With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...
From the article: Foursquare, one of the net’s hottest startups, got an unwanted message on June 20 from a white-hat hacker: it was leaking user data on a massive scale in plain violation of its privacy policy.

Jeremy Wood has turned the normally mundane task of lawn mowing into an art process. For the past nine years, Wood kept his mother's yard perfectly manicured, tracking every single motorized lawnmower ride with a GPS, and then converting the data into "maps".

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.
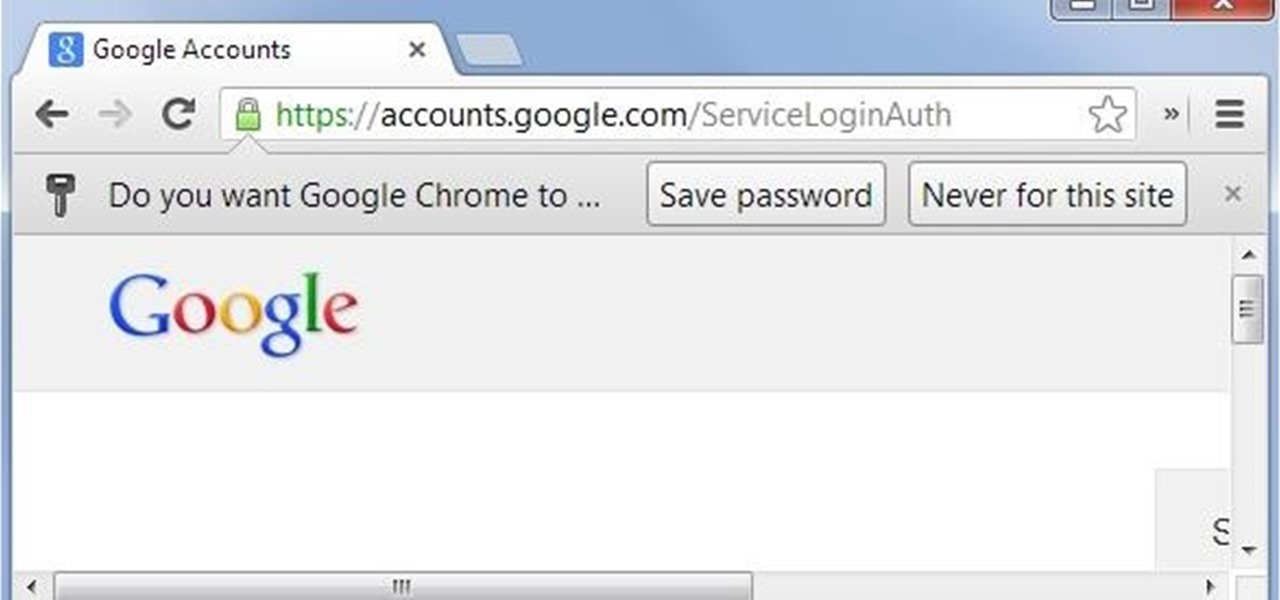
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

If you've recently noticed that you're missing Quick Settings toggles on on your Samsung Galaxy S6 or S6 Edge—specifically ones for Mobile data, Private mode, and Mobile hotspot—you aren't alone.

Wiretaps, which have increased almost tenfold since data was first reported in 1969, are only the tip of the surveillance iceberg. In 2011 federal and state courts approved a total of 2,732 wiretaps; but government agencies made over 1.3m requests for data to mobile-phone companies. That figure includes wiretaps and pen/traps, but it also includes requests for stored text messages, device locations and tower dumps, which reveal the presence of everyone—suspects and not—within range of a parti...

Jeremy at GamerTell shows us how to connect our X-Box 360 to the internet VIA Windows Vista and a Laptop Computer that is already connected to a wireless network. First we have to connect your laptop to your X-Box 360 using an Ethernet cable. Now we will turn on the Xbox 360. Make sure you are on the correct TV Input or channel. Now go to your laptop and Click on the start button on your laptop and find control panel. Once your in control panel select Network and Internet. Now we will select ...

You never know when you may lose your BlackBerry and expose all your personal information to whoever finds it. That's okay, protect private data on your mobile PDA by setting a password. Now you don't have to worry about strangers stealing your secrets anymore. Set a password for your BlackBerry Bold.

This Adobe CS4 tutorial shows you how to use the dynamic linking features available in the Creative Suite. This tutorial will specifically cover how to work with Dynamic Link in After Effects, Premiere Pro and Encore. See how to exchange data between these Adobe CS4 programs without rendering and exporting intermediate files. Use Dynamic Link in Adobe Creative Suite 4 (CS4).

SQL Server Reporting Services allows you to design and deploy nicely formatted and interactive reports representative of your data. Suitable for print or online distribution, these reports and it allows you to get professional results very quickly. This video demonstrates how to set up Reporting Services and the Business Intelligence Development Studio to build reports using the wizards and design. Use SQL Server Reporting Services.

Full-Text search allows you to save large portions of text – even Microsoft Word documents, or other file formats – into your database and perform complex queries based on this textual data while expecting great performance. This lesson demonstrates how to set up Full-Text search paying particular attention to the nuances of setting it up within SQL Server Express. Enable full-text search in an SQL database.

Learn how to create more advanced subroutines or blocks in the Lego Mindstorms NXT programming environment that will use data hubs and other functions to perform complex tasks. Create advanced blocks in the Lego Mindstorms NXT.

This video shows you how to use the new measurement features in Photoshop CS3 Extended. You learn how to set a measurement scale, save it as a preset, measure items, manage the measurement log, and export measurement data to a spreadsheet program. Check out this video created by Ashley Manning Still now! Use measurement features in Photoshop CS3 Extended.

Have you ever worked with Photoshop and Fireworks at the same time? This video shows you how to import files from Photoshop into Fireworks. It also goes over maintaining layer hierarchy, XMP data, layer styles, and blending modes. Check out this cool video created by Tom Green now! Import Photoshop files into Fireworks CS3.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Welcome to Compute & Conquer! This article may seem a little basic. We all have an idea of what a computer is but the fundamentals are necessary. Without knowing how something works, how can we determine a problem and find a solution when something goes awry? Way too often, I find myself helping someone with a very "easy to fix" problem on their computer. A problem which could have either been avoided or fixed had they had the basic knowledge of how to use a computer. Even worse, I've seen to...
; Assembler test for DCPU ; by Markus Persson

The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games.

How to use trendlines in Excell 2007 In this tutorial I will show you how to use trendlines in microsoft excell 2007. Trendlines can only be used for certain types of charts.

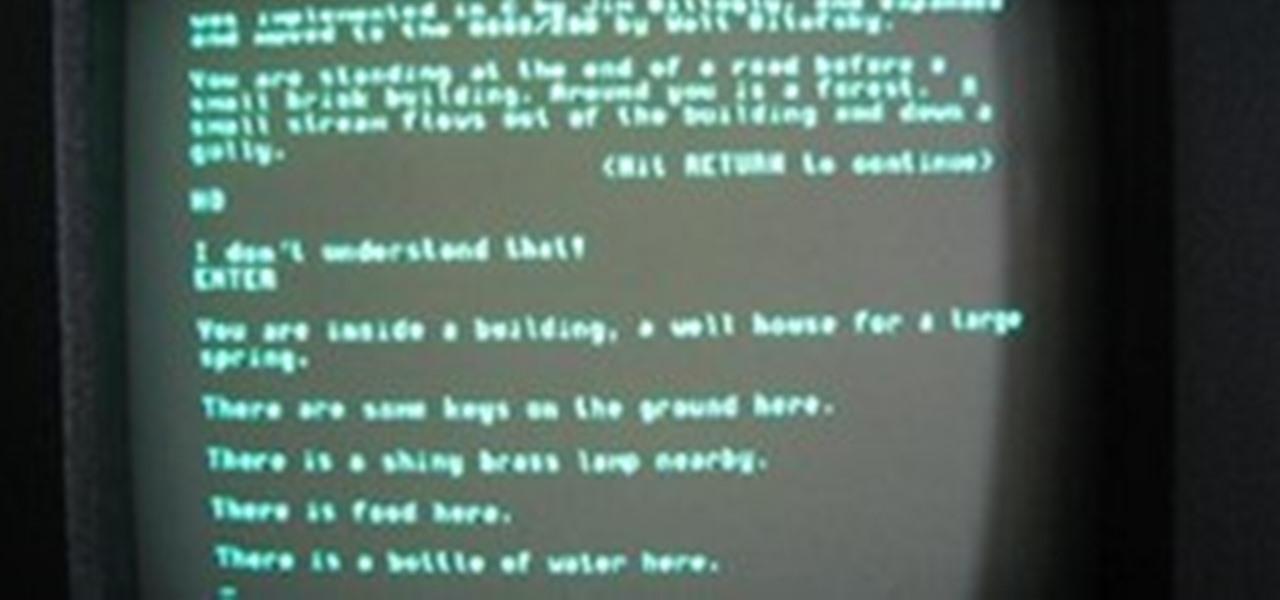
Adventure gamers would love to know what was the first adventure game. Well, it was a 1970s computer game titled "Colossal Cave Adventure", also known as "Adventure". Designed by Will Crowther, the game was in FORTRAN and initially had 700 lines of code and data, which was later expanded to 3,000 lines of code and more than 1000 lines of data.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.

Understandably, the tragedy in Japan has substantially risen the level of worldwide radiation-related hysteria. So much so, as an alternative to stampeding health food stores for iodine tablets, crafty individuals and organizations are hacking together personal radiation detectors. Rather than relying on the government, the creation and modification of handheld Geiger counters provides a self-sufficient solution to today's questions regarding radiation. Profiled below, three admirable organiz...

Written by JD Coverly of WonderHowTo World, LoadSave:We've spent the last week with Sprint's new phone, the HTC Evo 4G. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple has unveiled the new version of their phone this week and thankfully it's debatable as to which phone is better. The iPhone has better battery life and a more robust App store, but it suffers from a smaller screen, smaller camera resolution, no HDMI out, face talk only on wi-fi networks, and ...

My father recently suffered a stroke. Now in Neuro Rehab at Cedars Sinai, he is enduring daily physical therapy, recreational therapy and occupational therapy sessions to help improve his balance, mobility and fine motor skills. I was initially worried about how I could incorporate his current PT regime in his daily life after he's discharged. That was until I saw the devices he used in the PT gym. Despite their "medical device" designations, the high tech stuff is remarkably similar to what ...

Verizon Wireless advertises that their highest data plan caps at 10GB, which unfortunately isn't enough for a lot of users (especially if you're fond of tethering your phone). Go over their limit, and they'll slap you with seriously unwelcome charges—$15 per 1GB over. It's funny then that a Computer World writer discovered that Verizon actually does offer plans over 10GB, they just aren't too eager to advertise them.

You store everything on your computer's hard drive… precious family photos, your favorite music and video files, valuable financial information, and let's not forget about all that porn (just kidding). You can't back up your data when it crashes, so don’t wait another day to protect your hard-earned hard drive data.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to set up a WiFi network on a mac, For Dummies.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

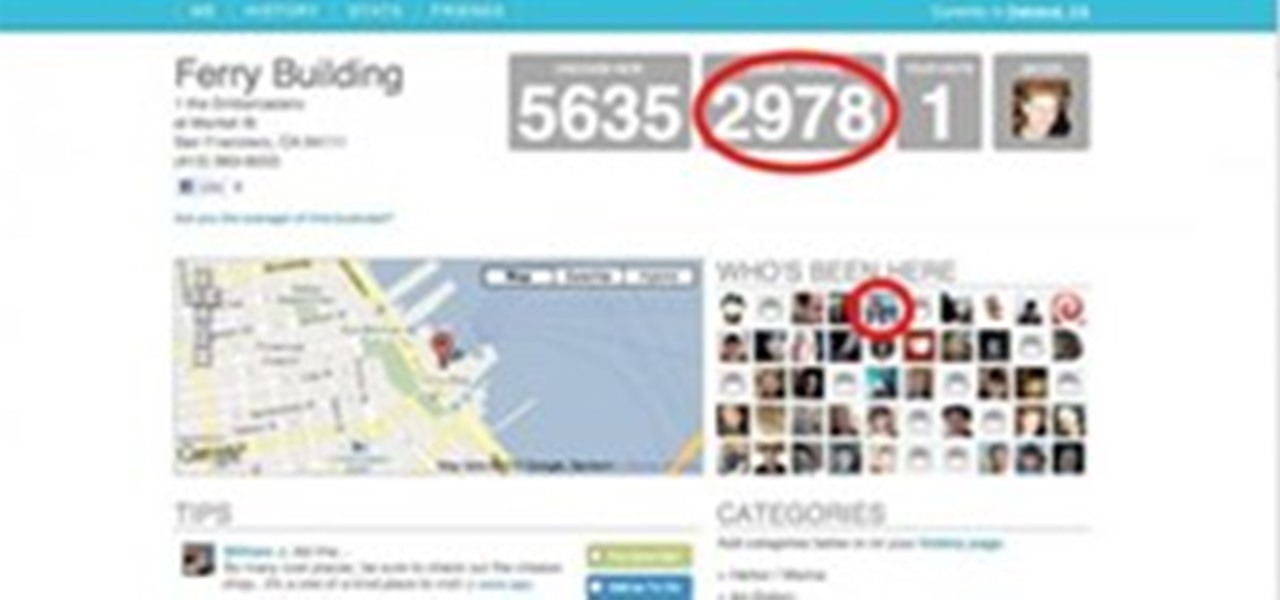
+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

In this video tutorial, viewers learn how to set and encrypt the wireless password using WEP Apple Airport. Begin by opening the Apple Airport utility program. Then find the network's name and double-click on it. The Configure "Apple Airport Express" opens, click on the Airport tab. Then click on the Wireless Security button. Now click on the Wireless Security drop-down menu and select 128-bit. Click on the Set WEP Password button, type in the password and verify it. Finish by clicking on Upd...

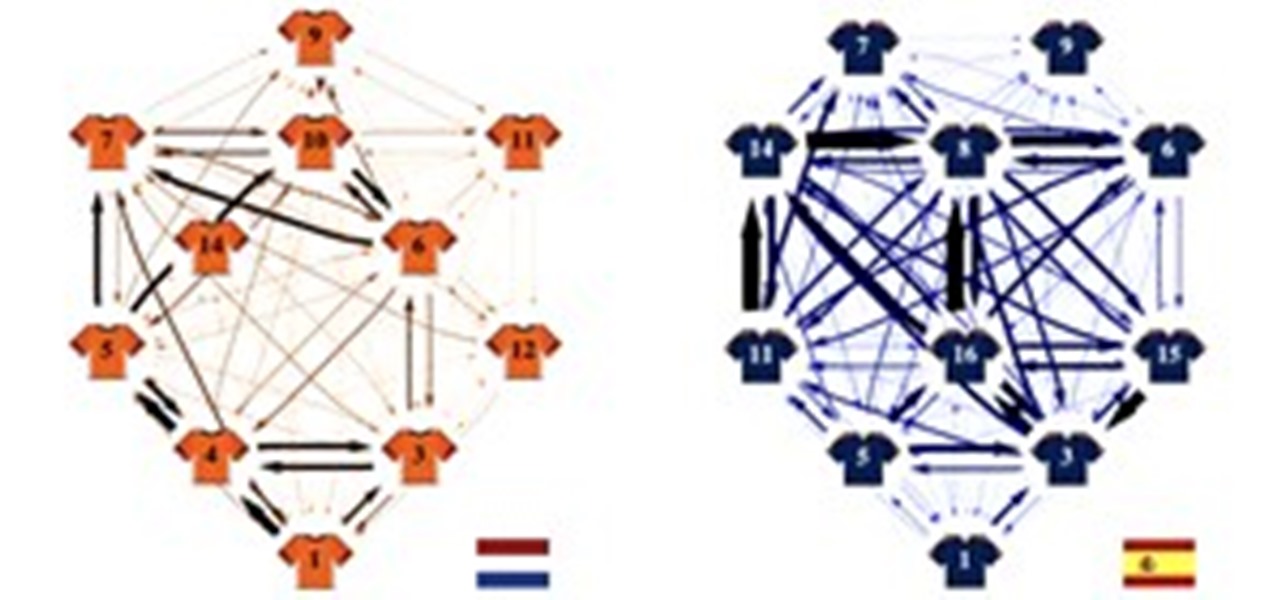
If you're a believer in the power of logic, may as well skip the game tomorrow. Two math professors at the University of London have supposedly determined who will win the World Cup, and have displayed their findings as a sophisticated infographic:

Spent the weekend with Sprint's new phone, the HTC Evo G4. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple will be announcing the new version of their phone this week. If it's comparable to leaked phone shown over at Gizmodo, then to say which phone is better is debatable. The iphone might have a better battery life but the Evo has an unlimited data plan, unlike AT&T's new tier pricing structure.

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...
The House of Representatives has approved an amendment to the draconian National Defense Authorization Act (NDAA) that will limit the Department of Defense from using data collected by unmanned spy drones against Americans.
Police officers stopped people on New York City’s streets more than 200,000 times during the first three months of 2012, putting the Bloomberg administration on course to shatter a record set last year for the highest annual tally of street stops.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.
This week, researchers from Symantec shared information on the recent discovery of a new variant of the Zeus Trojan. This new variant of the popular and ever-changing banking Trojan makes use of P2P communication exclusively, making the botnet have no single point of failure and ensuring it can be kept alive and gathering data that the cybercriminal can profit from. In other words, this new variant requires no central Command-and-Control server to control the bots.

This video showcases a number of artists and designers who rely on open source programming languages like Open Frameworks, Processing and Pure data to create digital art. If you want to help turn this into 3 documentaries about open source, art, programming and innovation, contribute to their goal of $27k on Indiegogo.

Lady Gaga and Polaroid's upcoming Grey Label Camera Glasses can record video and snap pictures, but who really wants to show the world what they're up too on those mini LCD screens? It's nothing more than a fancy gimmick between a pop star and a failing company. Isn't the intention of camera glasses to capture things around you as they are? Drawing attention to yourself with clunky video-displaying eyewear kind of defeats the purpose, but that's why they're "fashion" glasses and not practical...