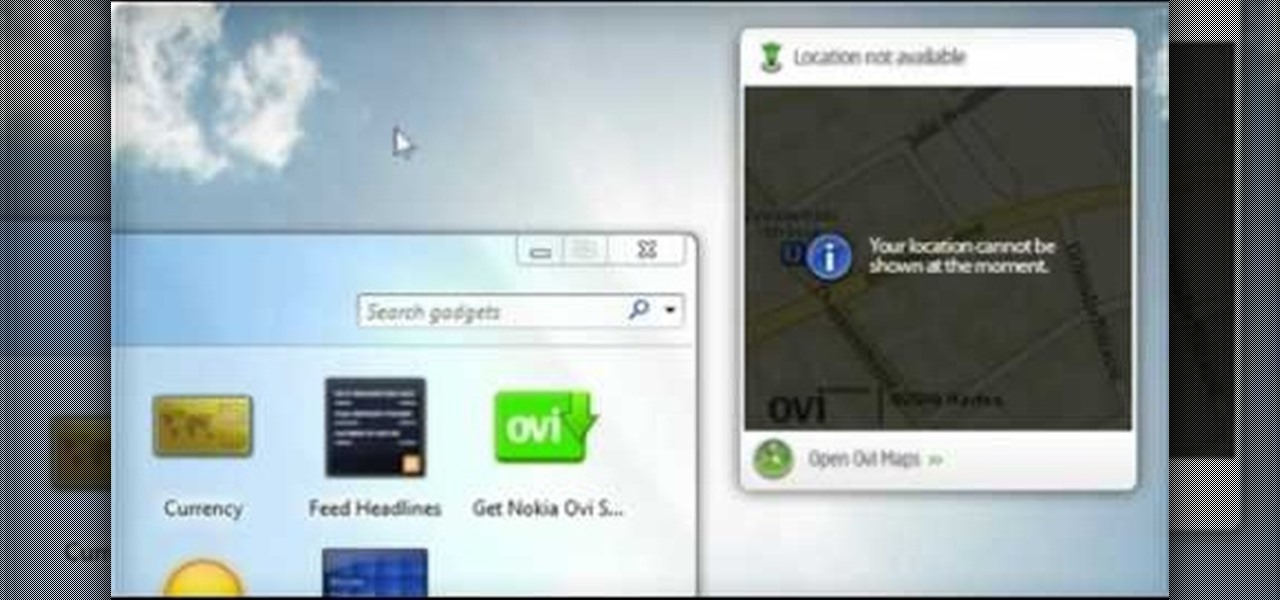
The Nokia Booklet 3G netbook is capable of utilizing GPS when the 3G network connection is active. If you want to find your location and see a map of the area around you, try out the Maps gadget available as part of the Ovi Suite.
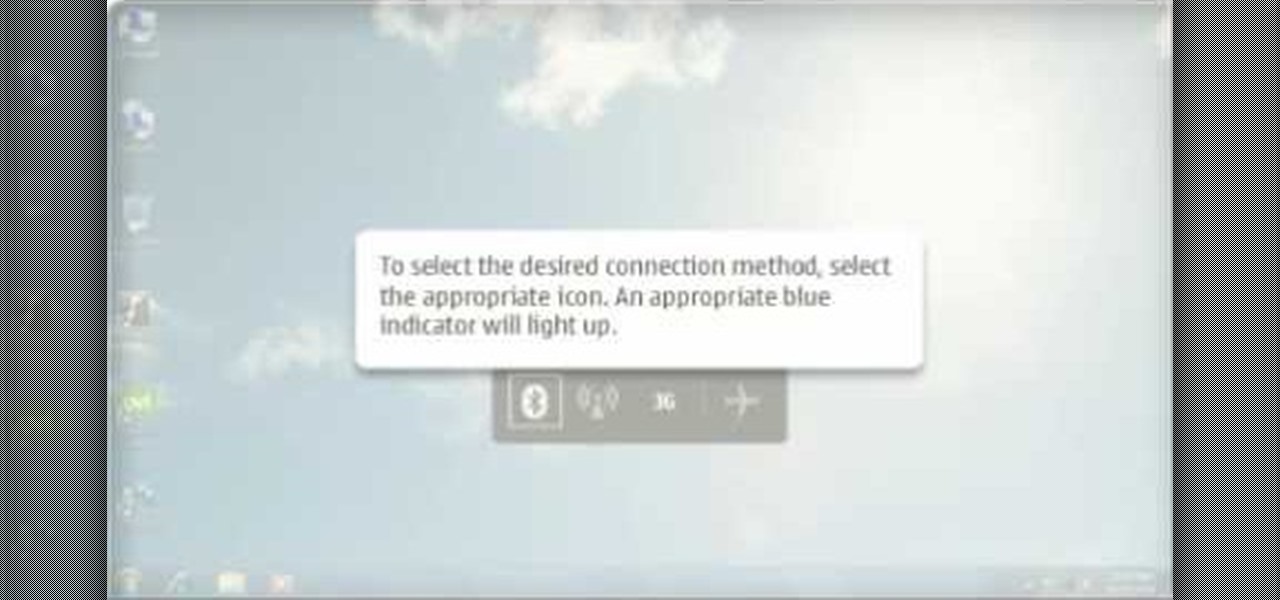
If you hit the FN + F10 keys on your Nokia Booklet 3G, you'll see the available internet connections methods for your netbook including Bluetooth, wifi, and 3G.