
How To: Format a drive or USB flash drive
Reformatting a flash drive will update its drivers and rid it of all data. This can help in a lot of occurances. This tutorial will show you exactly how to format flash drive properly.


Reformatting a flash drive will update its drivers and rid it of all data. This can help in a lot of occurances. This tutorial will show you exactly how to format flash drive properly.
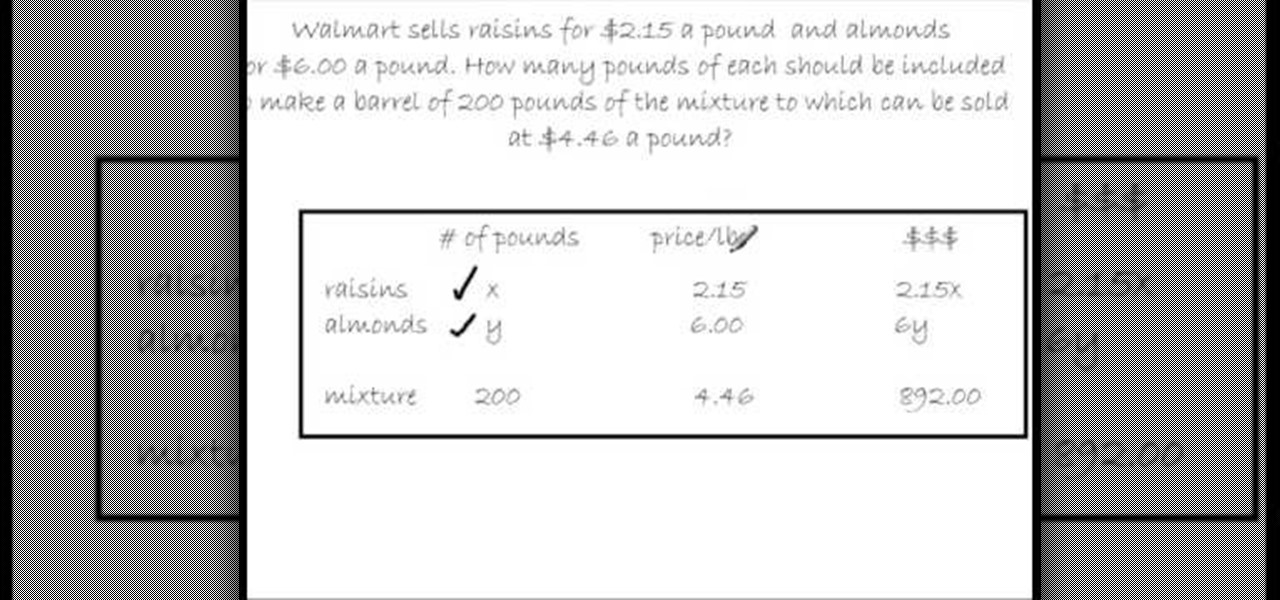
In this video the instructor shows how to solve mixture problems using two variables. Usually in these kind of questions the problem statement goes like, if A costs $x for a pound and B costs $y for a pound, in what ratio should they be mixed such that one pound of the new mixture sells for $z a pound. So, in these kind of problems start with a box where you list down all the given data in the form of a table as shown in the video. Now denote the unknown quantity of A and B by two variables a...

New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck.
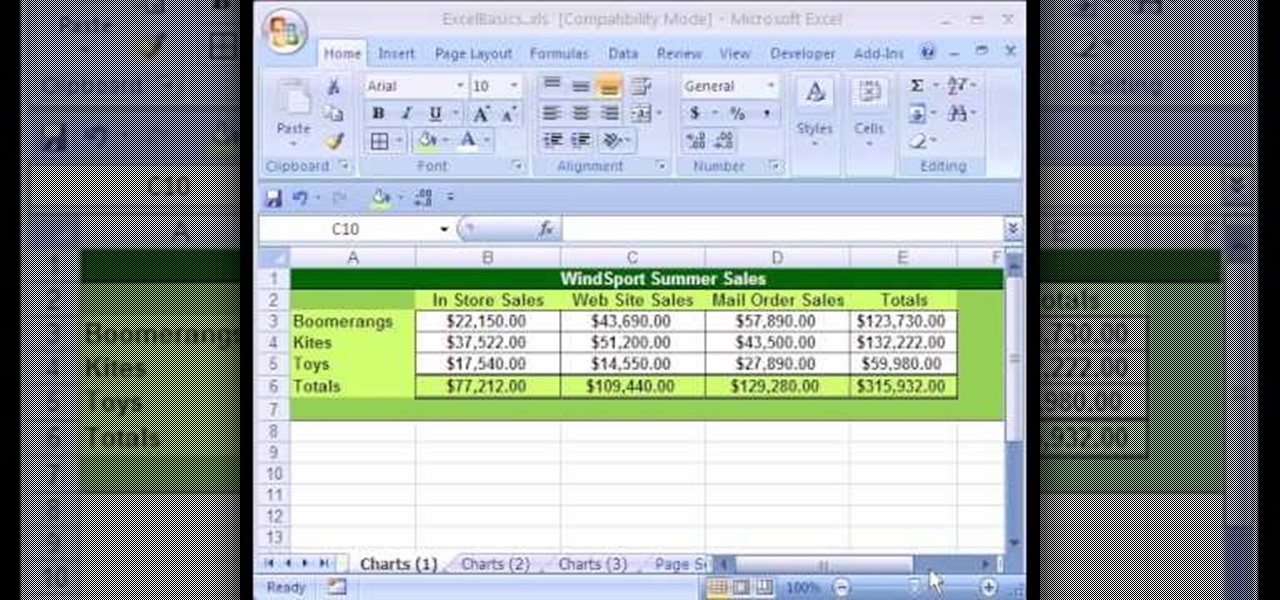
In this Excel basics video, the instructor talks about the basics of charts. There is an enormous difference in how you make charts between Microsoft Excel 2003 and 2007. In both the versions, to make charts the first thing you do is highlight the data cells in your workspace. Now use the toolbar and click on the charts button there. Now Excel automatically generates the charts based on the data and the column and row names. But there are various changes between the charts produced in the dif...
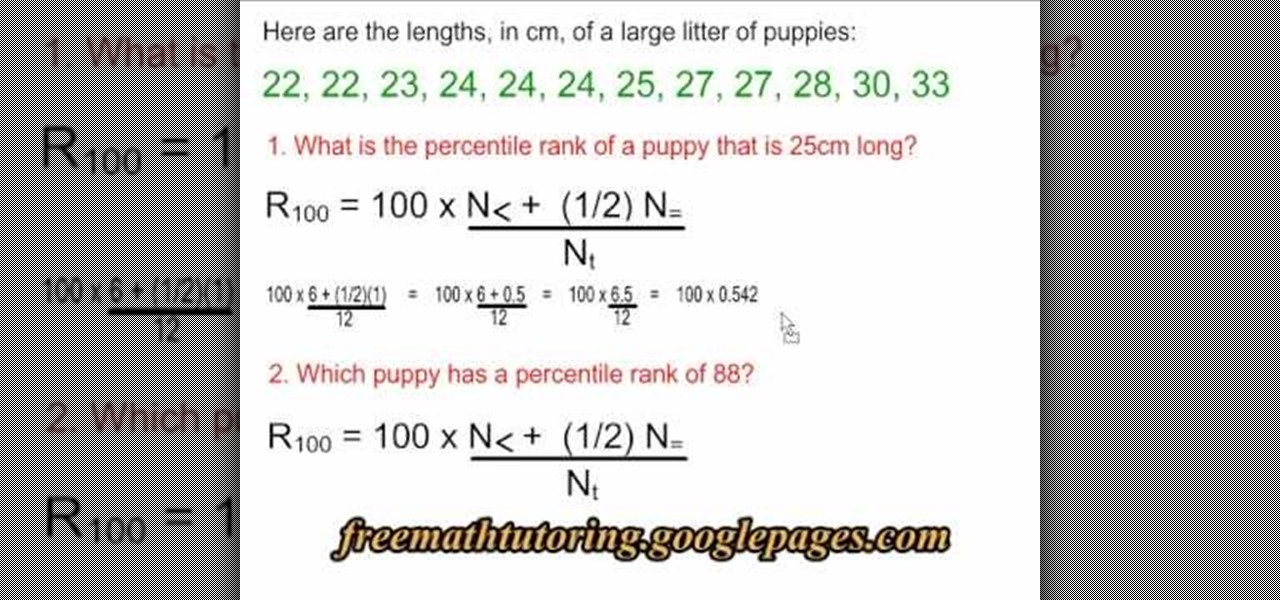
In this tutorial the instructor explains the percentile formula. He says that the percentile formula is used to find the percentile rank of a data point in a group of data. He takes an example that consists of the lengths of puppies. Now he intends to find out the percentile rank of any puppy in the group. He shows that the formulate to compute a percentile rank of a particular puppy is rank R = 100 * (N< + (1/2)N= )/ Nt, where N< is the number of puppies whose length is less that the length ...
This video presented by Cris Ippolite makes a comparison between flat files and relational databases made with FileMaker Pro 10. It starts by showing flat files, which programs like Microsoft Excel use. Flat files have a big disadvantage: they cannot communicate with other files, even those with related data. If you wish to make your job easier, you should use relational databases. With databases, the tables communicate between one another. Once you store an entry in a table, you can use it i...
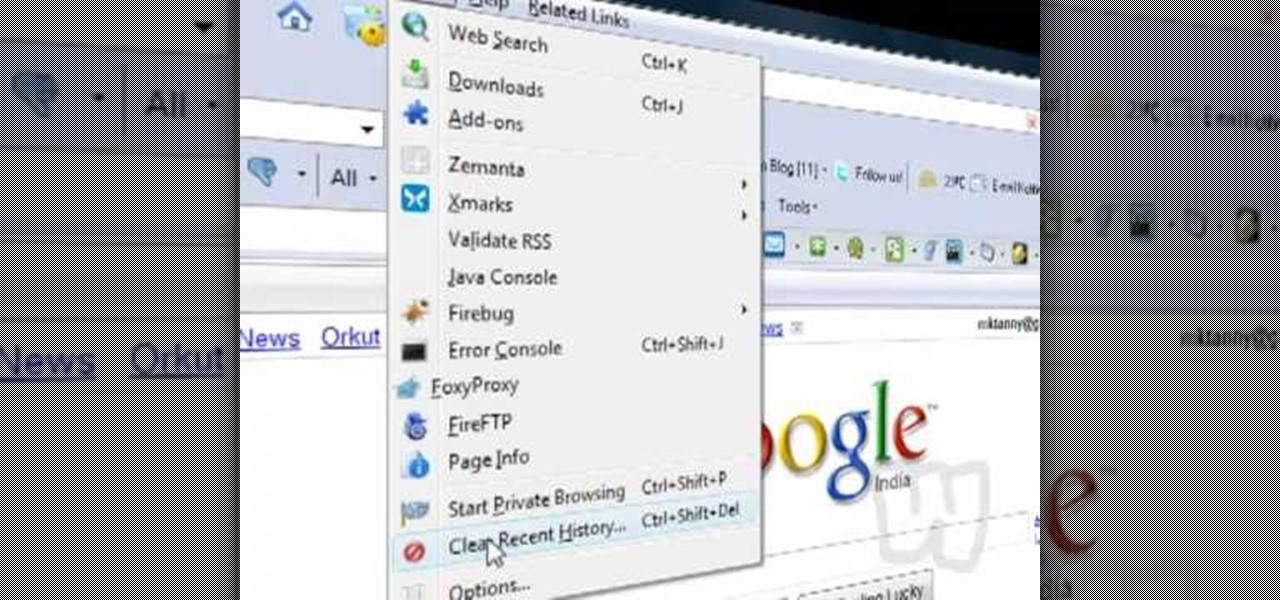
This video shows you how to easily delete cookies from your browser. First thing you have to do is open the web browser you usually use (the video shows how to delete cookies from Firefox) and go to the Options tab in the upper menu. Then choose the Clear Private Data or Clear Recent History item. In the pop-up window, check Cookies and Cache and then press the Clear Now button. The Clear Private Data/ Clear Recent History window also can be opened by pressing CTRL+SHIFT+DEL. That's it! Good ...
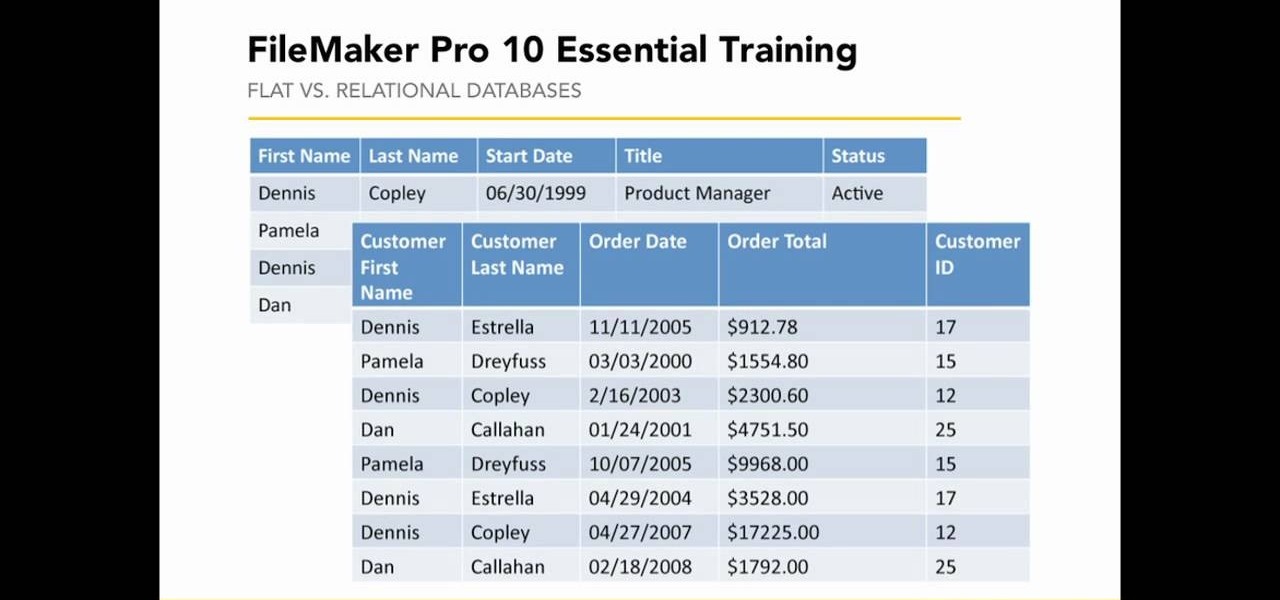
This video, presented by Cris Ippolite, makes a comparison between flat files and relational databases made with FileMaker Pro 10. It starts by showing that programs like Microsoft Excel uses, what in the databases circles, are called flat files. This flat files have a big disadvantage: it cannot communicate with other files even those have related data. So, instead of using those, if you want to ease your job, you should use relational databases. With databases, the tables communicate betwee...

Learn how to set up the Internet for T-Mobile on an iPhone clone. First you need to create a GPRS data account and a WAP profile for T mobile to bring up the service icon. Then click the data account button, then the GPRS button, then chose the correct account for you, change the APN to Link (all lower case). Before you finish this process make sure the user name and password fields are blank.

We know, we know: How many people actually burn stuff onto CDs these days? Well, while external hard drives that hold several terrabytes of data and flash drives have kind of replaced our reliance on CDs, every now and then they're good for quickly compiling a "Pop Hits of the '80s" CD for your girlfriend or simply for storing your illegal version of Microsoft Office.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. Generally, the DataPager control is used with the ListView control. The ListView control is data driven. First create a ListView control and provide it some data. Next drop ...
In this video tutorial, Chris Pels will show how information can be passed from one page to another using a query string. First, see how to construct a query string including variable names and values from information on a data entry form. Next, see how to access the query string information when the page is posted including how multiple query string variables are handled. As part of the server side processing of query string information, see how to implement validation for existence of query...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:
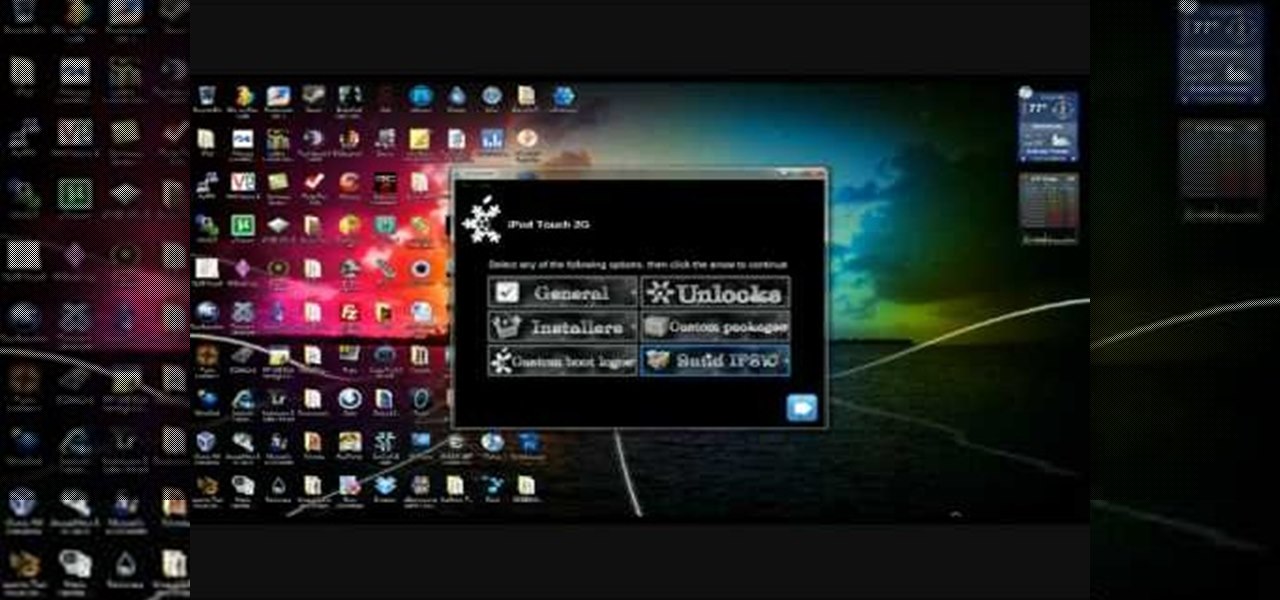
In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!
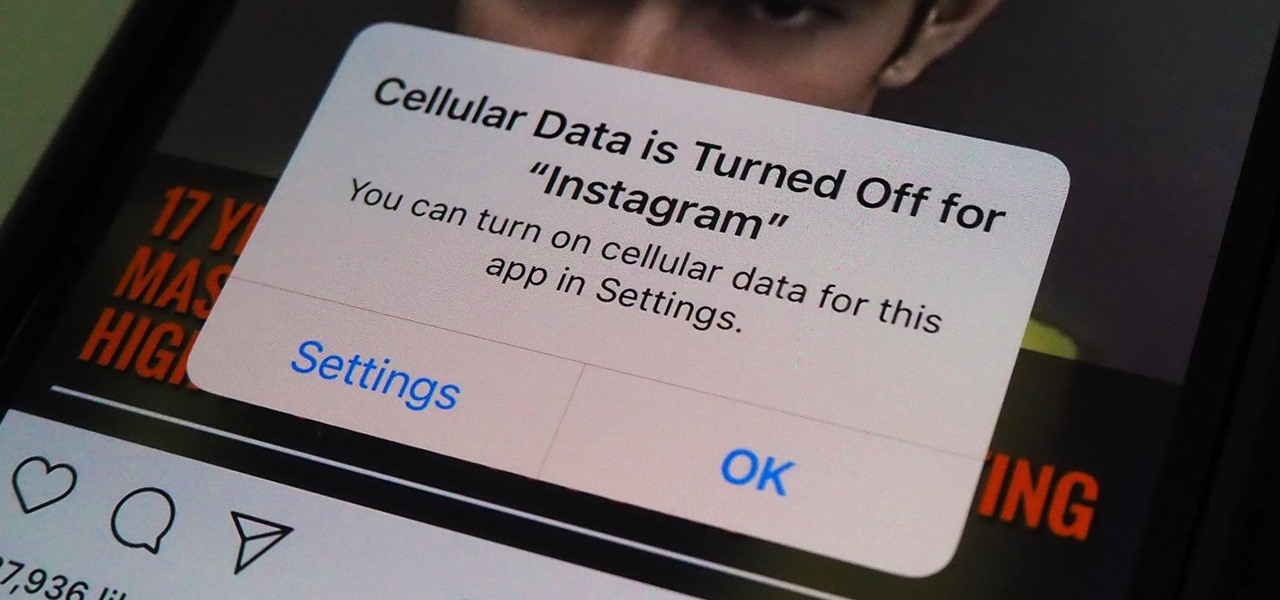
If you're on a cellular plan with a low data allotment, being thrifty with your data can help you avoid a higher bill. But even if you have an affordable unlimited plan from wireless carriers such as T-Mobile or Verizon, going over a certain amount of data may throttle your connection, leaving you with slow web speeds. One way to prevent hitting these thresholds is to keep certain apps in check.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.
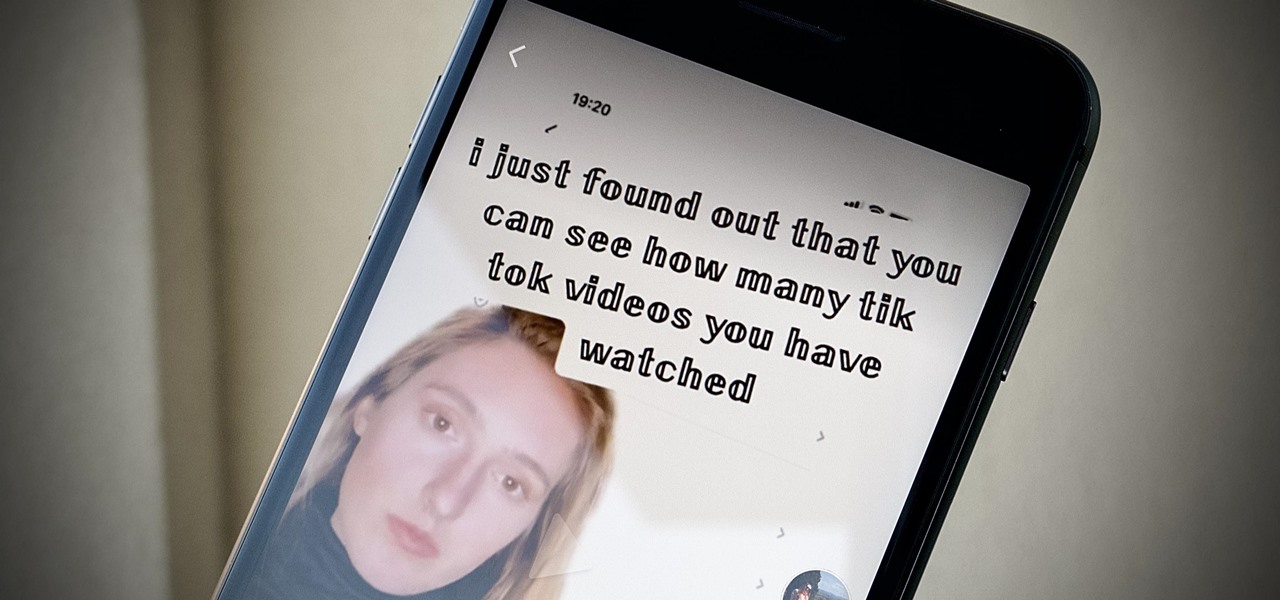
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.
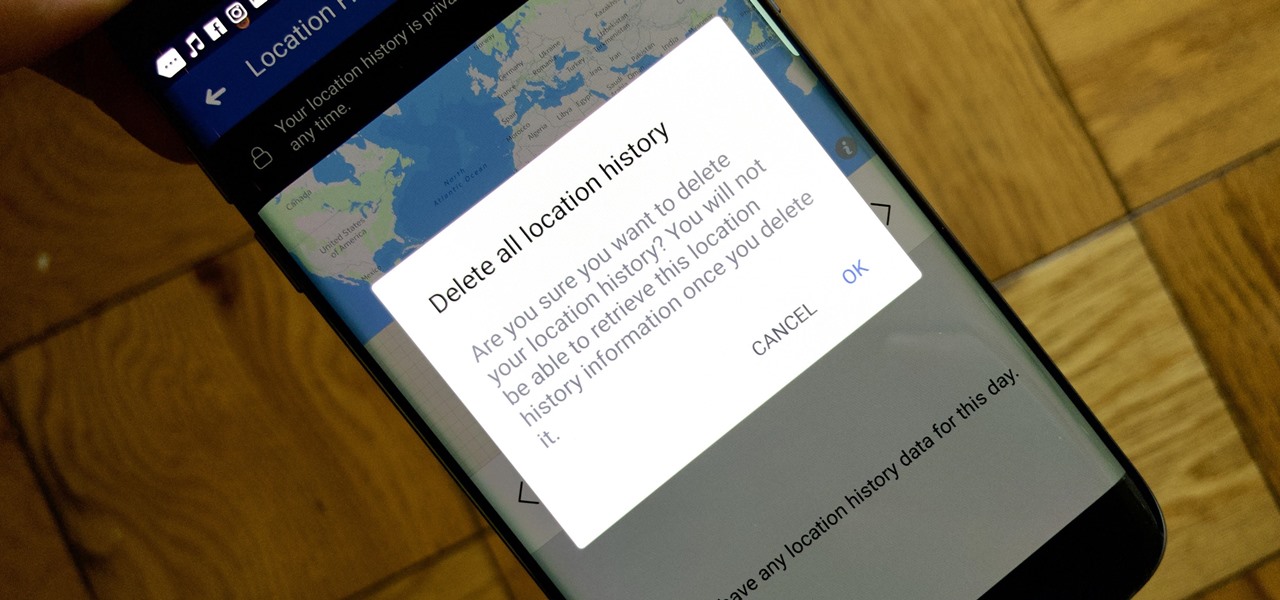
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.
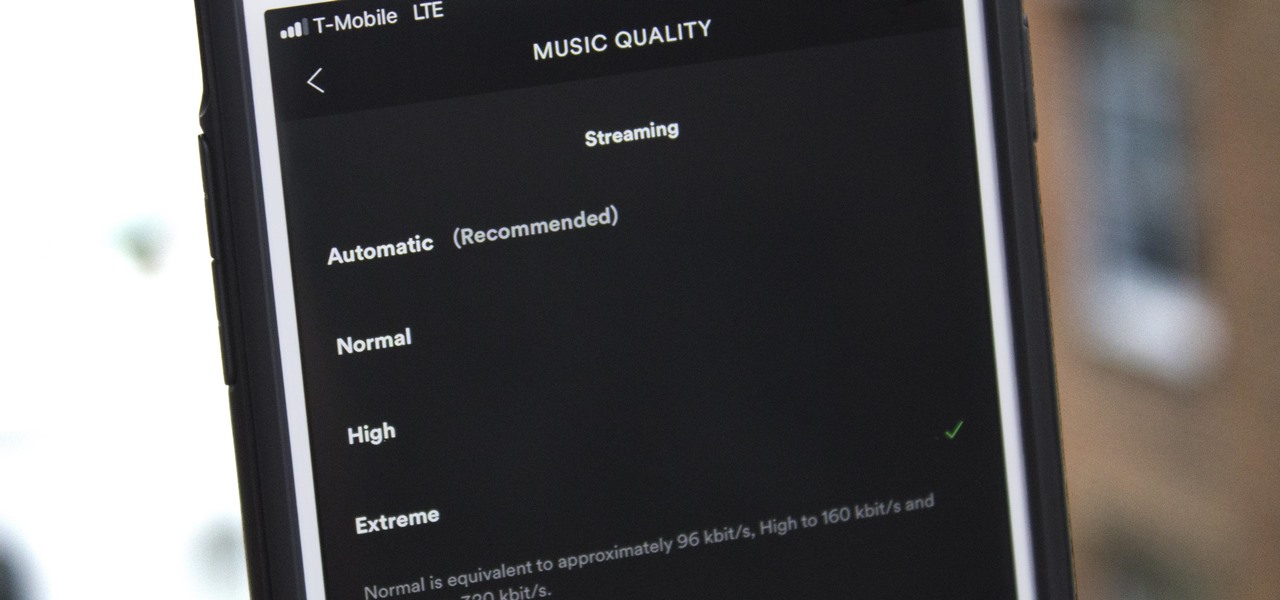
Spotify's massive song catalog can be streamed in decent quality on iPhone or Android without any tinkering. But if you're an audiophile, you've probably noticed that the sound quality can fluctuate from time to time.
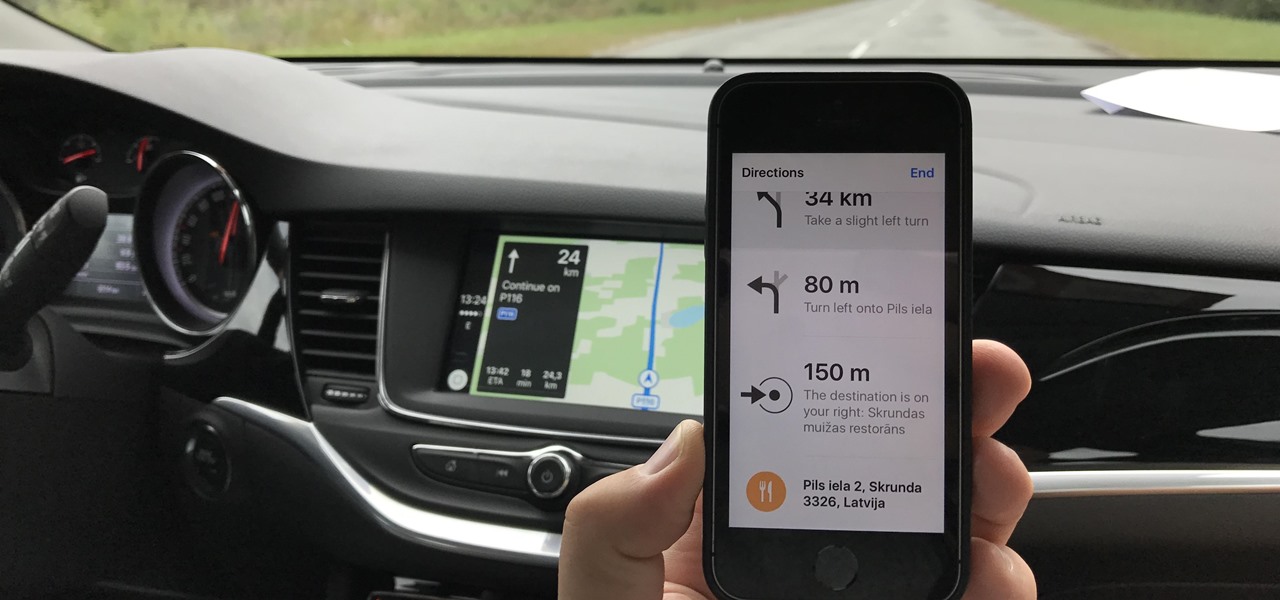
According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

Oftentimes, seemingly insignificant, nondescript features have the most impact on enhancing our Android's usability. A great example is Nougat's inclusion of customizable Quick Settings tiles, which adds greatly to the user experience by letting individuals tailor their expandable status bars to suit their unique needs.

Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC filing.
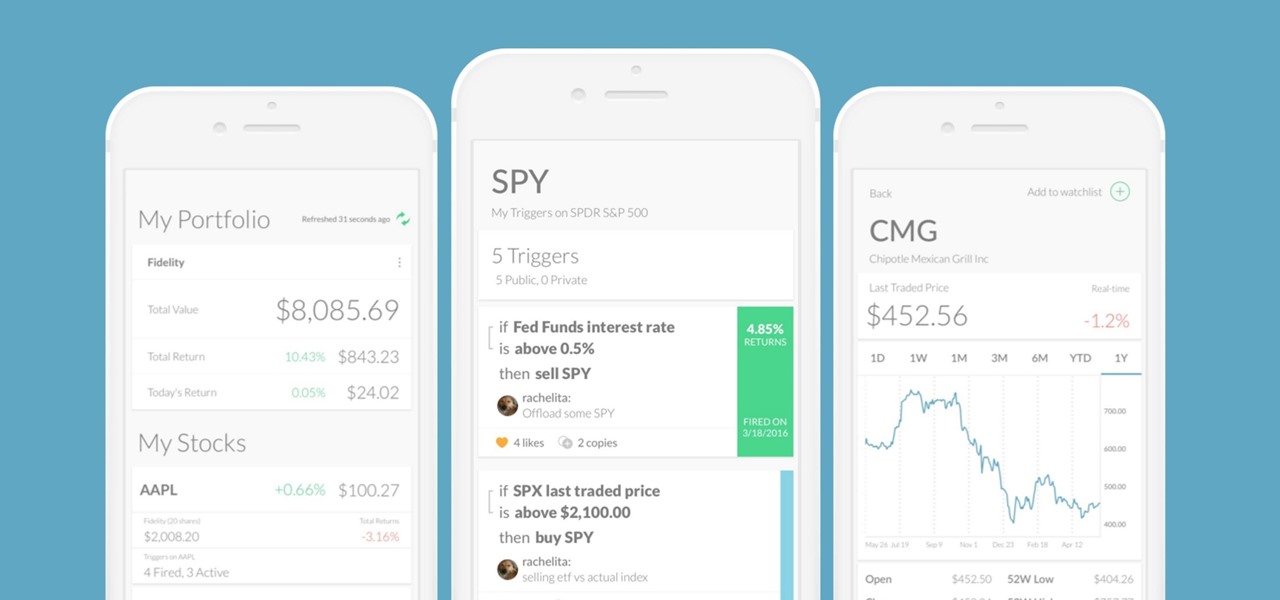
Every time Donald Trump tweets about a stock you own, Trigger Finance, or just Trigger—the app founded on the "if this, then that" rule to track and invest in the stock market—alerts you with a notification for real-time analysis of financial data.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.
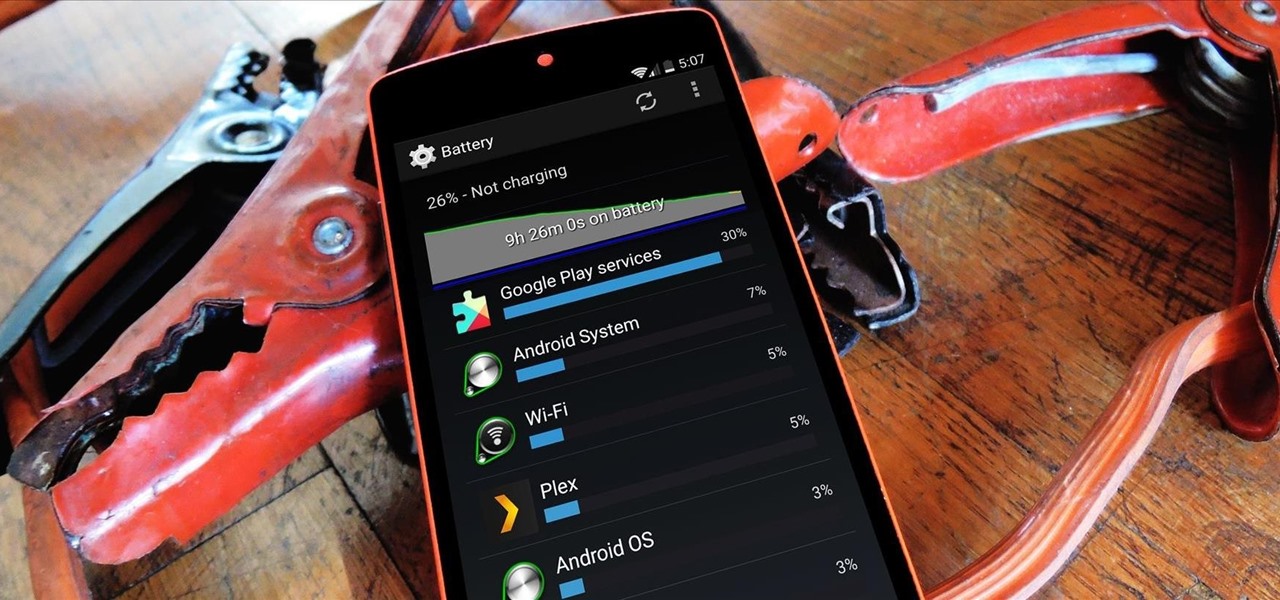
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.
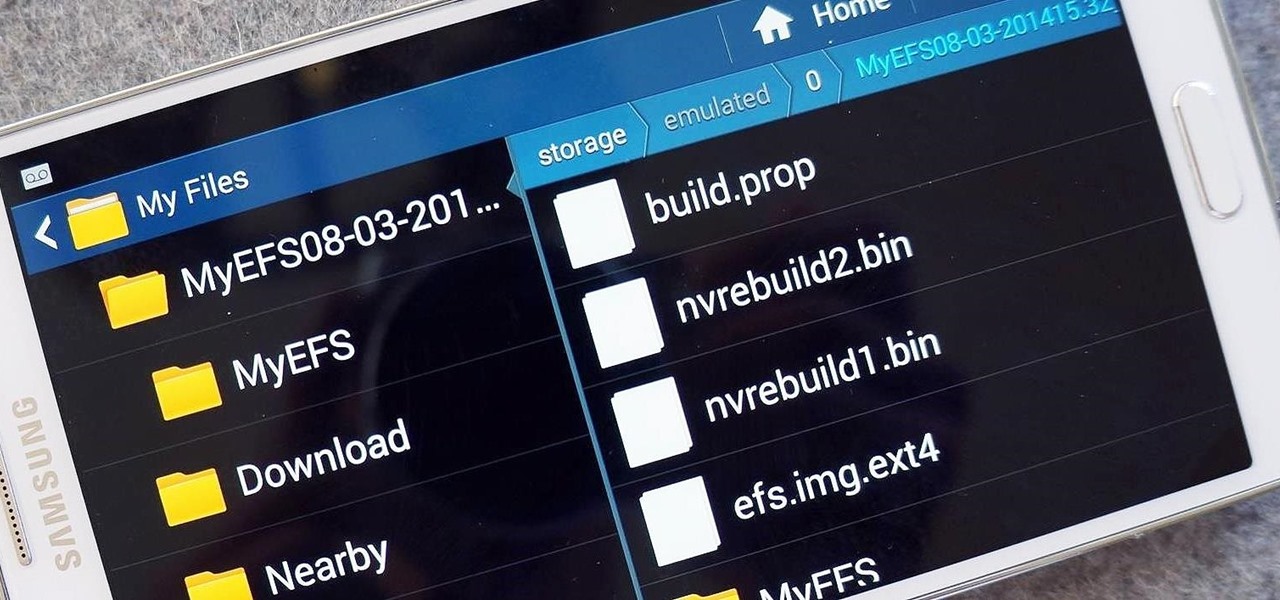
The options for customization are virtually endless when you're rooted and have an unlocked bootloader and custom recovery. However, there is always risk involved when flashing new mods or installing new ROMs. I always make backups in case something happens, but when I'm testing certain mods out, I sometimes get a damaged EFS partition.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).
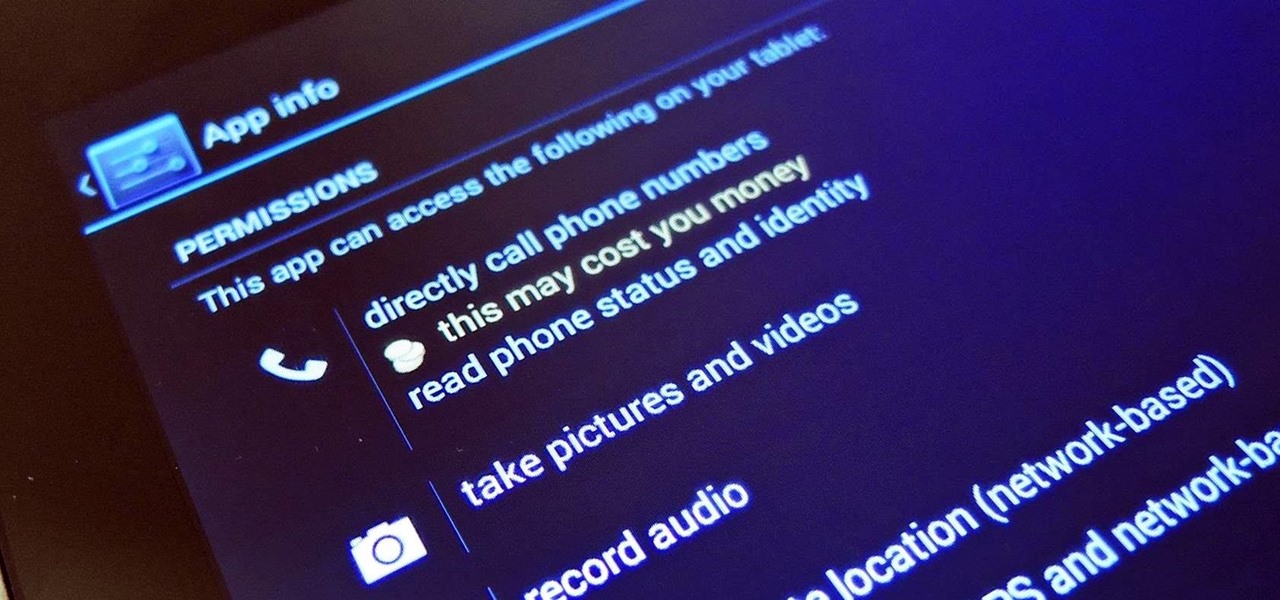
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

This video shows us how to use the following functions in Excel: average, count, counta, min, max, and sum. First, start off by create a set of numbers to work with. After that, click on an empty cell that you want to use for the functions. To do an average, click on the functions button on the top right corner of the menu bar, you'll see a list of all the functions that are available. Select average, and then highlight all the numbers that you want to find the average of. Repeat the exact sa...
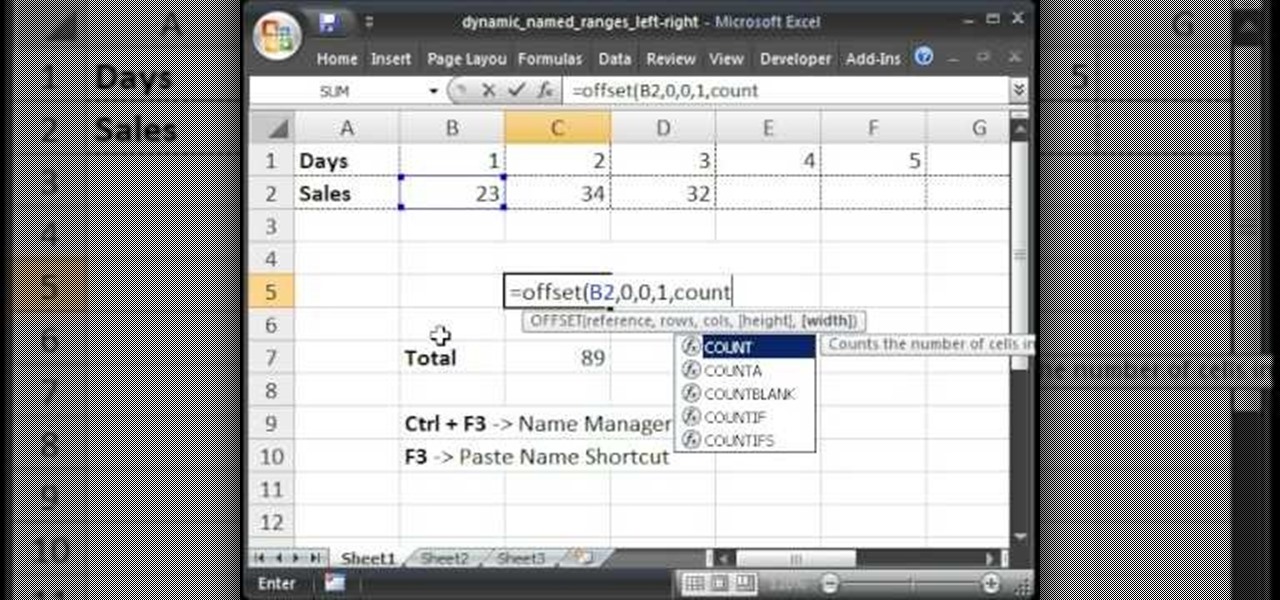
Teach Excel describes how to create a dynamically updating named range that goes from left to right using Excel. First, you define the named range by highlighting the cells containing numbers in a certain row. In the name box to the left of the formula bar, type the name of the data. In this example, the numbers correspond to sales, so type "sales." To check if the named range works, click on an empty cell and enter =sum(sales). That should return the sum of the highlighted cells. However, as...