Outlook is one of those applications that has 100 ways to do the same task. Today I’m going to show you how to automatically extract data from an email and have it populate fields in various modules in outlook (Contacts, Tasks, Calendar)

Watch this software tutorial video to learn how to use HijackThis to find malware hiding in the alternate data stream. This how-to video will make finding hidden malware easy and help you protect your computer.

Look at this video tutorial to see how to remove viruses from your computer if you live in Charlotte, or anywhere else in the world. This will help you remove viruses from your computer yourself, without paying mega bucks to get it fixed. You'll see how to get a free virus scanner, for virus removal. This could take up to an hour or two, depending upon the data information on your PC.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.
In this episode I show you a few of the innumerable uses of Quicksilver. Quicksilver is an unified, extensible interface for working with applications, contacts, music, and other data. The possibilities are endless. These are just a few of the ways that I use Quicksilver on a daily basis.

How to change the alignment of headings in Open Office Calc to fit all your data onto one page.

Larry Jordan explains the advantages and trade-offs of various external drive solutions, compares data rates or FireWire drives vs. SATA drives, what solutions work the best and how to avoid clogging your Final Cut Pro workflow.

Cells in Numbers '08 are the same as in Excel. Basically, they are where you store your data. This tutorial will show you how to use the different functions of cells.

A spreadsheet software wouldn't be much good if you couldn't use formulas and functions on your data. This tutorial goes over how to use them in Numbers '08.

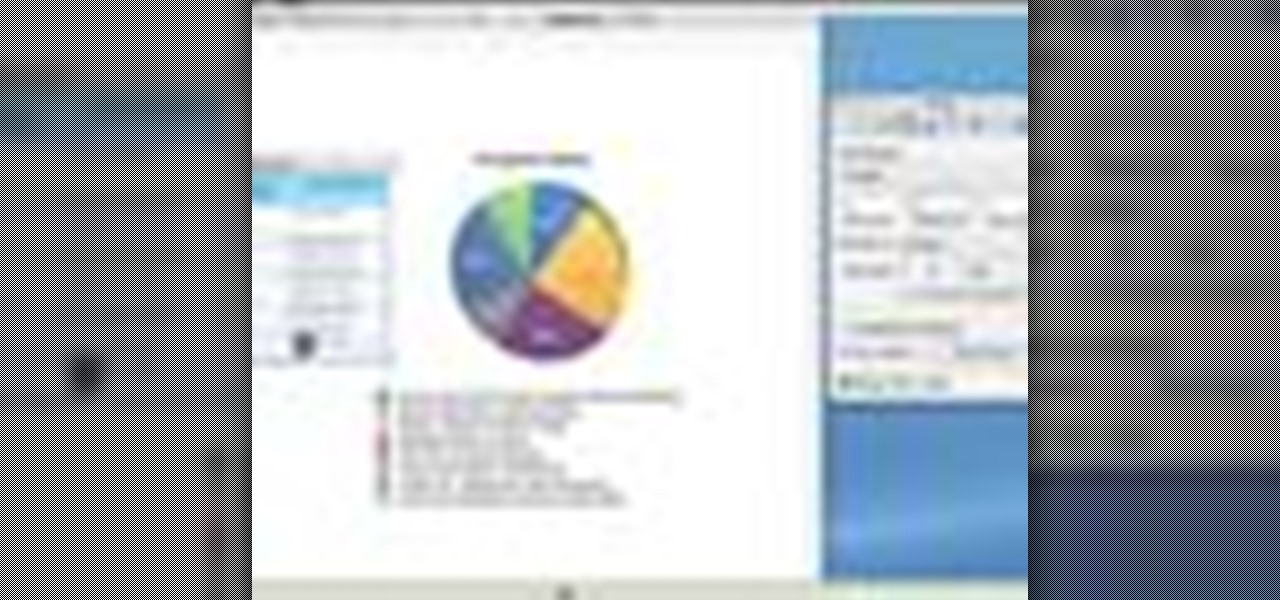
It's often best to use a graphical representation of the data you've assembled or calculated. This tutorial shows you how to create charts to visually show your results.

In Numbers '08 you can enter data dynamically with interactive buttons and sliders known as cell controls. This tutorial goes over using check boxes and sliders.

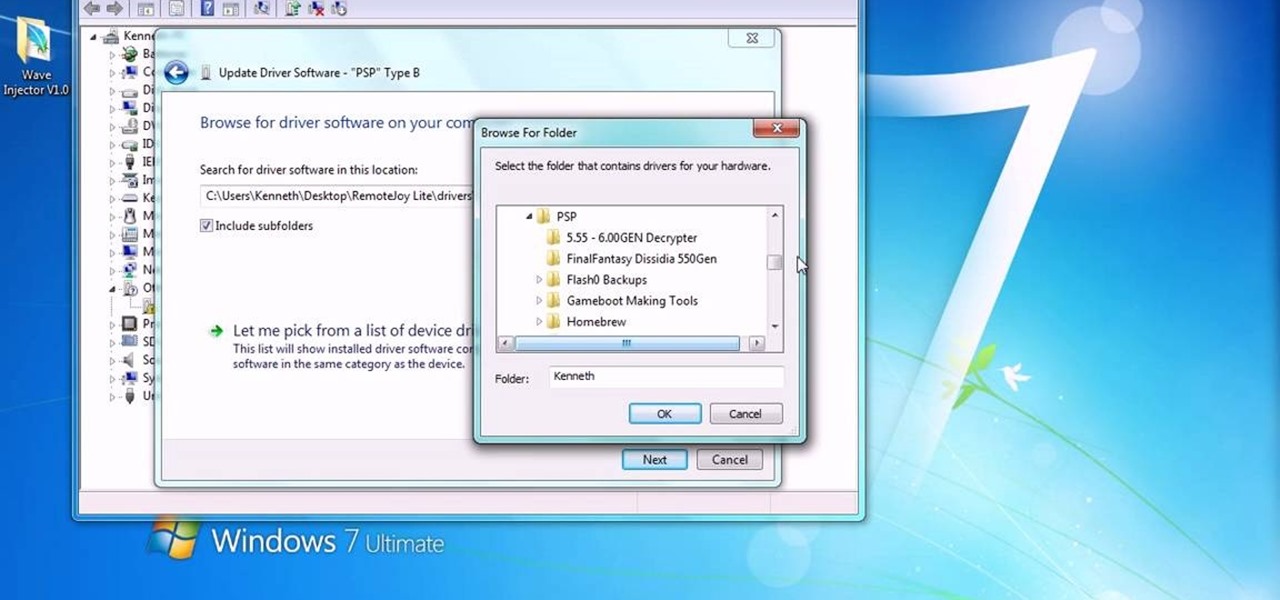
You can install Remotejoy on Windows vista/7 64-Bit. First turn on your computer and press the F8 button during the startup and disable the driver signature enforcement in advance boot option. Now download the Remotejoy and

Charles M., an attorney and bonsai cultivator, demonstrates how to transfer a field grown Japanese Black Pine that is ready for training. A 5-gallong nursery specimen was purchased and planted in the ground with a bonsai compound soil to keep its roots close and compact during trunk thickening. The tree was allowed to grow for three years, with the main foliage under four feet, but with two “sacrifice” branches allowed to shoot out without trimming. One sacrifice branch at the top of the tree...

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

The photos and videos you take with your iPhone contain bits of information, known as metadata, including the location where they were taken. This metadata makes it easier for Photos to organize your media, but put these photos and videos in the wrong hands and anyone can find out where you live or work. Luckily, iOS 13 makes it easy to wipe the geotag from images and videos before sharing.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

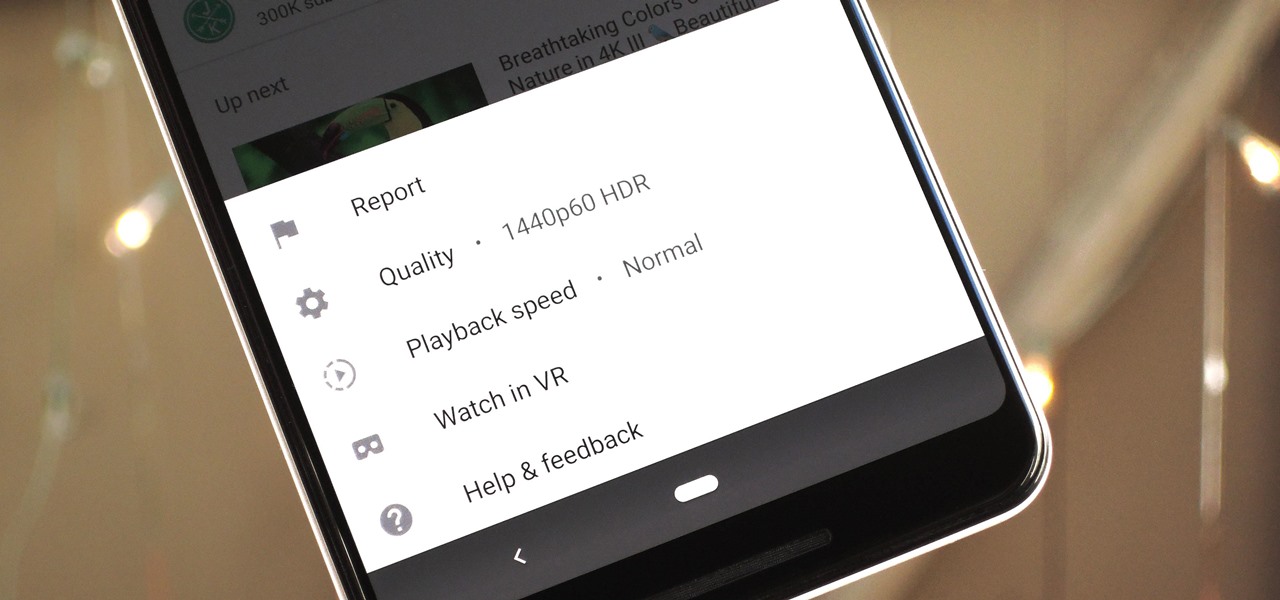
The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

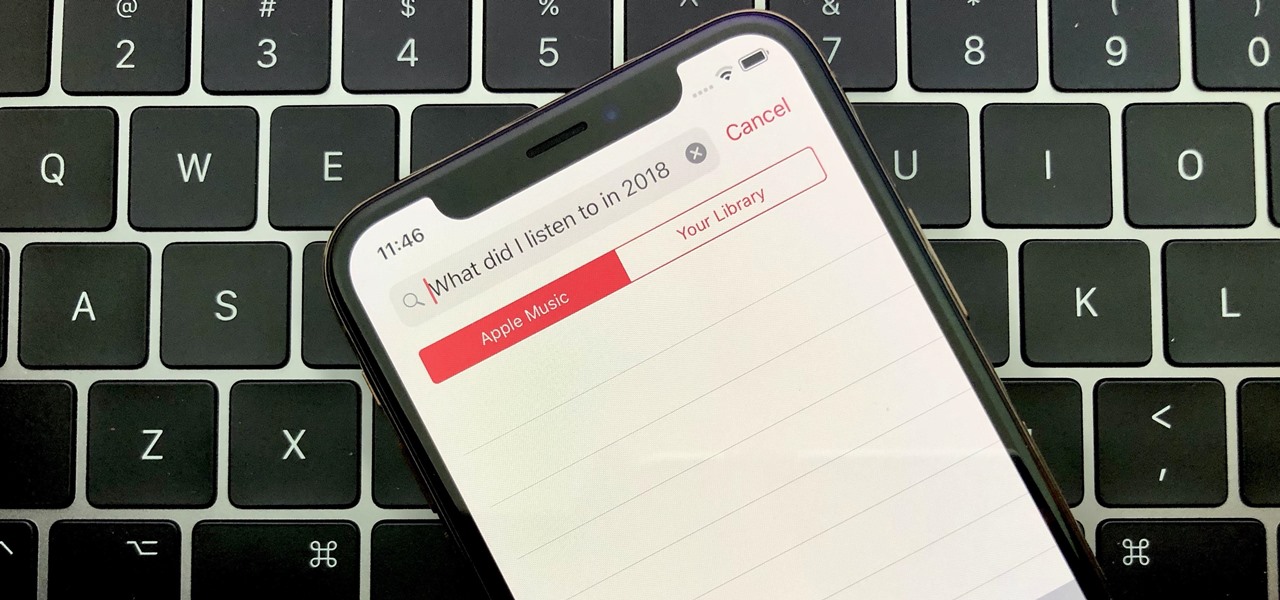
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

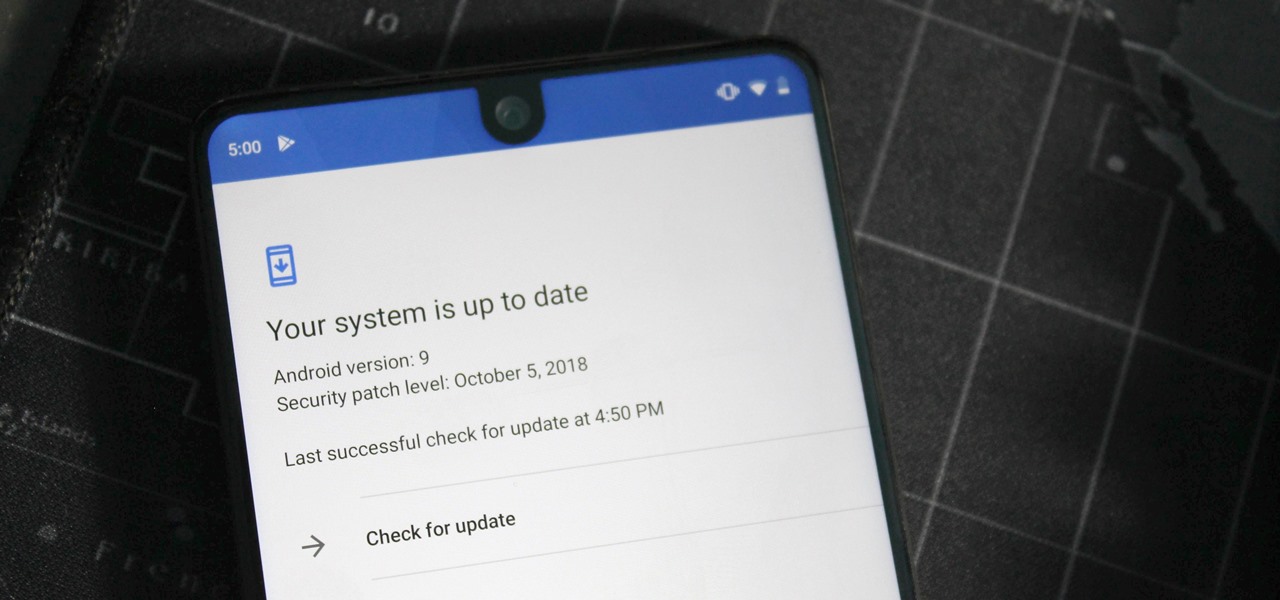
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

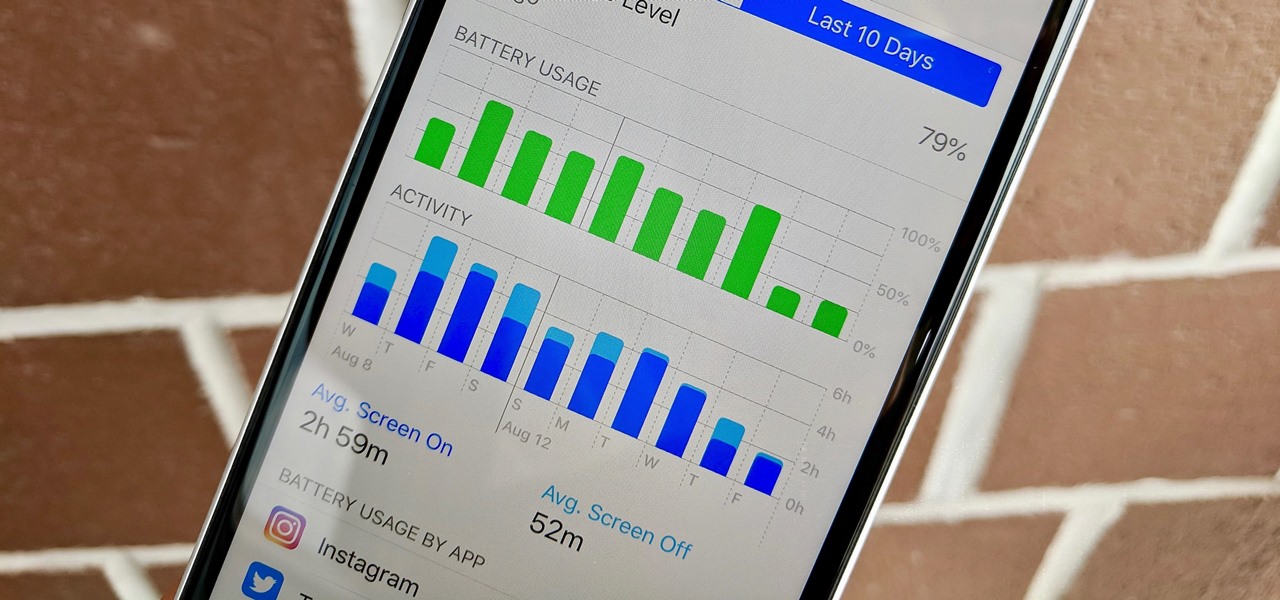
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

While having no internet connection is definitely a bad thing when you need it, you can at least bide your time until you're back online with a hidden Easter egg inside of the Google Chrome browser. This gem unlocks a secret side-scrolling game that can keep you busy during your downtime.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Apple Maps. For years now, its reputation has been that of a punchline. Although Apple and Google battle for supremacy in most hardware and software categories, in the map game there's no question who has the superior app. But the news of the day shows Apple expanding the cities it plans on collecting street data from, opening up speculation that they're not ready to throw in the towel on Apple Maps.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.