You know how it goes - every year they've got new and better technology available and you're left wondering how you're going to afford it. You could always sell your current stuff, of course, but how do you sell your iPhone without selling all your friends' information? In this video you'll learn how to reset your iPhone to wipe its SIM card which will also delete your contacts from it. If you're feeling extra paranoid, you can even go ahead and remove the from the phone. Now all you have to ...
Twitter has consumed the world, so make sure you're up to date on your Tweets. One way to do that is with Gwibber 2.0 on Ubuntu Linux, the computer operating system that could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to retrieve unlimited tweets with Gwibber 2.0 on Ubuntu Linux.
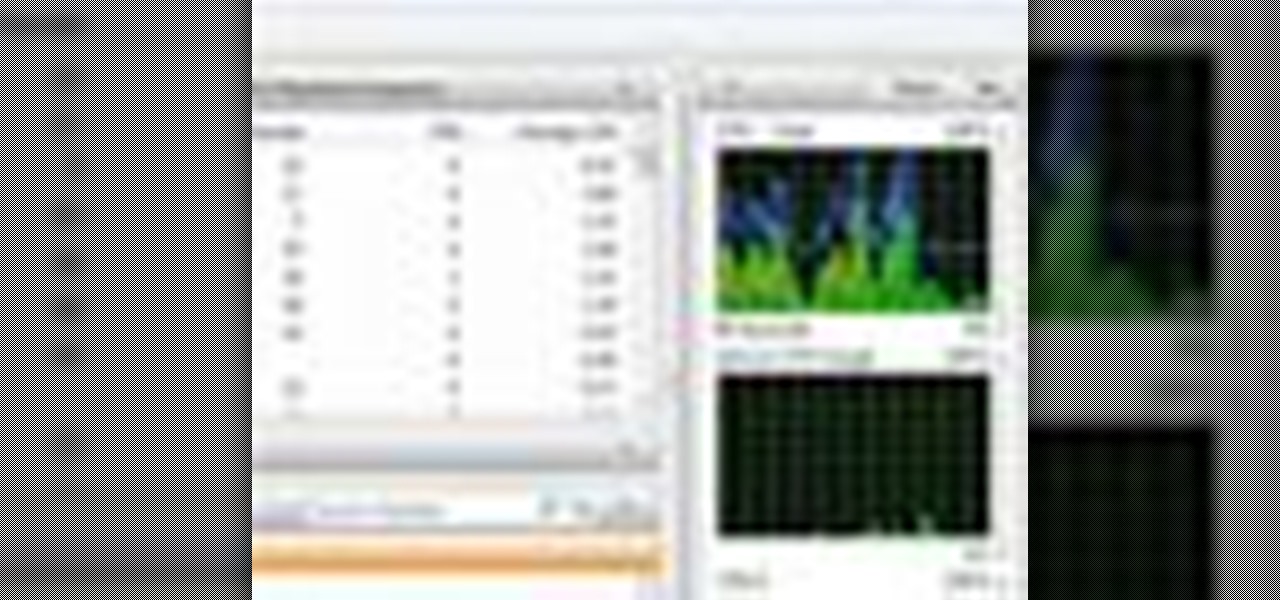
Windows users probably remember the system resource tab in the task manager which showed you your resource usage. Well, in Windows 7, this feature has been revamped. This tool will give you real-time reports for CPU, disk, network, and memory usage.
Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!

This video tutorial shows how to get MMS on iPhone 3G for Tmobile on 3.0 or 3.0.1. Not that this works on T-Mobile's Network ONLY
Create a black brute with changing cloth on http://tobeburtan.mybrute.com. Before you start you will need to have 1: Monzilla firefox 2: Temper data.

MAKE brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

Notorious hacker Chris Tarnovsky opens his underground laboratory to WIRED, providing a peek into the world of satellite television smart-card hacking. This complicated process involves nail polish, a pin head and various acids -- so don't try this at home (unless you're Chris Tarnovsky)! Chances are you won't even know what's going on here, but that's not going to stop you from watching this video tutorial on how to reverse-engineer a satellite TV smart card, is it?

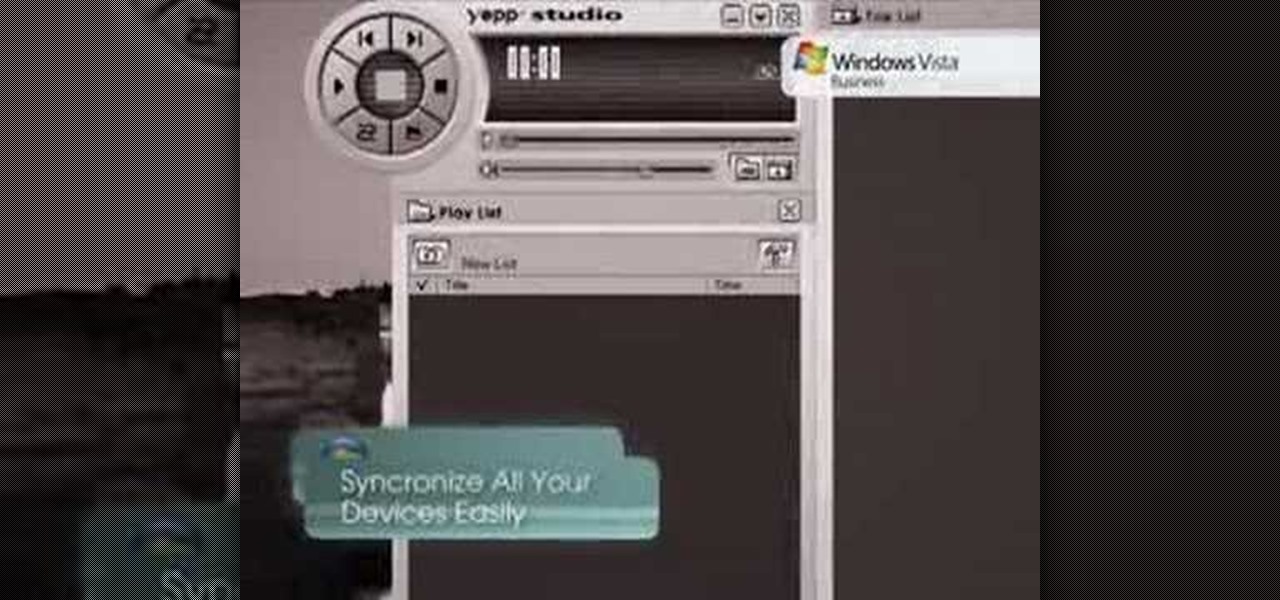
PCs are quickly becoming the center of our digital universe. With PDAs, cell phones, portable media players and other electronic devices; keeping your content synchronized has been a challenge. With the new feature, Windows® Sync Center in Windows Vista™, you now have a single place to keep all of your devices and information up to date. For detailed instructions on using Sync Center for your own data syncing needs, watch this how-to.

This image editing software tutorial covers resampling an image down to an optimal print size in Photoshop CS3 so you can bring it to a lab for printing. It's nice to take pictures as large as possible, but it's not always so easy to get that data out of your computer and into print. If you don't have a nice photo printer at home and need to transfer your images, you may want to watch this video and learn how to resample them down to a good print size in Photoshop CS3.

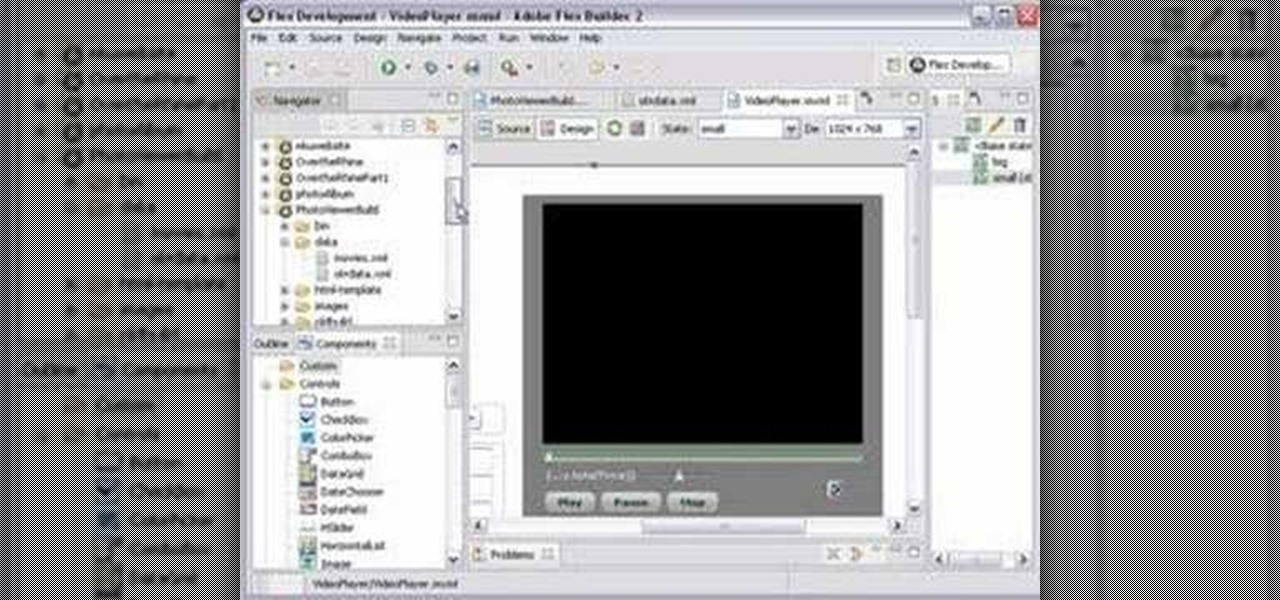
This is a simple Adobe Flex Photo Viewer. It uses a number of techniques that are not found in any one place in the literature - data shorting, tile repeater, xml http services, inline mxml actionscripting, click on double functions, use of CDATA Tags, tooltip, glow and fade effects - all done in less than 100 lines of code (once you take out the blank lines). This was created by Mike Lively Director of Instructional Design at Northern Kentucky University for the Over The Rhine project.

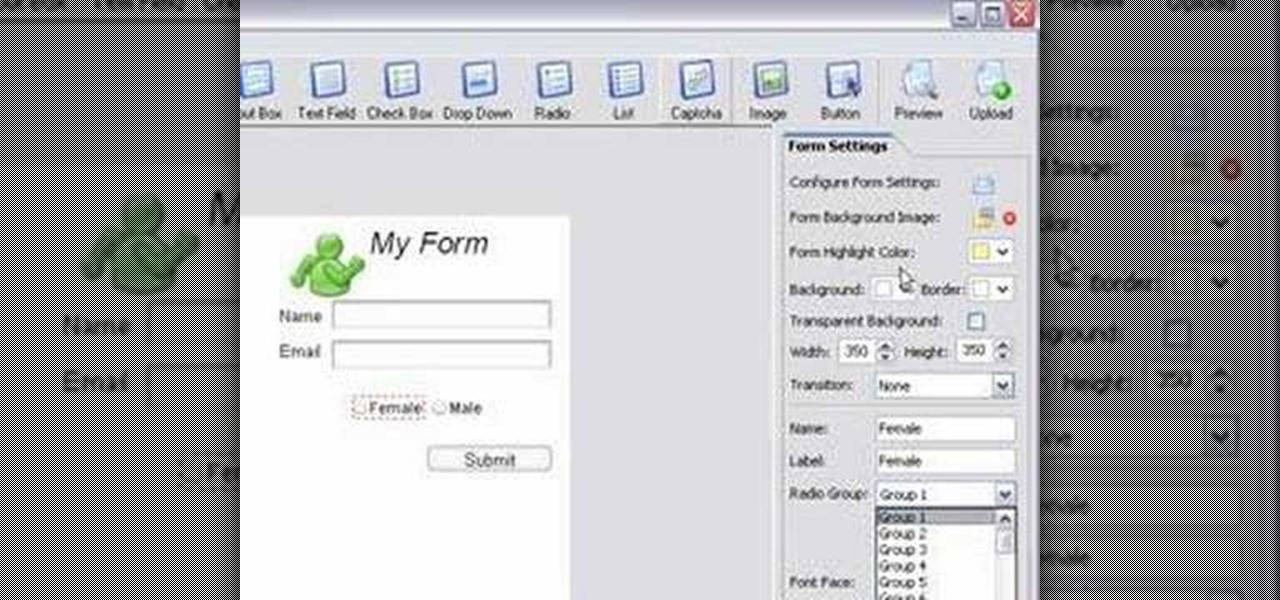
If you want to submit information to a user, you build a website; if you want to receive information from that user, you use a web form. As such, it's crucial that your web forms be well designed. One easy way to design web forms is with CoffeeCup's Web Form Builder.

This experiment uses a ballistic pendulum to determine the launch velocity of a metal ball. This is compared to a measurement of the launch velocity found using projectile motion. You may wish to emphasize why energy is not conserved in the initial impact of the ball into the ballistic pendulum, but momentum is, and conversely why energy is conserved as the pendulum rises but momentum is not conserved.

This video tutorial will show you how to take an old computer keyboard and use its circuitry as a physical computing input device. Once you have this device, you can then use it to interface with programs that you write using software such as pure data processing, MAX/MSP, and Ableton Live to name a few. What you are doing is replacing the switches within your keyboards with others for input devices. Make sure the interface is plugged in when you are testing but it's probably a good idea to u...

This software tutorial shows you how to set up your FTP server using Dreamweaver. FTP servers are a great way to share and transfer data, especially when it is too large for email. So if you have a website, make it easy on yourself and set up an FTP server with Dreamweaver and this tutorial.

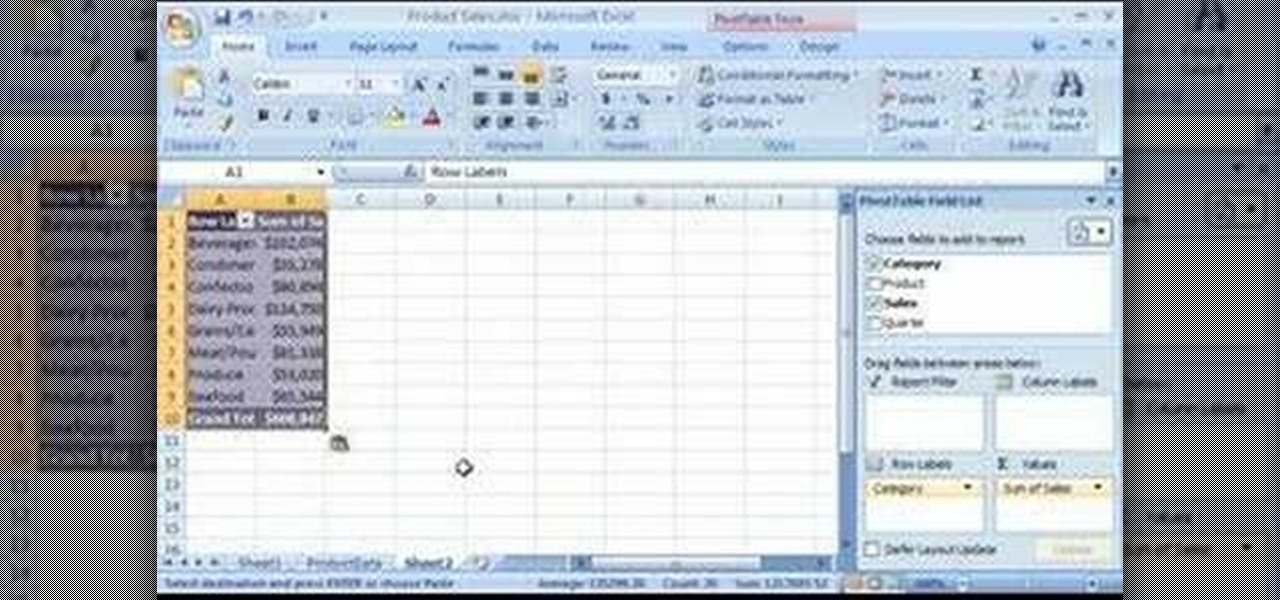
With PivotTable reports in Microsoft Office Excel 2007, your sales report will sparkle with power, flair, and functionality. Take a look at this instructional video to learn how to show the big picture, show all the details, or show anything in between. Easily create multiple worksheets to switch back and forth between the various versions of your report. Sort, filter, and summarize your data any way you like. Show the details of any summary value in your report.

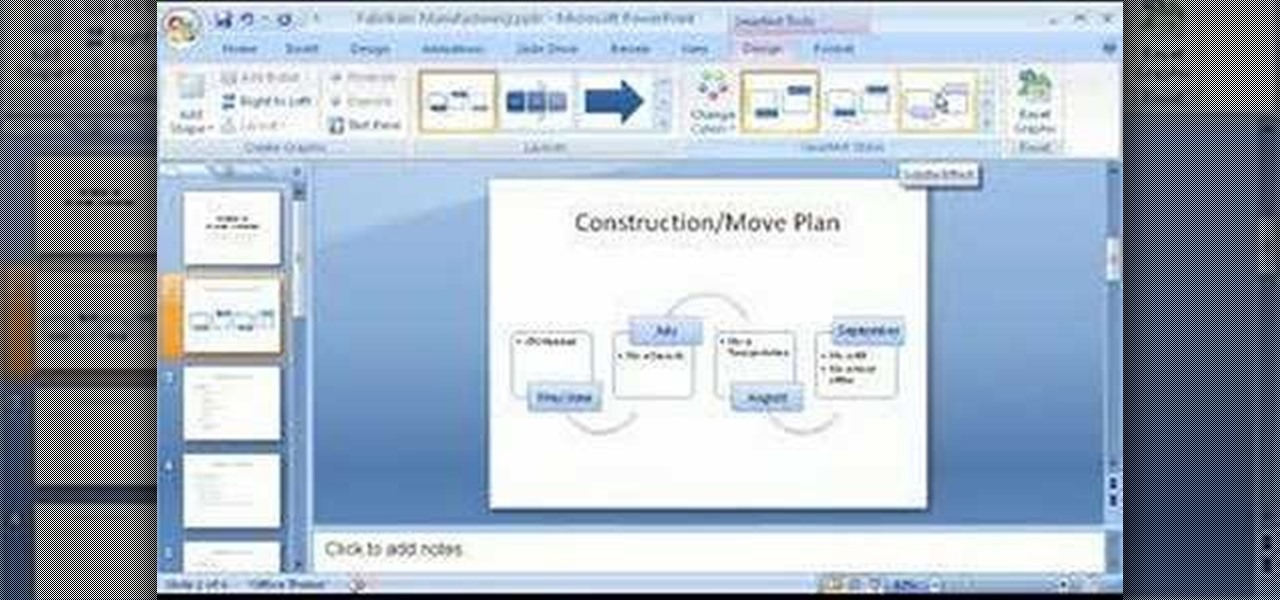
Learn how to add color, shape, and emphasis to your text and data in Microsoft SmartArt graphics in this tutorial. See which one works best for getting your point across. An organization chart? A time line? A process with sequential tasks? Non-sequential items? Pick one, and optionally customize it with colors, animation, effects such as shadows, bevels, and glows, and more.

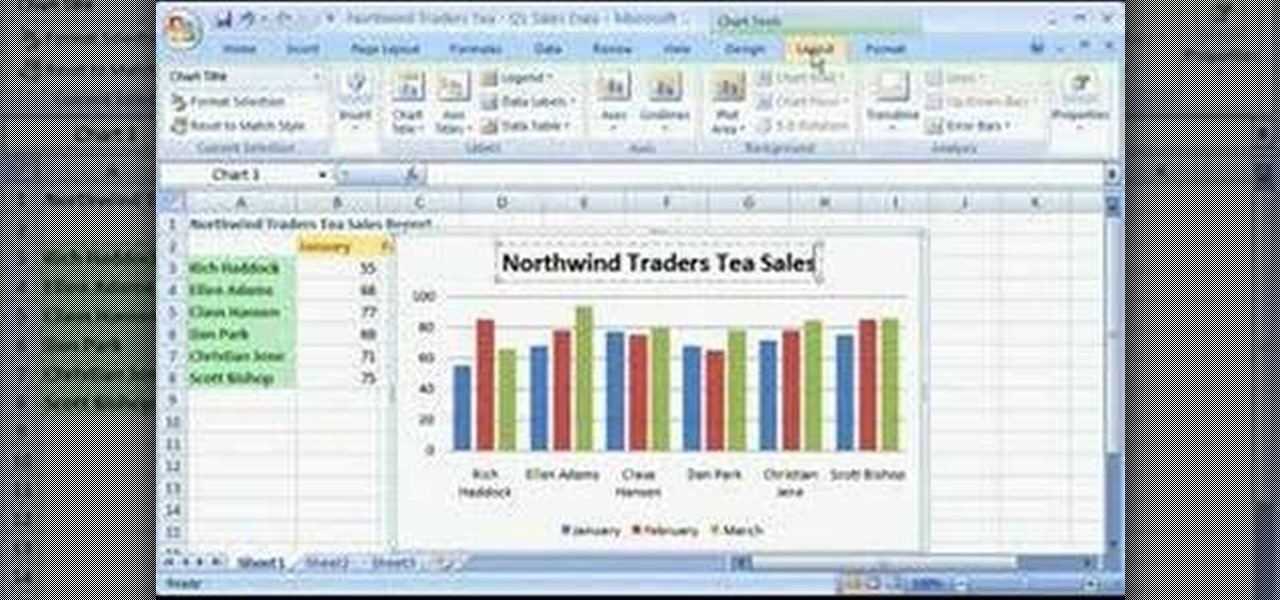
Check out this tutorial and learn how to create chars in Excel 2007. In Office Excel 2007, you just select data in your worksheet, choose a chart type that best suits your purpose, and click. Want to try a different chart type? Just click again and select a new chart type from a huge range of possibilities. Then work with the new Chart Tools to customize the design, layout, and formatting of your chart. You can see how various options would look just by pointing at them.

In this video tutorial, Chris Pels will show how to extend the standard set of ASP.NET configuration settings with your own XML configuration elements. First, see how to create a configuration section handler which is required to interpret and process the information in custom XML configuration elements. During this learn how to use declarative model for defining the behavior of a configuration section handler. Next, see how to add a custom section handler and custom elements to an ASP.NET co...

In this video tutorial, Chris Pels shows how to create a Cross Page PostBack in ASP.NET, where a control on a source page raises a PostBack event to a different target page. First, learn how to configure a Button control to PostBack to a different target page. Then, learn how to get information from controls on the source page with the PreviousPage property and the FindControl method. Then, learn how to use public properties on the source page to expose data to the target page, and learn how ...

To unlock Toon Link first go to Subspace Emissary, make sure you've completed it, if not you will not be able to unlock him until you have done so. Go to Subspace Emissary and click on the completed data with the crown and load it. Next go to "The Forest" and choose any difficulty and any characters. Now go forward and fight whatever you by until you reach a door and enter it. Now you'll see Toon Link and fight him and win. After winning you'll unlock him.

In this hands-on workshop, Googlers Mano Marks and Pamela Fox show how to use tools within Google Maps, Google Earth, and Google Spreadsheets to create, import, and edit KML. They also show a quick integration of KML in the Maps API, and briefly mention geo search and indexing. This talk is useful for developers who haven't had a chance to play with the Maps or Earth creation tools yet, and are looking for quick ways to create and share geo-data.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

Discover how After Effects redesigned Motion Tracker (After Effects Professional only) gives you more power to synchronize motion between two elements in a composited scene. Learn how Motion Tracker works by analyzing the moving pixels in each frame and then using that data to control the motion of a new layer. Set as many tracking points as you like or choose from a list of defaults. Also see how Motion Tracker's interface and controls have been simplified to be faster and easier to use.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

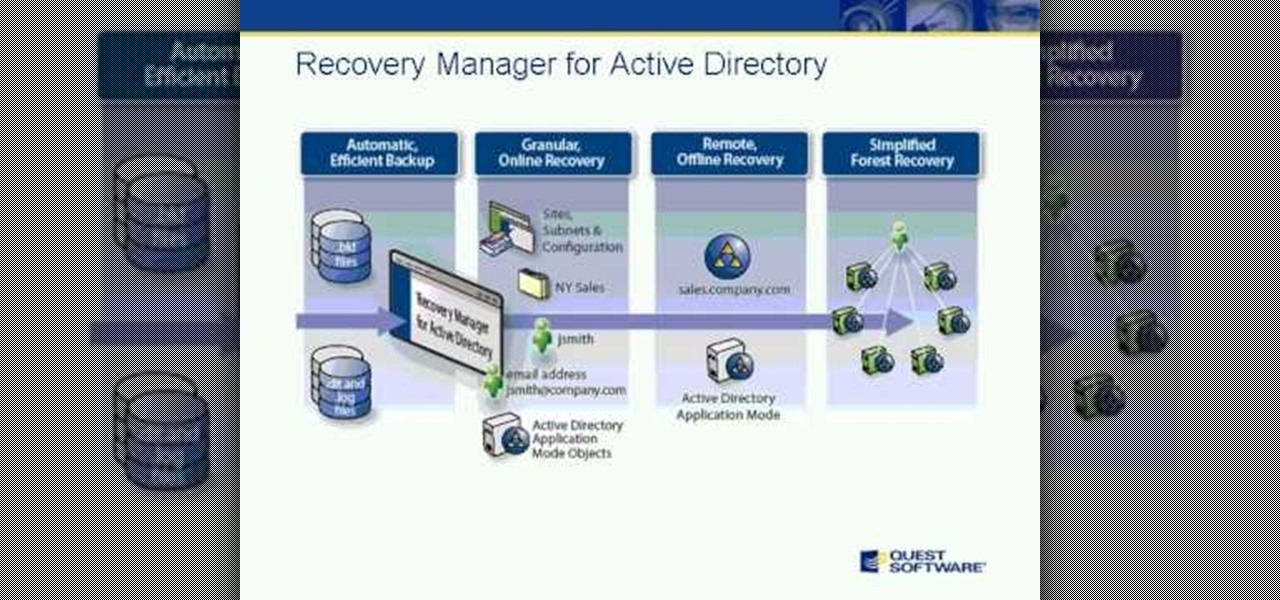
View our webcast to learn about the advantages of using a comprehensive Active Directory recovery solution -- and view a product demo. With Quest Recovery Manager for Active Directory, recovery time can be reduced from hours to minutes!

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

This how to video demonstrates how to do a non-surgical sperm recovery from the testicles using the needle aspiration biopsy method (NAB). Watch as our doctor demonstrates this procedure. This video is intended for medical professionals and medical students.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

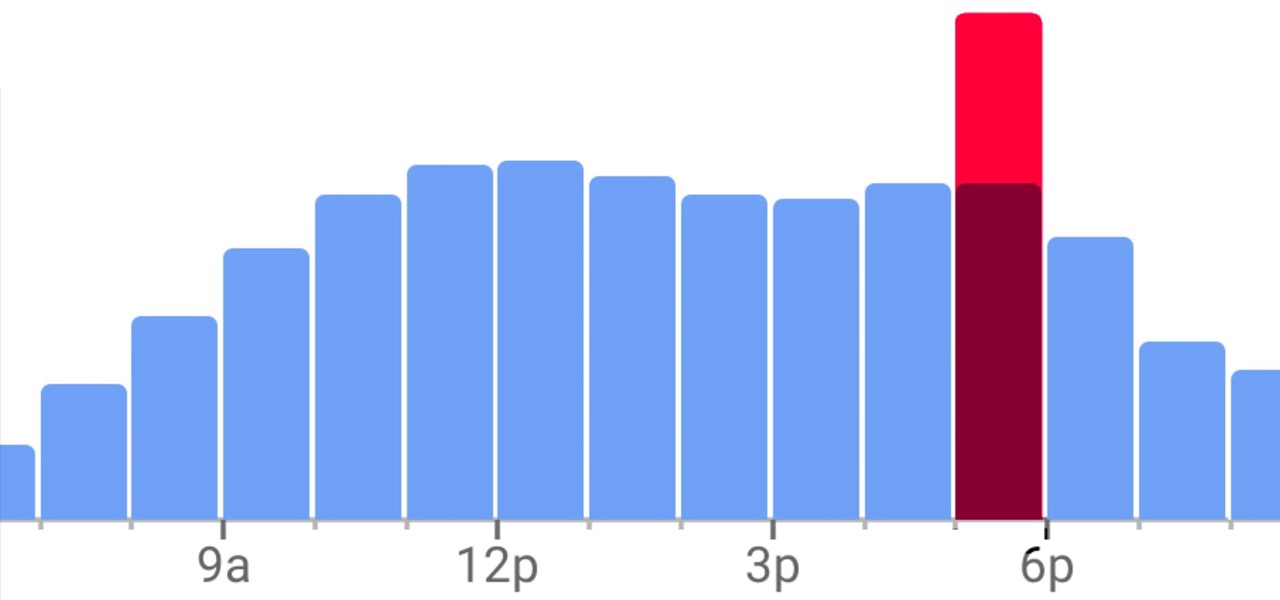
Unlike Apple Maps, Google Maps can tell you when a restaurant, bar, club, or other business you're thinking of visiting is busy. It's extremely helpful if you want to avoid peak times or wait for the place to be empty. If you can't pry yourself away from using Apple Maps, there's an easy alternative to see the popular times of most businesses.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

Fresh software updates can be amazing or a nightmare, but they're mostly the former since new and updated features can give your iPhone improved functionality. There are over 200 benefits in iOS 14 alone, and hopping on the iOS 14.2 beta includes new emojis and fresh wallpapers. For the longest time, however, being away from Wi-Fi meant no update for you. That is, until now, thanks to 5G.

We're living in a world that runs on Big Data. As the driving force behind everything from self-driving cars and Google algorithms to the latest medical technology and financial platforms, massive sets of increasingly complex data lie at the heart of today's most exciting and important innovations.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

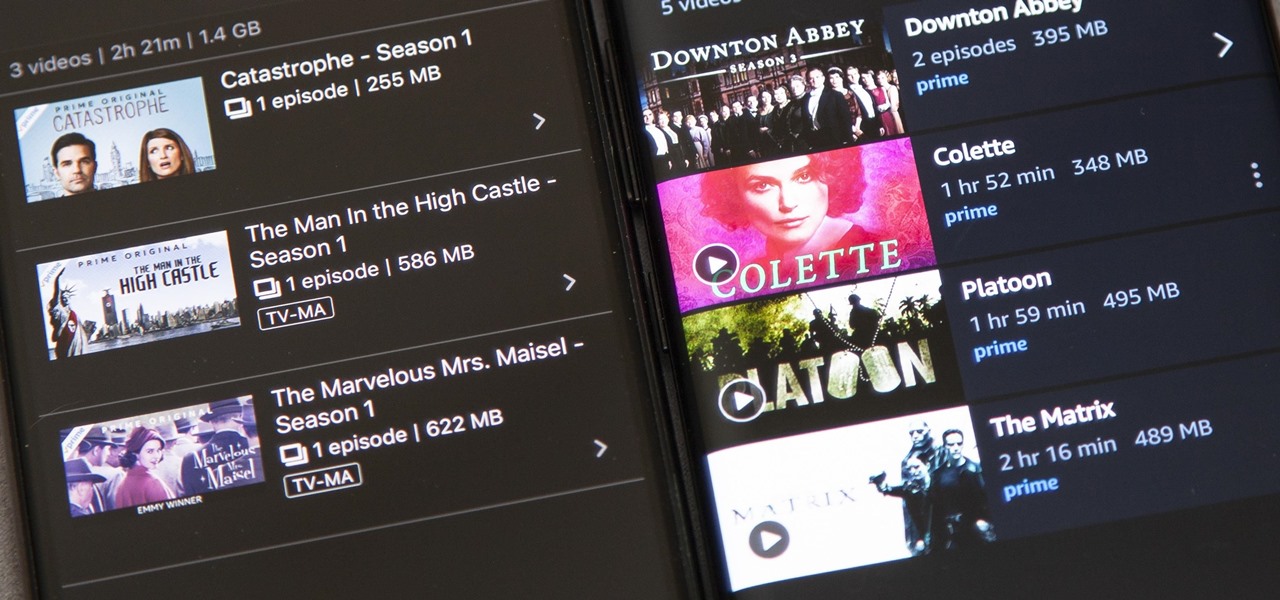
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.