Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar?

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Hello! I would like to share some data about the nests that rabbits and dwarf rabbits build. They represent good shelters for them and their babies.
Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

The video starts by informing about the basic safety precautions, tools needed and backing up data prior to hard drive replacement. There are a series of screws which need to be removed in the following order.1. Removing the battery from the back and then remove three screws thereby removing the RAM cover.2. Two more screws to be removed under the RAM cover.3. Two screws from inside front edge.4. Four screws from the bottom rear.5. Two screws each from the slim sides.6. Two screws near the hi...

How to make TCPO or bis(2,4,6-trichlorophenyl) oxalate, used in glow stick reactions. WARNING: This procedure should only be performed by, or under the direct supervision of, an experienced chemist. Please refer to the material safety data sheets of all chemicals for their hazards. Synthesis must be performed in a fumehood.

Having the Internet on your phone is definitely handy. You can look up anything at anytime, and connect with friends in so many more ways.

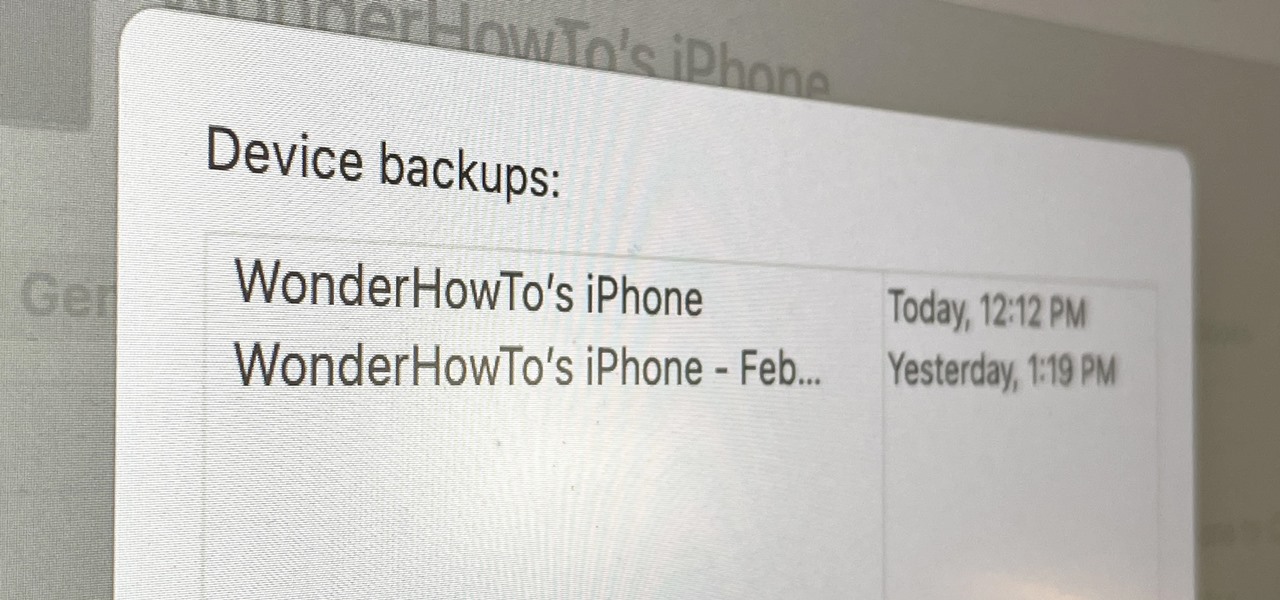
In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.

Working with Oracle, odds are you may, on occasion, need to build an Oracle database from MySQL. Happily, this DreamCoder tutorial will walk you, step by step, through the process. To learn how to build an Oracle database from MySQL data, take a look!

Pivot tables are great tools for comparing data, especially when dealing with long lists. See how to create pivot tables in Excel.

Borders and shading add aesthetic presentation to your spreadsheet data. See how to create borders and shading in Excel.

For most mainstream users, LiDAR sensors for precision depth sensing remain the exclusive domain of Apple iPhones and iPads, but Google is helping Android device makers close the depth gap on the software side via its ARCore toolkit.

If you want to try out one of Apple's beta programs on your iPhone — whether that's by becoming a developer, joining the public beta, or using an IPSW of an available beta update — there's always a possibility that you'll want to go back to the stable iOS version you were using before. Likewise, if you updated to the latest stable release but liked how iOS worked on the previous version.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

Lossless quality isn't for everyone. If you can't distinguish between lossless audio and other formats, you probably but don't need it. But if you're a musician who's sharing ideas with bandmates or a journalist interviewing people for a video, you might want the best possible quality, which is what lossless offers. And you might not know it, but the Voice Memos app on your iPhone supports it.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.