A few months ago, we showed you a pretty awesome light painting project that visually captured invisible Wi-Fi signals around town using a Wi-Fi detecting rod filled with 80 LEDs. With some long exposure photography, the results were pretty amazing. This project was inspired by those crazy Norwegians, but this build lets you do something even more amazing—capture pictures of colorful written text and drawn images, frozen in midair.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

QR codes are like smart little cubes of data. To unlock this data, you will need a QR reader. These are annoying because you typically have to download a third-party app, and some of these apps are shady. Luckily your Samsung Galaxy running One UI has a hidden QR scanner built right in.

While most smartphones have the ability to receive FM signals via a tuner, mobile carriers prevent users from taking advantage of this hardware — probably in an effort to get their customers to spend more money on data.

2017 has been a good year for Apple thus far. The new Kantar data is out, showing that from November 2016 to January 2017, the iPhone 7 has held steady as the top-selling phone in all the largest markets.

If you want to have windows .iso files for various purpose like you want to have windows 7 in virtualbox, then you need an .iso file. There are many methods of creating an .iso from installed windows. But what if microsoft provided all of them( I mean 7,8 &10) free of cost. The only requirement is that you own a product key for the respective Windows edition (and that's also is not a painful task to get).

If you've noticed moments when there's a drop in quality when listening to a song on Apple Music, it's not just you. When on a cellular connection, the streaming quality drops when compared to that of a Wi-Fi connection.

Who uses Yahoo! Image Search, you ask? Scientists apparently.

Interested in creating your own dynamic, web-based applications using Visual Basic 2005 Express? In this installment from the Absolute Beginner's Series of Visual Basic/ASP.NET video tutorials, how you can connect your applications to databases. You will learn how to enable your application to view and edit data stored. This will allow you to exercise the skills shown in the earlier videos. For more information, as well as tips for being a smarter user of Microsoft Visual Basic, take a look! ...

Interested in creating your own dynamic, web-based applications using Microsoft Visual Web Developer? In this installment from the Absolute Beginner's Series of video SQL tutorials, SQL Server beginners will learn about tables and definitions of data types, properties, keys, etc. in this second video. Find out how table rows, columns, and fields interrelate and whether columns can be empty. For more information, as well as tips for being a more effective user of Microsoft Visual Web Developer...

Interested in creating your own dynamic, web-based applications using Visual C# 2005 Express Edition? In this installment from the Absolute Beginner's Series of Visual C#/ASP.NET form control video tutorials, you'll learn how to use the Tree View control which provides a hierarchical view of data. . For more information, as well as tips for being a smarter user of Microsoft Visual C#, take a look! Use Tree View in Microsoft Visual C# 2005 Express.

Interested in creating your own dynamic, web-based applications using Visual C#? In this installment from the Absolute Beginner's Series of Visual C#/ASP.NET video tutorials, you will learn how to use the List View control which provides a graphical representation of data elements. For more information, as well as tips for being a smarter user of Microsoft Visual C#, take a look! Use the List View control in Microsoft Visual C# 2005 - Part 1 of 2.

This tutorial will show how to use GPG and the FireGPG plug-in to encrypt and decrypt messages in Gmail. GPG is an open source implementation of OpenPGP (Pretty Good Privacy) , a public-key-encryption system. With public key encryption you don?t have to give away the secret key that decrypts data for people to be able to send you messages. All senders need is the public key which can only be used to encrypt, this way the secret key never has to be sent across unsecured channels. Encrypt Gmail...

Ever hear of Spokeo? No, it's not a city in Washington state. It's a website called Spokeo.com, and it marks the complete end of privacy on the internet. If your phone number and address has been posted in a phone book, it's on there. If you own a house, chances are there's a picture of it. If you have a Facebook profile, it's probably listed.

"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.
National Security Agency whistleblower William Binney reveals he believes domestic surveillance has become more expansive under President Obama than President George W. Bush. He estimates the NSA has assembled 20 trillion "transactions" — phone calls, emails and other forms of data — from Americans. This likely includes copies of almost all of the emails sent and received from most people living in the United States. Binney talks about Section 215 of the USA PATRIOT Act and challenges NSA Dir...

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Have you guys seen this yet? Ben Purdy used projection mapping to create a "real life" Minecraft block. If you don't know what projection mapping is, it works like this:

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog posts, music tracks, and the like. And then there are those who are very mobile with their devices. They commute to and from work on a regular basis with their iPhone or iPad. Some users may travel a lot on business, or...

Want to see which country or city uses Google the most? Try Google's new eye-stimulating tool, Search Globe.

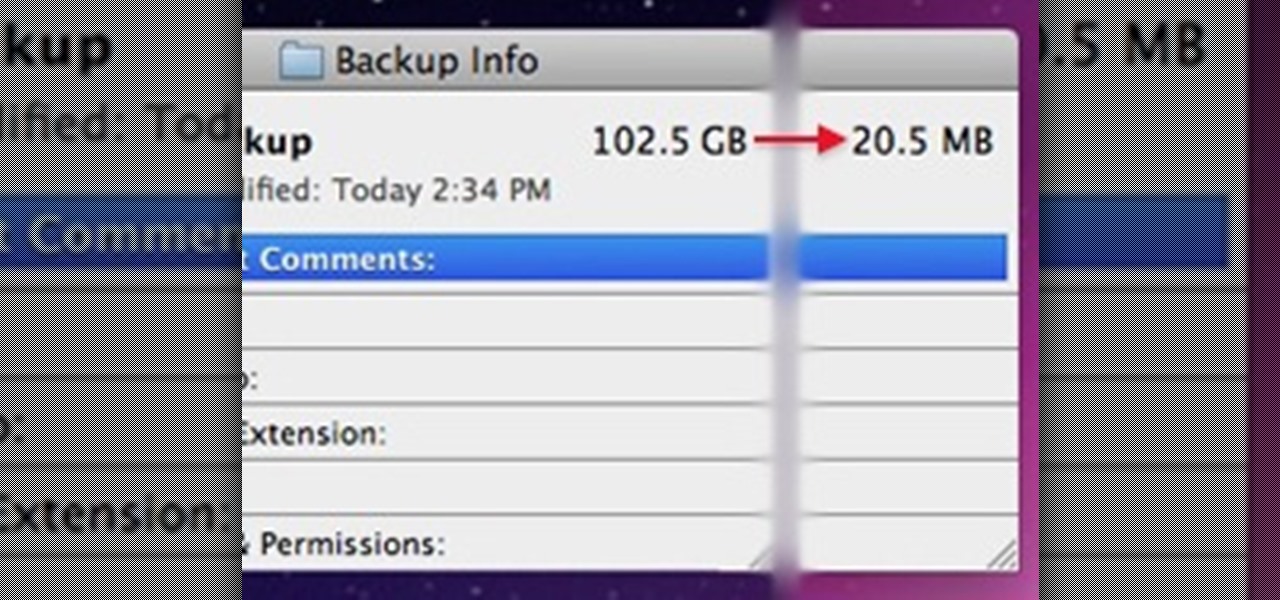
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

Have you ever left your computer one all night? Maybe downloading something, or just out of habit? Well there is a way you can turn that unused CPU usage in to cold hard cash: Distributed Computing.

About two months ago, the massive Gawker Media hack was a wake up call for many web denizens on the importance of proper password security. Data analyzed by the Wall Street Journal revealed the three most popular passwords recovered from the hack were downright idiotic—123456, password, and 12345678. If past events weren't motivation enough for crafting a strong password, then maybe a racy 8-bit stripper is. Naked Password is a jQuery plugin by Platform45 that rewards you with an accelerating...

Norwegian designers Timo Armall, Jørn Knutsen, and Einar Sneve Martinussen visually capture invisible WiFi signals by light painting signal strength in long-exposure photographs. The trio set up a four-meter long WiFi-detecting rod with 80 LED bulbs to depict cross-sections through the WiFi networks of various Oslo neighborhoods. Armall says:

By John Timmer, Ars Technica How much information can the world transmit, process, and store? Estimating this sort of thing can be a nightmare, but the task can provide valuable information on trends that are changing our computing and broadcast infrastructure. So a pair of researchers have taken the job upon themselves and tracked the changes in 60 different analog and digital technologies, from newsprint to cellular data, for a period of over 20 years.

Ever wonder what you look like to someone else as you walk, talk? How it looks from above, behind, or to the side? Seeing yourself in a video flattens the experience into two dimensions, but this wireless camera rig experiment from Instructables member BigRedRocket brings it into the third dimension:

What if everything in life was controlled by augmented reality? Keiichi Matsuda imagines: "The architecture of the contemporary city is no longer simply about the physical space of buildings and landscape, more and more it is about the synthetic spaces created by the digital information that we collect, consume and organise; an immersive interface may become as much part of the world we inhabit as the buildings around us.

100% functional LEGO ATM by Ronald McCrae. This bonafide brick bank performs the following functions:

Remember, in the Terminator movies, when Arnold's field of vision is superimposed with all sorts of data? Sci-fi writer Vernor Vinge also described electronic contact lenses, technology that "projects" information right before the eyes.

Don't worry, the robot apocalypse is not upon us...yet. Wired reports it may be closer than you think:

Are Twitter and Facebook in trouble with the advent of Google's brand new social networking tool, Google Buzz?

In this Dreamweaver 8 video tutorial you will learn how to display records by extracting info from a database. Learn how to create a data connection, create a query, work with recordset, display items, and use repeat regions. Note: To use this tutorial you need XAMPP and make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Display records in Dreamweaver 8.

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).