hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

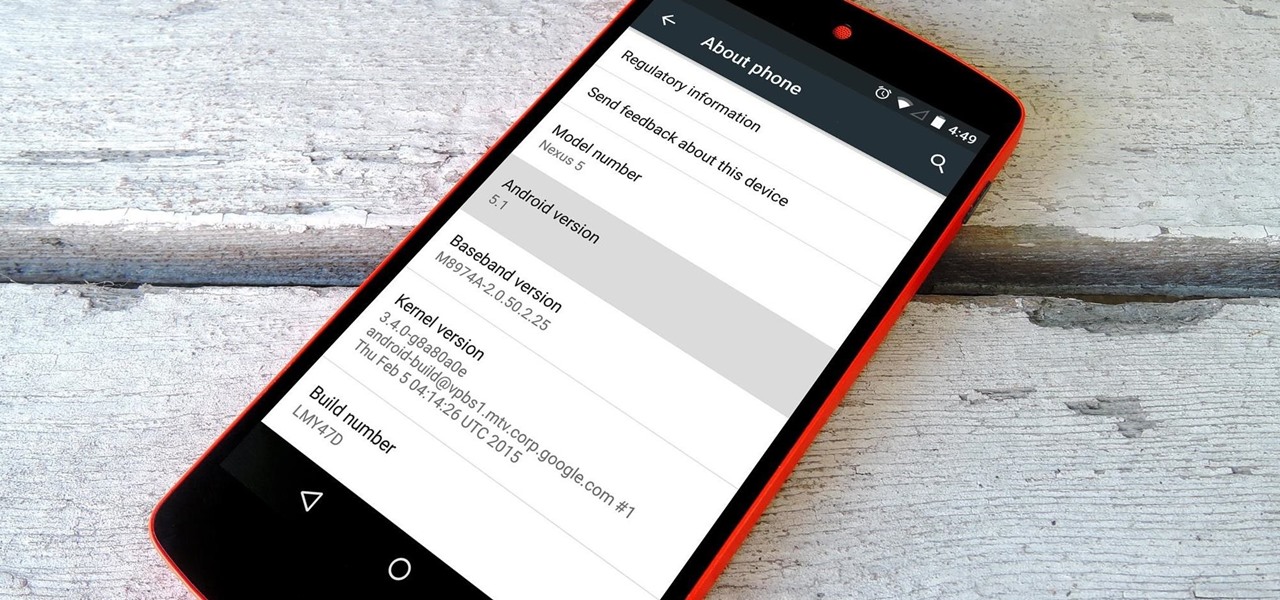
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

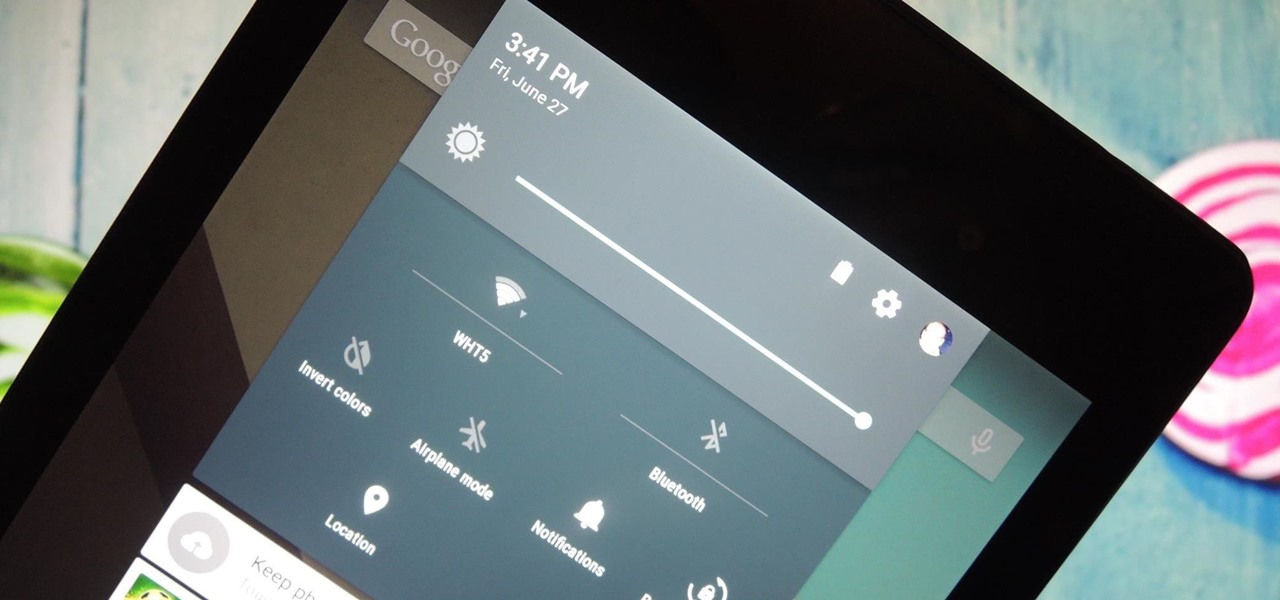
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

So, you've finally scored the coveted upgrade to chocolaty KitKat deliciousness, or you've managed to get your hands on a Nexus 5, the freshest thing from LG and El Goog. Satisfied with your new lease on life, you direct your phone's web browser to catch up on your Amazon Instant Video library, but not all is well—there are errors to be found. Much of the internet utilizes Adobe Flash, and Amazon Instant Video (who does not have an Android app) is just one such example. It simply won't work u...

Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

To make soap, you need fat, and if you've seen Fight Club, you're probably well aware of where soapmaker Tyler Durden got his fat from. Liposuction clinics. If you're not willing to go that far for a perfect bar of homemade soap, you can just use some drain cleaner and America's favorite food instead—bacon!

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21st. Though the whole world seems to be anxiously awaiting the announcement, there has also been some controversy surrounding the iPhone 5's production. With the high number of suicides and poor working conditions at Foxc...

In this video series, learn how to make Microsoft PowerPoint presentations. Our expert will show you how to use this handy piece of software to organize your data in a slideshow format, making for an easy viewing experience at any meeting. Topics covered include how to use the design template, how to change backgrounds, how to add text and animate it to come in when you’re ready to make your next point, how to add photos, how to do slide transitions, and many other helpful tips.

In this online video you'll get tips for recognizing signs of drug & alcohol addiction from a former addict. John DePalma explains how drugs can affect the brain and the long-term affects of addiction on the body. He explains the symptoms of several types of drug use, from alcohol and marijuana, to harder drugs like cocaine, crystal meth and heroin, and warns of the dangers of abusing prescription drugs like pain killers and anti-anxiety drugs as well. He then explains how to approach an addi...

Zip drives, floppy disks, compact discs, external hard drives and flash drives are many options for storing your data outside of a computer.

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

Learning to "dig" squash shots out of the corners can be puzzling for beginners. This video shows you how to approach the ball, and how important it is to keep away from the walls when playing shots close to the wall and corner.

If the patient has no neck or spine injury and is again breathing on their own. You now move the patient to the recovery position. Move the patients left arm over their head and cross their legs, pull their body on their side and allow them to recover on their own. Place a patient in the recovery position.

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

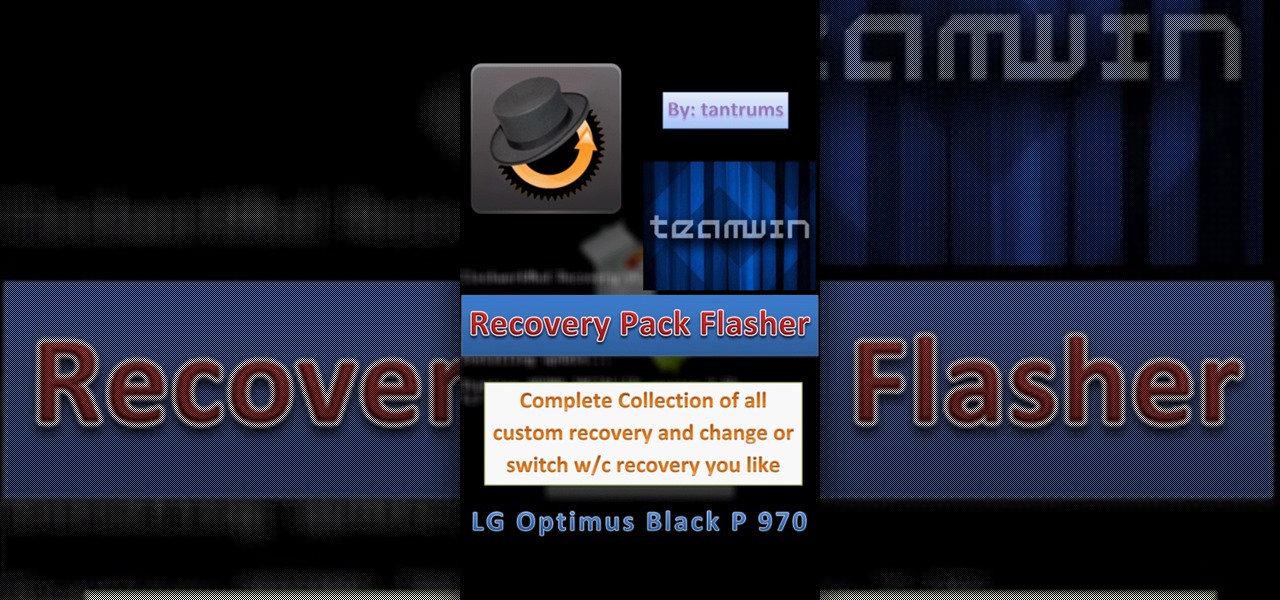
The following tutorial applies for all the LG Optimus Black (P970) Smartphones. So many of us might have installed custom ROMs like Zeus or Marvel. They come with the TantrumMod CWM recovery tool that installs by default in our phones.

More than 100 missions targeted at Earth's moon have been launched by space explorers since the late-1950s. NASA landed a total of 12 men on the lunar surface, collecting more than 800 pounds of moon rocks and lunar soil samples. But still, the moon remains a mystery, especially its formation. NASA's new mission aims to find out exactly how the moon came to be with the Gravity Recovery and Interior Laboratory, or GRAIL, part of NASA's Discovery Program.

If you've ever tinkered with a phone, you're familiar with booting into recovery mode. You're probably used to using a combination of hardware buttons to get into recovery, which usually includes the power button and one of the volume buttons. The thing is, you don't really need to press the power button.

So, you're all excited you went ahead and 'upgraded' your iPhone 3G to IOS 4.0X so you could reap all the benefits of all the new features.

They've been at it for a few years now, but the crazy group of amateur rocket scientists who call themselves Copenhagen Suborbitals have triumphed over adversity, successfully launching their DIY rocket nearly 2 miles into the sky last Friday. The privately funded, non-profit aims to one day send human beings into suborbital space on the cheap, without the need of government budgets and administration.

When downloading any application on an Android device, you will always be prompted by the following... Whether it's Angry Birds, Shazaam, or Chrome, every application will ask for permissions. If you try and deny these permissions, it won't install, leaving you with no other option but to accept. So what can you do?