Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

There is nothing worst then having to wait for something you really want. It doesn't matter how old you are or what the item is, the fact that you have to wait for it makes you want it even more. It's the love-hate relationship I have with Amazon and anything I order, and when that anticipation is for a new smartphone, it's amplified by about a thousand. The LG Nexus 4 has received great reviews and is one of the most sought after phones this holiday season, but it's a hard one to get a hold ...

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...
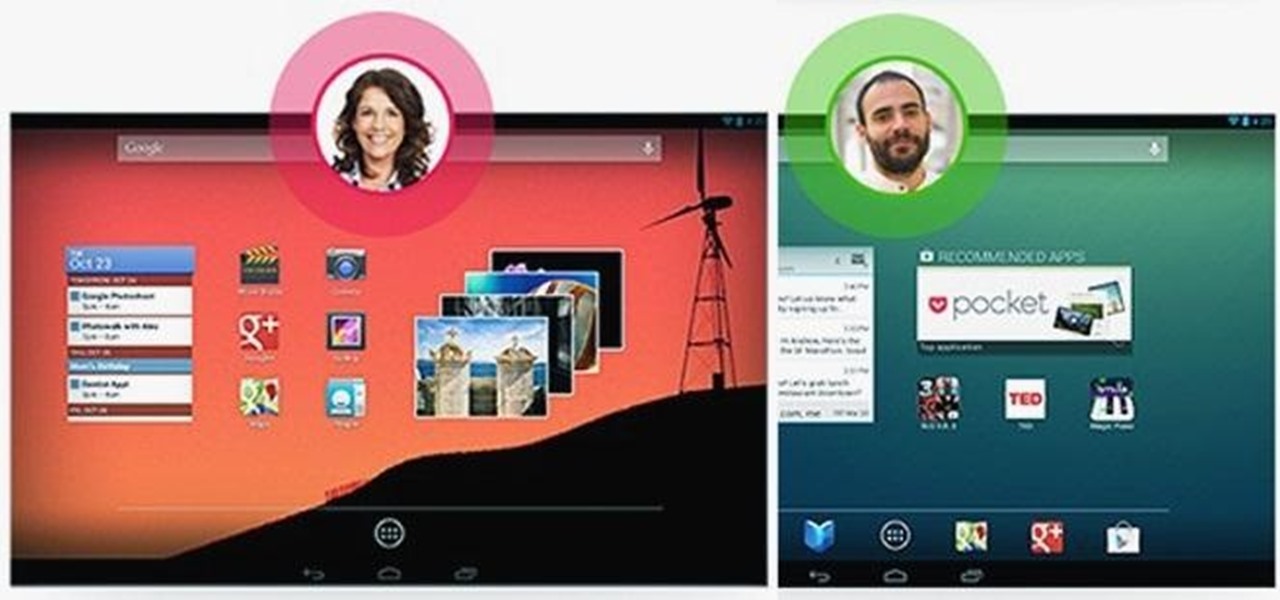
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

If you have the international version of the Samsung Galaxy S2 (I9100) and are sick and tired of waiting for the Jelly Bean update to hit your device, you're in luck—XDA-Developers member izap has leaked what appears to be the final version of Android 4.1.2 for the S2.

Whether it's forgetting your driver's license or misplacing your cell phone, forgetting things at home can be a pain in the butt. Car keys, wallet, purse, papers, sunglasses—the list can go on. Sometimes I even surprise myself at the important things I forget... Oops.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

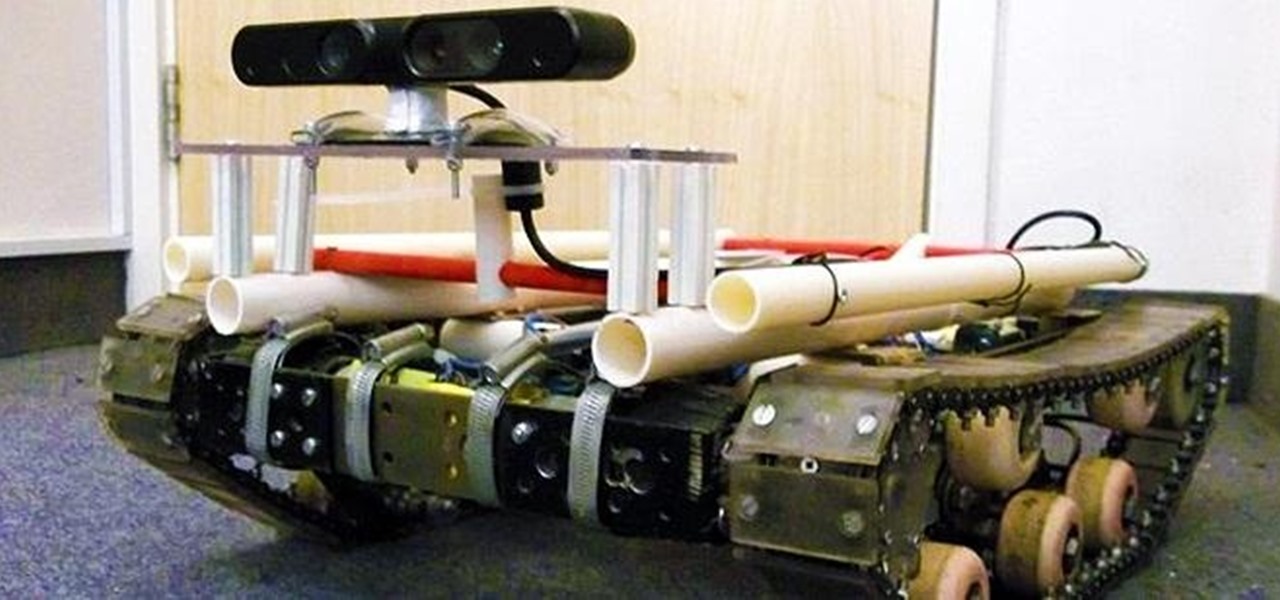
There are plenty of tank robots out there, but how many of them can recognize 3D objects and map their environment? Tanky, the tracked mobile robot, can do all that and more while rolling around on his bicycle chain treads. Created as a Master's thesis project, Tanky is made almost entirely of parts you can find at your local hardware store. It was built in two "layers" with the motors, electronics, and batteries on bottom and the processing unit, a laptop, on top. The motors came from cordle...

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Even though iOS 6 has only been out for a day, the folks over at iPhone Dev-Team have already released a Redsn0w jailbreak that works on the iPhone 4, iPhone 3GS, and iPod touch (fourth generation). As of right now, there's only a tethered jailbreak available, which means that you'll have to connect your device to your computer every time you power it up, but an untethered version that works on more devices is more than likely on the way. Until then, tethered is better than nothing, so here's...

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.

Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar?

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Google's Nexus 7 tablet has just been released, and for only $199, it seems like a great deal. Now, some of you are probably immediately thinking that you're going to want to root this thing as soon as possible to install all of your tweaks. Luckily, some clever hackers have already developed a fairly automated solution to rooting the device. Here's how it works. A word of caution however, rooting your tablet will very much void the warranty and there's no 100% guarantee that this procedure w...

Hello! I would like to share some data about the nests that rabbits and dwarf rabbits build. They represent good shelters for them and their babies.

Video: . » Iran Threatens to Block Tankers in Response to Oil Import Embargo Alex Jones' Infowars: There's a war on for your mind!.

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

Having the Internet on your phone is definitely handy. You can look up anything at anytime, and connect with friends in so many more ways.

The video starts by informing about the basic safety precautions, tools needed and backing up data prior to hard drive replacement. There are a series of screws which need to be removed in the following order.1. Removing the battery from the back and then remove three screws thereby removing the RAM cover.2. Two more screws to be removed under the RAM cover.3. Two screws from inside front edge.4. Four screws from the bottom rear.5. Two screws each from the slim sides.6. Two screws near the hi...

How to make TCPO or bis(2,4,6-trichlorophenyl) oxalate, used in glow stick reactions. WARNING: This procedure should only be performed by, or under the direct supervision of, an experienced chemist. Please refer to the material safety data sheets of all chemicals for their hazards. Synthesis must be performed in a fumehood.

In this video tutorial, you'll learn how to use the Second Copy backup application, for the Windows operating system, to protect your most important data. For step-by-step instructions on installing and using Second Copy, take a look at this backup how-to.

If you're new to DreamCoder for Oracle, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your Oracle databases with ease. For step by step instructions, consult this how-to.

Working with Oracle, odds are you may, on occasion, need to build an Oracle database from MySQL. Happily, this DreamCoder tutorial will walk you, step by step, through the process. To learn how to build an Oracle database from MySQL data, take a look!

This tutorial video includes updated information regarding new functions of RAID Reconstructor & GetDataBack for NTFS. You'll see how to make an image for a RAID 0 setup. data recovery doesn't get any better with Runtime's software. Your computer's hard drive needs to be backed up.

Pivot tables are great tools for comparing data, especially when dealing with long lists. See how to create pivot tables in Excel.

Borders and shading add aesthetic presentation to your spreadsheet data. See how to create borders and shading in Excel.

For most mainstream users, LiDAR sensors for precision depth sensing remain the exclusive domain of Apple iPhones and iPads, but Google is helping Android device makers close the depth gap on the software side via its ARCore toolkit.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

Written language began with one of the most pedestrian tasks imaginable: accounting. The basis of poetry, epic mythologies, and novels initially involved marking down trades between livestock owners and grain suppliers. We rightfully think that literature is essential to the human spirit. But when contemplating how societies operate, spreadsheets are king.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

Lossless quality isn't for everyone. If you can't distinguish between lossless audio and other formats, you probably but don't need it. But if you're a musician who's sharing ideas with bandmates or a journalist interviewing people for a video, you might want the best possible quality, which is what lossless offers. And you might not know it, but the Voice Memos app on your iPhone supports it.