Introduction to KVM KVM is a free and open-source Kernel-based Virtual Machine using the Linux kernel for virualization and is very similiar to a hypervisor like Xen or VMware's ESXi. It is based on Qemu, a processor emulator. Any virtual machine created on or working on KVM can work on Qemu also, but with a great reduction in speed.
Want to see which country or city uses Google the most? Try Google's new eye-stimulating tool, Search Globe.

Have you ever left your computer one all night? Maybe downloading something, or just out of habit? Well there is a way you can turn that unused CPU usage in to cold hard cash: Distributed Computing.

About two months ago, the massive Gawker Media hack was a wake up call for many web denizens on the importance of proper password security. Data analyzed by the Wall Street Journal revealed the three most popular passwords recovered from the hack were downright idiotic—123456, password, and 12345678. If past events weren't motivation enough for crafting a strong password, then maybe a racy 8-bit stripper is. Naked Password is a jQuery plugin by Platform45 that rewards you with an accelerating...

By John Timmer, Ars Technica How much information can the world transmit, process, and store? Estimating this sort of thing can be a nightmare, but the task can provide valuable information on trends that are changing our computing and broadcast infrastructure. So a pair of researchers have taken the job upon themselves and tracked the changes in 60 different analog and digital technologies, from newsprint to cellular data, for a period of over 20 years.

Ever wonder what you look like to someone else as you walk, talk? How it looks from above, behind, or to the side? Seeing yourself in a video flattens the experience into two dimensions, but this wireless camera rig experiment from Instructables member BigRedRocket brings it into the third dimension:

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.

What if everything in life was controlled by augmented reality? Keiichi Matsuda imagines: "The architecture of the contemporary city is no longer simply about the physical space of buildings and landscape, more and more it is about the synthetic spaces created by the digital information that we collect, consume and organise; an immersive interface may become as much part of the world we inhabit as the buildings around us.

100% functional LEGO ATM by Ronald McCrae. This bonafide brick bank performs the following functions:

Remember, in the Terminator movies, when Arnold's field of vision is superimposed with all sorts of data? Sci-fi writer Vernor Vinge also described electronic contact lenses, technology that "projects" information right before the eyes.

Don't worry, the robot apocalypse is not upon us...yet. Wired reports it may be closer than you think:

In this Dreamweaver 8 video tutorial you will learn how to display records by extracting info from a database. Learn how to create a data connection, create a query, work with recordset, display items, and use repeat regions. Note: To use this tutorial you need XAMPP and make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Display records in Dreamweaver 8.

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).

Common programming blunders can be your best friend when trying to craft your own exploits. If you spend a little time reading what some of these common blunders are, they can uncover potential attack vectors or just show you the weird ways in which computers can store and recall data or access system resources.

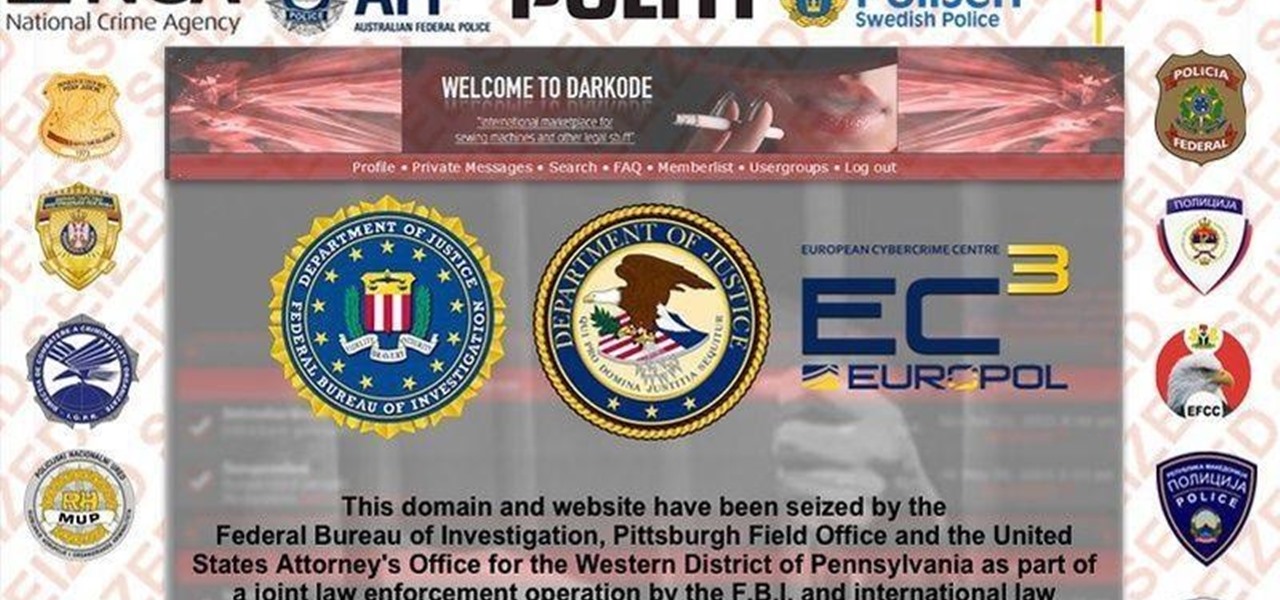
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

For the month of April, Android maintained it's edge over Apple's iOS platform, 52.5% versus 41.4%, with Blackberry, Microsoft, and Symbian rounding out the top five (2.5%, 3.3%, and 0.2%, respectively). Due to the vast number of OEMs that manufacture Android smartphones, Apple does have a solid lead in the device market, with a dominant 41.4% market share, with Samsung, LG, Motorola, and HTC rounding out the top five (27.7%, 6.5%, 6.3%, and 5.3%, respectively). The research, compiled by comS...

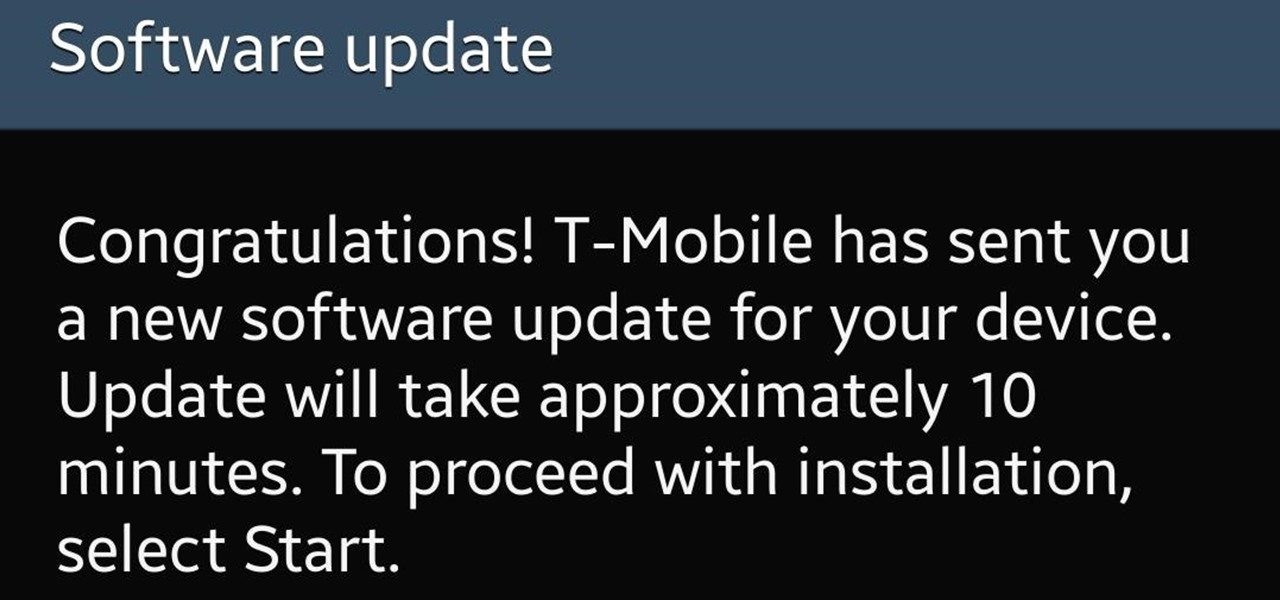
Starting today, T-Mobile has begun rolling out the Android 4.4.2 KitKat update to their Galaxy S4s. The roughly 390MB update brings the standard KitKat fare to your GS4, including:

All you Sprint customers still rocking the HTC EVO 4G LTE got some good news last night. Per Martin Fichter, a US Vice President at HTC, the once flagship Sprint device has been issued a final update, taking the device from Android 4.0 (Ice Cream Sandwich) to Android 4.3 (Jellybean). While not the latest Android version, this update also carries the upgrade to Sense 5. As the company stated in their Reddit AMA, HTC will continue to update their flagship devices to the latest Android versions ...
QR Code is a 2D barcode symbology capable of encoding all types of data, such as numeric, alphabetic characters, Kanji, binary, text, url etc. To build a qr code generator in Microsoft Visual Studio, we can use a qr code generator .NET DLL by Avapose.com and follow these steps:
Hello! I am working on merging two databases. The first has 1,500 contacts - just first name, last name, and company. The second has 5,000+, with first, last, company and email. I want to search the 5,000 email list, if the name appears on the 1500 list, I want to copy the email address from the 5,000 list.

As discussed in a previous tidbit, people are over-confident in their abilities for many reasons. Here's an example...

Two former high-ranking officials at the U.S. National Security Agency (NSA), a federal bureaucracy that collects data and intelligence on foreign communications for national security purposes, have come forward with allegations that the NSA actively monitors Americans as well. According to testimonies from both Thomas Drake, a former NSA senior official, and Kirk Wiebe, a former NSA senior analyst, the agency actively monitors and collects intelligence on every single American as part of a m...

This how-to is aimed at the uncynical, bright-eyed outsider who wants to become a television producer…the talented person who believes he or she has the ‘it’ to crack Hollywood. The ‘Sammy’ who just arrived in 90210.

In this video tutorial, viewers learn how to set and encrypt their Wi-Fi password using WPA in Apple Airport. Begin by opening the Airport Admin Utility application from the CD. Then locate your the name of your network and double-click it or press the Configure button at the bottom right of the screen. Now enter your password and click OK. The network should be opened now. Then click on the Airport tab and click on Wireless Security. In the pull-down menu, select WPA2 Personal. Then click on...

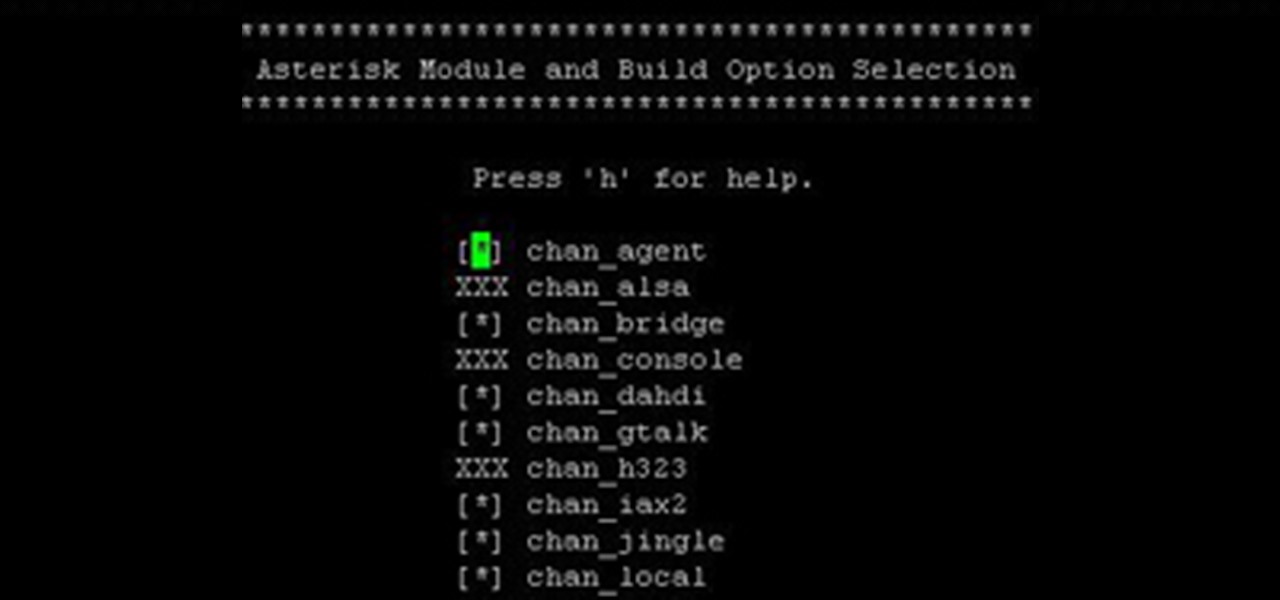
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Social networks like Facebook and Google+ are great for staying connected with family, friends and coworkers—even fans. But sharing and communicating with practically anyone in the digital realm has alienated us from most of the flesh-and-blood beings we see everyday—our neighbors. How well do you know your neighbors?

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

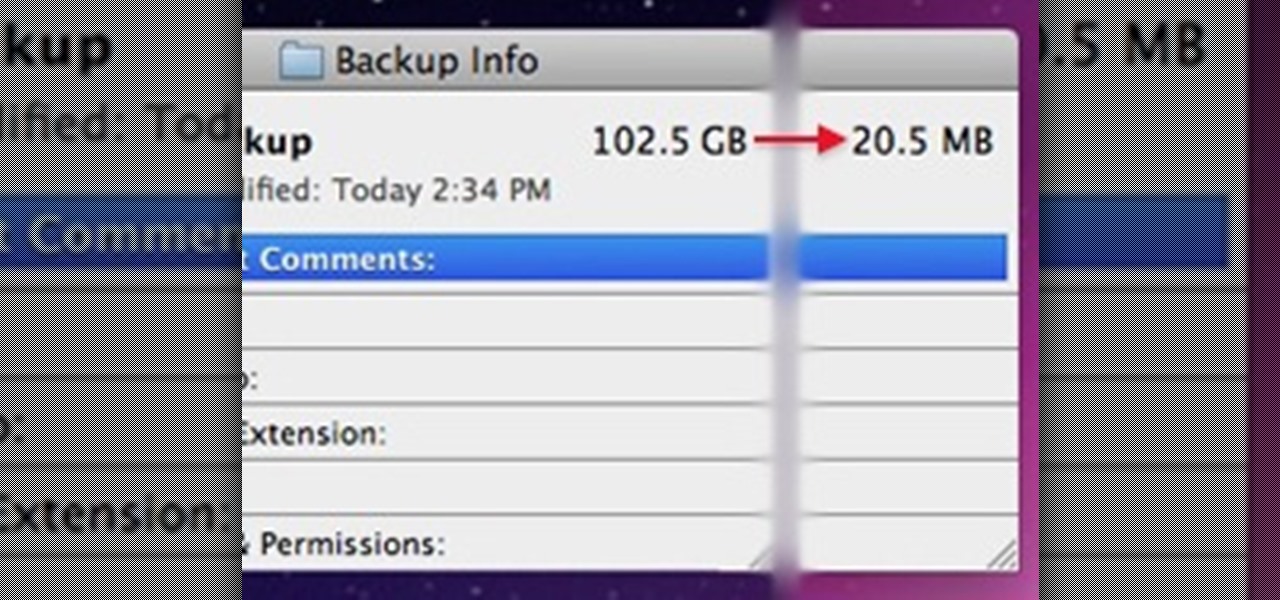
Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

It looks like Sony is adding some cool features to their upcoming portable game system called NGP (Next Generation Portable).

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

Firefox's hidden advanced menu gives you several ways to tweak the way it works under the hood. Here are a set of settings to change to get it to browse faster than ever.
HOW TO CAPTURE STREAMING MEDIA many websites stream songs and videos

How much do the producers of Lonely Girl make? How much do the producers of American Idol make? How much does COPS cost to make? I decided to share what I have learned for the CES audience in Vegas.

Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to add titles. Take a look. Add titles in Premiere Pro CS4.

A tutorial showing how to send messages in a Windows-based network without any programs. Send messages on a Windows network with the cmd prompt.