Do you'll know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?
Do you know a program software to detect unmask caller's for cellphones for abroad network's carriers, as i often travel abroad to Hong Kong ,Japan and Malaysia and i went switch to those networks via changing the States sim card to the local domestic sim card i often received unmasked/private number's callers calling myself but i have not way of finding out who is it?

Samuel Granados has discovered an efficient way to display geographical data in 3D physical reality. Use LEGOs.

HoloDecon , is a Interfered Perception Dispositive , constructed by the modification of celular phones , used to activate alternate perceptive channels , in a trajectory that talks to the nature of impermanent as an experience of conditioned phenomenon to the understanding of substance ,

Parody of the social network using Pres Obama.

There are many reasons to clear your cache. Privacy, protection, and performance are but a few reasons. This video shows you how to clear all of your cache except for your form data and saved passwords. This will teach you how to remove Temporary Internet Files, Cookies, and History. Clear cache in Internet Explorer 7.

You might know the feeling: the sinking stomach that informs you something terrible has happened. You click on your trash bin. Nothing is there. Your hard drive has been wiped clean.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

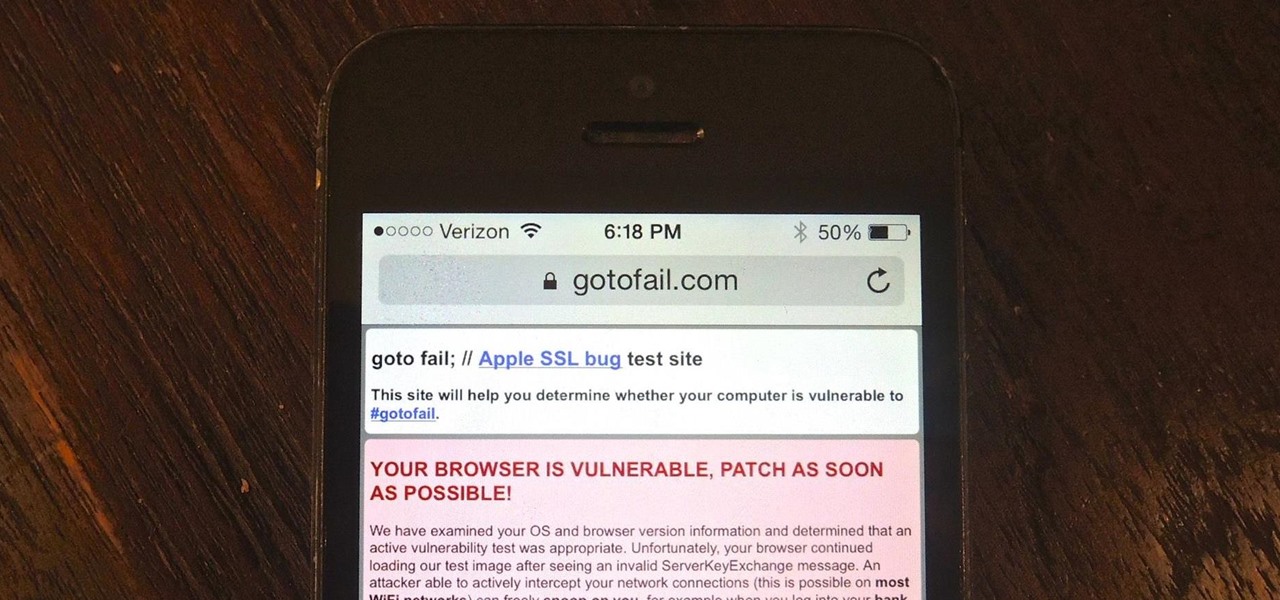
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.

Finally, what appears to be a fair and worthy competitor to the iPhone: Google's Nexus One. Unfortunately, not much competition concerning the price- runs exactly the same amount as the iPhone.

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

Just acquired a new Sony PlayStation 3? Well, in order to start using the many extra online features of the PS3, you will need to set up your internet connection. This interactive video walkthrough takes you step-by-step through the process of connecting your version of the PlayStation 3 to the web.

Here is my investigation on Teen Stress Base on FTA. QR/ER on Stress

What if your fridge knew your food and expiration dates? What if your fridge could tell you which ingredients are missing and where you can get them the cheapest?

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

This infographic from SingleGrain aptly and succinctly describes the primary differences between Facebook and Google+. Which social network will reign supreme?

The whole world is connected to the Internet, which means bank for advertising companies who track your every move online. Most of the content you see on the web is free, and that's because of advertisements. If there were no ads, none of us would be addicted to the Internet because none of us would be able to afford it.

It's been a long time coming, but Microsoft has finally released a software development kit (SDK) for the Kinect on Windows 7 PCs. The word "hacking" is no longer needed, thanks to the free beta download available at Microsoft Research that allows anyone with a Windows computer and some coding knowledge to take advantage of the Kinect's motion-sensing capabilities.

This clip presents a look at one of the basics of Houdini: Polygons - point, vertex and primitive data, smoothing and faceting, subdivision, removing inline points, orienting polygons and making polygons planar. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instruction...

April NPD Video Game Sales Every month around the second thursday the sales chart for video games and consoles are released for the previous month. They are released by the NPD group, the main company tracking video games sales in the US. Here are the top twenty games in the month of april (courtesy of Gamasutra http://www.gamasutra.com/php-bin/news_index.php?story=28566 ):

Interested in creating your own dynamic, web-based applications using Microsoft Visual Basic 2005 Express Edition? In this two-part installment from the Absolute Beginner's Series of VB/ASP.NET form control video tutorials, you'll learn about the basics of using the List View control, which provides a graphical representation of data elements. For more information, as well as tips for being a smarter user of Microsoft Visual Basic, take a look! Use the List View control in Visual Basic 2005 -...

How to Make the Internet Faster in Windows 7 Go to Control Panel.

This video demonstrates how to create pivot chart in Excel 2007. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to create pivot chart in Excel 2007, For Dummies.

This video demonstrates how to create a graph or chart in Excel 2007. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to create a graph or chart in Excel 2007, For Dummies.

This 3D software tutorial shows you how to use images to affect models in 3D Studio Max. Using the displacement modifier in 3ds Max we are able to use either image data or procedural texture maps to drive geometry in a design model. Modeling with images is a great way to model quickly and with details hard to get using other methods. See how in this 3ds Max tutorial. Model with images in 3ds Max.

In this software tutorial, Corey demonstrates how easy it is to create 3D graphs using Illustrator. You don't have to run to Microsoft Excel anymore to get good looking charts and graphs. OK, well you do if you need super accurate data fast, but not if you just need some 3D graph effects! Create 3D graphs in Illustrator instead with the help of this tutorial. Create 3D graph effects in Illustrator CS3.

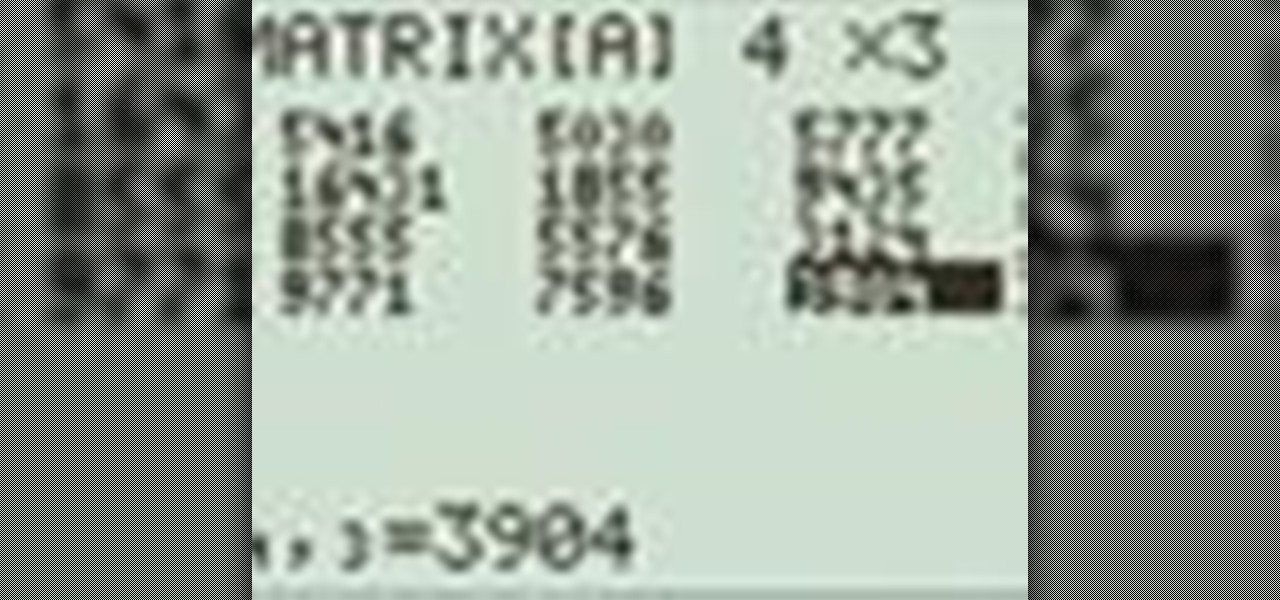
Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to clear a list with a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to create boxplots with a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to calculate deviation with a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to determine a regression equation with a TI-83 graphic calculator. That's not all...

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to perform a chi-square test on a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to use ANOVA with a TI-83 graphing calculator. What is ANOVA? One-way Analysis of Variance.

In this video, you'll find instructions on how to use the Ettercap plug-in dns_spoof to set up DNS spoofing on a local area network. This Ettercap plug-in is ony one potential way to pull of DNS spoofing, and only works if the attacker is on the same subnet. To get started DNS spoofing with Ettercap, press play! Use DNS spoofing in Ettercap.

In this article, I'll show you how to make a simple Gmail notifier. Python can do various things in terms of notifications; sending commands to an Arduino unit, playing sounds, opening windows, etc. The code below simply plays some music, but the possibilities of notification methods are endless. If you aren't familiar with python, there are many sites with tutorials like this one, or this one.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.
I've struggled for a long time trying to set up a virtual network between my KVM virtual machines. I tried several forums and tutorials on the web, but still on my system it just wouldn't work. I eventually got it owrking, so I've decided to make some notes of my own. Hopefully it will be helpful to you as a reader as well.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

Wall studs are both critical for maintaining the structure of your home and supporting items of weight and function on the interior walls (e.g. cabinets, shelves, plasma TVs, etc.). With wall studs playing such a critical role, consistently being able to find them is important. The problem with finding them is that drywall and wallboard isn't exactly see-through.