This week has been pretty exciting for both Facebook and Google. Facebook announced a slew of features that seem on the surface to copy Google+. For Google+ users, a lot of improvements, updates and features were implemented, and they're seeing a lot more overall integration with their Google account.

Once you get past the initial quick start setup of the Canon EOS 5D Mark II, capturing pictures in auto mode is a breeze. But what do you do after you've snapped those photos? This quick guide will show you the easy steps to viewing your images directly on the camera.

The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search.

Last week, we discussed whether Google should require you to use your real name for Google+ profiles. Google is working on eliminating fake profiles, and in the process, they've booted some real people, including actor +William Shatner. If you find out that your Google+ account has been suspended, you can appeal the suspension and get your profile reinstated.

It's called a Quick Response code, but most know it simply as QR code, a matrix barcode dedicated to the world of smartphones. The information contained within the square black modules could be text, a URL, vCard, or some other kind of data. And even though mobile tagging has been around for eight years, it's just now spreading like wildfire across the globe, being incorporated into artistic portraits and wall art. And most recently... "social clothing".

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...

You've had a hard day at work and need to get out of the house, have a few drinks, but you don't want to go just anywhere—you want the right crowd and the right bar. For those nights, barhopping just isn't the answer, it's SceneTap.

Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.

Introduction to KVM KVM is a free and open-source Kernel-based Virtual Machine using the Linux kernel for virualization and is very similiar to a hypervisor like Xen or VMware's ESXi. It is based on Qemu, a processor emulator. Any virtual machine created on or working on KVM can work on Qemu also, but with a great reduction in speed.

In the wake of the recent tragedy in Japan, Southern Californians have been hyper alert to any news regarding dangerous levels of nuclear radiation drifting over from Fukushima. At this time, official statements from the California Department of Public Health and the EPA are assuaging the population that there is nothing to fear. While there has been some detection of radiation in the air, the current levels recorded are "thousands of times below any conservative level of concern". But despit...

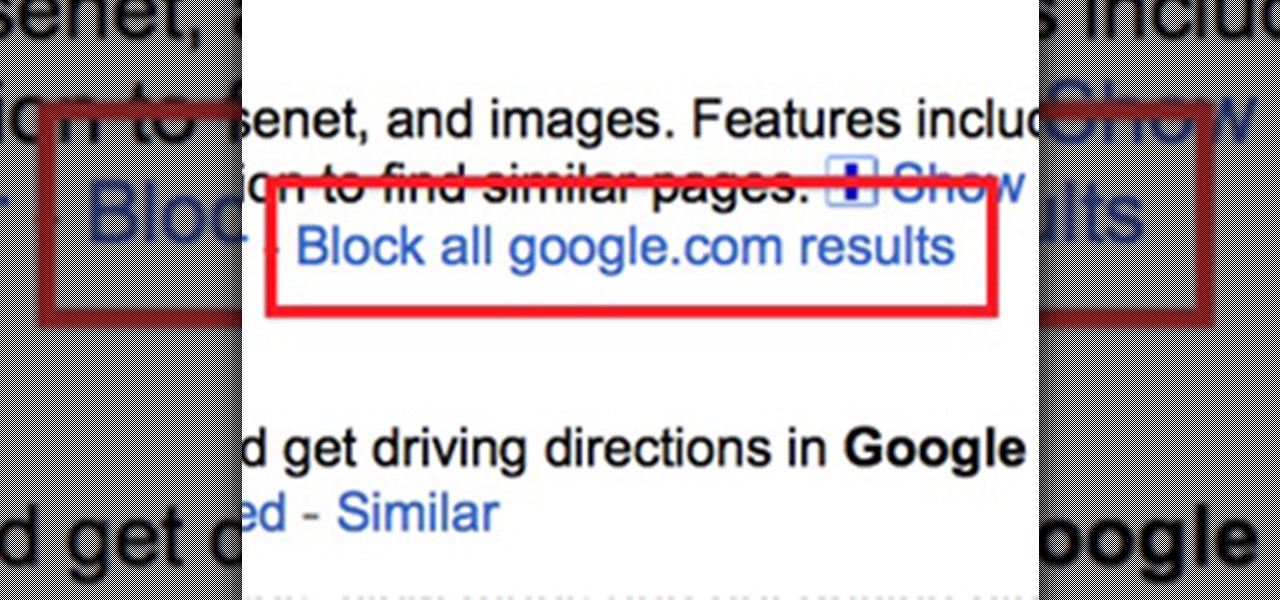
Google recently rewrote their search algorithm to make "low-quality sites" disappear from your front page results, putting the emphasis on better, more relevant answers with original content and in-depth information. And now Google has added a new feature to their search system that gives you some of the control of what you see in your results.

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

Sure, you go online to email and shop and do research. But have you ever been curious about how the internet actually works? Don't worry, you don't need a degree in computer science to get a handle on how your info gets from point A to point B. Learning the basics of the internet will give you a whole new appreciation for all those emails and chat messages that seem to magically appear. Get ready, because we're about to enter the wonderful world of digital data!

Destroy Black Ops Noobs First of all, these tips are great for any consoles that run Black Ops. Whether it be your Sony PS3, Nintendo Wii, XBox 360 or your PC.

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

Dual booting Ubuntu 10.10 Maverick Meerkat and Windows 7 is fairly easy. If you don't believe me, just read on!

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

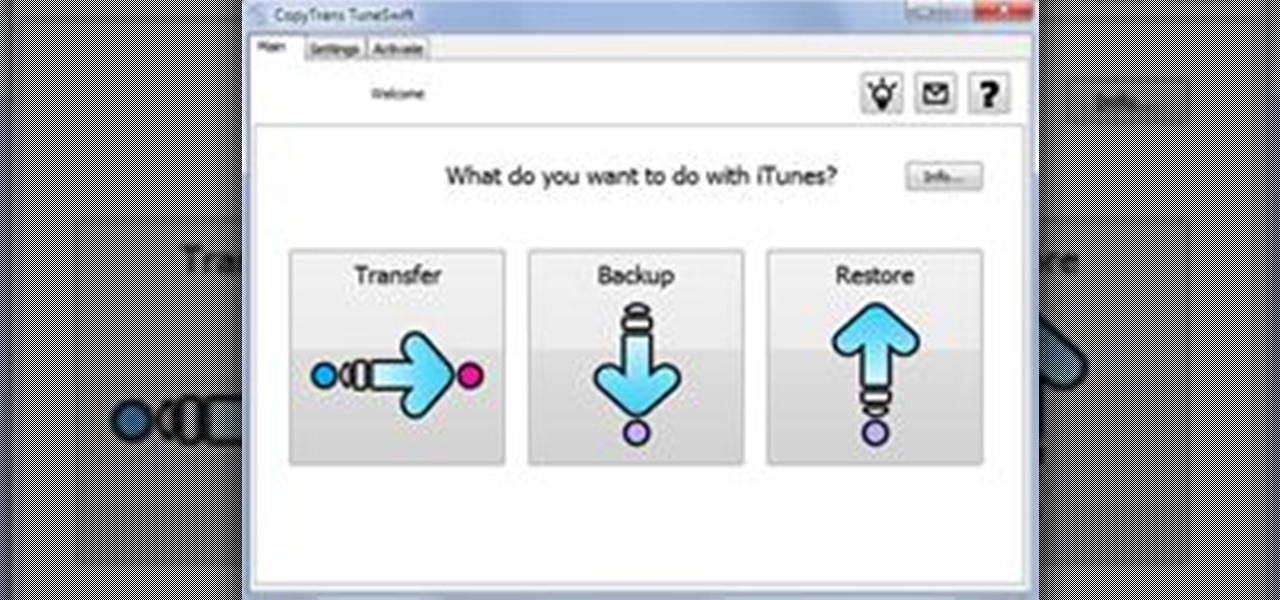
How to transfer iTunes from PC to Mac You want to switch from PC to Mac and you want to take your iTunes library with you? There are several ways to move iTunes from your Windows PC to your new Mac. You can manually move all your iTunes contents to an external hard drive and from it to your Mac, or you can use a software like CopyTrans TuneSwift that does the job for you. Let's start with the easier way!

We have no control on the weather yet it is a part of our lives which influence what we do, what we eat, what we wear and many times where we live. How did people predict the weather before there was the Internet, television, radio or the weatherperson with all of their gadgets?

Are you tired of counting your hair while waiting for your computer or laptop to respond? Then, these easy steps are perfectly fit for you, especially if you're a Windows 7 user.

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

There's never been a better time to learn to code. If picking up this crucial skill has been on your bucket list, the Interactive Learn to Code Bundle can get you up to speed.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Skyrim really took the cake this year. With its awe-inspiring gameplay, much improved combat and leveling system, and a fresh new look, it's no wonder the game has already received a Game of the Year award. But for hardcore gamers, the fun may be over. You've played the game for thousands of hours, and have exhausted the entire game's main and auxiliary quests. You need more.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Real time redstone clocks are a marvel of redstone technology. Not only can they keep track of time, they are capable of powering other more complicated redstone machines. Regardless of whether a redstone clock runs a ten second or twenty-four hour time span, they operate on the same principles, which can be easy and straightforward to understand.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Now that Google+ is open to everyone, there are a lot of new people who aren't techies trying out the service. When you first sign on, it can be overwhelming. I've decided to round up a bunch of resources to help you get started, and recommend some people for you to follow, if you want to stay on top of tips and new announcements.

G+Me is one of our favorite Chrome extensions here at Google+ Insider's Guide. We love it because it's one of the most comprehensive extensions out there. It attempts to address the "noisy streams" issue, with list mode, and collapsible posts and comments. The creator, +Huy Zing, is very responsive to feedback, and he's been quick to address any issues that arise, including privacy concerns. He's even created a G+Me (Paranoid Edition) extension, for the extra careful Google+ user. And if you ...

Last week's round up was all about third party services that sprang up to fill any Google+ voids. This week, I'll let you know how to keep up with the latest Google+ updates, and give you some great tips for interacting with your followers.

Although Google+ has solved many of our problems with social networking, it's not perfect, and we all wish they'd be a just a little bit faster with the improvements. In the meantime, you can stave off your hunger with useful Google Chrome extensions that improve upon Google+.

As I was listening to Apple's WWDC conference today, what ran through my mind the most is if there were ever a time to switch to the world of Apple computing now is it. Today's WWDC keynote presentation was chock-full of new and updated iOS mobile software—too much to cover in this one article. But the most "new thing" coming from Apple this Fall is iCloud, a file sharing and streaming service that requires no wired connections.

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.