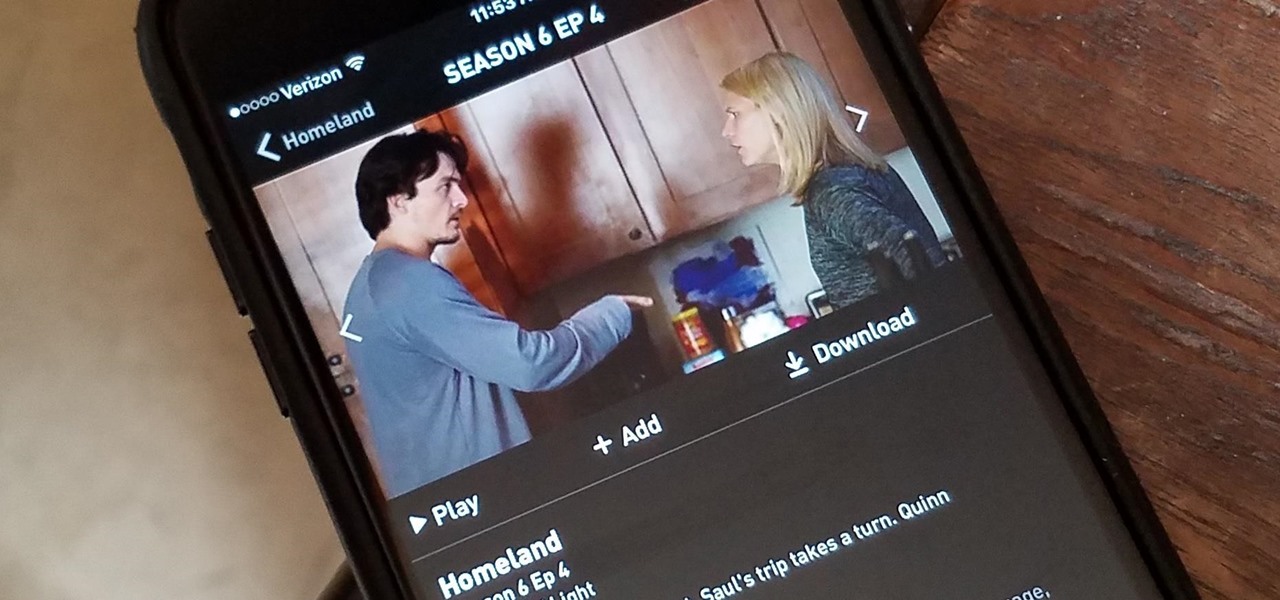
Have you ever wanted to catch up on Homeland or Shameless, but are out and about and don't want to use up your data? Those problems are for days of old now, as Showtime has announced their mobile app will allow titles to be downloaded and viewed without an internet connection.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

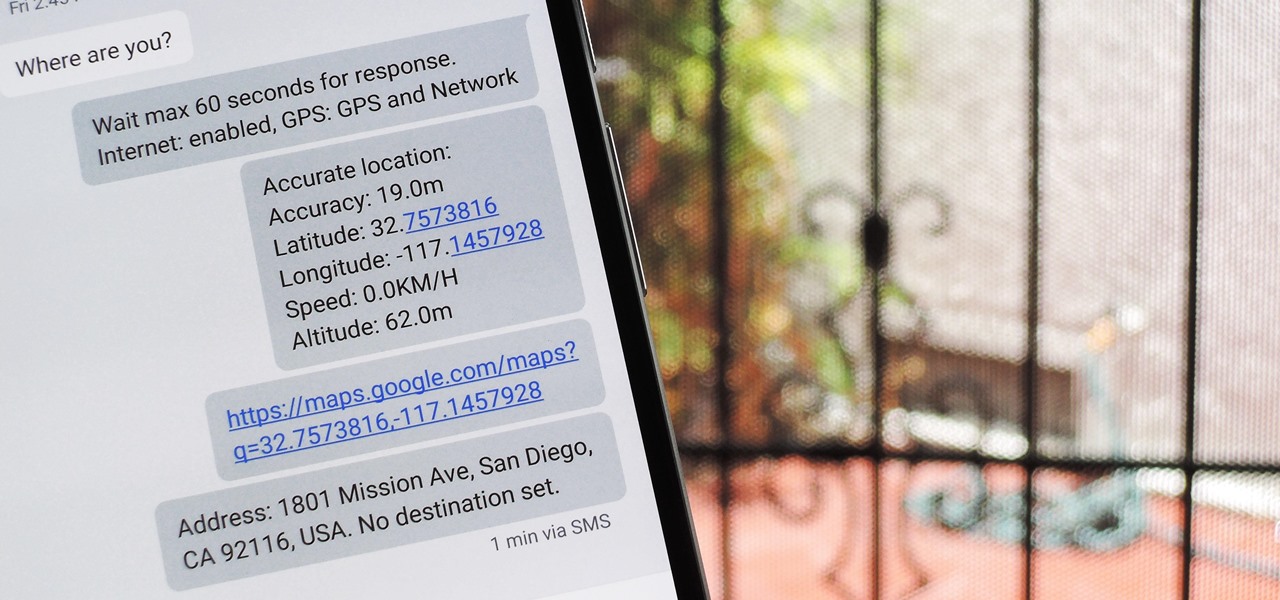
TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Many midrange phones are being manufactured without a gyroscope sensor—the Moto X Play, third-generation Moto G, and several of Samsung's Galaxy Grand models, among others. It's not exactly an essential smartphone sensor, and leaving this out keeps the phone's price point down, so it's an understandable omission.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

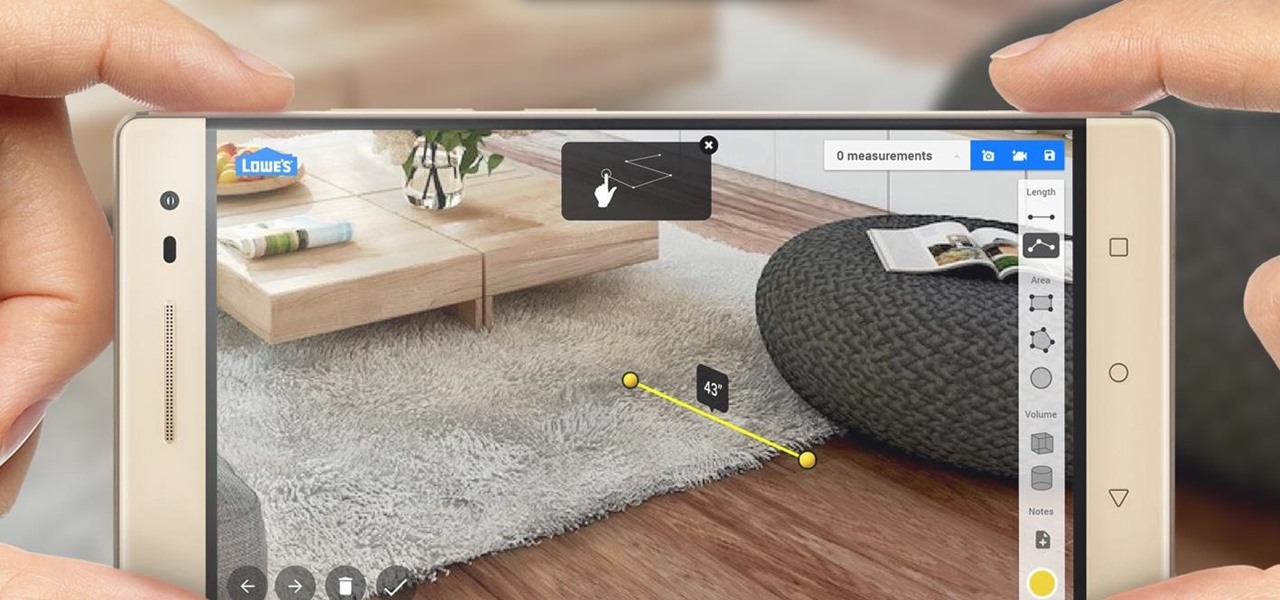
Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

Lenovo announced at Tech World '16 a slew of new products, and one of them aims to upend the smartphone accessory ecosystem: Moto Mods. Moto Mods are proprietary modular add-ons developed for two new Motorola phones that were also announced in the keynote, the Moto Z and Moto Z Force. Sixteen magnetic nodes align the bottom back of the phones that connect and hold accessories, forming a case appearance. The nodes transfer both data and power at high speeds, a fact that Lenovo hammered home wi...

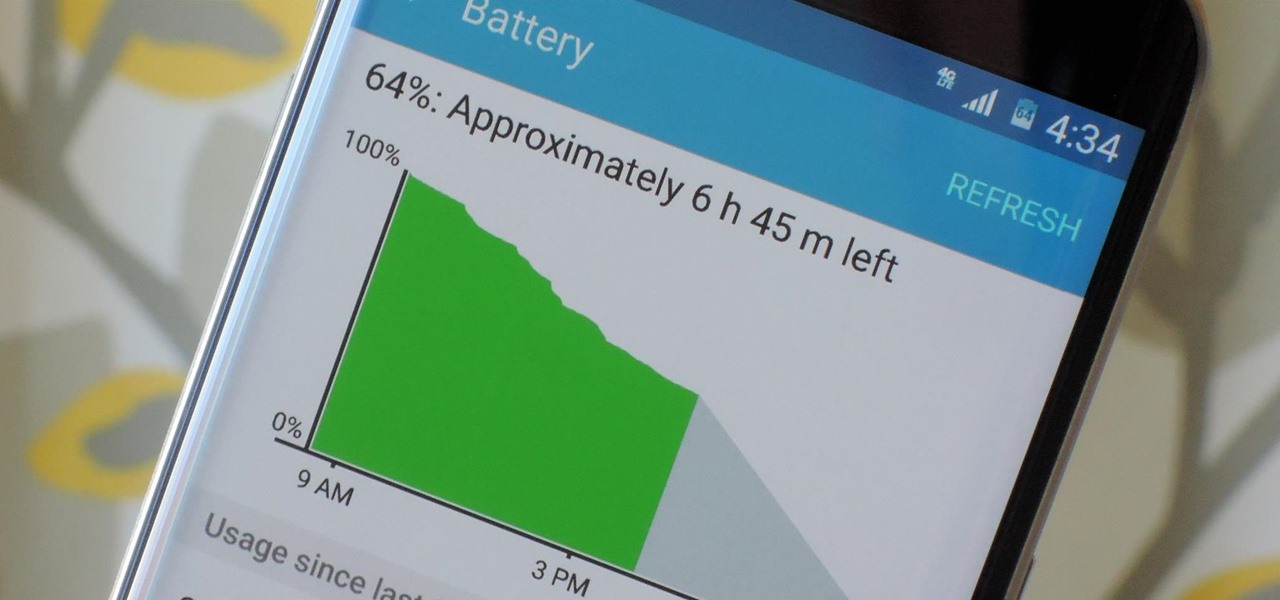
Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

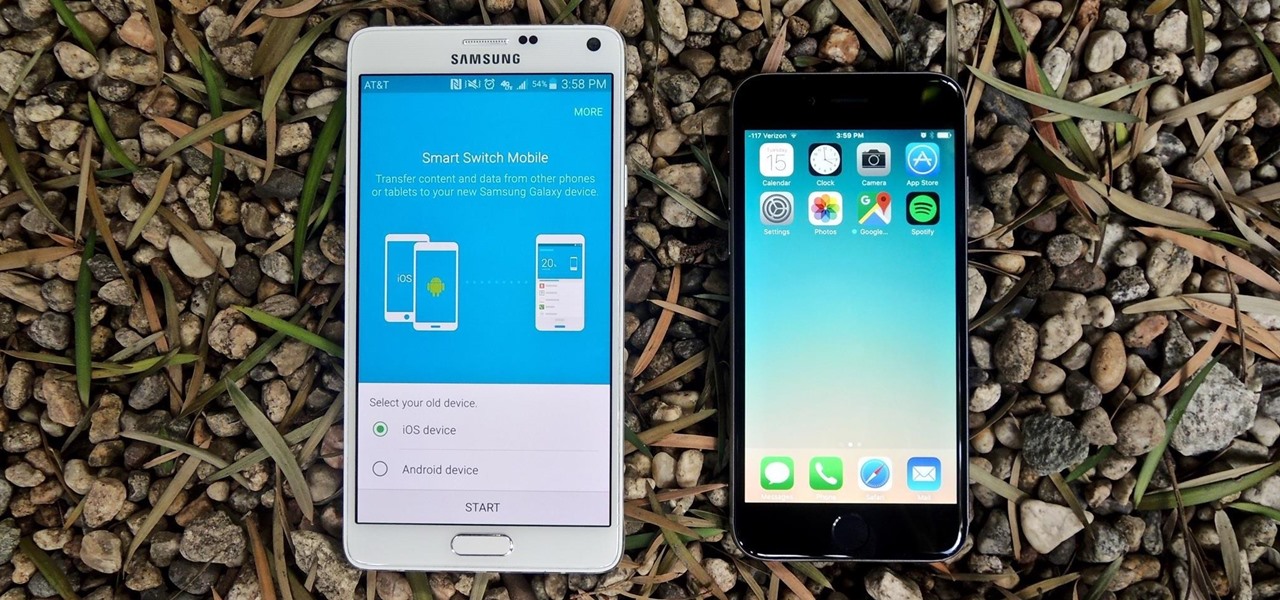
Thanks to Smart Switch, it's easier than ever now to ditch your iPhone for a brand new Samsung device, like the Galaxy S6 Edge+ or Galaxy Note 5.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

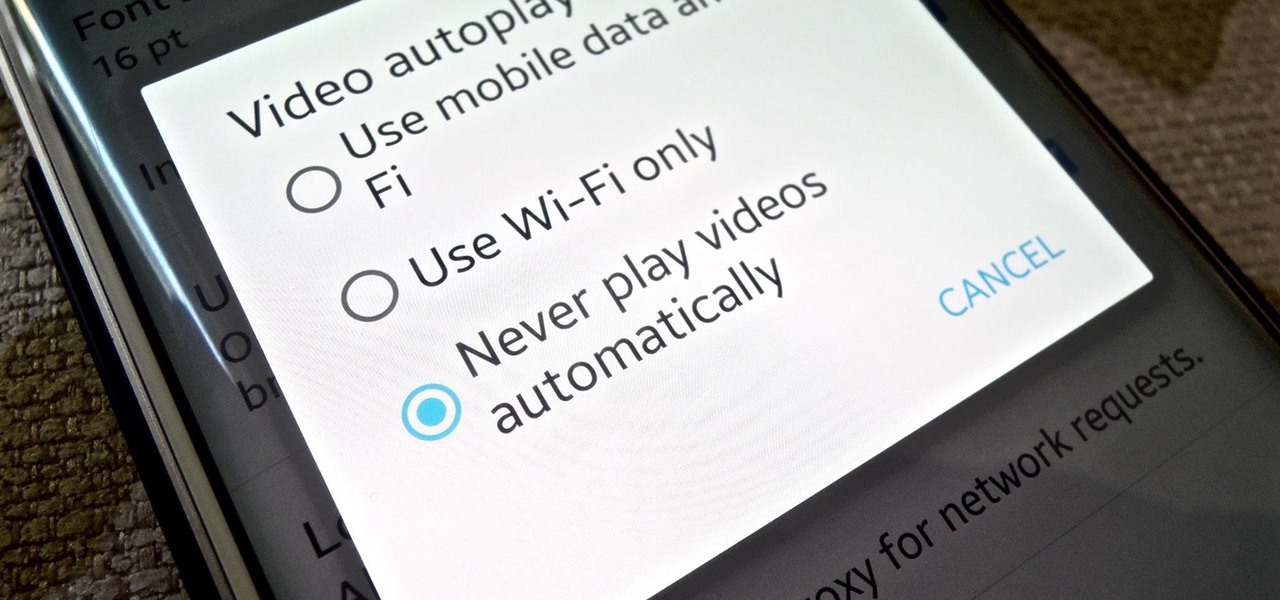
It's bad enough that we have to deal with autoplaying video advertisements all over the Web, so why do we have to be subjected to autoplaying videos on Twitter, too? Autoplay video are muted by default, but that doesn't make them any less annoying, especially if you have a small data plan on your phone.

Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

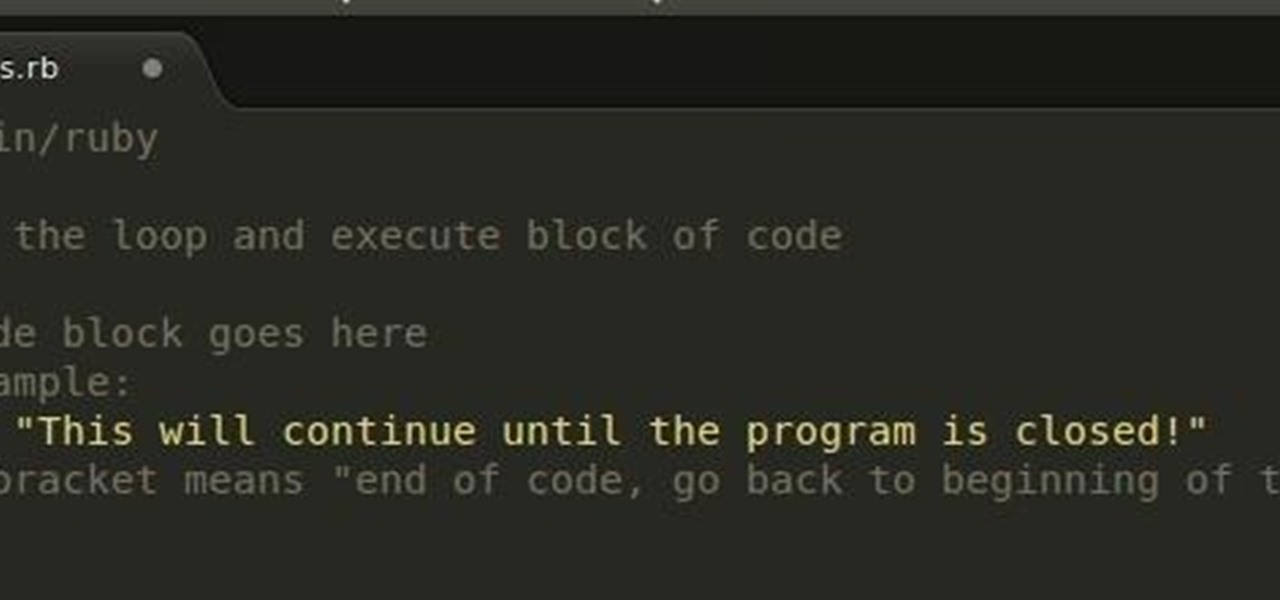
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

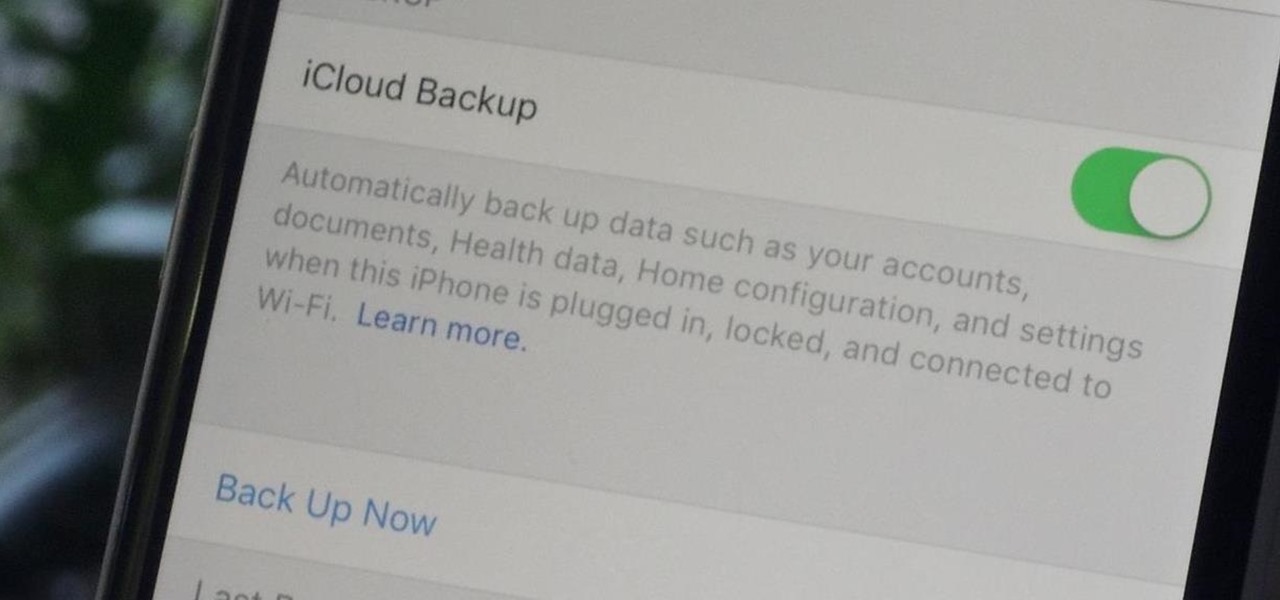
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin.

It's no secret that Google stores your search history in order to provide you with targeted ads when surfing the web. What's even more interesting (or freaky) is that your Google Now voice searches are also being stored, and you can actually listen to them right now.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.

One of the few areas where Android lags behind iOS is a comprehensive backup solution for apps. Root tools, such as the popular Titanium Backup, are capable of backing up all of your apps and their data, but not everyone wants to root their device and potentially run into issues with voided warranties.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.