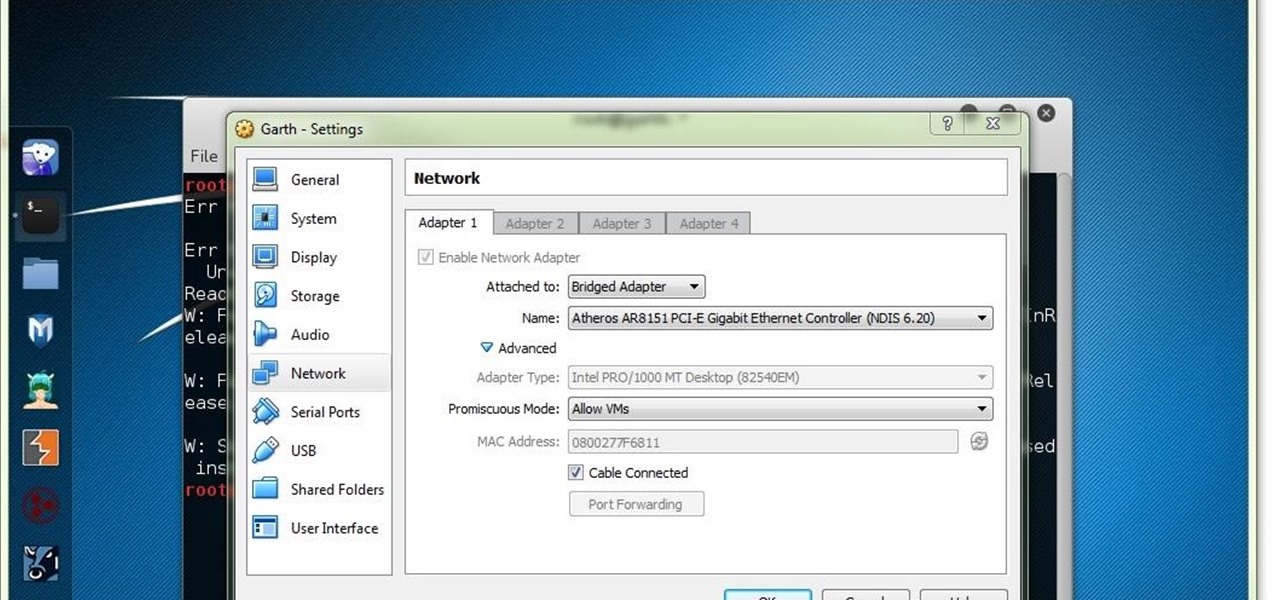
In this clip, you'll learn how to use the Entity Framework and RIA Services to migrate data from an SQL database to a Silverlight DataGrid (data grid). Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look. Move data from an SQL da...

Most of us swipe on Tinder while on the go. With all the pictures, Tinder on Android and iOS uses a decent amount of data. If you know the pain of Tinder triggering overage fees, limit the data-hungry app. There's a little trick you can use to help keep your swiping up and your mobile bill down.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

While we're waiting for Google to sort out the mess over suspended Google+ accounts, it's a good reminder that you have the option to download much of your Google+ data with Google Takeout. Google Takeout, created by an internal Google engineering team marketed as the Data Liberation Front, is a free service that provides a handy and easy way to download data from your Google+ stream, your contacts and circles, and other information in a zip file.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

I use my iPhone's personal hotspot all the time. Whether I need a connection on the train, in a coffee shop with no Wi-Fi, or when my friends don't have service, my personal hotspot is a lifesaver. But all that data comes from somewhere, of course, that somewhere being your cellular plan. Luckily, you can see how much data your hotspot has used, as well as who or what used more of it.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

Ever hear of Spokeo? No, it's not a city in Washington state. It's a website called Spokeo.com, and it marks the complete end of privacy on the internet. If your phone number and address has been posted in a phone book, it's on there. If you own a house, chances are there's a picture of it. If you have a Facebook profile, it's probably listed.

In this ASP.Net video tutorial, Chris Pels will show how to use the ObjectDataSource as the intermediate layer between data bound user interface elements and a custom data access class for a business object. Uses of the ObjectDataSource in the GUI Design mode and declaratively in the source view of an .aspx page are discussed. In addition, the considerations for design of the data access class and business object for use with the ObjectDataSource are covered. Use the ObjectDataSource for ASP....

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

Data restrictions suck, but Google wants to make it suck just a little less. Rolling out is the latest update to their mobile Chrome browser, Chrome 32.

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to measure dispersion with a TI-83 graphing calculator.

Most of you are familiar with using Ettercap for attacking systems, but what about using it to find attackers? This tutorial will cover using Ettercap to find people sniffing on your network. The plug-ins we will be using are search_promisc, arp_cop and scan_poisoner. Have fun detecting network sniffers. Detect hackers on your network with Ettercap.

I was looking around on this site and this article caught my eye. It was about hiding text in ADS or Alternate Data Streams. While this is nothing new in the tech world, it seems that more and more people are looking at ADS for one reason or another.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

This video shows you how to import frames from a DICOM file into Photoshop CS3 Extended, and manage import options. You also learn how to remove personal data, export the frames as JPEG files, and display time series data as an animation that can be exported as an AVI, MPEG, or FLV file. Open and edit DICOM files in Photoshop CS3 Extended.

Adobe, eBay, and iCloud have been hacked...now add Spotify to that list. The company has stated that on May 27th, they became aware of "some unauthorized access to [their] systems and internal company data" but that "only one Spotify user's data has been accessed and this did not include any password, financial or payment information."

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it could also contain all sorts of sensitive corporate data for work.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

About Today's topic Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it is a real pain.

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we've covered over time.

A few months ago, we showed you a pretty awesome light painting project that visually captured invisible Wi-Fi signals around town using a Wi-Fi detecting rod filled with 80 LEDs. With some long exposure photography, the results were pretty amazing. This project was inspired by those crazy Norwegians, but this build lets you do something even more amazing—capture pictures of colorful written text and drawn images, frozen in midair.

Since the release of Microsoft's Kinect, there's been no shortage of useful and fun hacks. In the past, we've seen the Kinect modded for things like x-ray vision, World of WarCraft gameplay, air guitar and 3D video. And now there's even a use for all of you MineCraft gamers!

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

Want to be able to print wirelessly without having to buy a pricey network printer? Now you can! All you need to do is follow these simple, quick, steps.

Set up your network storage system with the help from a kind of creepy blonde woman. Great tutorial though. Easy to follow. Set up a nas200 network storage system.

When downloading any application on an Android device, you will always be prompted by the following... Whether it's Angry Birds, Shazaam, or Chrome, every application will ask for permissions. If you try and deny these permissions, it won't install, leaving you with no other option but to accept. So what can you do?

This article relates to changing the settings in Adobe Flash so that you can improve your overall computer security and privacy. Changing these settings might have a negative performance impact on your computer - but it is worth while.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers: