For people that live outside of the United States, how many times has this happened when surfing through U.S. streaming services? If you're outside of the U.S. market and want to stream stateside services like Hulu, MTV, CBS, Pandora, and others—you're in luck. Tunlr is an application that re-addresses certain data envelopes, tricking the receiver into thinking the data originated from within the U.S. by using its own DNS server's IP address. You can even watch some non-US shows stateside, li...
Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

In this video tutorial, viewers learn how to recover and restore deleted files using Recover. Recover is a freeware data recovery program. Recover recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Start by selecting the type of file. Continue by inputting the information. It will then take an hour to scan the drive for the deleted files. Once finished, it will display all the deleted files. The green files are recoverable and the red files are...
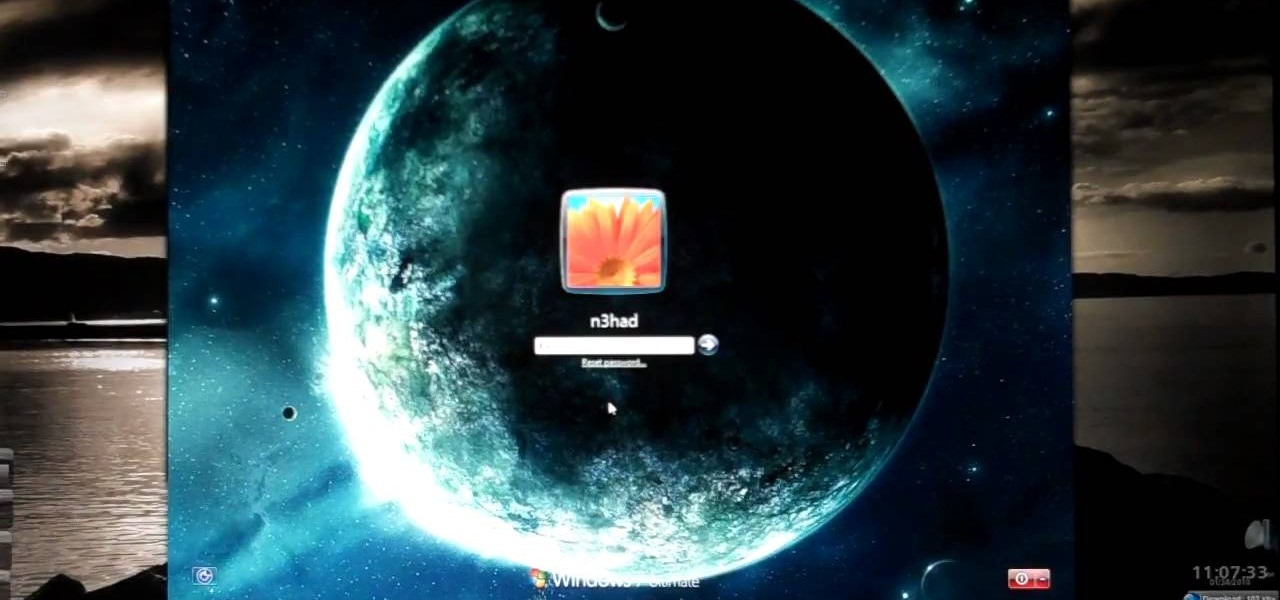
Windows is a mess sometimes, full of problems. And your password just might be the biggest problem of all, if you've lost it, of course.

Learn how to browse the Internet at work and get away with it. Load Excel (Any version will do). Click on the Data tab. Click 'Import External Data'. Click 'New Web Query'. Once the window has loaded, click through the prompts, selecting Yes. When the window has loaded completely, go to your favorite website in any browser you want. For this example, Twitter is used. Go to the RSS Feed and copy the link that appears at the top. Paste the link into Excel and click the Import button. Accept any...

Taking a cue from Apple and its Health app for iOS, Google has created a central hub to collect health and fitness data on your Android device. With it, you can share and sync health and fitness data, such as steps, heart rate, water intake, sleep quality, and calories burned, between different apps and devices and use your favorite app to view all the information.

HBO Max is finally here, all while unlimited cellular data plans have never been more available. The two seem like a perfect pair, but you might find that you can't binge "Friends" or "Westworld" on the go. At least, not without downloading episodes beforehand. Fortunately, there's an easy way to fix that.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

One of the great things about Google Fit is how it gives you a central hub for all the fitness-related data in both your personal life and workouts. You can track the steps you take, log your heart rate measurements, or even record your sleeping habits. The easier it is to access this data, the more useful Google Fit becomes.

Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

Less than a month after launching its augmented reality Swim Goggles, wearables startup Form is preparing to add a major new feature for aquatic athletes.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Did you know that the YouTube app can tell you how much time you've spent watching videos? If you're like me, you'll be surprised to know exactly how much of your life is spent inside the popular app. You can get a specific breakdown of how much you YouTube you consume.

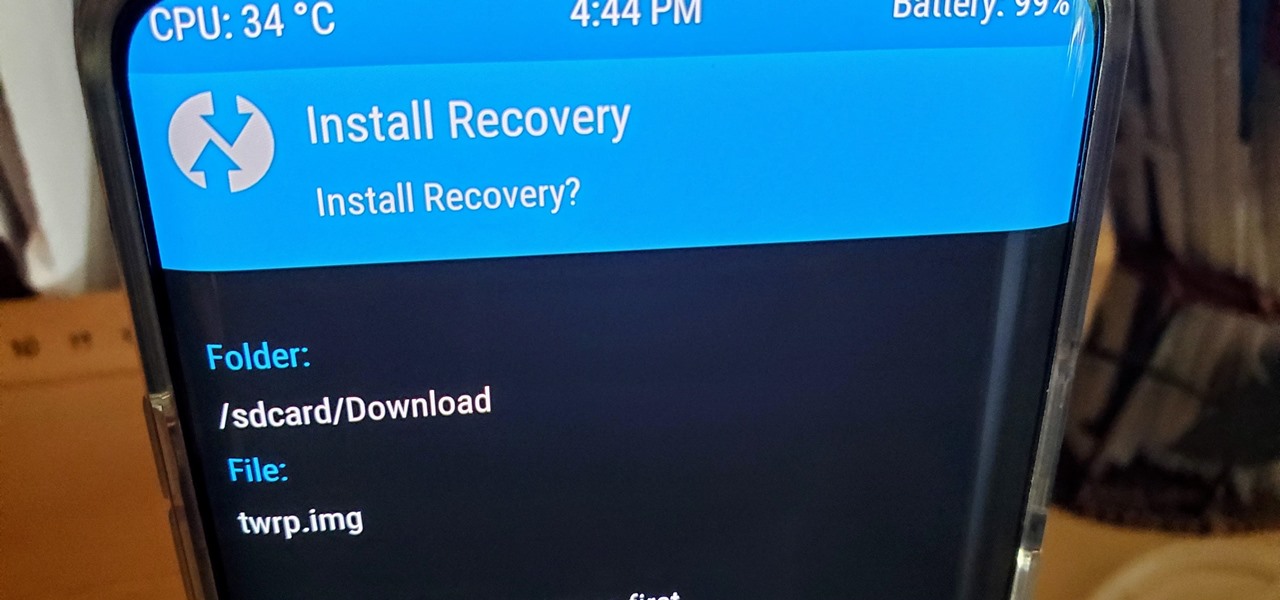
When it comes to modding your Android device, you'll want to be familiar with the TWRP name and what it stands for. It's a tool that you'll be using to make NANDroid backups or to install just about any mod file you can think of — the number of uses is quite awesome. You'll mostly be after Magisk for root access and potentially a custom kernel as well.

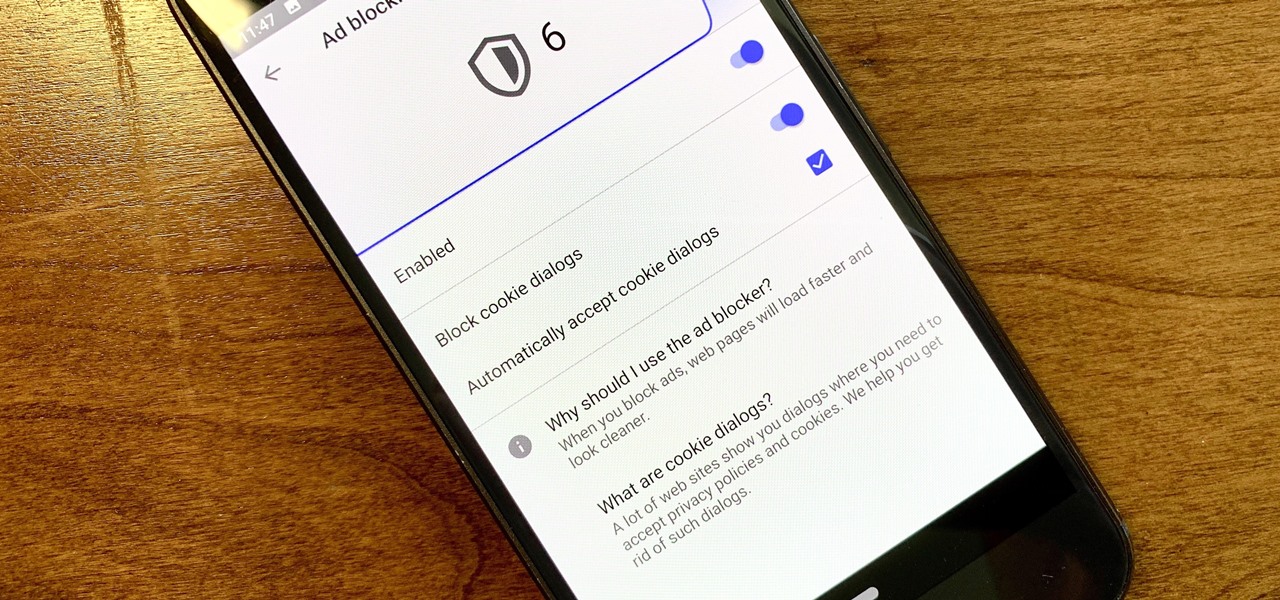
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

There are a lot of holiday tech deals starting to trickle out as Black Friday approaches. We've already rounded up some of the best deals for Android, iPhones, and headphones, but Google just dropped a big announcement for users of their Project Fi MVNO service. Now through December 17, you can earn yourself a free Moto X4 or Chromecast by referring your friends and family to Project Fi.

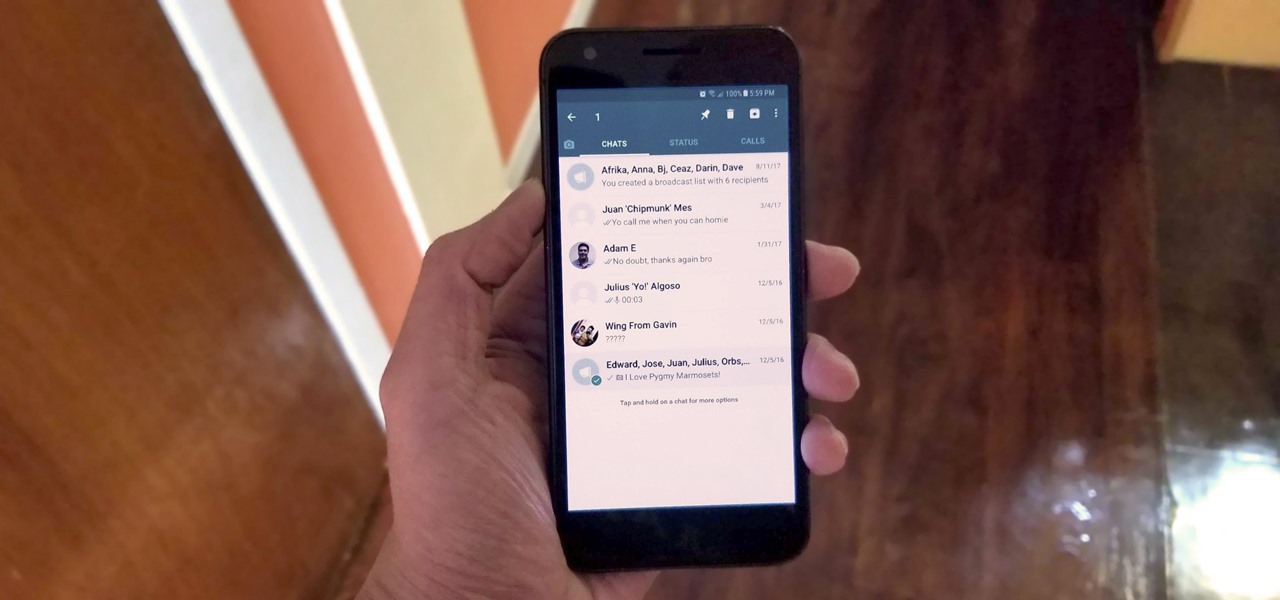
One of the downsides of living in an unprecedented age of connectivity is the near-constant bombardment of information. WhatsApp, the go-to messaging app for people the world over, is just as susceptible to buildup of useless media files, thanks to awesome features that allow us to communicate in multiple ways, such as broadcasting to friends and family. Luckily, the app makes it easy to remove old and unwanted data from your iPhone or Android.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Apple just jumped on the auto-play bandwagon with their revamped App Store in iOS 11. Now, when you visit an app or game page that has a video trailer, it will automatically play. This can not only get pretty annoying, but it can eat up your precious data. Luckily, there's a way to restrict these auto-playing videos to Wi-Fi only — or disable them altogether.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

Beijing- and Seattle-based DataMesh have announced the release of a new enterprise geared mixed reality middleware — MeshExpert. This solution for collaborative interaction with dynamic data is made up of two primary components: MeshExpert Live!, a 4K mixed reality capture system built off of the Microsoft Spectator View, and MeshExpert DataMix, which offers the ability to blend different types of data with XR and mobile hardware.

Microsoft announced yet another exciting partnership for HoloLens today — thyssenkrupp, an industrial engineering company best known for their elevators — continuing to prove how useful augmented reality is in the workplace.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

At Adobe Summit 2017 this week, Adobe announced they are looking to occupy a new space in the market by combining their analytic capabilities with augmented reality. Teaming up with Microsoft, the company has combined Adobe Sensei software with the HoloLens, reports GeekWire. Together, the tech and software create a new tool for retailers to track their consumers' habits.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Cancer is a complicated illness, but the more we understand it, the likelier we are to beat it. The 3D Visualisation Aesthetics Lab at the University of New South Wales took to virtual reality to help improve our odds by allowing scientists to walk through virtual representations of actual cancer cells.

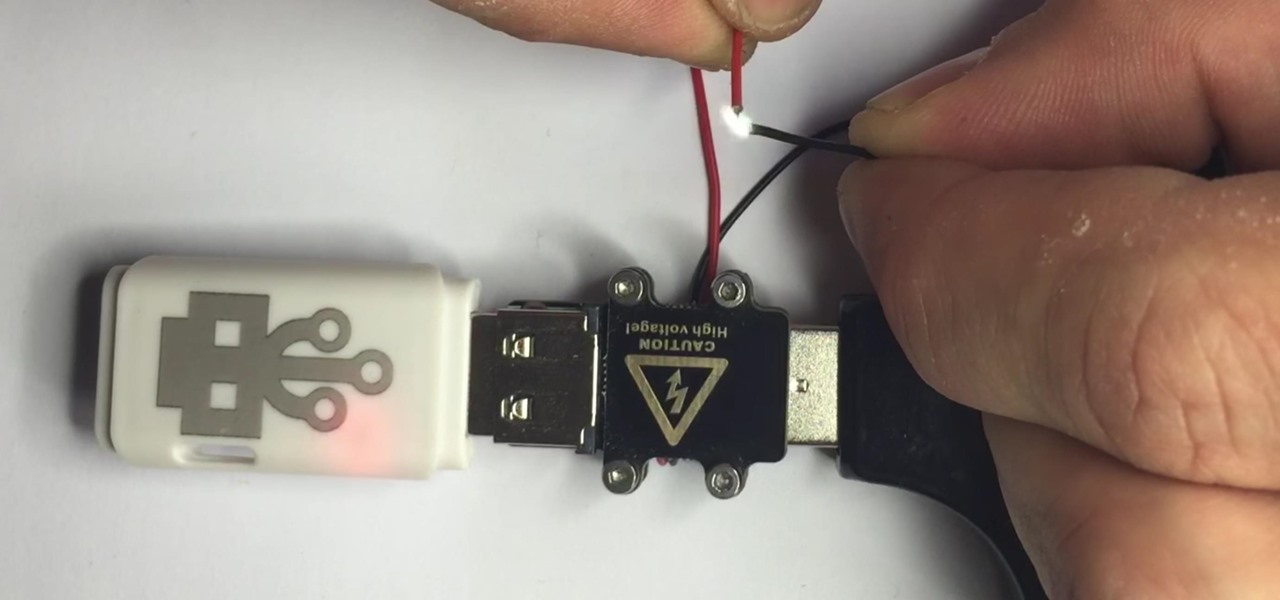
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.

Complex games in mixed reality require a pretty detailed scan of the room, and getting this process right can be both time-consuming and annoying. Computer science students at the University of Washington decided to fix that by turning it into a game.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.