When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Deciding what to remove from your iPhone in order to free up space isn't the easiest thing in the world. You've got to decide which apps, videos, and photos are worth keeping, even though in a perfect world, you couldn't have to part with any of them.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

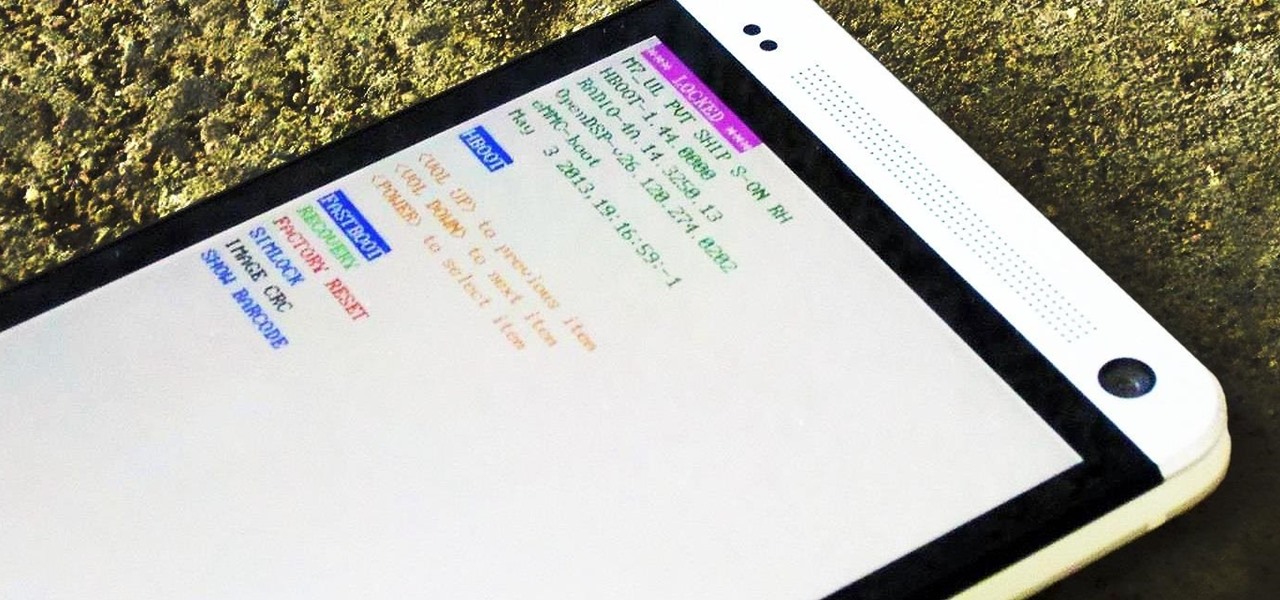
If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

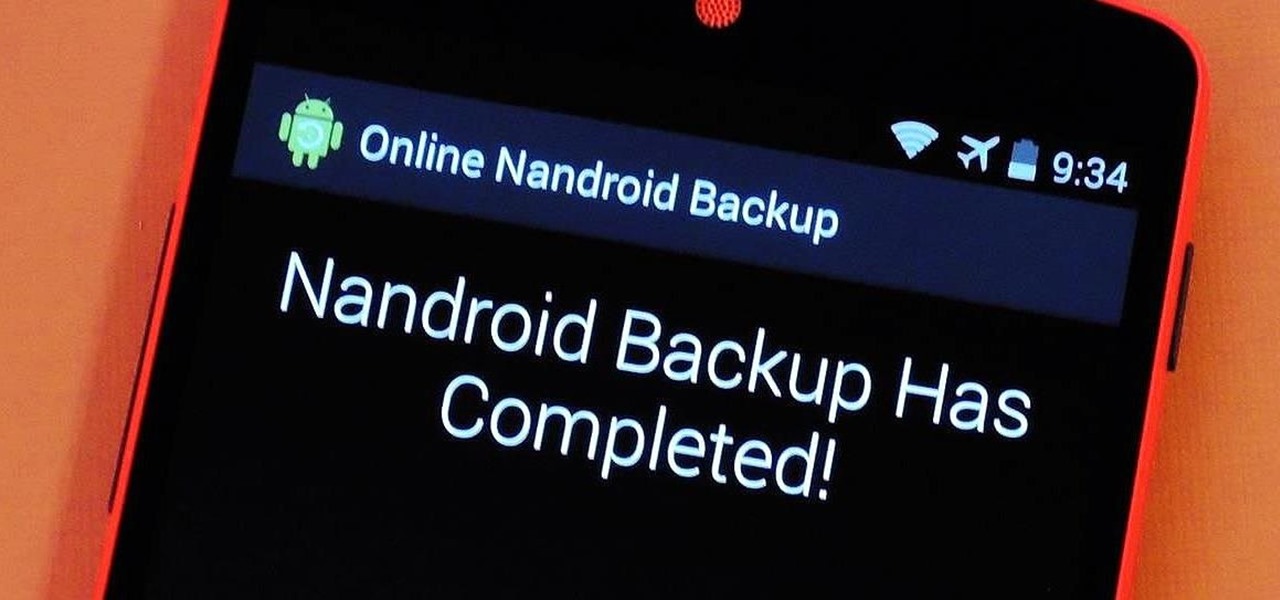
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

Video: . Optimize your Marketing with a Mobile Website

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Sometimes it's necessary to format your memory card in your mobile phone or digital camera, just like you need to format a hard drive, because of virus problems or slower speeds. This video will show you the steps to formatting (or reformatting) the SD memory card for a cell phone, using a memory card reader. You'll also get details about a write protect error that could happen.

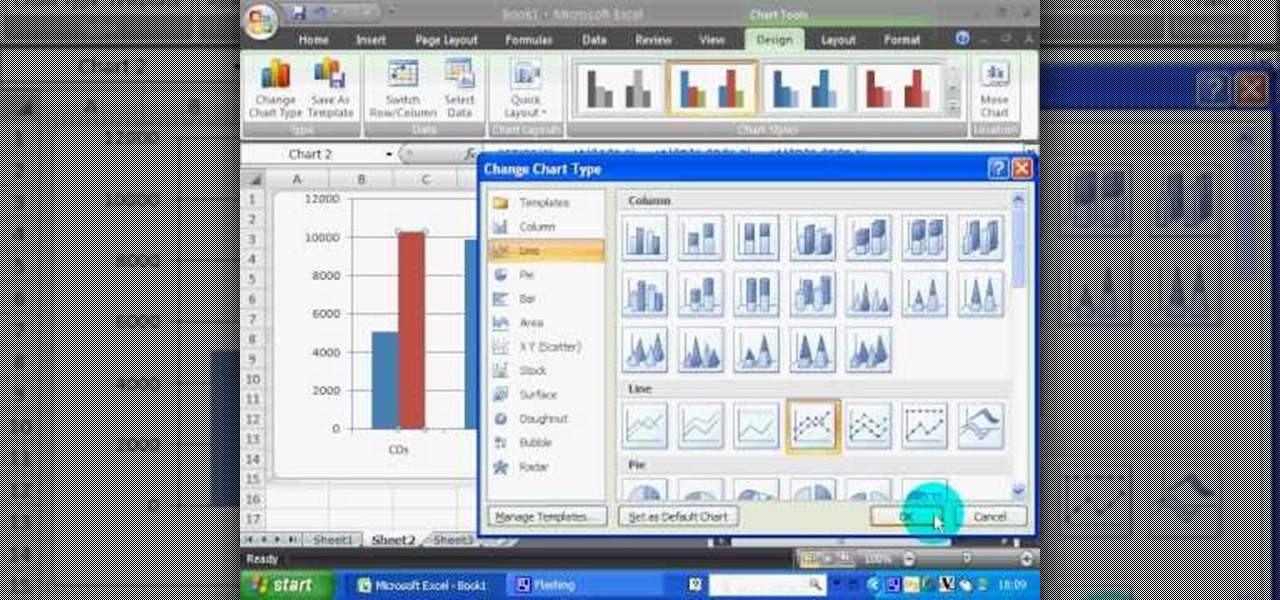
In this software video tutorial you will learn how to create a column line graph in Microsoft Excel 2007. First you type in the data in to the work sheet. Then highlight the data and click 'insert' on the menu bar. Here you select the 'column' option and go down and click on the type of column that you want. And the graph is automatically presented. Now click on 'move chart' and select a sheet where you want the graph to be moved to and click OK. To change any field in the chart in to a line ...

Is your SD memory card getting a little too full? Is it not working? Try reformatting it. It's the first and sometimes last step to troubleshooting card problems. So, if your SD card has become too cluttered, this guide will restore it to a like-new condition with a simple format.

In your Windows XP or Vista computer the hard drive contains only a single partition by default. Partitioning hard drive helps to easily manage you data by segregating them into different drives. You can partition a single drive into multiple logical drives. You can also delete the partitions. First go to the start menu and go to the Computer button. Right click on it and select the Computer Management option. In the Computer Management window, at the left hand side select storage and select ...

Not enough space on your laptop? No problem! Grab a new hard drive from your local office supply store and follow this tutorial to learn how to install it.

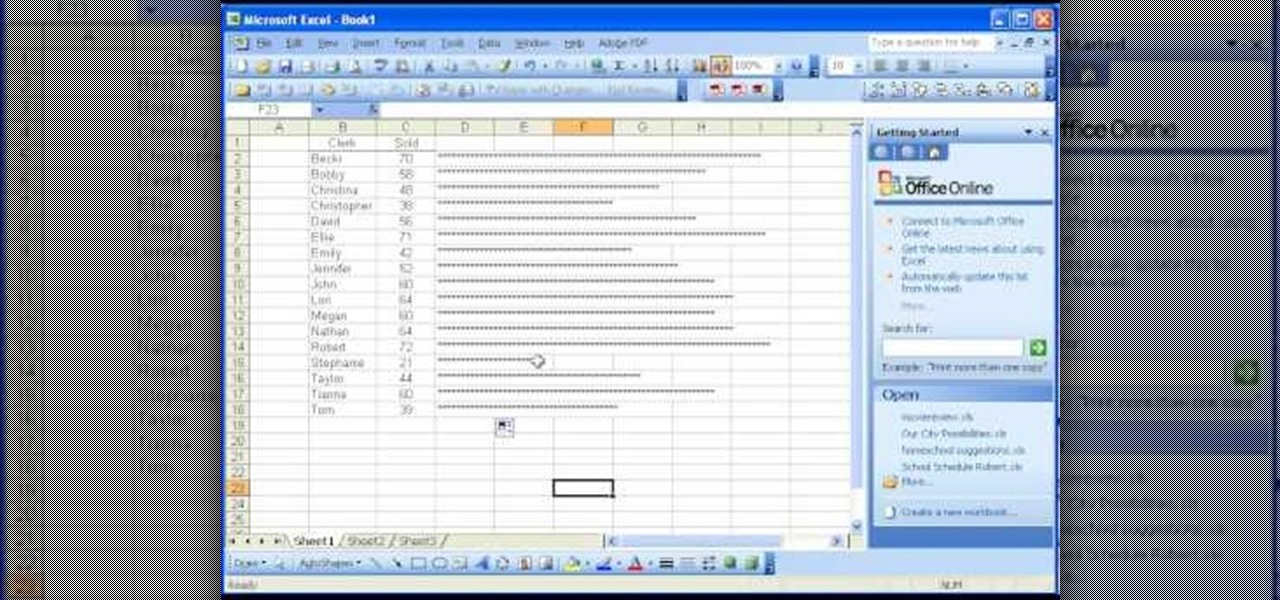
There are many functions in Microsoft Excel. One function that people rarely use is the Repeat function or REPT. In this video, an example used is a chart of people and their sales of a certain item. Just looking at the numbers, it is hard to compare the different sales easily, but a more visual approach may work better. Next to one of the cells, type in "=REPT(" which is the repeat function. A popup should say "=REPT(text, numbertimes)". For "text", type in *** or anything, really. For "numb...

If you're a Firefox user and frequently use free image hosting services à la ImageShack & Photobucket, then you've no reason not to check out the ImageBot Firefox extension, which does quite a lot to streamline the picture uploading process.

This video gives instructions on how to cite sources when giving a speech. When giving a speech, you want to appear persuasive and credible to the audience. In order to do this, you must cite the sources of your speech's content. Prior to giving your speech, research materials relevant to your topic. In the course of giving the speech, mention where you got your data. In this case, the speech is about Emotional Intelligence in the Workplace. While making your first main point, mention that "a...

Unlock and jailbreak your iPhone! You can either reinstall the entire operating system, wiping all the data from your phone, or you can wait for Black Snow to come out. In the method shown in the video, you can unlock right away. To restore, hold option (on a Mac) or shift (on a PC) and click restore. After it is done restoring, you should be getting an error message that the phone isn't registered and to insert a SIM card. Insert the SIM card you want to use. Close iTunes and open up www.bla...

Removing the cookies from Firefox and Internet Explorer is explained in this how-to video. First let's see how to delete cookies from Firefox browser, just follow the following steps:

Every once in a while, you will have a lot of work to do in FarmVille, and a lot of space to cover. Use the fullscreen option to make life easier and see more at once.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

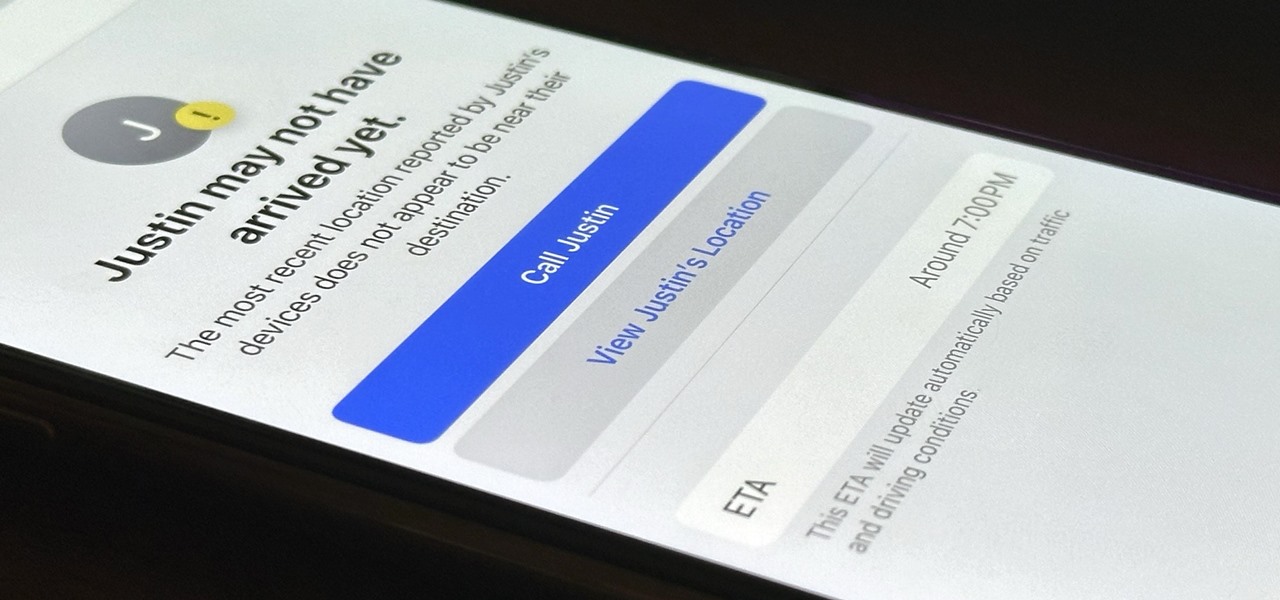
Check In is a new safety feature built into the Messages app that can automatically notify a family member, friend, another contact, or a group the moment you arrive safely at a destination, giving them peace of mind in knowing you're all right. If you never reach your stopping place, it will also send them clues to help them figure out what went wrong.

It's easy to lose the TikTok video you were watching when you accidentally refresh your For You feed, but it's not gone forever. TikTok has a new feature for your iPhone, iPad, or Android device that can show you all your watched videos over the last seven days. There are also other, more hidden ways to see your watch history — one that goes well beyond a week.

If you have an iPhone running iOS 15 that's connected to Google Fi or another mobile virtual network operator, you may not be getting any photos or videos in Messages. That may be because you recently installed a software update, and you'll have to restore your cellular data network settings to get MMS working again.

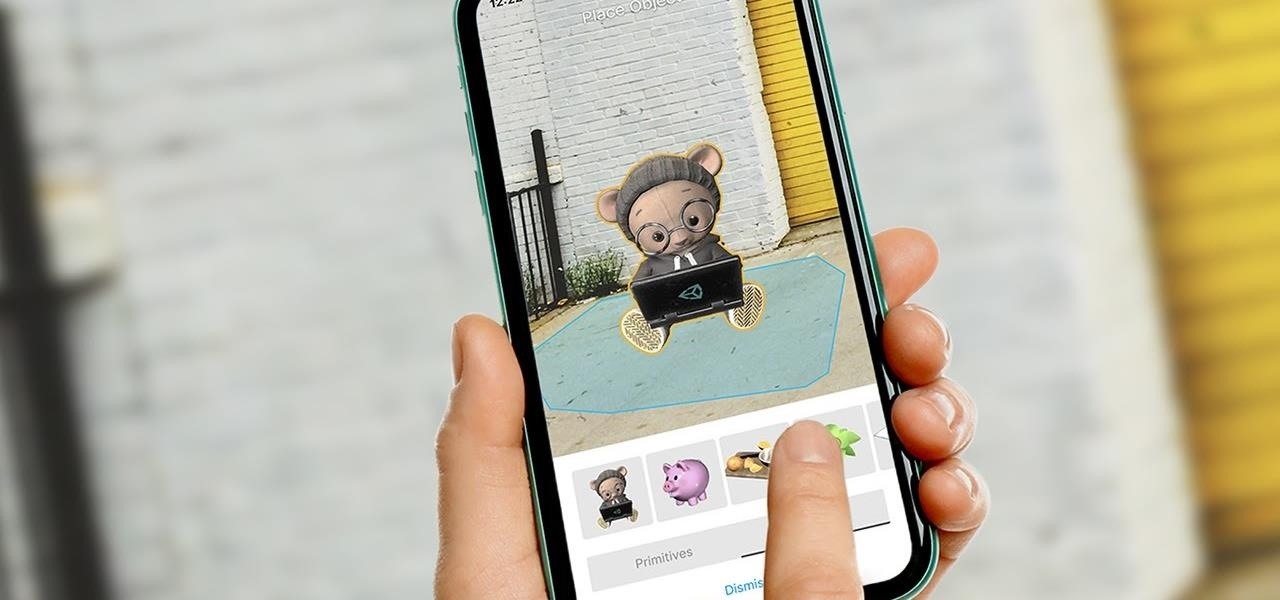
Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

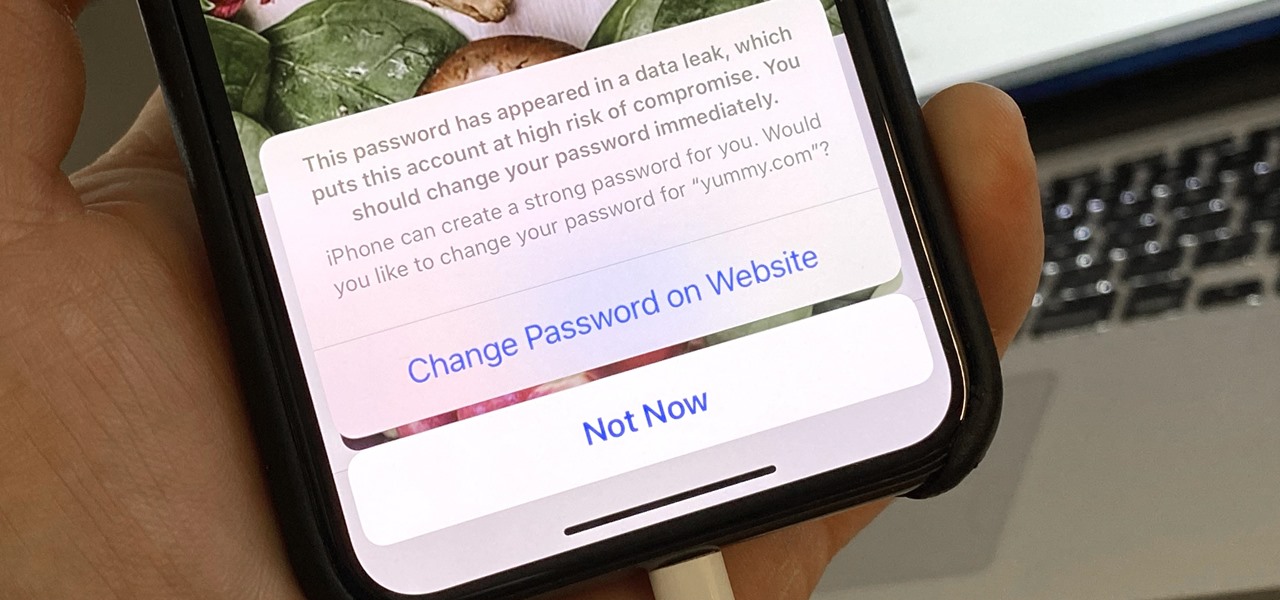
Everything lives online these days, so it's not uncommon to have hundreds of credentials for different accounts on apps and websites. That's why a password manager is a must, and your iPhone has one built right into iOS that you can start using today. In iOS 14, it's gotten even more useful since it can now monitor your passwords regularly to see if any match leaked password lists online.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.