The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 97th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a data form in both Excel 2003 and 2007 as well as how to add a button to Excel's Quick Access toolbar.

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

Here, you'll be shown how to revert your Windows Vista computer back to its factory settings, if you get stuck with a bad virus or anything else like that. Make sure to back up all of your important data before you decide to go back to the original factory settings, as you don't want to lose that precious data. After a quick backup, we'll run through the options from start to finish. We will run through a few restarts of the system, and then show you the easy path to getting your system back ...

Do you want to know how to sync an iPod with the XBox 360? You must have an iPod and a XBox 360. Connect your iPod with your XBox with the USB cable. Transfer the files from the iPod to the XBox XBox helps play AAC format as well as MPEG movies. The iPod must be connected to the portable device section. This will help you share movies, music, pictures and other data and you can even copy the downloaded data to your iPod from the Xbox.
Get MMS working on iPhone 3G, iPhone 3GS, MMS on 3.1 for AT&T. Step 1 : First of all, you have to update to 3.1.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

In this screencast, we look at how changing the page style of each sheet in your spreadsheet can enable you to apply different formatting settings for each one.

You may think you know Microsoft's apps, but did you know that you could be using them as a power user and make yourself way more productive in the process? Thankfully, the easiest way to master them from home is on sale right now, as The Premium Microsoft Office & Data Apps Certification Bundle is on offer for just $39.99 — a huge 97% off the regular price of $1,782.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

There's a direct correlation between the proliferation of augmented reality apps and the demand for 3D content, and PTC just quantified that in dollars.

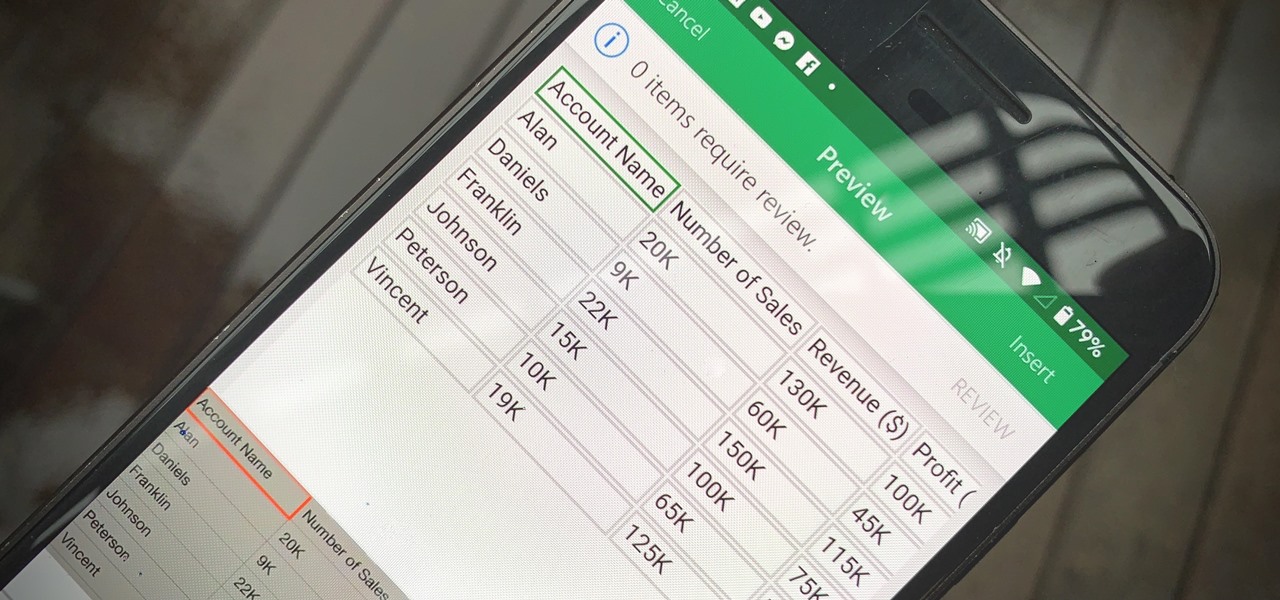
Creating a digital spreadsheet by hand can certainly be tedious, especially if you're copying a printed paper table word for word, number for number. Instead of typing information that's already there, however, use Microsoft Excel on Android or iOS to snap a photo of that printed chart and import it directly into your digital one.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Back in 2018, Spotify began testing a new mobile feature that has grown very tiresome: three to eight-second looping videos that take over the entire screen. Known as Canvases, they effectively hide the cover art and lyrics of the current song — and they're still very much around to annoy and distract the hell out of you. Thankfully, Spotify has also included a way to get rid of these things.

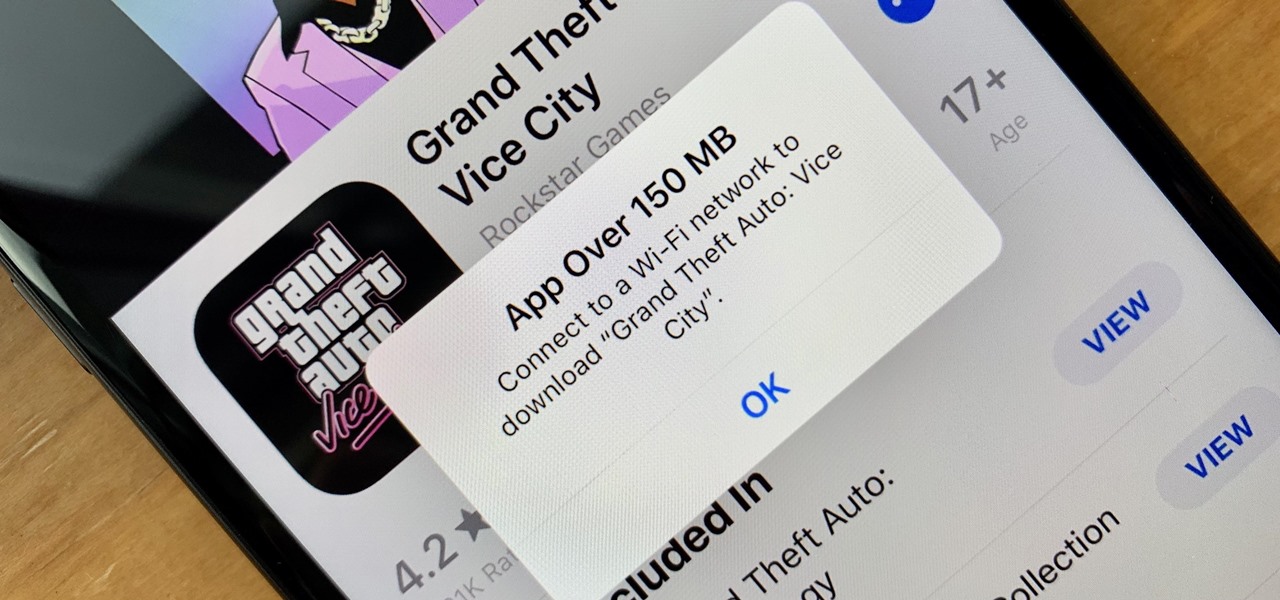
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

With so many apps being cloud-based, cached data has started to become a problem. This is particularly true if you're low on storage, so developer Dhi decided to do something about it.

When Apple revamped the storage management system in iOS 11, it built in a feature that lets you free up space on your iPhone in a more efficient manner. The option allows you to remove an app while preserving its data and documents should you choose to reinstall it later — and it can even do so automatically for unused apps when you're running out of space.

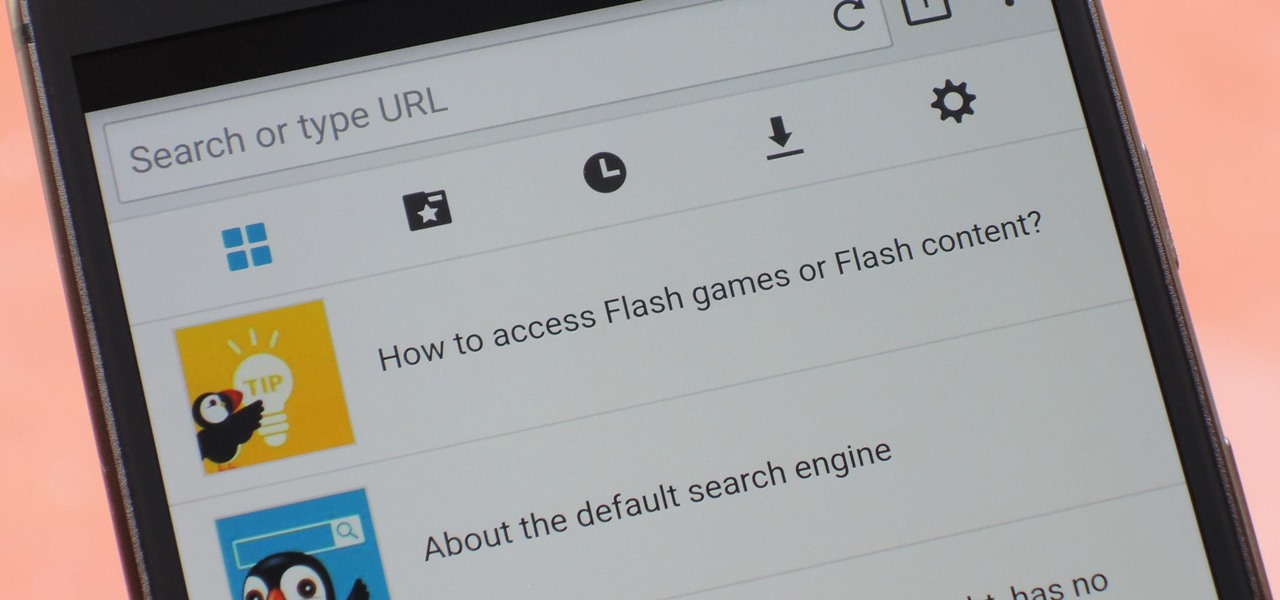
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

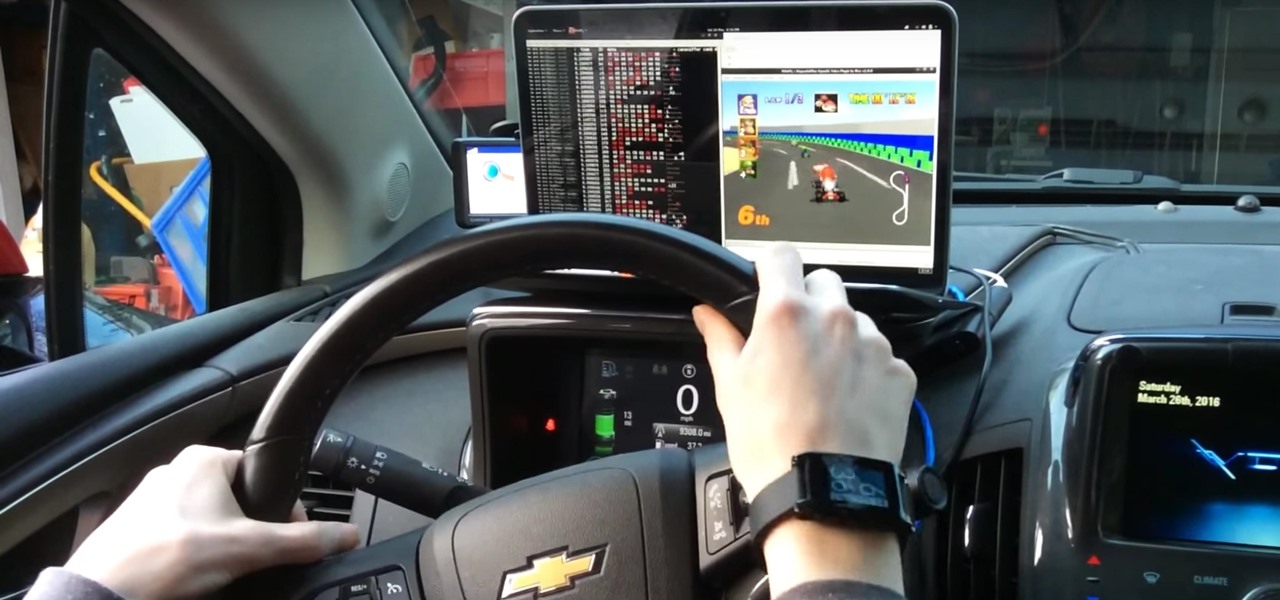
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

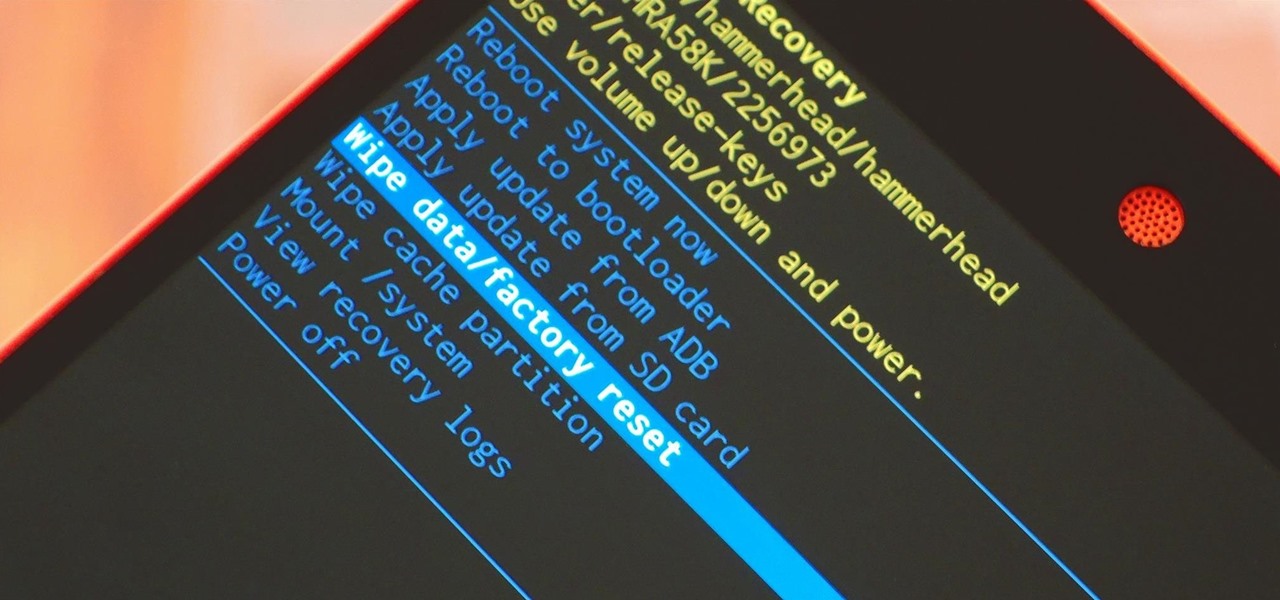
When it comes time to sell your smartphone or trade it in for your annual upgrade, you'll have to make sure that all of the sensitive data the device accumulated while you owned it is properly erased so that no one else can access it. This process is referred to as a "Factory Reset," and regardless of if you own an iPhone or Android device, like a Samsung Galaxy model, HTC One, or Nexus, I'll show you how to do it below.