QR codes are like smart little cubes of data. To unlock this data, you will need a QR reader. These are annoying because you typically have to download a third-party app, and some of these apps are shady. Luckily your Samsung Galaxy running One UI has a hidden QR scanner built right in.

While most smartphones have the ability to receive FM signals via a tuner, mobile carriers prevent users from taking advantage of this hardware — probably in an effort to get their customers to spend more money on data.

2017 has been a good year for Apple thus far. The new Kantar data is out, showing that from November 2016 to January 2017, the iPhone 7 has held steady as the top-selling phone in all the largest markets.
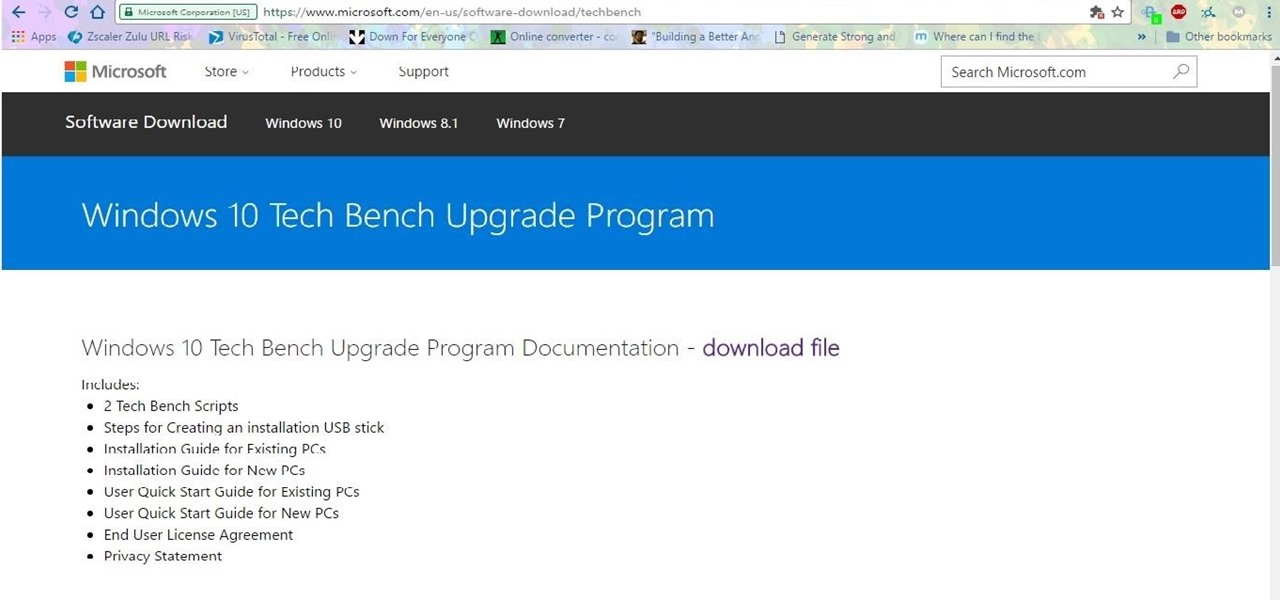
If you want to have windows .iso files for various purpose like you want to have windows 7 in virtualbox, then you need an .iso file. There are many methods of creating an .iso from installed windows. But what if microsoft provided all of them( I mean 7,8 &10) free of cost. The only requirement is that you own a product key for the respective Windows edition (and that's also is not a painful task to get).

If you've noticed moments when there's a drop in quality when listening to a song on Apple Music, it's not just you. When on a cellular connection, the streaming quality drops when compared to that of a Wi-Fi connection.

Who uses Yahoo! Image Search, you ask? Scientists apparently.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Interested in creating your own dynamic, web-based applications using Visual Basic 2005 Express? In this installment from the Absolute Beginner's Series of Visual Basic/ASP.NET video tutorials, how you can connect your applications to databases. You will learn how to enable your application to view and edit data stored. This will allow you to exercise the skills shown in the earlier videos. For more information, as well as tips for being a smarter user of Microsoft Visual Basic, take a look! ...

Interested in creating your own dynamic, web-based applications using Microsoft Visual Web Developer? In this installment from the Absolute Beginner's Series of video SQL tutorials, SQL Server beginners will learn about tables and definitions of data types, properties, keys, etc. in this second video. Find out how table rows, columns, and fields interrelate and whether columns can be empty. For more information, as well as tips for being a more effective user of Microsoft Visual Web Developer...

Interested in creating your own dynamic, web-based applications using Visual C# 2005 Express Edition? In this installment from the Absolute Beginner's Series of Visual C#/ASP.NET form control video tutorials, you'll learn how to use the Tree View control which provides a hierarchical view of data. . For more information, as well as tips for being a smarter user of Microsoft Visual C#, take a look! Use Tree View in Microsoft Visual C# 2005 Express.

Interested in creating your own dynamic, web-based applications using Visual C#? In this installment from the Absolute Beginner's Series of Visual C#/ASP.NET video tutorials, you will learn how to use the List View control which provides a graphical representation of data elements. For more information, as well as tips for being a smarter user of Microsoft Visual C#, take a look! Use the List View control in Microsoft Visual C# 2005 - Part 1 of 2.

This tutorial will show how to use GPG and the FireGPG plug-in to encrypt and decrypt messages in Gmail. GPG is an open source implementation of OpenPGP (Pretty Good Privacy) , a public-key-encryption system. With public key encryption you don?t have to give away the secret key that decrypts data for people to be able to send you messages. All senders need is the public key which can only be used to encrypt, this way the secret key never has to be sent across unsecured channels. Encrypt Gmail...

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

How To Stop The Weirdness Lag, Pauses Etc...In FaceBook/ Zynga Games Via Flash! How-To Topics » Facebook, games, facebook games, online games, zynga

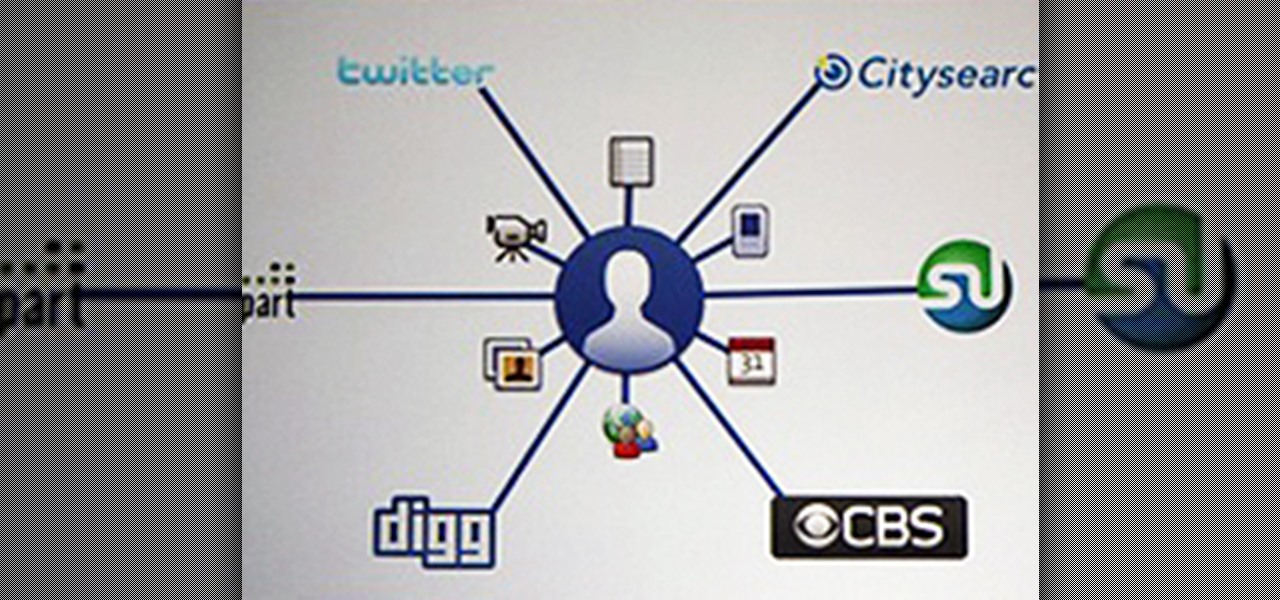
+Guy Kawasaki is someone you should definitely circle on Google+ if you want to keep up with the social media world. He's always got interesting links, and he posts multiple times a day (you may want to drop him into a noisy people circle). He created this great graphic to help you decide which social network to choose: Facebook, Twitter, or Google+.

The group social networking application Fridge has been purchased by Google, and two of its team members will be moving to Mountain View to work on the Google+ team. Fridge, in addition to being a group social sharing site, has photo and event sharing features. The event and calendar-sharing are popular requested features for Google+ users.

This video gives you tips on how to use social networks to find new job opportunities. ..

Two trailers with the exact length in time, their audio is swapped and synchro magic occurs. Here is the Social Network trailer visuals with the Let Me Go Audio, then the Let Me Go visuals with the Social Network audio.

Here is the amazingly original social network trailer Here is a parody of that trailer done for ping. Its amazing what a single track of music can do to create the feeling of a trailer.

Here is the official trailer for "The Social Network" which is David Fincher's film about FaceBook. The official website for this movie is http://500MillionFriends.com

Startup promises to catch 100% of network attacks - Techworld.com.

Ever found yourself not able to connect to a Wi-Fi network on your Android device that you know damn well was there? The worst part is that you know it's your device, because you can see everyone else around you on that network! WHAT GIVES?!? Well, maybe it has something to do with your phone’s Wi-Fi country code!

Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

The 68th Annual Golden Globe Awards take place this Sunday, January 16th, 2011 between the hours of 5 and 8 PM PST — that's 8 & 11 PM for those of you on the East Coast (and Somewhere in the Middle for those of you Somewhere in the Middle).

After years of false rumors and abandoned hopes, the day has finally come. Verizon Wireless is finally getting the Apple iPhone!

"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!
National Security Agency whistleblower William Binney reveals he believes domestic surveillance has become more expansive under President Obama than President George W. Bush. He estimates the NSA has assembled 20 trillion "transactions" — phone calls, emails and other forms of data — from Americans. This likely includes copies of almost all of the emails sent and received from most people living in the United States. Binney talks about Section 215 of the USA PATRIOT Act and challenges NSA Dir...

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

More than 100 missions targeted at Earth's moon have been launched by space explorers since the late-1950s. NASA landed a total of 12 men on the lunar surface, collecting more than 800 pounds of moon rocks and lunar soil samples. But still, the moon remains a mystery, especially its formation. NASA's new mission aims to find out exactly how the moon came to be with the Gravity Recovery and Interior Laboratory, or GRAIL, part of NASA's Discovery Program.

The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search.

Have you guys seen this yet? Ben Purdy used projection mapping to create a "real life" Minecraft block. If you don't know what projection mapping is, it works like this:

Although Google+ has solved many of our problems with social networking, it's not perfect, and we all wish they'd be a just a little bit faster with the improvements. In the meantime, you can stave off your hunger with useful Google Chrome extensions that improve upon Google+.

It's called a Quick Response code, but most know it simply as QR code, a matrix barcode dedicated to the world of smartphones. The information contained within the square black modules could be text, a URL, vCard, or some other kind of data. And even though mobile tagging has been around for eight years, it's just now spreading like wildfire across the globe, being incorporated into artistic portraits and wall art. And most recently... "social clothing".

Google recently unveiled the start of their new social network Google+, which is set to compete with Facebook and fix the awkward, broken aspects on online sharing they claim exist. It's currently only open to a limited number of Googlers during its "field trial," and if you weren't one of the lucky ones given an invitation, you can still sign up to be notified when Google+ is available in your area. You can also stay up to date on its Twitter page, GooglePlus.

Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.