
News: The Google+ API Has Finally Launched with Read-Only Public Data
Google+ launched their API for public data today. For now it provides read-only access to public data in the form of People & Activities. Here are some links to get you started:


Google+ launched their API for public data today. For now it provides read-only access to public data in the form of People & Activities. Here are some links to get you started:

You've seen the felt mouse, which made computer clicking comfortable and chic, now brace yourself for something a little more interactive—DataBot.
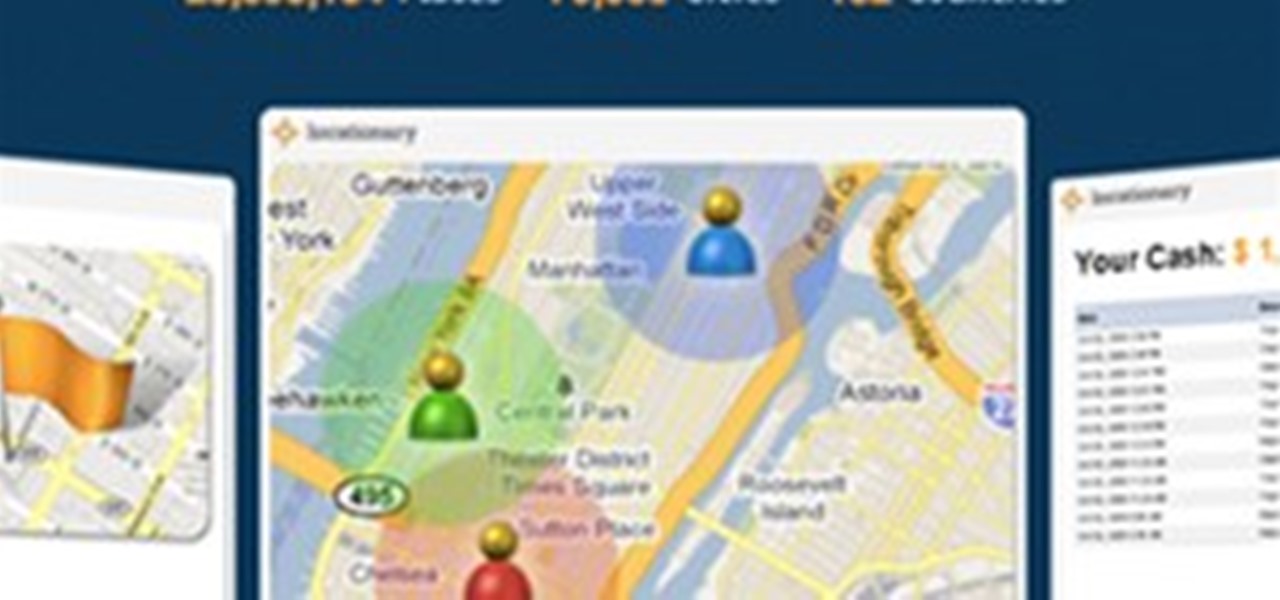
Watch the video to learn what it is all about. Locationary is a new system which rewards you for sharing your local knowledge.
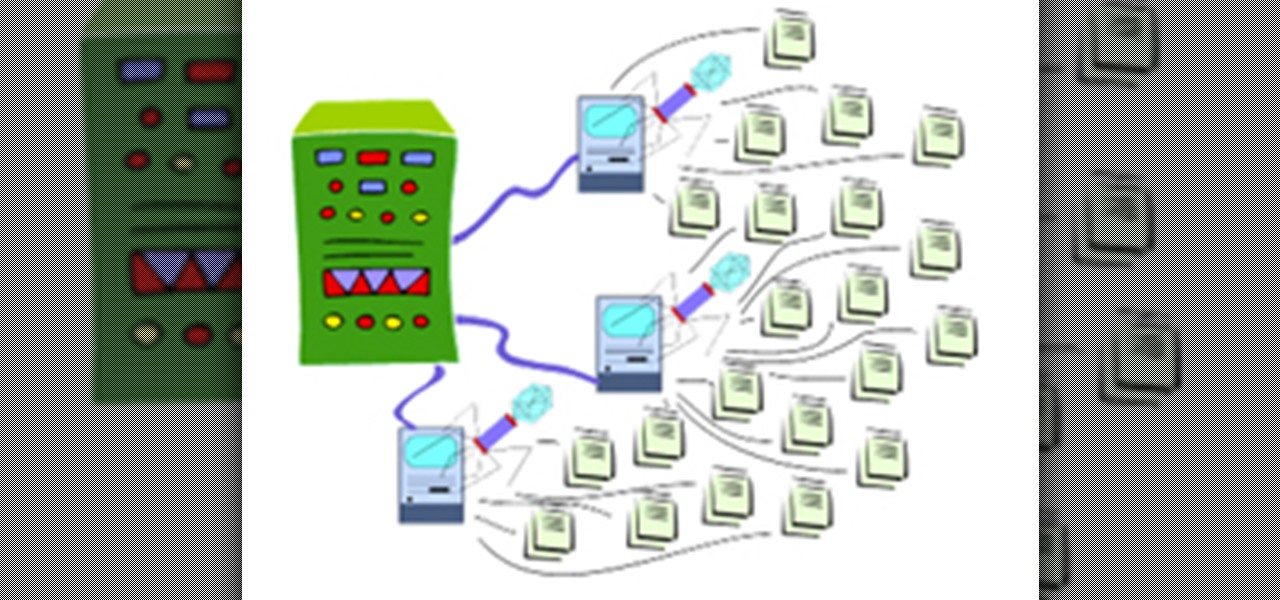
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.
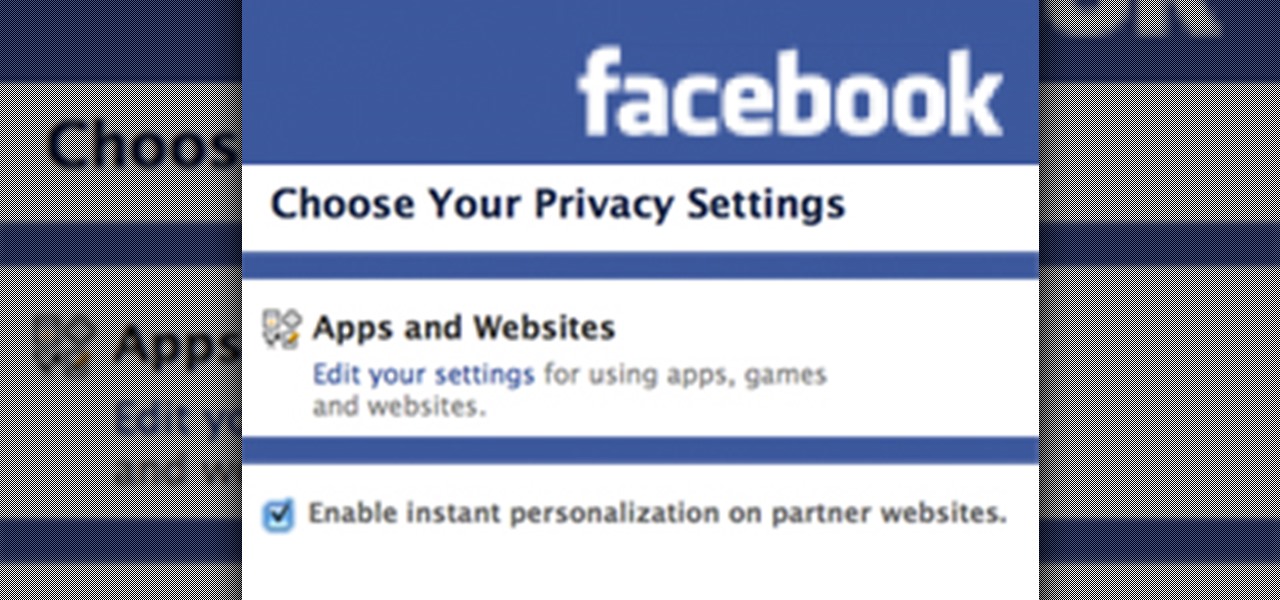
Instant Personalization. If you have a Facebook account, you've probably heard of it by now. If not, you need to educate yourself— and fast. Because they recently made some changes, affecting your privacy settings.
Technology: The Less You Know the Better?

Check with your ISP about alternatives to the Internet. The speed of your Internet connection is the most important variable in your download speed. If you have dial-up Internet access, consider upgrading to a Digital Subscriber Line (DSL) or cable connection. Even if you already have cable, your ISP could have faster cable service available.

This video demonstrates how to create a pivot table in Excel 2007. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to create a pivot table in Excel 2007, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to back up files with Time Machine, For Dummies.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to create histograms with a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to create a histogram with a TI-83 graphing calculator.

Jeb just announced a great new feature that will be added in the 1.2 update. This map format, titled "Anvil," will open Minecraft to so many more possibilities with the new update to mod compatibility.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog posts, music tracks, and the like. And then there are those who are very mobile with their devices. They commute to and from work on a regular basis with their iPhone or iPad. Some users may travel a lot on business, or...

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

How to send pop-up messages to friends on a local Windows NT network. Send pop-up messages to friends on a Windows network.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

Update: Based on comments from Adam Novak, this article has been updated to better reflect how the video memory range works. You can check out his working emulator (written in c) here.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

Meet Newstweek, a hidden device engineered to hack news items being read at public WiFi hotspots (cafes, libraries, airports, etc.). Both nefarious and tech-saavy, the ingenious mechanism wasn't fathered by a group of web hackers, but rather a pair of Berlin artists, Julian Oliver and Danja Vasiliev. The duo are interested in exploiting the "trustworthiness" of big media outlets in order to demonstrate the vulnerability of relying on just a few dominant networks.

Tetherd Cow Ahead posts an interesting science experiment. All you really need is a little bit of iron powder and a magnet, and you can unveil the info behind the magstripe on a credit card.

How to disable Wi-Fi SSID broadcast on an Apple AirPort in seven simple steps. Open your AirPort Admin Utility application. Find your network's name and double-click it or press the Configure button on the bottom right of the screen. Enter your password and click OK. The Configure "Apple AirPort Express" Base Station should open. Click on AirPort tab. Select the "Create a closed network" check box. Click OK on the dialogue box. Click the Update button on the lower right part of your screen. D...

Figuring out the Wi-Fi at a new location is challenging enough. Connecting to said Wi-Fi should be as easy as possible. Unless someone you know is already connected on their iPhone, you're probably used to the usual routine of heading to the Wi-Fi page in the Settings app to get yourself online. Luckily, there's now a much better way to do so.

General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them.

If you're an owner of a BlackBerry smartphone, chances are you're going to want to use BBM, which for all of you newbie BlackBerry owners, stands for BlackBerry Messenger. BBM is an instant messaging application developed solely for BlackBerry device owners.

InfoWorld has some expertise advice for the new Windows 7 operating system from Microsoft. Now that Microsoft has made the Windows 7 beta available for public download, many people are trying to figure out what's new and different. And many others not willing to risk their PCs by installing a beta OS are curious, too.
Truecrypt 5.0 adds many new features, most importantly Windows system partition encryption. To put it in slightly inaccurate layman's terms, this means encrypting your entire C: drive. Even if you already write your sensitive data to an encrypted space, files are sometimes squirreled away in unencrypted temp space or in the page file where they may be recovered. Using Truecrypt to encrypt your Windows XP system partition will help eliminate this problem.

In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like this are unlimited. For example, I modified the basic code so I would receive a text message letting me know every time someone rang my doorbell. The program could interface with Arduino through a serial port, and send d...

In this 3D software tutorial we cover a basic planar projection for UV mapping in modo 301. The video gives a brief explanation of the concept of UV data and a real world application of manipulating the resulting map. Learn how to work with UV projection in modo 301. UV project in modo 301.

Interested in creating your own dynamic, web-based applications using Microsoft Visual C#? How about an RSS reader application? This lesson shows the design and planning of the RSS reader application. For more information, as well as tips for being a more effective user of Microsoft Visual C#, take a look at all five videos.
If you're new to Microsoft Visual Basic 2005 Express Edition, and you're wondering how you can work with RSS feeds, then this video series is perfect. There are five videos in total, and they take you through every step needed to complete an RSS reader application using VB 2005.

This video demonstrates how to improve wireless network performance. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to improve wireless network performance, For Dummies.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.
Sergio Peralta Advisor: Jessica Davis

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.