Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

Since the release of Microsoft's Kinect, there's been no shortage of useful and fun hacks. In the past, we've seen the Kinect modded for things like x-ray vision, World of WarCraft gameplay, air guitar and 3D video. And now there's even a use for all of you MineCraft gamers!

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

This article relates to changing the settings in Adobe Flash so that you can improve your overall computer security and privacy. Changing these settings might have a negative performance impact on your computer - but it is worth while.

Google+ launched their API for public data today. For now it provides read-only access to public data in the form of People & Activities. Here are some links to get you started:

You've seen the felt mouse, which made computer clicking comfortable and chic, now brace yourself for something a little more interactive—DataBot.

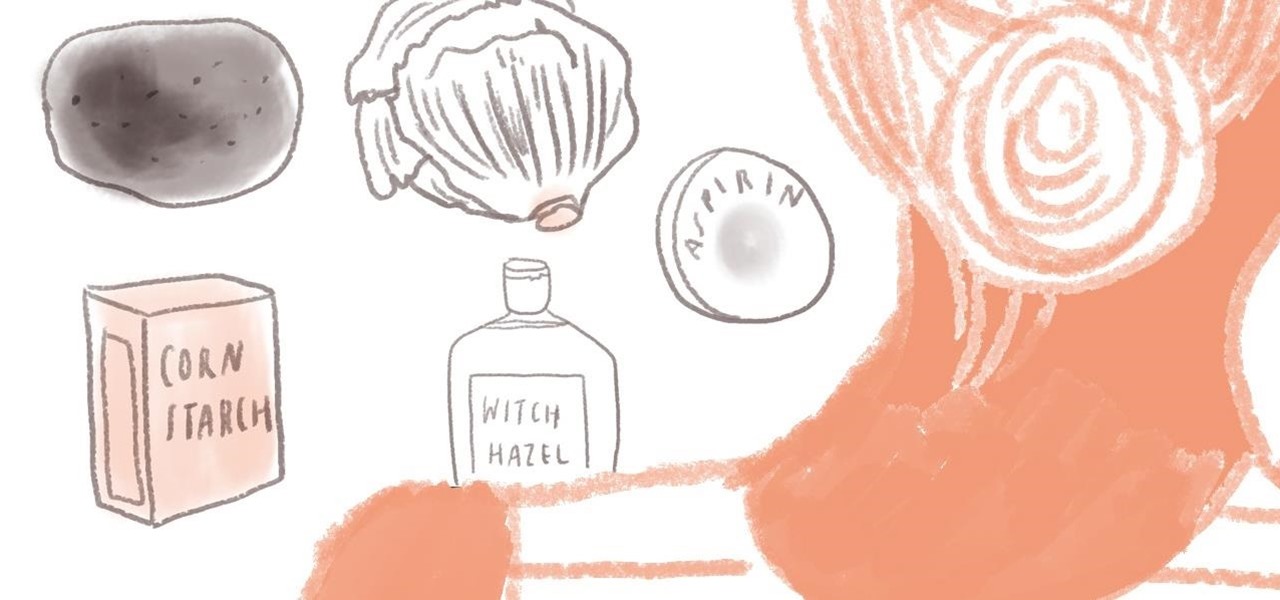
Too much partying and lounging under the mid-day sun? If your attempt at a toasty caramel tan has instead resulted in a bright red sunburn, you fortunately have many common household items at your disposal to relieve the discomfort and speed up the recovery of your burnt skin.

On the same day that Google launched their new social network, Google +, a team of Google engineers calling themselves the Data Liberation Front announced their first service on Tuesday—Google Takeout, a product that allows users to easily move their data in and out of Google products, including Buzz, Contacts and Circles, Picasa Web Albums, Profile and Stream (the equivalent of Facebook’s newsfeed).

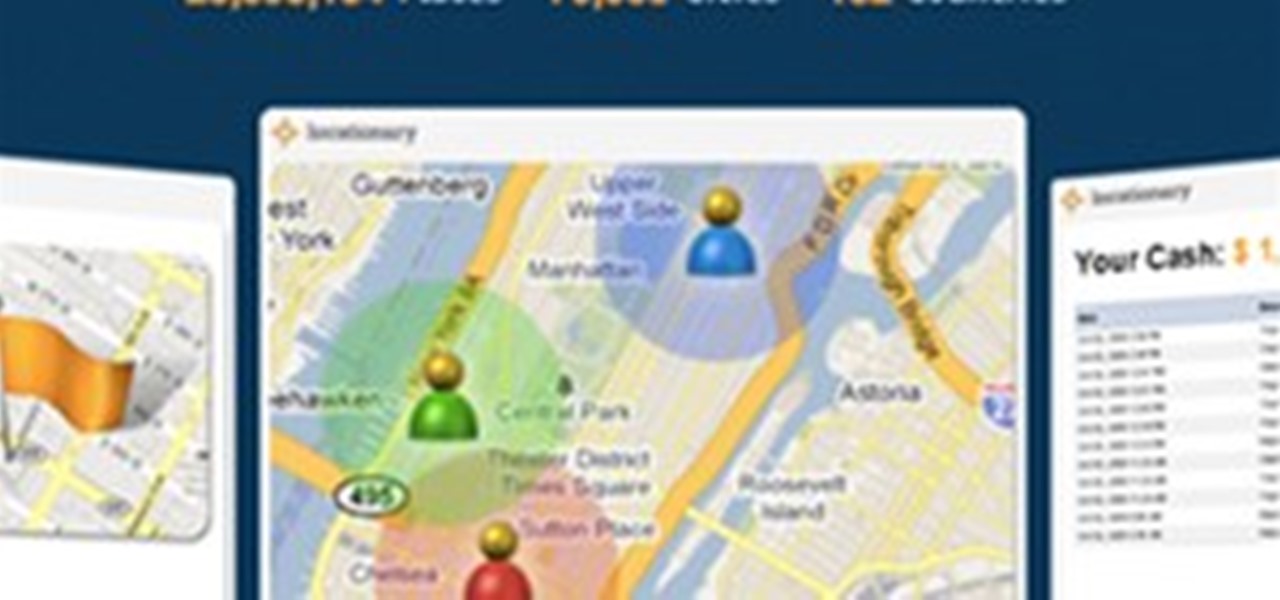
Watch the video to learn what it is all about. Locationary is a new system which rewards you for sharing your local knowledge.

I don't know how else to say it. In a word, the DTV (Dual Tracked Vehicle) Shredder from BPG Werk is just plain awesome. "Built as a first response modular platform to better equip the soldier to deal with crisis situations, the DTV is a new class of vehicle that can handle any terrain at high speed. It’s low center of gravity and rugged design make it ideal for a wide variety of applications including, reconnaissance, rescue/recovery, mobile surveillance/offensive platform, med-evac, rapid r...

Though summer is almost over, that doesn't mean you should ever be lax when it comes to protecting your skin from sun overexposure. However, should you find yourself with red and burning skin after a last-minute weekend trip to the beach, listed below are 9 simple and cheap home remedies for relieving symptoms of sunburn.

It's mid-January and some of you happy tax-paying citizens have already started receiving your W-4s and 1099s in the mail. But before you start filling out your 2010 Federal Tax Return, make sure you're hip to all the tax tricks in 2011. You could end up saving some money!

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Technology: The Less You Know the Better?

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Jeb just announced a great new feature that will be added in the 1.2 update. This map format, titled "Anvil," will open Minecraft to so many more possibilities with the new update to mod compatibility.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

This video demonstrates how to create a pivot table in Excel 2007. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to create a pivot table in Excel 2007, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to back up files with Time Machine, For Dummies.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to create histograms with a TI-83 graphing calculator.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to create a histogram with a TI-83 graphing calculator.

Update: Based on comments from Adam Novak, this article has been updated to better reflect how the video memory range works. You can check out his working emulator (written in c) here.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

Tetherd Cow Ahead posts an interesting science experiment. All you really need is a little bit of iron powder and a magnet, and you can unveil the info behind the magstripe on a credit card.

General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them.

In this 3D software tutorial we cover a basic planar projection for UV mapping in modo 301. The video gives a brief explanation of the concept of UV data and a real world application of manipulating the resulting map. Learn how to work with UV projection in modo 301. UV project in modo 301.

Truecrypt 5.0 adds many new features, most importantly Windows system partition encryption. To put it in slightly inaccurate layman's terms, this means encrypting your entire C: drive. Even if you already write your sensitive data to an encrypted space, files are sometimes squirreled away in unencrypted temp space or in the page file where they may be recovered. Using Truecrypt to encrypt your Windows XP system partition will help eliminate this problem.

In this article, I'll show you how to send SMS messages with Python. You'll need Python 2.7 or later, urllib and urllib2. The code basically uses an online text messaging service to "POST" html data, as if a person was entering the data themselves. The uses for something like this are unlimited. For example, I modified the basic code so I would receive a text message letting me know every time someone rang my doorbell. The program could interface with Arduino through a serial port, and send d...

When returning a serve requires some decision making, eg take the ball high in the air, let the ball drop, let the ball hit the side wall before volleying, or maybe volley boast.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a squash forehand horizontal and vertical swing.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a squash solo drill: backhand drive.

Squash is a racquet sports game, seemingly similar to tennis, but played on a small indoor court with hollow rubber ball, much small than a tennis ball. Squash is an intense, high impact sport. This squash tutorial demonstrates a Squash backhand volley, boast, drive off.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.
Sergio Peralta Advisor: Jessica Davis

From the article: Foursquare, one of the net’s hottest startups, got an unwanted message on June 20 from a white-hat hacker: it was leaking user data on a massive scale in plain violation of its privacy policy.