According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.
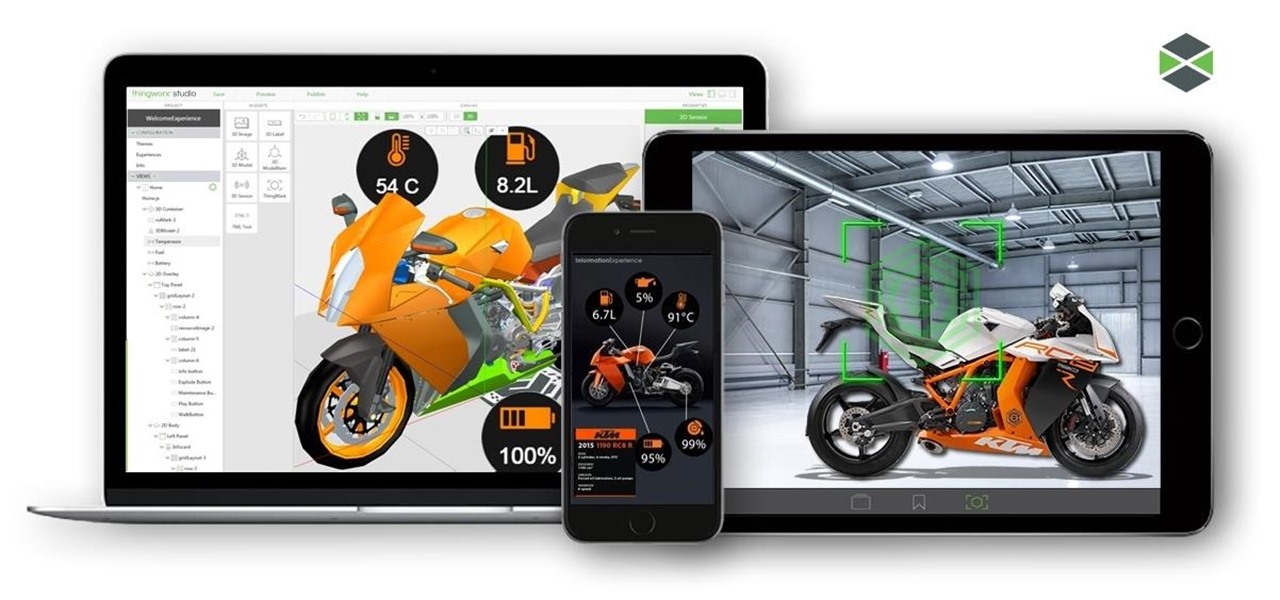
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

As if being pregnant did not come with enough worry, a new study found that certain antibiotics are linked to an increased risk of spontaneous abortion, or miscarriage — a terrifying finding for any expectant mother.
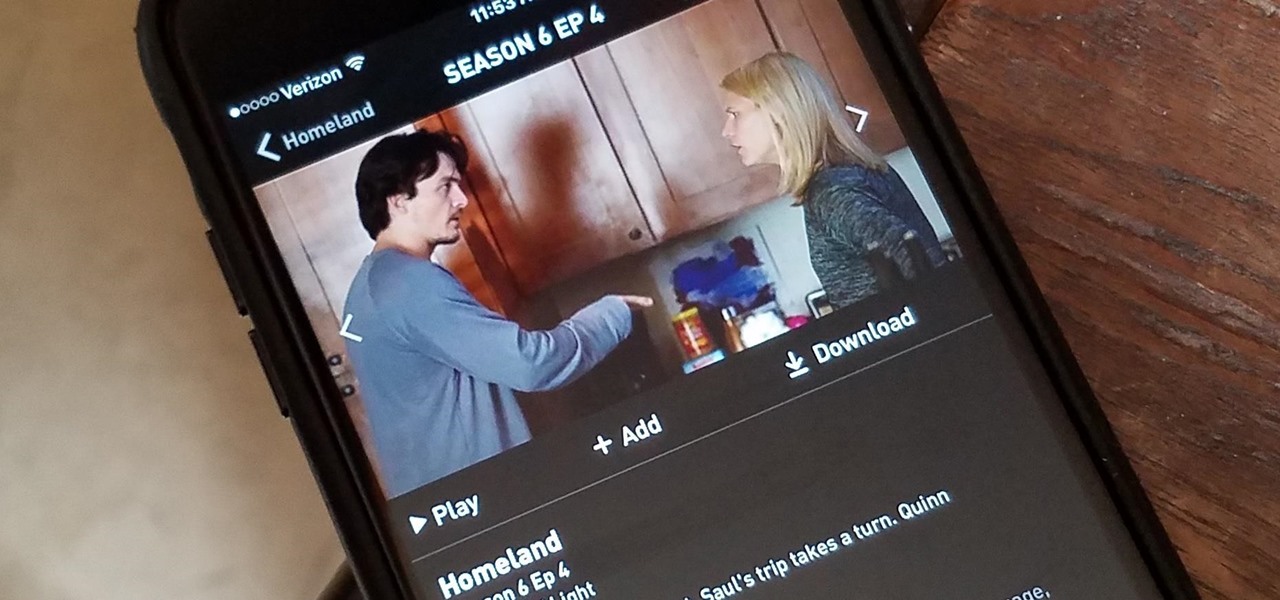
Have you ever wanted to catch up on Homeland or Shameless, but are out and about and don't want to use up your data? Those problems are for days of old now, as Showtime has announced their mobile app will allow titles to be downloaded and viewed without an internet connection.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Lenovo announced at Tech World '16 a slew of new products, and one of them aims to upend the smartphone accessory ecosystem: Moto Mods. Moto Mods are proprietary modular add-ons developed for two new Motorola phones that were also announced in the keynote, the Moto Z and Moto Z Force. Sixteen magnetic nodes align the bottom back of the phones that connect and hold accessories, forming a case appearance. The nodes transfer both data and power at high speeds, a fact that Lenovo hammered home wi...

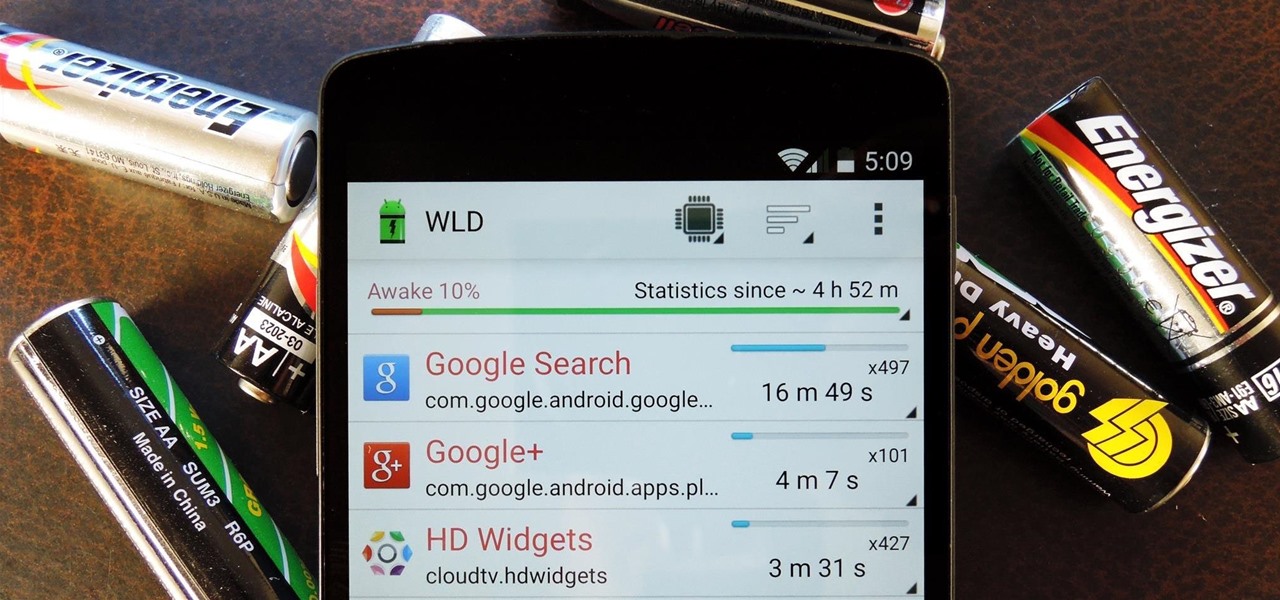
Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

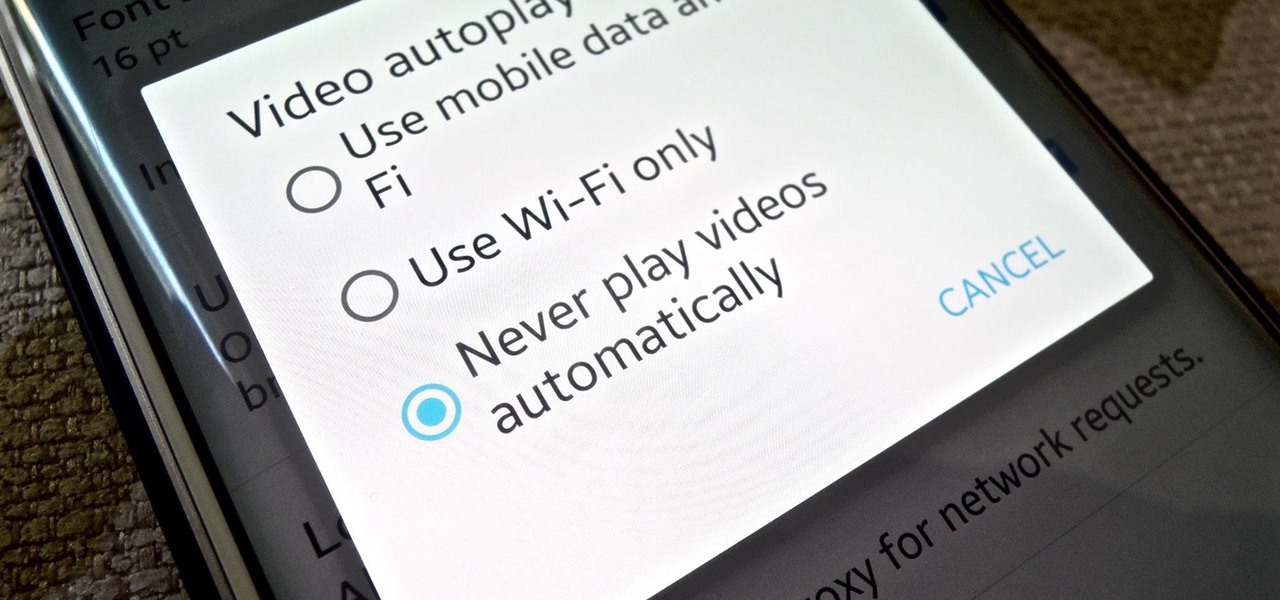
It's bad enough that we have to deal with autoplaying video advertisements all over the Web, so why do we have to be subjected to autoplaying videos on Twitter, too? Autoplay video are muted by default, but that doesn't make them any less annoying, especially if you have a small data plan on your phone.

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

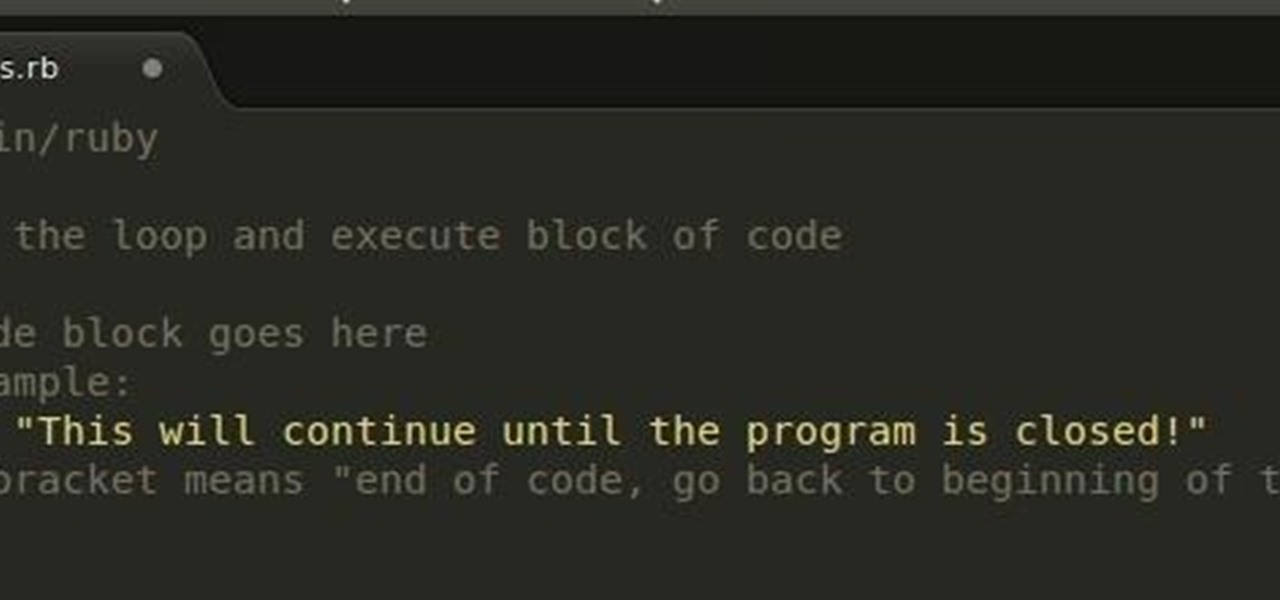
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

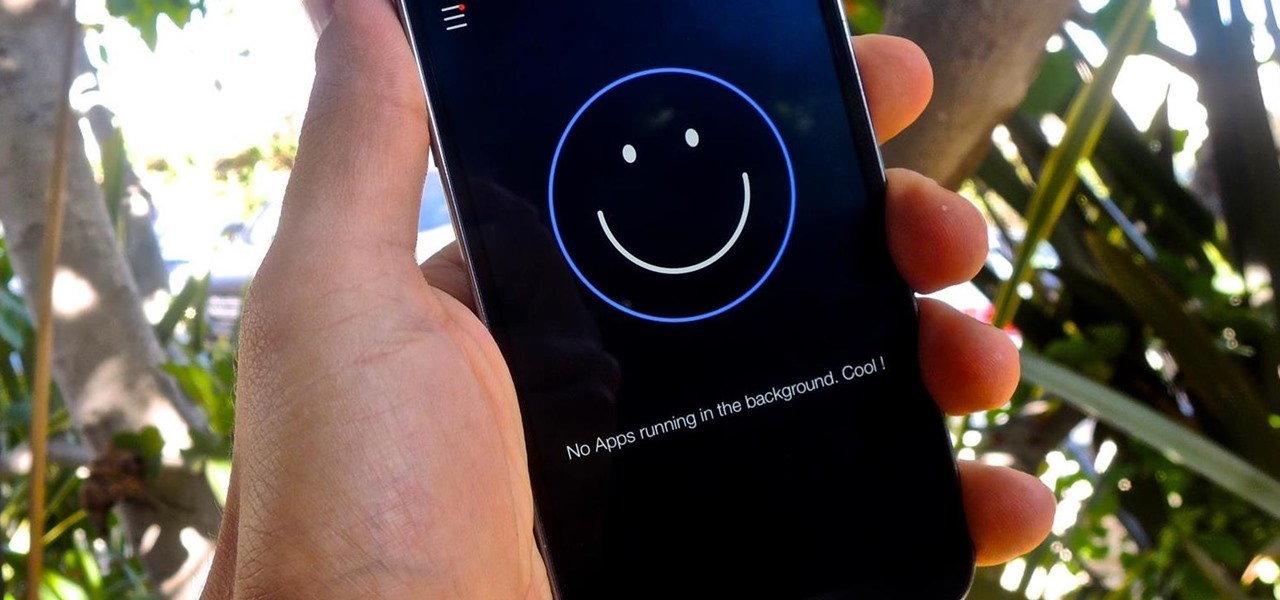
Contrary to what you may think, clearing or swiping away apps in the Recent Apps view on your Android device does not necessarily stop app activity or running tasks—and these running processes can actually be eating away at your battery life. Depending on the app or process, it may only be a small percentage, but every little bit helps these days.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

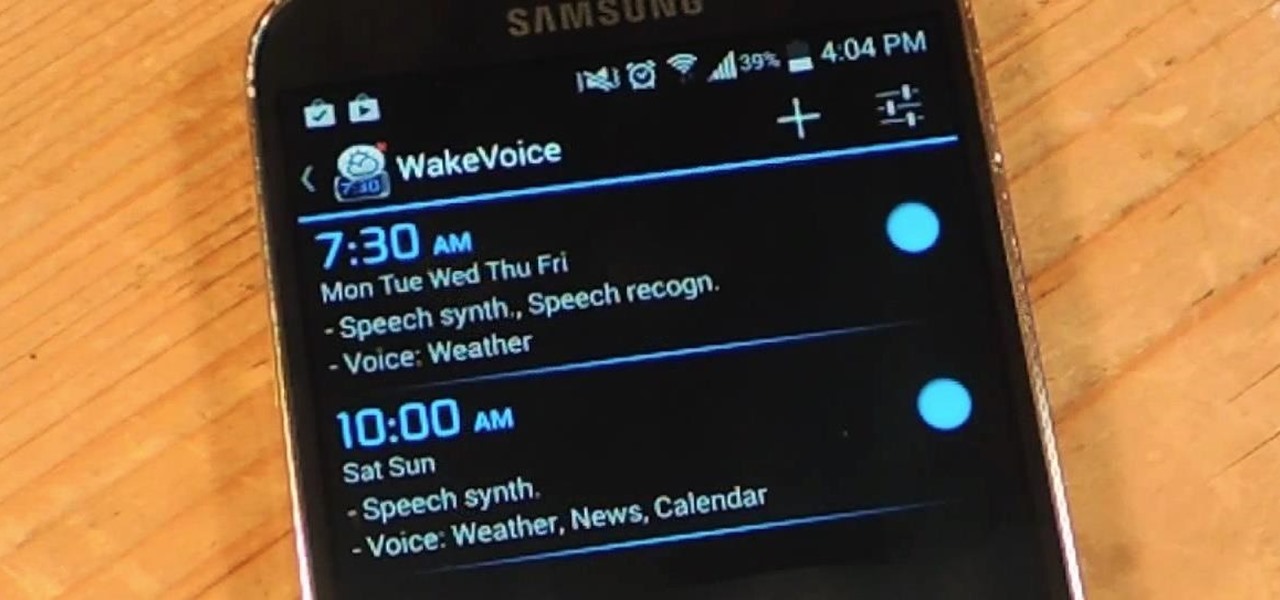
My stock alarm clock does exactly what it's supposed to—it wakes me up. But for those really tough mornings when I just need to hit the snooze, getting my head out of the sheets is a no-go. This leads to trying to find my phone with an outstretched arm, which means knocked-over water glasses and my phone falling under my bed—even more out of reach. Ugh!

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

For $100 each year (unless you used Faisal's workaround to save yourself twenty bucks), Amazon Prime membership gives you access to all the best that Amazon has to offer. From free 2-day shipping to Prime Instant Video, there's a lot to like about the service.

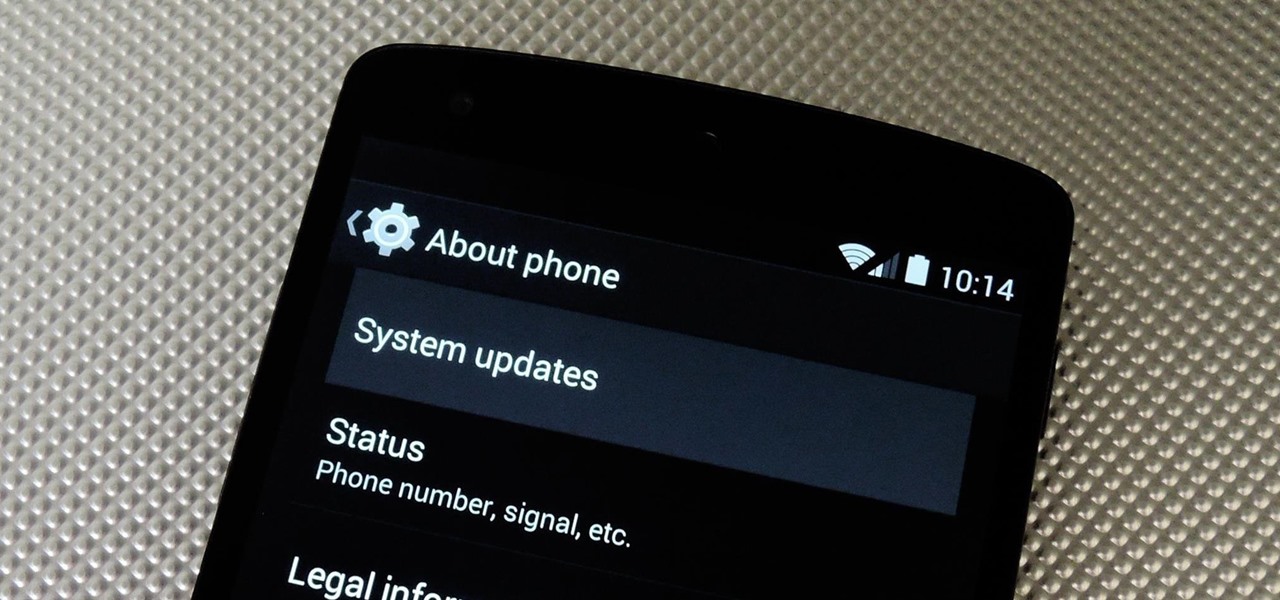
According to T-Mobile's website, an Android version bump is due out today. While details of specific changes are sparse, the support documentation for Nexus devices very clearly notes a release date of June 2nd for the software. Sprint may have jumped the gun with its own outing of a 4.4.3 update about a month ago, but all indications point towards today's date marking the beginning of a staged-rollout from Google.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

An average of 140,000 hard drives crash in the United States each week, according to online backup service Mozy. Additionally, 70 percent of Americans have lost a laptop, smartphone, or tablet, and the average person now loses 1.24 devices each year—less than half of which are ever recovered.

With the Xperia Z release for most major U.S. carriers expected sometime very shortly, many are both excited and curious at Sony's new flagship device. Much of the hype surrounding the new smartphone has stemmed from several ads that Sony has released, touting their waterproof phone to be as innovative as their Trinitron, PlayStation, and Walkman brands. Your worries about dropping your phone in a tiny fishbowl are finally over.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

If you use Facebook's Messenger app on your iPhone, your cell phone bill might just get a little cheaper. After recently adding voice chats to Messenger, the company just rolled out its new Free Call feature on the latest version of the iOS app, which allows users to make calls over Wi-Fi or a cellular data connection. The feature only works between two people who are both using the latest version of Messenger and is not yet available on the Android app. Facebook says it "will be rolling out ...

How much time do you spend outside, as opposed to inside? Whether it's because you're working, studying or just have a bunch of errands to run, it may seem like the majority of your day is spent indoors. Ever wondered exactly how much time you spend indoors and outdoors? Now you can, thanks to this DIY Arduino-powered tracking device by Instructables user Gramsky.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

Rockets will always be cool no matter what age you are, and building your own rocket is even better. If you have an iPhone that you aren't afraid to blast off into the sky, then you can try and build your own iPhone Rocket to record and analyze flight data, like Byte Works did. The list of parts is a little hefty, but their blog provides you with all of the information you need to make sure you have everything. The most important thing you need is the sensor tag, so that you can record the am...

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.