
News: What's all the fuss about World of Warcraft?
So what's all the fuss about World of Warcraft? I guess the first question would be 'is there a fuss?' and the simple answer is Yes there is, very much so.


So what's all the fuss about World of Warcraft? I guess the first question would be 'is there a fuss?' and the simple answer is Yes there is, very much so.

Big weekend with a lot of new releases: the social network, Waiting for Superman, some Woody Allen, a little Buried but Mike wants you to watch something else instead. A hint: it's a mockumentary about hosers and it's called FUBAR 2.

Part 1. Part 2.
The Creators Project is a new network dedicated to the celebration of creativity and culture across media, and around the world.

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

Zuck Farmville? Rather than end its strained relationship with Facebook, social-gaming outfit Zynga has opted to formalize it. This morning, the company, which had been rumored to be reconsidering its dependence on the popular social network, said it has entered into a five-year strategic relationship with it instead.

New and old school publishing collide. Letter to Jane's newest issue is available in app format for the iPad for $0.99.

Jacques Pense is the designer behind this amazing award-winning stationery for 13th Street, a German horror network. Total and utter carnage. The punch hole impalings are truly awesome.

Exquisitely detailed Star Wars wedding cake! Amazing sugar art representation of Luke Skywalker lying in dead tauntaun innards, made for Star Wars artist Chris Trevas and his wife Julie.
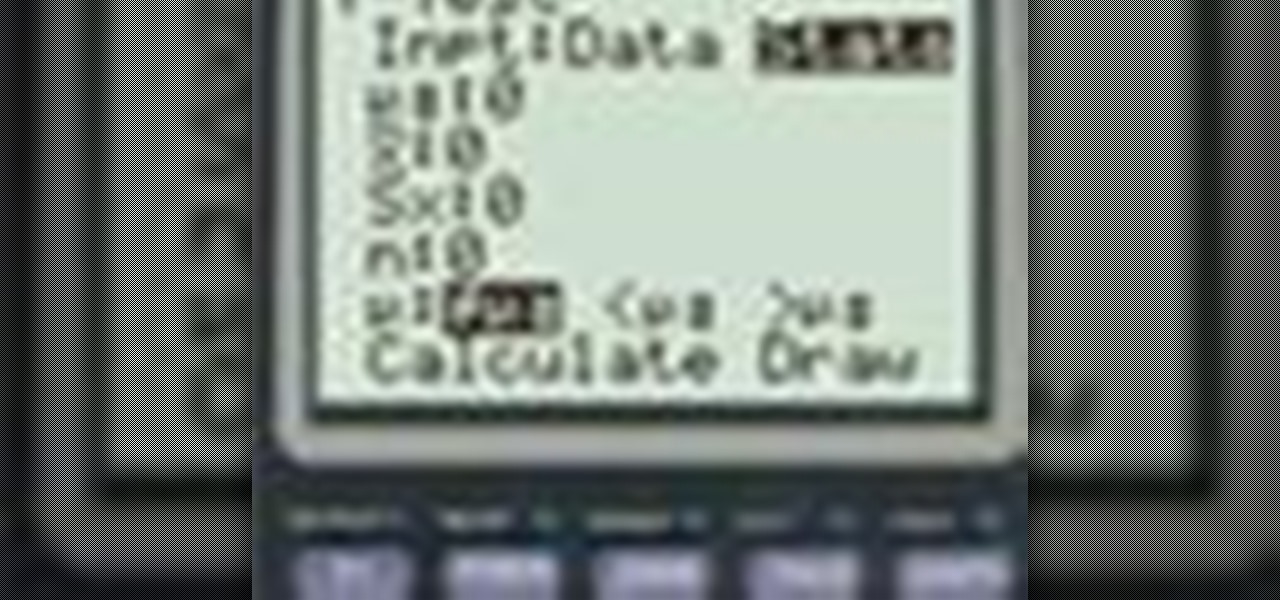
Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to test a population mean with a TI-83 graphic calculator.

Sprint has their EVO 4G. AT&T has their Inspire 4G. And now HTC has designed Verizon Wireless's first 4G smartphone—the ThunderBolt. It launched last week with high praises amongst Android devotees, despite its hefty weight, mainly because of the blazing fast speeds Verizon users are experiencing on the new 4G LTE network.
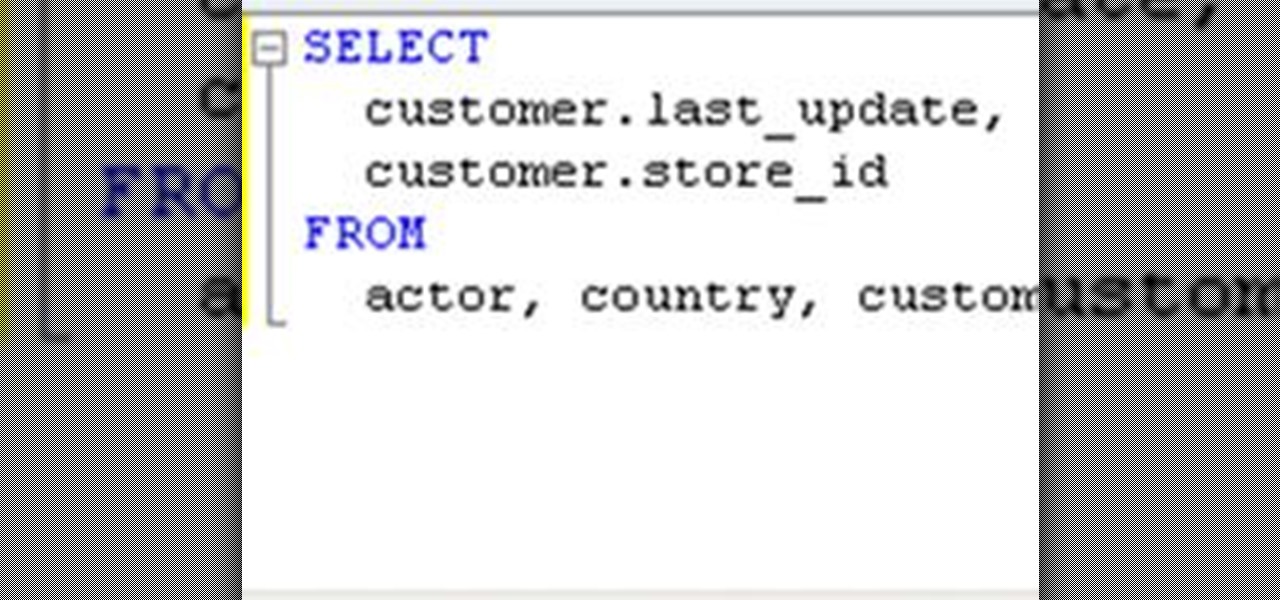
If you need to build a SQL query, you can choose one of two alternatives. The first and a rather old way is using a console. But if you build your queries in MySQL console, you have to remember all the commands and keys. This is not a convenient way, because query execution is a time-consuming process. Another way is to use some graphical interfaces for MySQL. It can fulfill many developers' requirements, including query execution.

Connecting your new smartphone gadget to your desktop isn't just connecting these products with a USB cord. It is important to sync them to allow the transfer of data from your smartphone to your computer and vice-versa. This is desired if you wish to transfer information including images, music in addition to daily schedules from the PC to your portable phone.
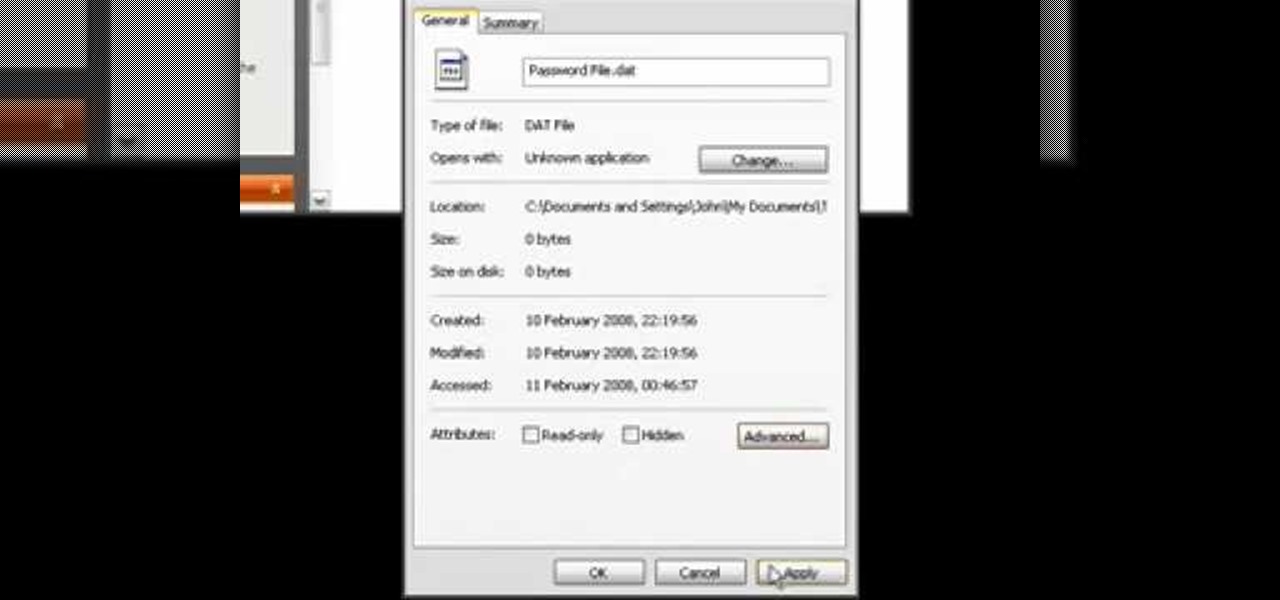
If you have files on your PC that you don't want other window's accounts to be able to access, you can encrypt them. Right click the file that you want to encrypt and select properties from the drop down menu. Once the properties page comes up, choose advanced. Now choose Encrypt contents to secure data and click ok. Now you click on apply. Select encrypt the file only and click ok. Hackers and administrators will not get an access denied message when they try to open the file. To make things...

In this Rhino / Grasshopper 3D software tutorial we rebuild the shift tutorial provided by David Rutten.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping your desktop clean and clutter free, along with the use of software to find documents you have misplaced.

With those icy winter months setting in, it's time to start sipping your bourbon warm. Spike your classic eggnog, hot chocolate, and even lattes with a splash of Wild Turkey bourbon. Below, five recipes to add a little fire to your typical cold weather beverages. Adjust the recipes to get more servings, and you've got some great ideas for Christmas party favors.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topology where sharing your wireless Internet via Ethernet would just be a better option.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

By now you’ve heard about the iPhone 4S announcement, possibly through our article about Apple’s newest smartphone. However, the star of the show was not the only announcement, so here are a few other announcements that were served along side the main entrée this morning. Let’s talk iCloud, iPod, iOS, and more.

Apple's "Let's talk iPhone" event has just ended, and the information isn't anything that wasn't already anticipated. Much to everyone's hopes, the iPhone 5 was not the headliner of the event. Instead, Apple's new CEO Tim Cook unveiled the iPhone 4S to the 250-seat audience, a speedier version of the iPhone 4. Here's the details.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out: Gears of War 3 and Dead Island, to name a few.

This Null Byte is a doozey.

You may not know him by name, but Eric Leebow is the man we can all thank for inventing social networking. At least, that's what he thinks.

We're ending the week with a lot of big announcements and updates. To date, Google+ has updated its name policy, but is still forbidding pseudonyms. Blocking people on Google+ became even easier, and yesterday, games on Google+ launched.

We've covered Chrome browser extensions that make your Google+ experience richer and more useful, but there are still many users who prefer to use Firefox. To that end, I've gathered 13 Firefox add-ons to aid in the enhancement of your Google+ experience.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

You've had a hard day at work and need to get out of the house, have a few drinks, but you don't want to go just anywhere—you want the right crowd and the right bar. For those nights, barhopping just isn't the answer, it's SceneTap.

Finally, summer is just around the corner! And while there are delicious fruits and vegetables available nearly every season, summer yields some of the very best picks. Equip yourself with one or more of the tools below before your next trip to the farmers market.

STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/

This one-two tutorial offers advice on how to work with bespoke shaders and compositing networks in Houdini 10. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look. Refine 3D trails in Houdini 10 - Part 1 of 2.
This clip presents a walkthrough of how to go about creating a particle based explosion in Houdini 10. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

This clip offers instructions on how to create your own lighting models using an illuminance loop in a VOP network. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look. Make lighting models in Houdini with illuminance loops.
Microsoft SharePoint is a business management system introduced by MICROSOFT. It has many build in functions to work in web based environment easily. Microsoft SharePoint 2010 is released on April 17, 2010. It is introduced with the promise of better performance than its predecessor version for both developers and IT professionals. It is entitled as “Business Collaboration Platform for the Enterprise and The Web”.