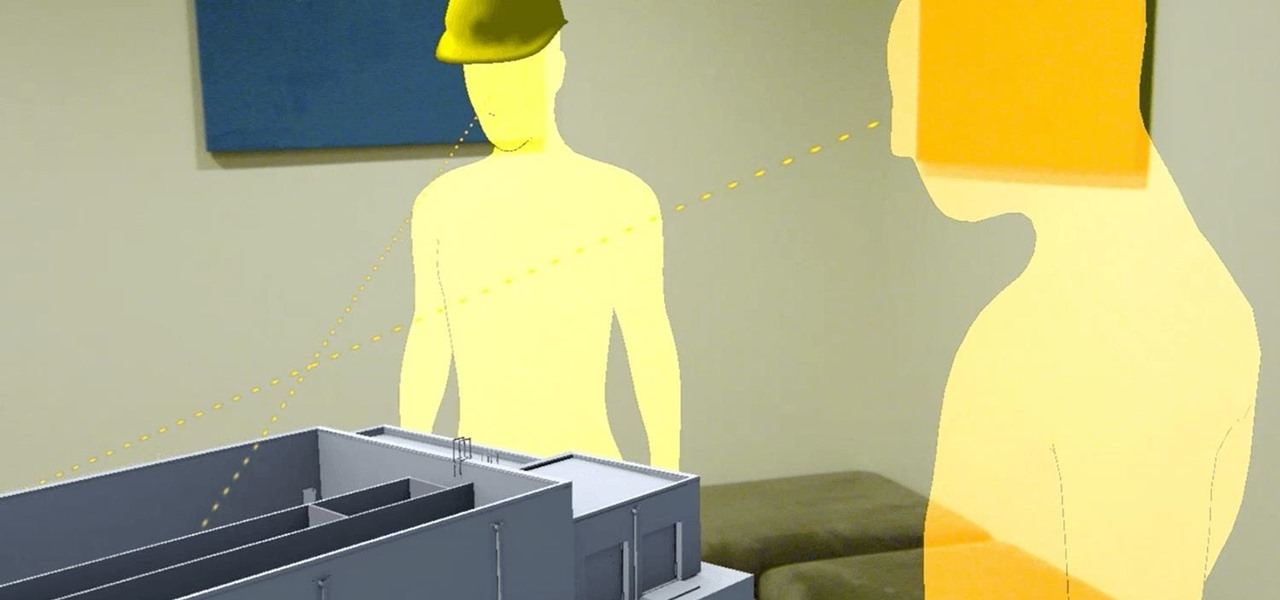
With developers already figuring out how to use the HoloLens for home improvement tasks, it's no surprise that the device has greater applications in construction. Tech blog Digital Trends points out that holograms are a natural evolution of the blueprint, and several other aspects of construction work.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

With the DOJ attempting to rip Apple a new one and an Apple attorney firing back, the President offered his opinion on the recent encryption debacle between the FBI and Apple at SXSW, amidst some talk about the direction of today's tech industry.

Out of nowhere, Google released a preview build of the upcoming Android N release back in March—a full two months early. As if that weren't enough excitement for one day, they topped themselves by following up that announcement with the debut of a new "Android Beta" program that allows users with eligible devices receive preview builds as a regular OTA update, meaning no losing data or manual installation.

Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

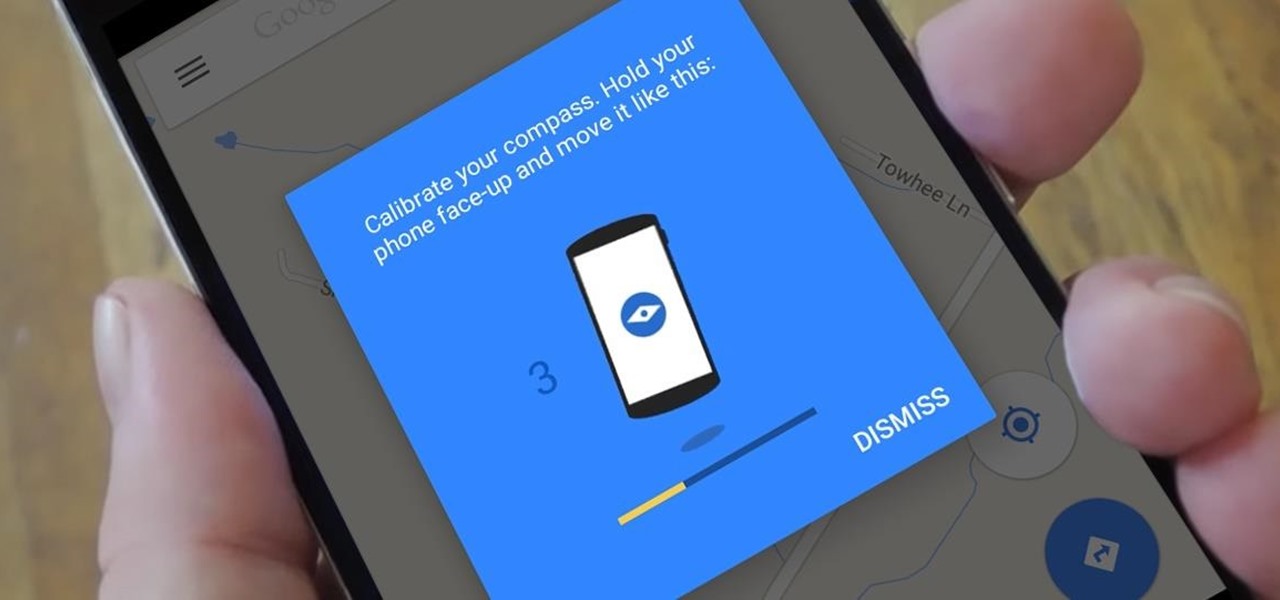
A lot of users with newer Android devices, particularly the Nexus 6P, have been complaining about issues with their device's compass. I've experienced the issue a few times myself—when you open Google Maps and try to get directions somewhere, you're prompted to calibrate your compass before you can proceed.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Taxi drivers and cab companies across the globe are in an uproar over Uber, and for good reason, too—you just can't compete with the low fares and ease of use that Uber brings to the table. The only downside is that the groundbreaking ride share service usually requires a smartphone—but that shouldn't be an issue anymore with one simple tip that I'll outline below.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Of all the new features in Android 6.0 Marshmallow, an automatic battery-saving function called "Doze" might just be the most interesting. What it all boils down to is that if you set your phone down on a flat surface, the device uses internal sensors to detect that it's motionless and not in use, then responds by drastically scaling back battery-sucking services until the next time you pick your phone up.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Although I am a loyal premium Spotify subscriber, I still regularly use Pandora in hopes of stumbling across new artists and songs. If I'm fortunate enough to come across something I enjoy, it's easy to use the Like feature in Pandora to locate the song later.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

As many of you may have heard, Apple's new iOS 9 is "rootless", which supposedly would make jailbreaking much more difficult. However, it has been shown to be possible. ih8sn0w posted a youtube video of his jailbroken iphone running iOS 9 and even gave some hints about it in the video description section. However, he also stated that he will NOT be releasing it to the public. So it would be quite the feat and adventure to take his hints and comments and use that to figure out how to jailbreak...

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

While its hardware may already be a little outdated compared to newer flagship phones, the OnePlus One is still a great value thanks to the dedicated community that continues to develop ROMs for it. Cyanogen 12 and Oxygen OS are the two most popular ones, but neither offers the type of unique experience you get with Xiaomi's MIUI (pronounced "Me You I").

Living in Southern California means I don't really have a need to check the weather all that often. But every now and then, I'm caught off guard by a particularly chilly or hot day—no one wants to be the only person walking around with a T-shirt and sandals on a rainy, 50-degree day.

Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent.

Upon getting the new Samsung Galaxy S6 Edge here at the office, there are countless things we wanted to do before actually diving in and using the device. One of those things is removing all of the unnecessary pre-installed applications we never asked for.

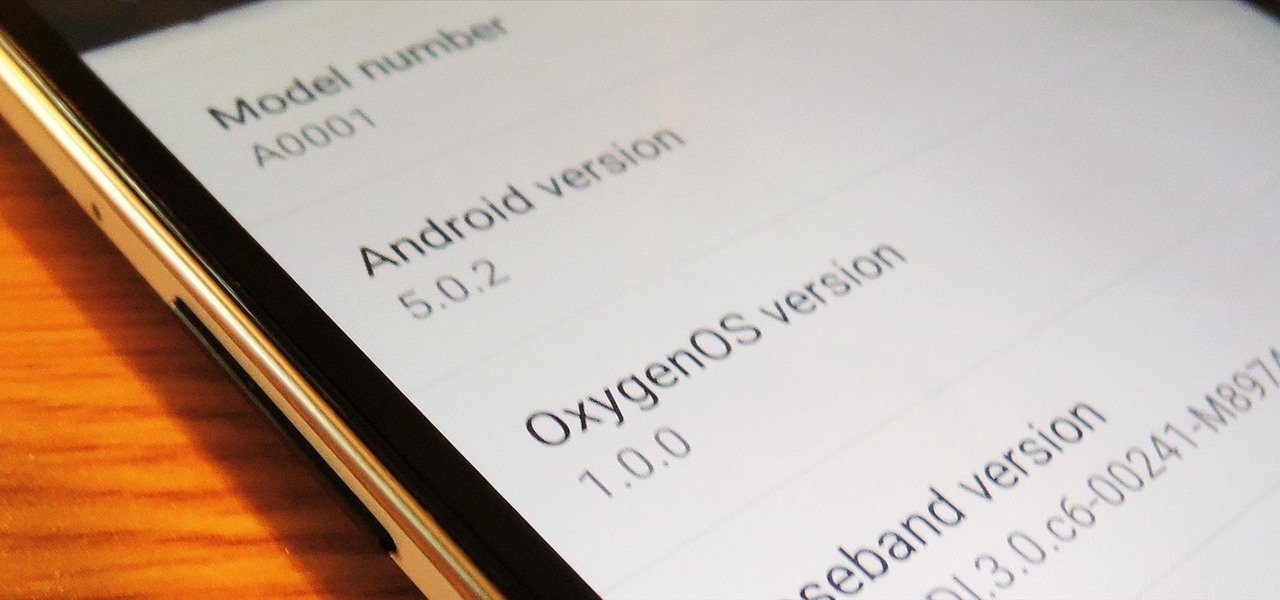
Despite CyanogenMod actively working on their CM 12S Lollipop-based ROM, OnePlus has opted to develop their own ROM, and after a few setbacks, OxygenOS is finally out. The OS is the result of OnePlus wanting to ship their devices without needing an outside company to create a ROM to power it. Like CyanogenMod's ROMs, Oxygen OS offers a vanilla Android Lollipop experience tailored for the OnePlus One.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.