Adobe Premiere Pro CS4 software is the start-to-finish video production solution ideal for editors, filmmakers, cable and network broadcasters, event and corporate videographers, rich media creative professionals, and hobbyists. In this Adobe Premiere Pro CS4 video tutorial, you'll learn how to export audio to multimedia formats such as Blu-ray and YouTube as well as how to launch the Adobe Media Encoder and render vide. Export a project from Premiere Pro CS4.

The Interactive Lab Primer (ILP) has been developed as part of the Royal Society of Chemistry Teacher Fellowship Scheme, one of the themes of the Chemistry for Our Future program, and initiative which aims to secure a strong and sustainable future for the chemical sciences in higher education. The aim of the ILP is to address the diverse range of experience and skills students bring with them to a university by offering a resource to support their transition from school to the university chem...

Check out this interactive video tutorial from Verizon Wireless on the Samsung i730 mobile phone. If you have just purchases this sleek cell phone, here's your chance to learn everything you can possibly know about it.

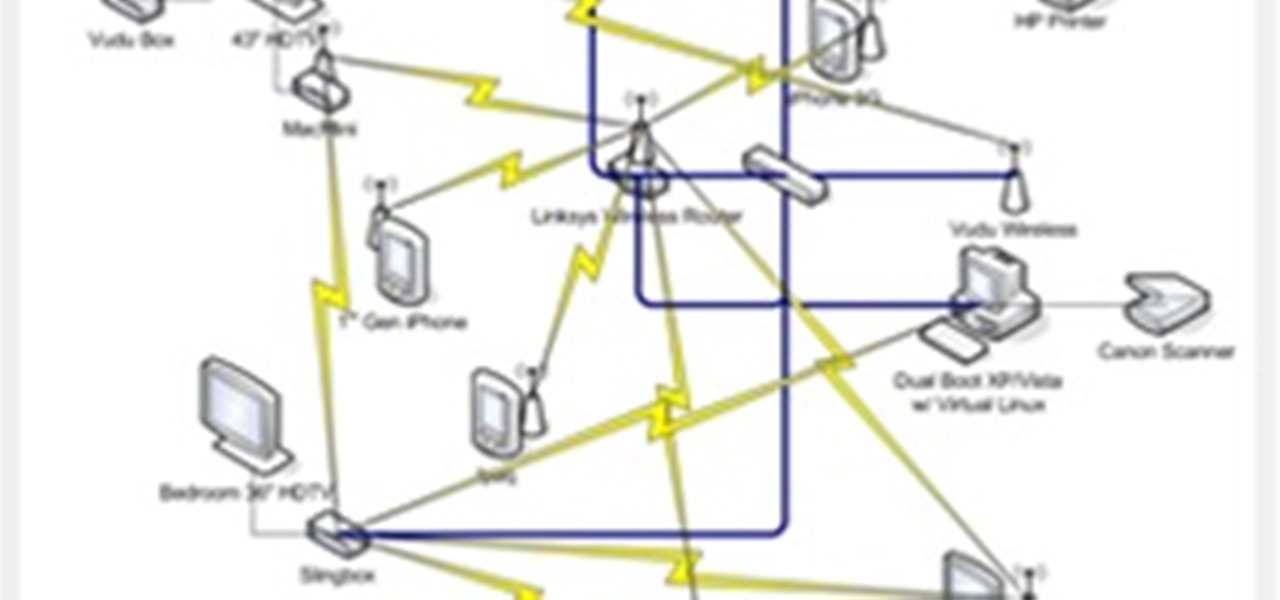
Having Internet connection problems? Is your PC's net connection dead? Learn some steps you can take to troubleshoot and fix the problem including dealing with cables, routers, ISPs, and Windows network settings. Reset your Internet connection.

In this video tutorial you will learn to export Photoshop layers into Flash. See how to export each Photoshop layer as a PNG file so you can import each file into Macromedia Flash 8. Portable Network Graphics (PNG) format is especially useful when you have transparencies in your files. Export Photoshop layers into Flash.

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Google+ is the most exciting new social network to come around this decade, and the only product with a chance of challenging the monopolies we know as Facebook and Twitter. As an Internet addict, I've joined every major social network there is - from Friendster (who?) to MySpace (so ugly) to LinkedIn (yawn) to Twitter (irritating) and Facebook (annoying to manage). Competition is delicious, especially between well-financed monopolies. Google+ really seems to have identified an Achille's heel...

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.

Introduction In the competitive world of today's video game scene, PC gamers are known to squeeze out the best possible visuals in their games. Every few months a new video card rolls out, and RAM is ever increasing; constant upgrading is the norm of staying ahead the curve. One of the most important things a PC gamer looks at is how many FPS (frames per second) he gets. It defines his gaming experience.

Very easy way to burn a movie or data disc.

Don't fret if your boss has sent you a long Excel list of employees and asked you to separate the first and last names. In this video tutorial you will learn a neat trick to take a person's name in one column and separate the data into two columns, one for first name and another for last name. Learn the quick process without retyping or cut/paste! Split data in mulitple columns quickly in Excel.

The iPhone 4 for Verizon is already old news, thanks to Sprint's unveiling of the Kyocera Echo smartphone last Monday.

This tutorial offers a look at using point clouds in shading, and the pcopen, pciterate, and pcimport nodes in VOPs. It also gives a further example of a POP network. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

This four-part tutorial series presents a look at how to combine traditional keyframe animation with DOPs simulation. This first part contains an overview of how DOPs differs from SOPs and how to examine DOPs data using the Details View. It then looks at the RBDKeyFrameActive node as a method for combining keyframe and simulation animation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself wi...

This is a tutorial on coding an iPhone App in XCode.
(CNN) -- Abu Yahya al-Libi, the No. 2 man in al Qaeda and a longtime public face of the terror network, has been killed by a U.S. drone strike in Pakistan, a U.S. official said Tuesday.
The Department of Homeland Security has been forced to release a list of keywords and phrases it uses to monitor social networking sites and online media for signs of terrorist or other threats against the U.S.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.
Backtrack 5 R2 was recently released and added over 40 new tools and updates to their old tools. Along with a new Linux 3.2.6 Kernel and better networking support.

http://www.seonorthamerica.com Learn how to sign up for and use Onlywire's automatic social network and social bookmarking submission service.

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

Google Reader is ostensibly just an RSS aggregator, a tool that lets you catch up on your favorite blogs. How could Google have anticipated that getting rid of its social features could have angered so many people who were actually using it as their default social network, and who enjoyed it precisely because it didn't function like Facebook or Google+?

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

G+Me is one of our favorite Chrome extensions here at Google+ Insider's Guide. We love it because it's one of the most comprehensive extensions out there. It attempts to address the "noisy streams" issue, with list mode, and collapsible posts and comments. The creator, +Huy Zing, is very responsive to feedback, and he's been quick to address any issues that arise, including privacy concerns. He's even created a G+Me (Paranoid Edition) extension, for the extra careful Google+ user. And if you ...

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

Shelfari is a cool free widget that allows users to install a virtual bookshelf with custom picks on most blogs and social networks (Blogger, Typepad, Wordpress.com and more). Appears to be owned by Amazon; check it out.

MAME/SNES/GENESIS/NES/+ Arcade style 2 player cabinet. Features

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

An original musical composition created by cutting together existing sounds from within David Fincher's films. There is NO outside audio, sound effects, or music. David Fincher is an Academy Award nominated director.

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

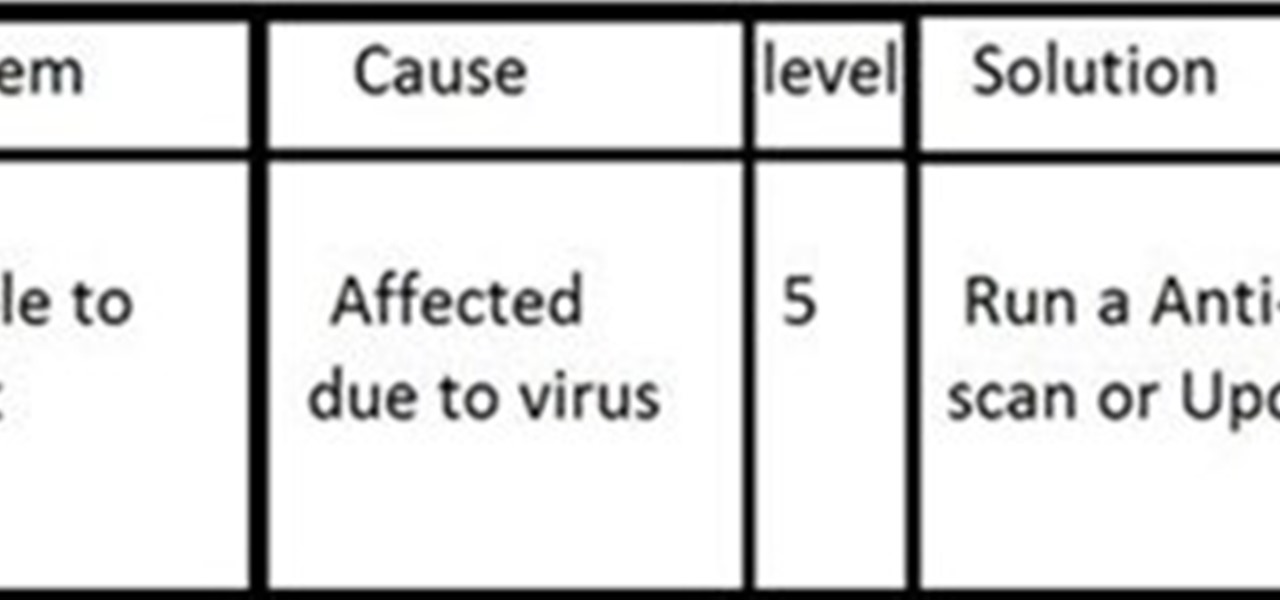
INTRODUCTION The everyday PC user doesn't think much about its PC and problems that can cause critical damage to their data or other stuffs stored on Hard drive and other electronic parts until the problem actually occurs. Once a failure happens, the repairs can be costly and very time-consuming and one also have to sacrifice their data stored on hard drives if the damage is more severe!