
News: Man Walks On Half a Million Volts of Electricity
Michael Faraday was an English chemist and physicist - a bona fide electromagnetism and electrochemistry genius. Without him, men couldn't walk on live electrical wires. Wait, what?


Michael Faraday was an English chemist and physicist - a bona fide electromagnetism and electrochemistry genius. Without him, men couldn't walk on live electrical wires. Wait, what?

Get Google Chrome Download and install Google Chrome.

Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

Inception may not be the lead contender for the 68th Golden Globe Awards, honoring the best movies and television from 2010, but Christopher Nolan's film still collected four nominations— Best Motion Picture, Best Director, Best Screenplay and Best Original Score.
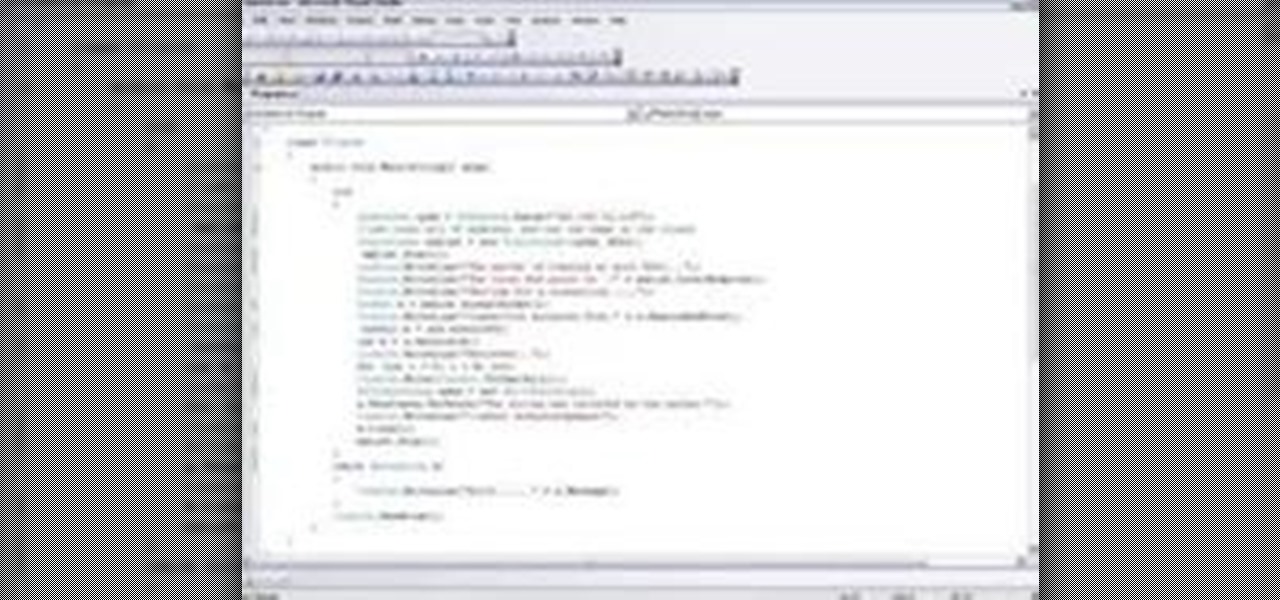
Socket programming in Unix allows multiple computer programs to "talk" to each other in the form of open "pipes". This is used in many popular programs for the Linux system (see any distribution). This how-to is created to understand the simple creation of a socket and what the various parts of the call mean.

Has your hard drive been broken, overheated, or simply worn down from old age? Learn how to recover data from a crashed hard drive with a few simple tips and utilities. Resurrect a crashed hard drive.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we've covered over time.

Written by JD Coverly of WonderHowTo World, LoadSave:We've spent the last week with Sprint's new phone, the HTC Evo 4G. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple has unveiled the new version of their phone this week and thankfully it's debatable as to which phone is better. The iPhone has better battery life and a more robust App store, but it suffers from a smaller screen, smaller camera resolution, no HDMI out, face talk only on wi-fi networks, and ...

Hello everyone, I am Brandon Hopkins from TechHut and I am going to be showing you how to install Minecraft Texture Packs on Windows, Linux, and Mac. I will also link you to one of the best Texture Pack I have used and a website where you can download 100+ different texture packs.

Charts can be used to visually present your data. In this tutorial we will take a look at how to create basic column and pie charts using MS Excel. Learn it to create a sales chart for your boss! Creat charts in Excel.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.
Back in the eighties, I used to hate television commercials, but I eventually got used to them. Had to, in order to enjoy my favorite shows. Then, the increasing number of billboard ads annoyed me in the nineties. They followed me everywhere I went—no escape—persuading me to buy the newest whatever. It seemed like Big Brotherism—like They Live. But, I got used to it. When I finally entered the digital age and became a web addict, I was peeved at the constant sight of online ads everywhere I v...

After years of false rumors and abandoned hopes, the day has finally come. Verizon Wireless is finally getting the Apple iPhone!

My name is Noah Hornberger. I'm a former Pixar artist (Wall-E, 2008) and Professor of Animation (DePaul University, Chicago), and I have recently invented a motion-activated musical toy called the Dub Cadet. One Substance TV blogger has called my light-up sphere that transforms motion into music, "Daft Punk [the electronic music duo] meets Simon [the handheld toy] in a ball."

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

Your first, very basic web crawler. Hello again. Today I will show you how to code a web crawler, and only use up 12 lines of code (excluding whitespaces and comments).

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

Gamers like myself who have switched back and forth between Skyrim on PC and Xbox lack the ability to share game saves. This really sucks. I love playing Skyrim on a console. It's a very comfortable, easy and relaxed gaming experience. You don't have to worry about your frame rate being optimized, or wrist pains from using a keyboard. However, gaming on the PC can allow you to use texture enhancing mods and get an overall smoother experience due to a lack in glitches and bugs that plague the ...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

To the displeasure of many loyal Firefox users, Mozilla has been deploying what seems like a new marketing strategy to "catch up" to Google Chrome. I have no idea if this is because the version number is higher than theirs, but it is downright annoying. It's not all complaints, though. Firefox has done an amazing job at completely revamping its source code and redesigning all of its engines, making it a more than worthy competitor to Chrome. However, we are displeased with Firefox because eve...

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

This morning, the Official Google Blog and Chrome Blog revealed the new tab page, which lets you flip between your installed apps and your most visited web sites. To take a look at how it works, check out the video below. The Chrome Web Store also received a facelift. It's now a lot bigger and brighter, with infinite scrolling instead of pagination. Adding new apps and extensions is a snap; all you have to do is select your app or extension, read more about it, and then click on the +Add to C...

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one has access to your money, except you. It's decentralized from government, run by the people, for the people.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...