Mozilla is scheduled to release their updated Firefox browser on Tuesday, bringing the popular web browser up to version 6. Lately, the Mozilla team has been releasing newer versions of Firefox without a slew of new features, focusing on fixing bugs and getting the improved product out as quickly as possible, in order to compete more rapidly with other browsers like Google Chrome.

Hard drive space is one of the cheapest things you can add to your computer. But people take it for granted, thus game developers have given up any efforts in keeping games compact. With all of its expansion packs, World of Warcraft takes up more than 60 GB of hard drive space, and almost any AAA game consumes a gig or two.

Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was hacked by LulzSec, with 1 million passwords taken and 40,000 made publicly available. Comparing the two data sets, Troy Hunt found 88 accounts on both sites that used the same email address, and of those accounts, 67% use...

Lady Gaga and Polaroid's upcoming Grey Label Camera Glasses can record video and snap pictures, but who really wants to show the world what they're up too on those mini LCD screens? It's nothing more than a fancy gimmick between a pop star and a failing company. Isn't the intention of camera glasses to capture things around you as they are? Drawing attention to yourself with clunky video-displaying eyewear kind of defeats the purpose, but that's why they're "fashion" glasses and not practical...

For most Americans, the bane of the hangover is typically remedied by lots of water, painkillers, greasy food, and a day wasted on the couch. But if you're tired of potato chips and fried eggs, perhaps it's time you enter unfamiliar territory. Below, a combination of unorthodox methods for taming the beast, derived from science, sparkly Whole Foods new ageism, and the far East.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

What's the next best thing to being an official scientist? Being a non-official one. A new website called Science for Citizens helps you find the science experiment of your dreams, hook up with the scientists involved, and actually take part in the experiment itself. Here are some examples of what you can do:

With the globally rampant use of such social networking platforms as Facebook, Twitter, and Foursquare, the issue of privacy has become a prevalent concern for many. And for good reason—there's the violation of Facebook employing user names in ads, the Etsy slip-up, and of course, the everyman act of recklessly sharing too much information via common social media outlets: a night of drinking results in morning after embarrassment, or worst case scenario, sloppy Facebook posts and tweets resul...

Screw the airplane man. Ticket prices are too high. Competitive consumer choices are pretty much nonexistent. And need I go into the pain of being crammed into those tiny seats, elbow-to-elbow, thigh-to-thigh with a perfect stranger? Even your average Richie Rich winces at the astronomically high prices for a First Class seat.
You and I know that everyone's lookin for a killer deal for cellphone service. A lot of us hear about good deals for the plans, or who's got the hottest phones at the moment. Though most of us these days are just looking for something simple, that has all we need, and is fairly cheap too. But how cheap is too cheap?
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane"
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity

If you're an owner of a BlackBerry smartphone, chances are you're going to want to use BBM, which for all of you newbie BlackBerry owners, stands for BlackBerry Messenger. BBM is an instant messaging application developed solely for BlackBerry device owners.

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)
Microsoft office 2010 is the successor version of office 2007 and is code named as office 14. It is the first 64 bit version of office which is only compatible with Microsoft service pack 3, Windows vista and windows 7. It was released on April 15, 2010. It is the first Microsoft application which offers free online version of word, excel, PowerPoint and one note. These can be easily used with all the popular browsing software. The various functionality which are added in office2010 are descr...

BPA: Why Plastic Ain't Good For You BPA or Bisphenol A is in many of the products we use. Everything from Ziploc bags to shower curtains, we are exposed to BPA all the time.

How much do the producers of Lonely Girl make? How much do the producers of American Idol make? How much does COPS cost to make? I decided to share what I have learned for the CES audience in Vegas.

Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough.

Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend:

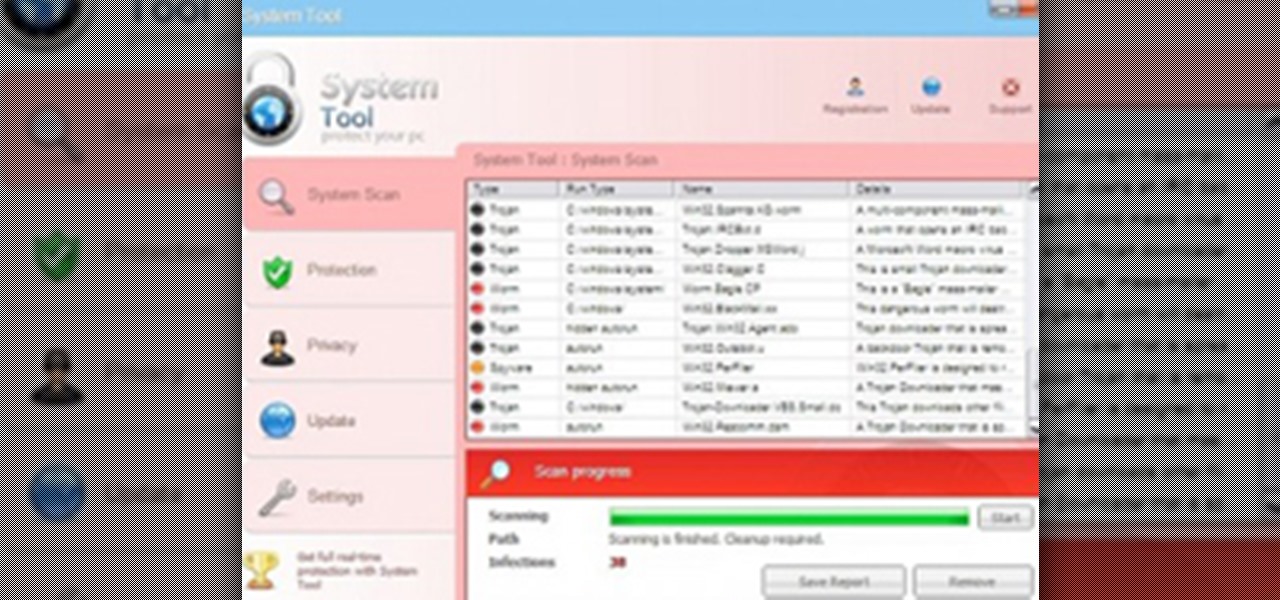
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

Dreamweaver's Validate Form behavior checks the contents of specified text fields to ensure the user has entered the correct type of data. In this Dreamweaver 8 video tutorial you will learn how to create validate forms. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create validate forms in Dreamweaver 8.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Don't ever be caught without your "go-to" items in your bag. In this video, Jennifer, Beauty Vlogger, shares her top seven makeup "go-to" items. Moisturizer

The Achilles tendon is subject to inflammation, tendonitis, tendinosis, tendon rupture and tendinopathy. Learn about the anatomy of the ankle and the Achilles tendon in these expert videos. You will get tips from our physical therapy expert for non-surgical treatment of the lower leg. Learning the appropriate exercises for the Achilles tendon can aid in flexibility and repair of the tendon. See how to perform important stretches to enhance the range of motion in your ankle and lower leg. Watc...

We've all relied on the internet more than ever during this pandemic. But while you're staying safe at home, are you being safe and productive while surfing the web? That's where a trusty VPN comes in handy!

Politics(the Government) is built to accomplish a few things: maintaining order, providing necessities, operating businesses (stimulating the economy, trade), maintaining public relations and the most important of all, protecting the rights of the individuals it governs. It has a broad role, and as such, an array of bills, laws and rules to regulate itself and the country.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

It’s been a pretty big week for Google, and Google+ itself. There were a number of articles proclaiming the end of Google+, because allegedly traffic dropped over 60% after it opened to the public. Then +Steve Yegge accidentally posted a long rant on Google+ itself, which was originally meant only for Google employees and colleagues to see. Interestingly enough, the most inflammatory content wasn’t actually about Google itself, but about the horrible work environment at Amazon. The accidental...

JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, slideshows, popup dialogs and calculators, or you create entire web-based apps. The list goes on nearly forever.

Things have been a bit quiet on the Google+ Insider's Guide this week. With the launch of the new Facebook, Google+ is finding itself a bit on the defensive. However, recent data shows that by making Google+ available to the general public, their traffic has jumped 13-fold, according to Mashable. With the new growth also comes the introduction of cool new features, which further enhance sharing.

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

Foldit is definitely a niche game. The sole gameplay mechanic is attempting to fold complex proteins into smaller and more efficient shapes following the rules of molecular physics and biology. Points are awarded based on how small one can make the protein. Online leaderboards track players' relative progress and allows them to view and manipulate other players' completed designs. It's original, certainly, but no developer is going to ship a million units of a game about molecular-level prote...