The Microsoft HoloLens mixes the digital world with the physical one, allowing you to coexist with holograms of your choosing. But those worlds won't fully blend until we can experience it all together and create for each other. Vuforia could make that possible in the near future.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

With most augmented and mixed reality devices, you wear a purchased headset and use it alone, in a place of your choice—but not this one. Ben Sax decided to reinvent the binoculars to create a mixed reality experience that anyone can walk up to and try for free. He calls it the Perceptoscope.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.
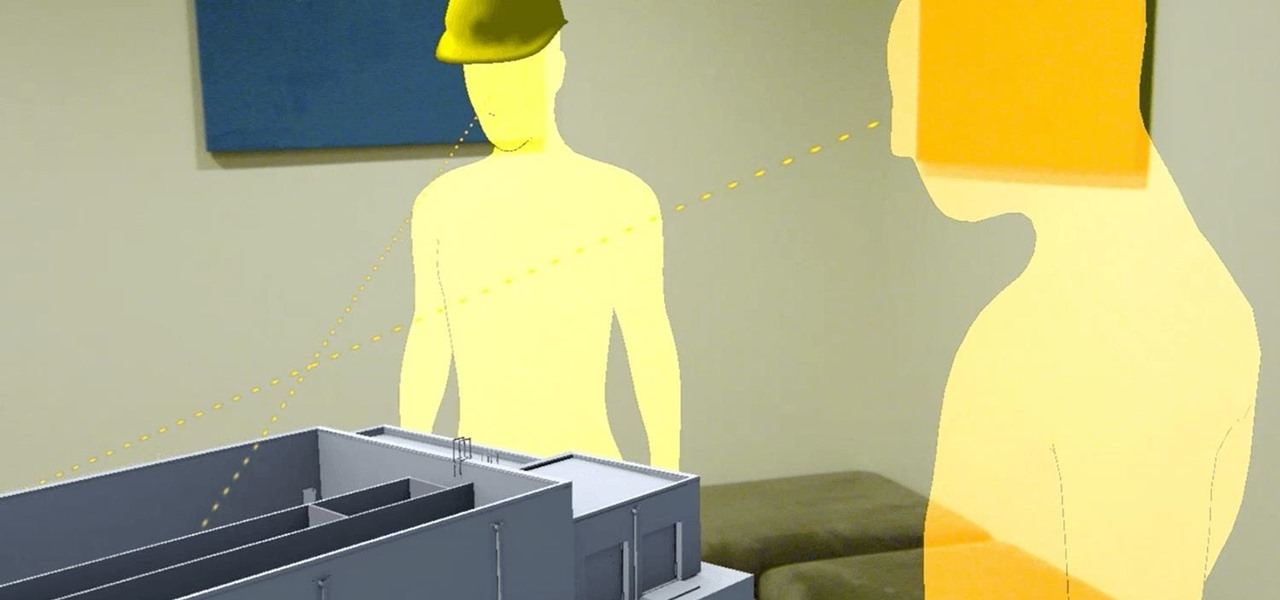
With developers already figuring out how to use the HoloLens for home improvement tasks, it's no surprise that the device has greater applications in construction. Tech blog Digital Trends points out that holograms are a natural evolution of the blueprint, and several other aspects of construction work.

Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

With the DOJ attempting to rip Apple a new one and an Apple attorney firing back, the President offered his opinion on the recent encryption debacle between the FBI and Apple at SXSW, amidst some talk about the direction of today's tech industry.

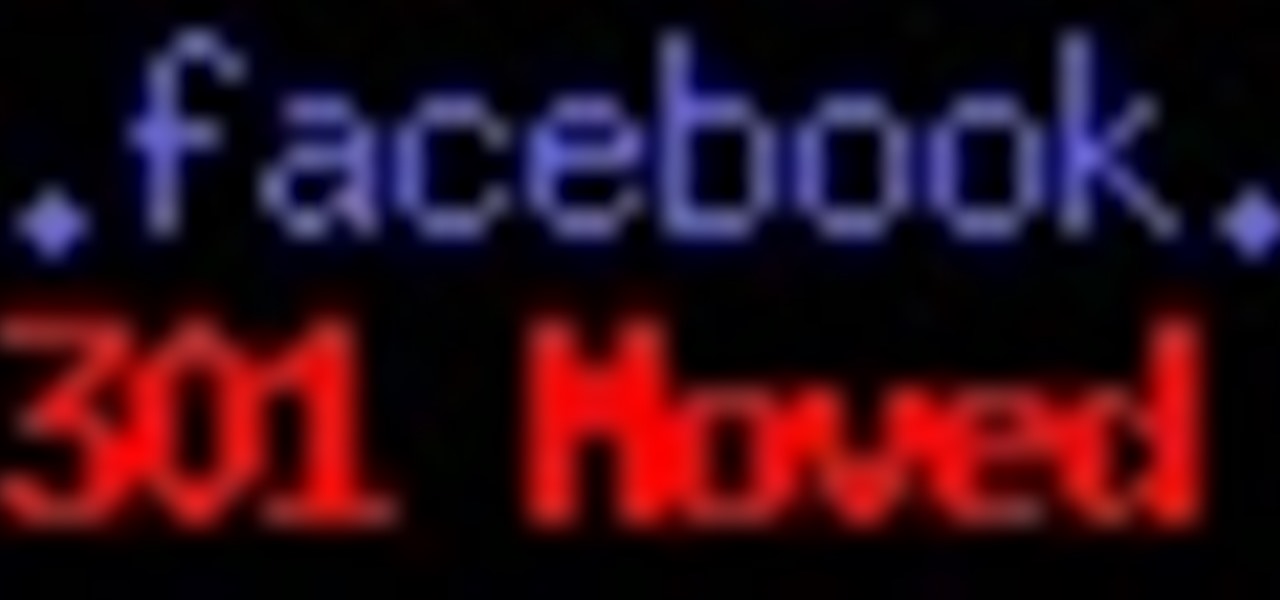
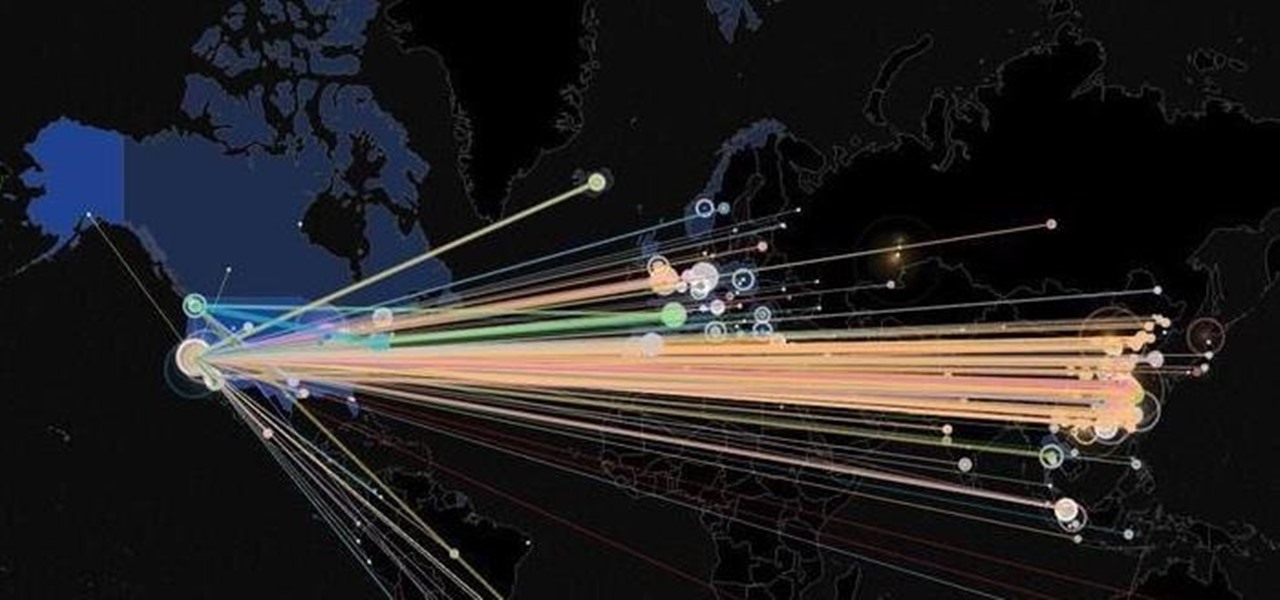
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

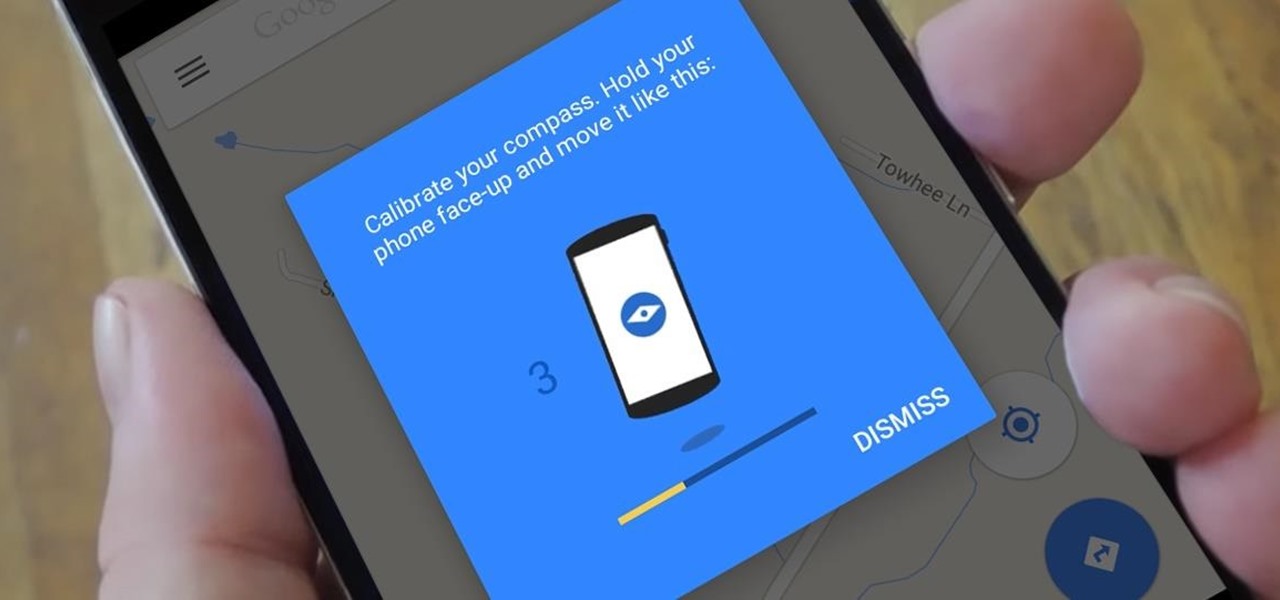
A lot of users with newer Android devices, particularly the Nexus 6P, have been complaining about issues with their device's compass. I've experienced the issue a few times myself—when you open Google Maps and try to get directions somewhere, you're prompted to calibrate your compass before you can proceed.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Although I am a loyal premium Spotify subscriber, I still regularly use Pandora in hopes of stumbling across new artists and songs. If I'm fortunate enough to come across something I enjoy, it's easy to use the Like feature in Pandora to locate the song later.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

As many of you may have heard, Apple's new iOS 9 is "rootless", which supposedly would make jailbreaking much more difficult. However, it has been shown to be possible. ih8sn0w posted a youtube video of his jailbroken iphone running iOS 9 and even gave some hints about it in the video description section. However, he also stated that he will NOT be releasing it to the public. So it would be quite the feat and adventure to take his hints and comments and use that to figure out how to jailbreak...

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Living in Southern California means I don't really have a need to check the weather all that often. But every now and then, I'm caught off guard by a particularly chilly or hot day—no one wants to be the only person walking around with a T-shirt and sandals on a rainy, 50-degree day.

Upon getting the new Samsung Galaxy S6 Edge here at the office, there are countless things we wanted to do before actually diving in and using the device. One of those things is removing all of the unnecessary pre-installed applications we never asked for.

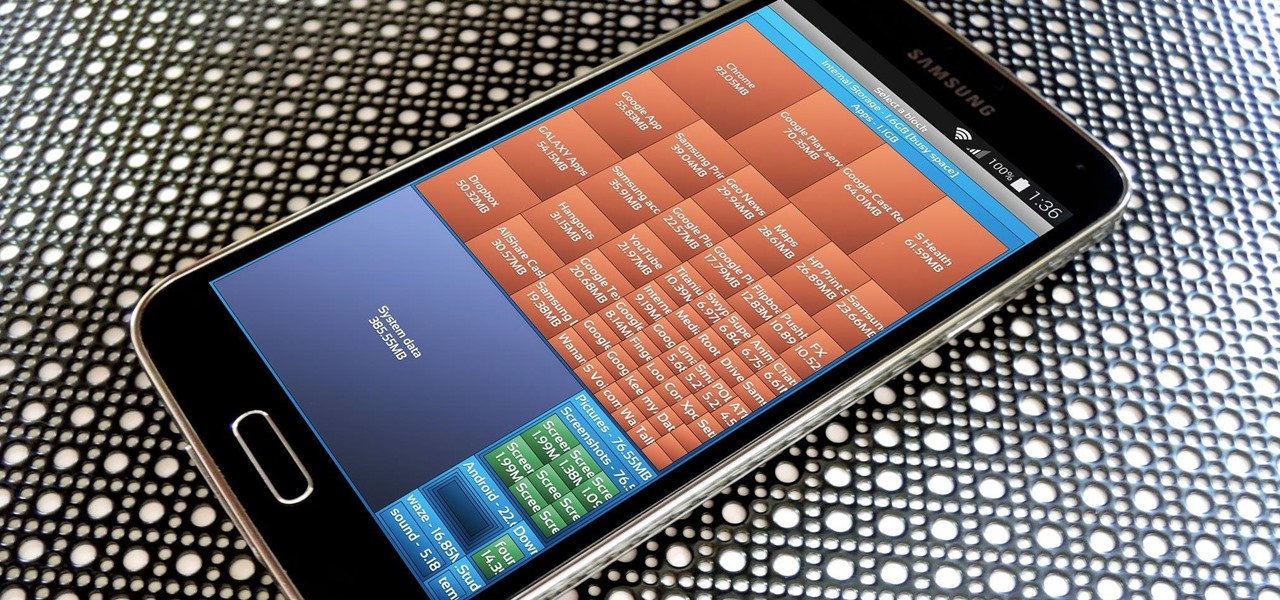
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

Before heading out on a hike, or any excursion for that matter, it would be wise to take a map with you just in case you get lost while on your quest.

In a long-awaited move, the popular messaging platform WhatsApp has finally made its official web debut. Desktop and laptop owners will be happy to know that they can now message their favorite contacts directly from their computers, without the need to install additional apps.

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

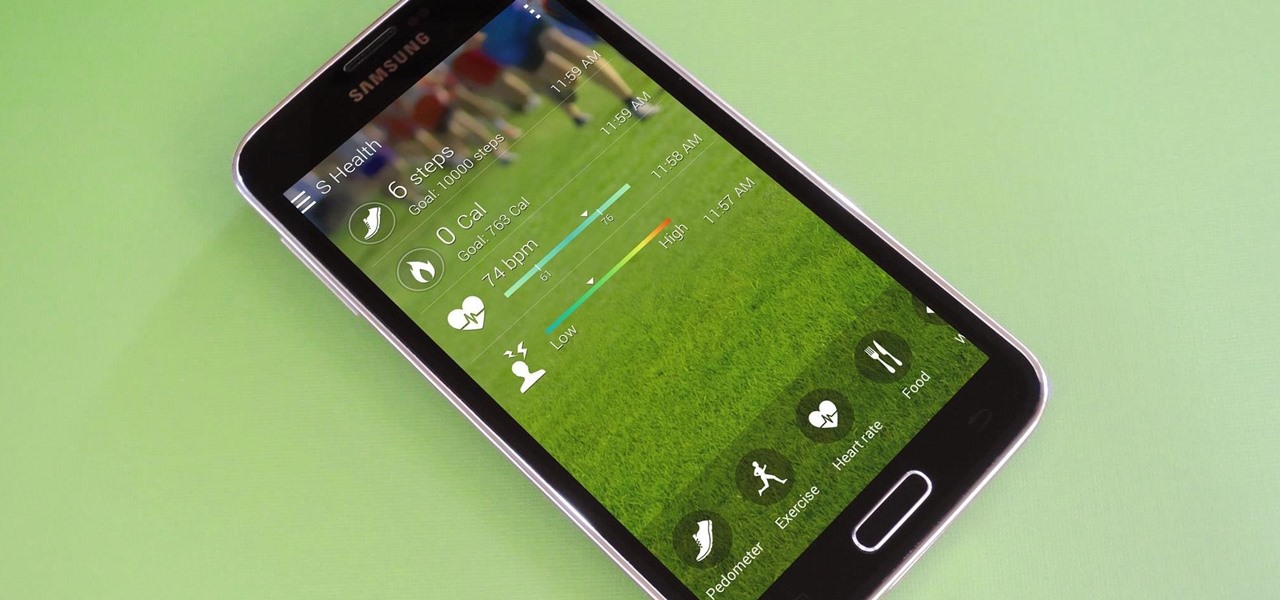
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

During initial reviews of the Nexus 6, the "double tap to wake" feature was something originally slated to be present on the device, since Motorola built it and it's been a key feature of the Moto X. However, the feature was scrapped for Ambient Display, which wakes up the screen when the device is picked up or a notification arrives. So while having both could be seen as overkill, it doesn't mean we shouldn't have the option.

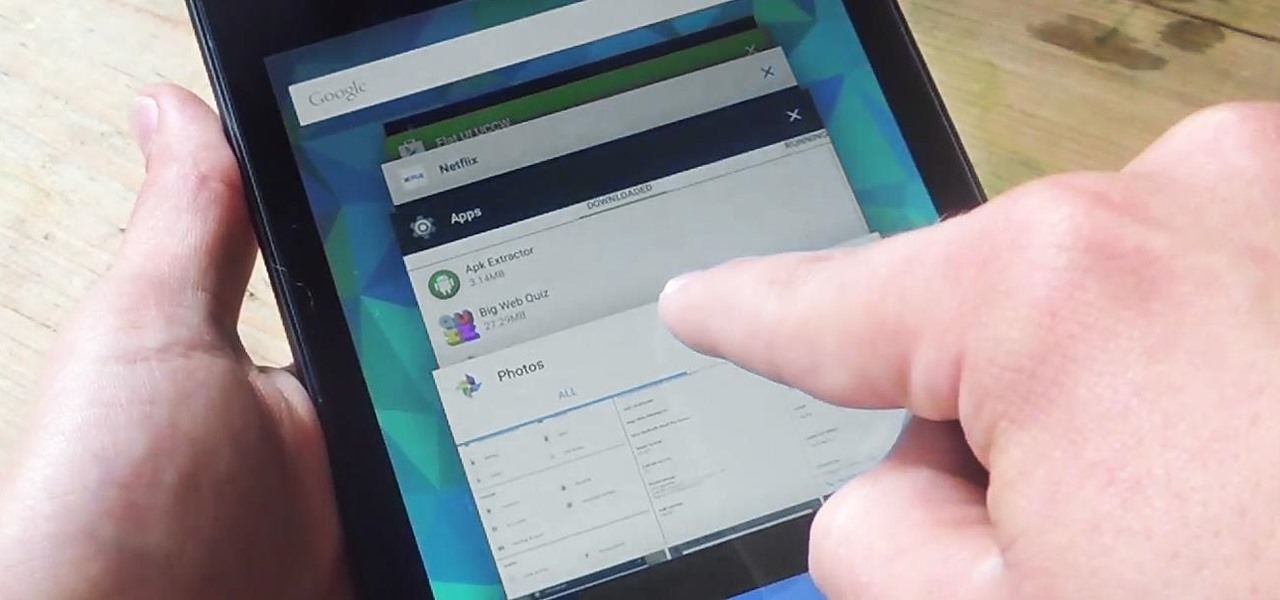
On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data.

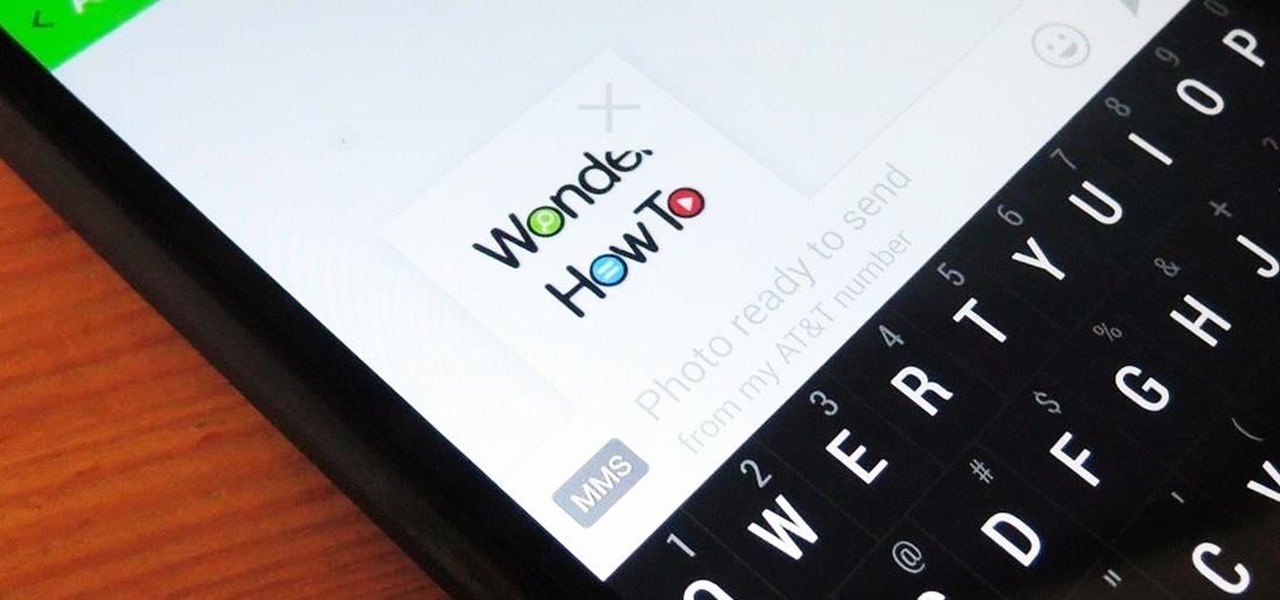
Whenever a picture is sent via MMS, a certain amount of compression needs to be done in order for a carrier's network to send it. That compression is meant to ease strain on the network, but in the end it leads to heavy downsizing and increased graininess in pictures.

While it can be argued that Google Chrome is generally a better browser, iPhone users tend to remain loyal to Safari. But one feature that gives Chrome the upper hand is its ability to recognize the language on any given page and offer you an option to translate it to your native language.

I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

Don't hit that button yet! I know that everyone is eager to update to iOS 8 as soon as humanly possible, but when it comes to enabling iCloud Drive, you need to wait.

Trying to remember if it's "beer before liquor or liquor before beer" can be too much of a hassle, especially if you've already have had a few too many. While it would be great if one rhyme could determine the amount of pain you will feel the next morning, we must accept that we all react differently to alcohol and that's that.

There is a question that has haunted man since the dawn of time: What if you could combine your tablet and your smartphone? Historians around the world have documented wars on the subject, and philosophers and kings who dared ask the question went down in the annals of history.

If you ever wanted to communicate with friends without having to deal with those pesky essentials like words and phrases, have no fear, Emoj.li is here!

Over the past decade, touch screens have changed the way we interact with our electronic devices. Gone are the days of clicking and pecking at keyboards, with these gestures replaced by swipes, taps, and long-presses on most of our newer devices. From the early years spent swapping out vaccuum tubes and reading light indicators, human interaction with computers has been constantly evolving. Can Qeexo's FingerSense usher in the next era in manual input?