This video demonstrates how to discover the dating history of people by searching on the website www.rateabull.com. The site searches their own dating database, as well as several other social networking sites.

Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!

Got movies and music on your PC? See how to stream through your Xbox 360 right onto your TV screen. You'll need to have your Xbox 360 connected to your home network first.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)
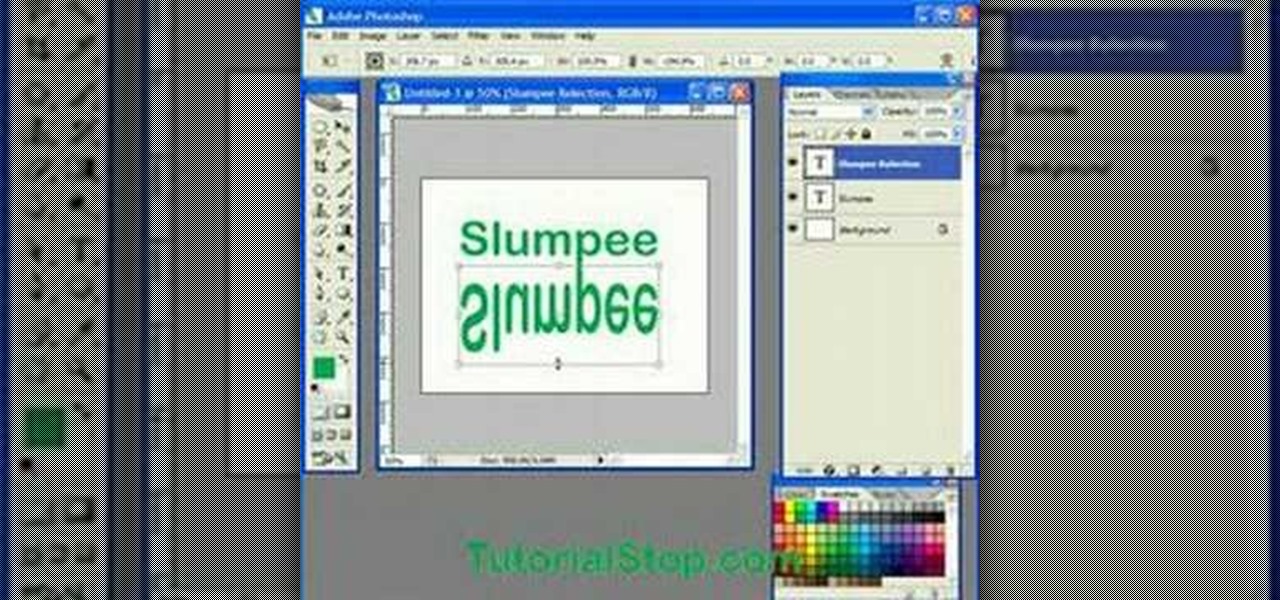
In this video tutorial you will learn to use Photoshop to create a shiny reflective logo in a web 2.0 style. Not sure what Web 2.0 is? It generally refers to a perceived second generation of web-based communities and hosted services — such as social-networking sites, wikis and folksonomies — which facilitate collaboration and sharing between users.
This video helps you to protect your computer against viruses and spyware often contracted when using peer to peer (p2p) networks like limewire, kazaa and emule.

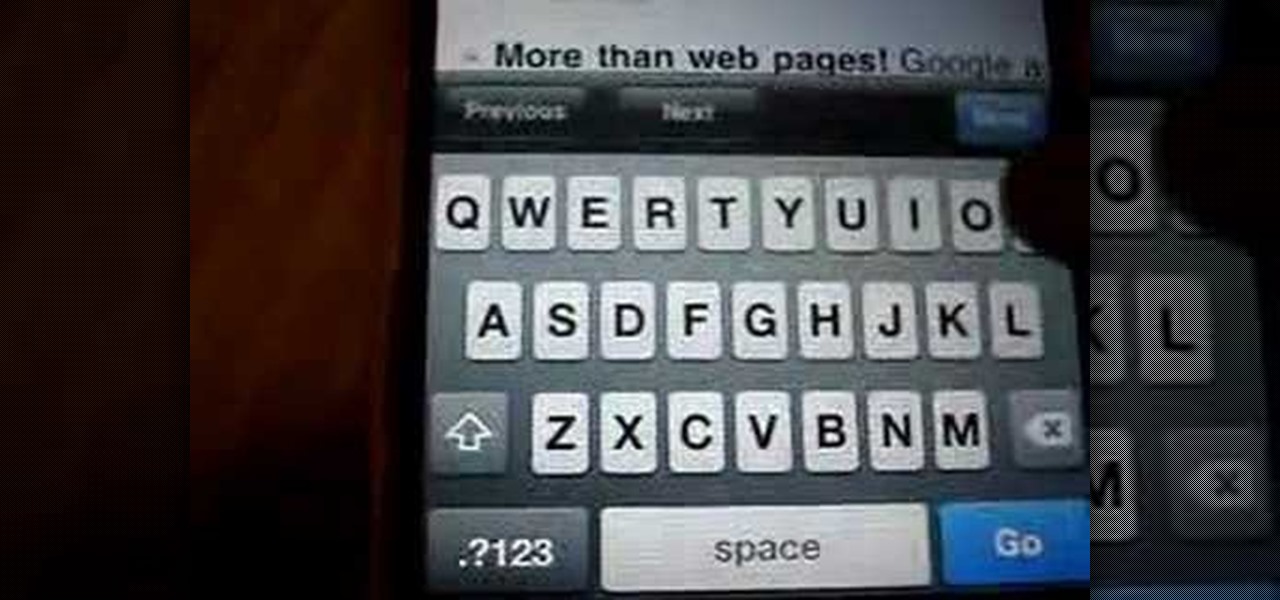
Speed up your EDGE network connection on the iPhone up to 5xs. Change your settings to optimize connection speed not using WiFi.

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...

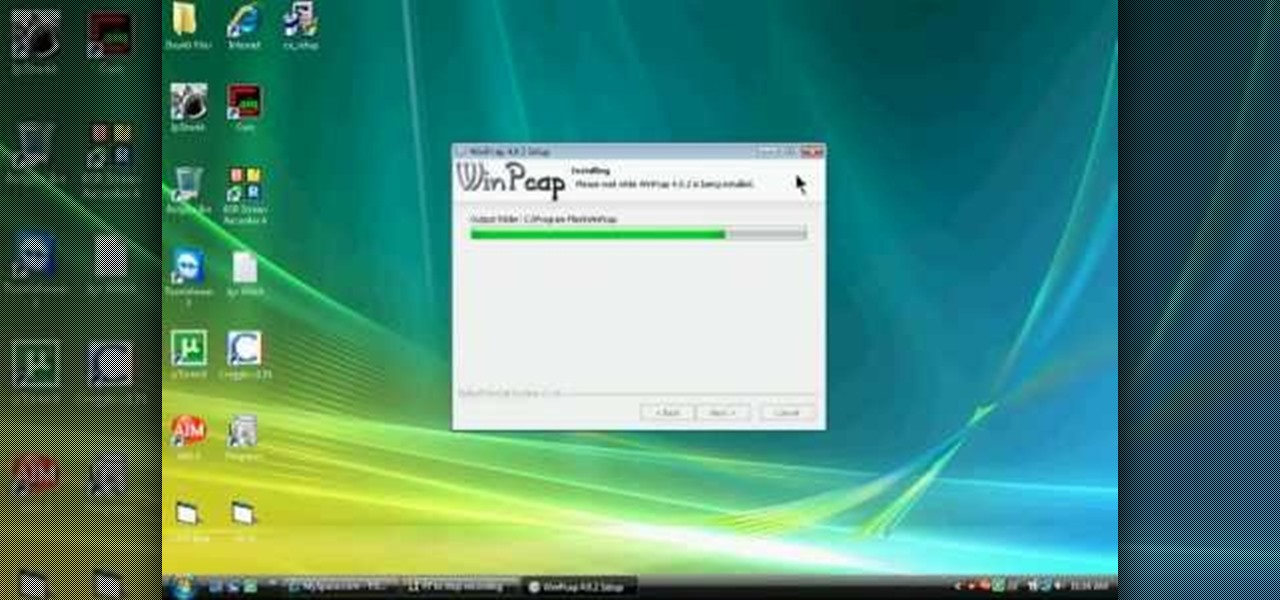
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...

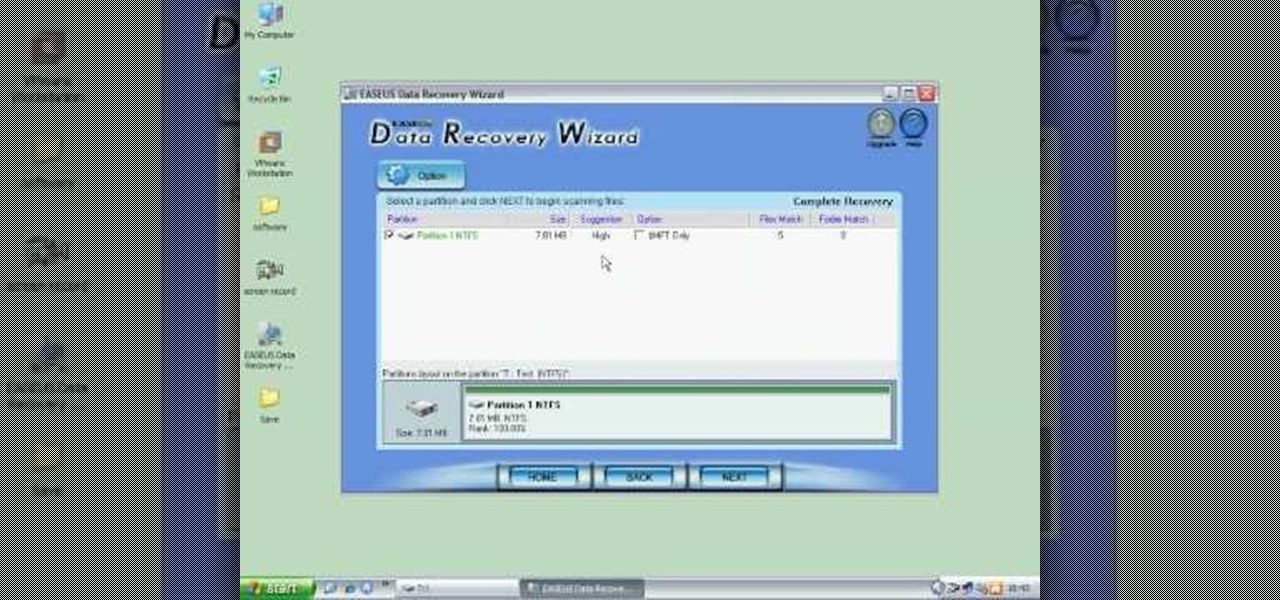
In this video the instructor shows how to restore lost data. When you delete your files you can restore them from the recycle bin. But if a hard drive is formatted all the data is lost and you can not even recover it from recycle bin. In such cases you will need to use data recovery tools to recover that lost data. In this video the instructor uses the Data Recovery Wizard software to recover the data. Start the Data Recovery Wizard. In that there are three options by which you can recover yo...

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

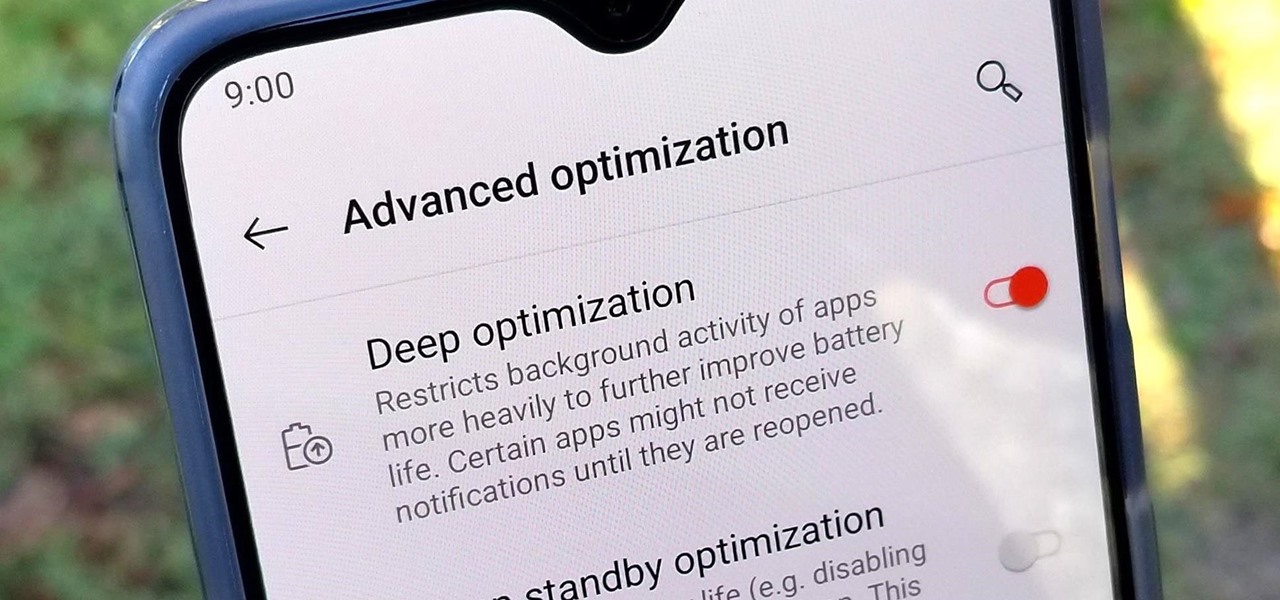
OnePlus is known for pushing the boundaries of what we thought was possible for a mid-range price. One of the best things about OnePlus phones is that their battery life is fantastic in general, but to achieve this, Oxygen OS will disable or delay notifications by default once your phone goes into deep sleep mode. You will not be notified until you wake the phone up — this could be an issue for some.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

If you've gone anywhere near a television in the US in the last 48 hours, you've probably seen some of the reports of Hurricane Florence and its devastating wind and rain making its way toward the Carolina coast.

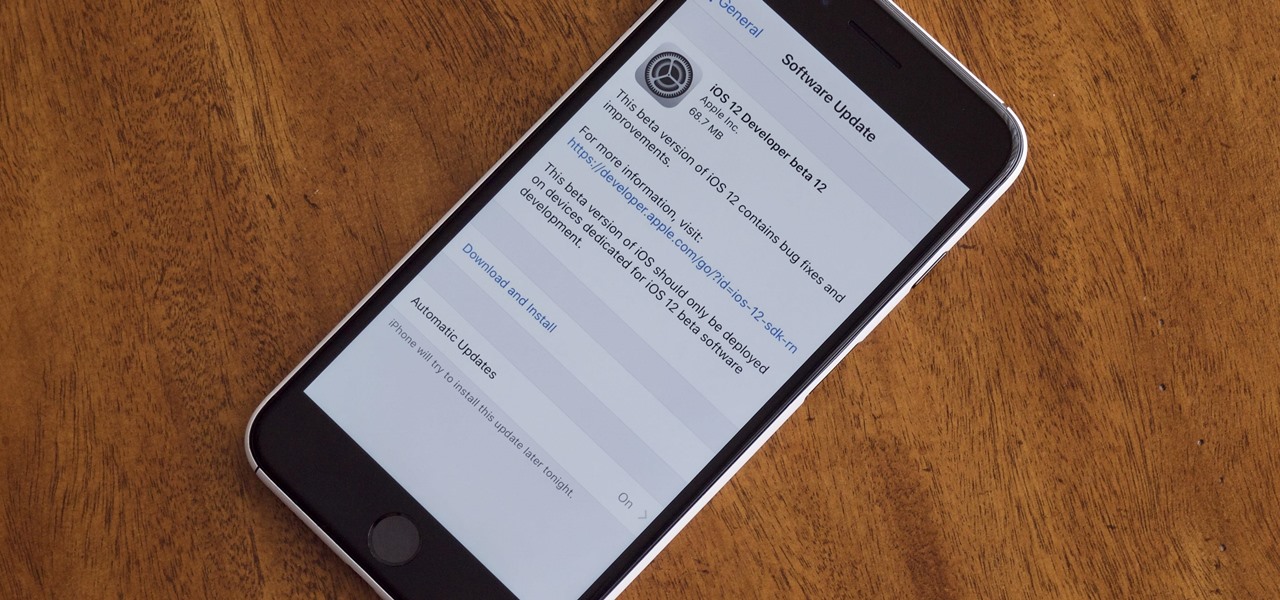
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

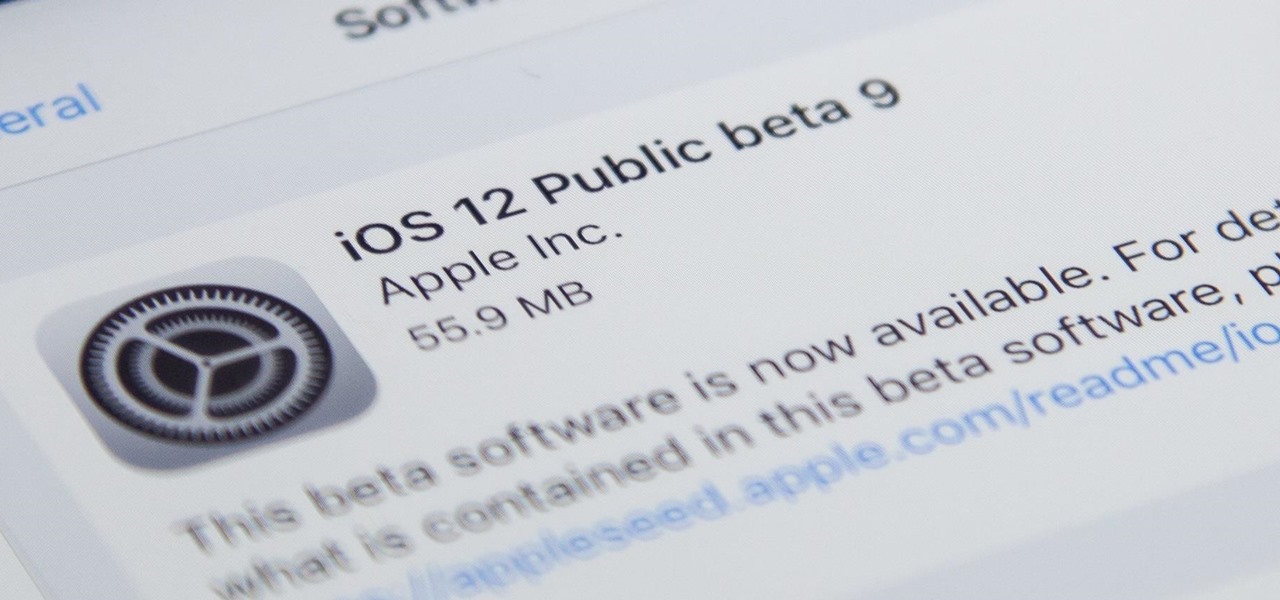
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.

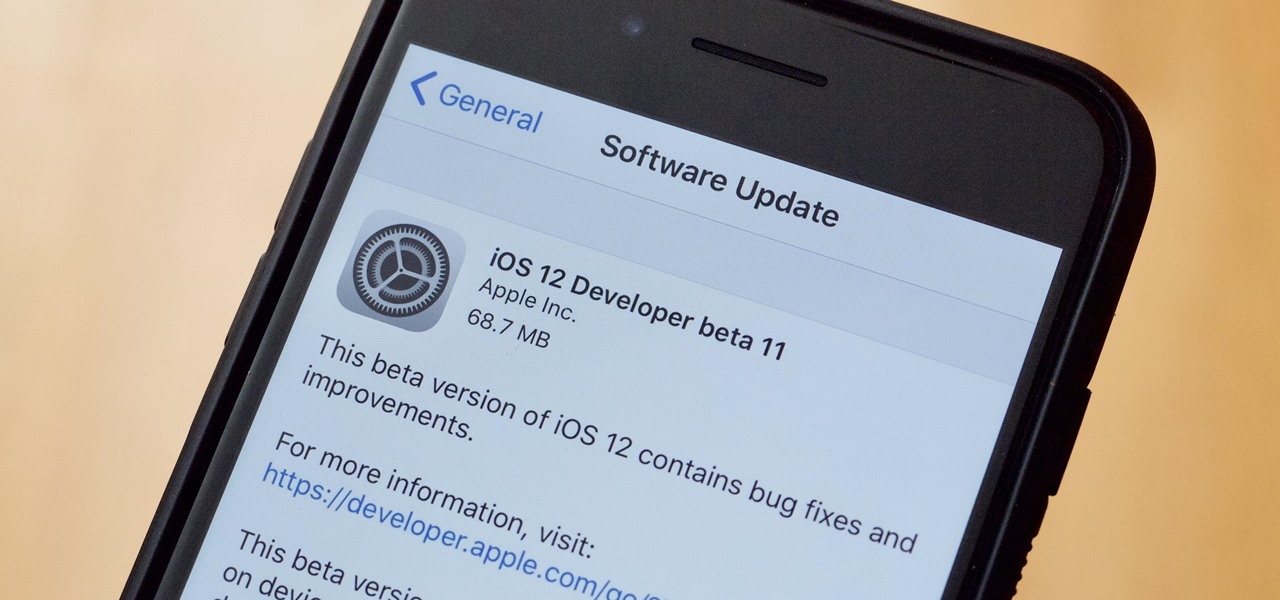
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.