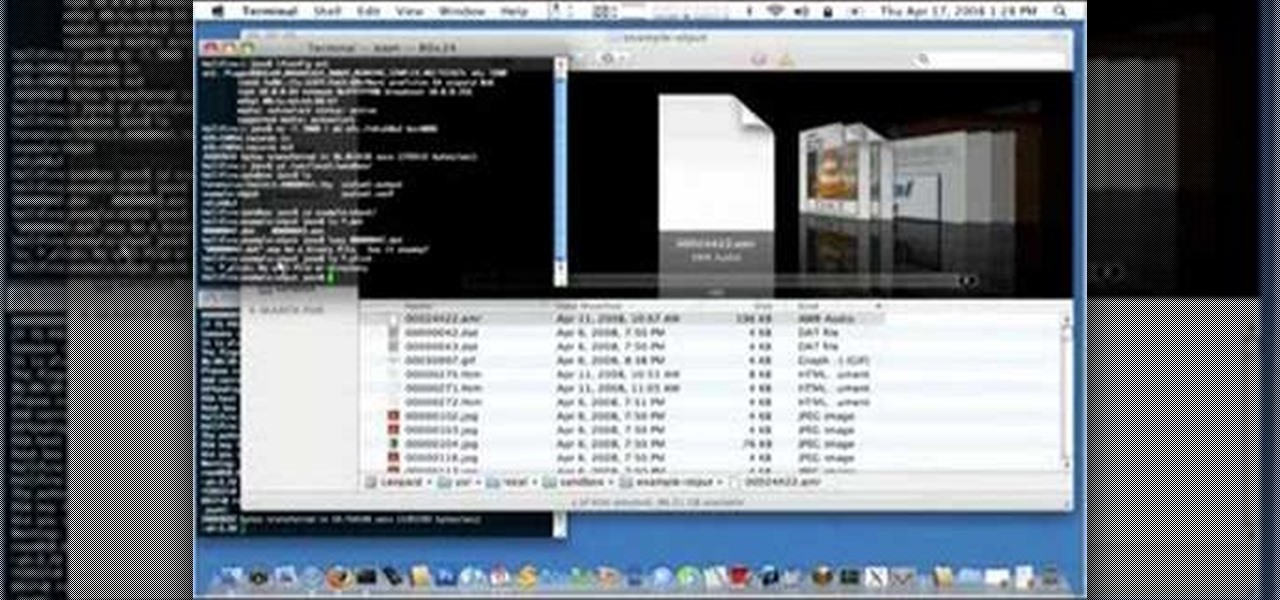
In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!
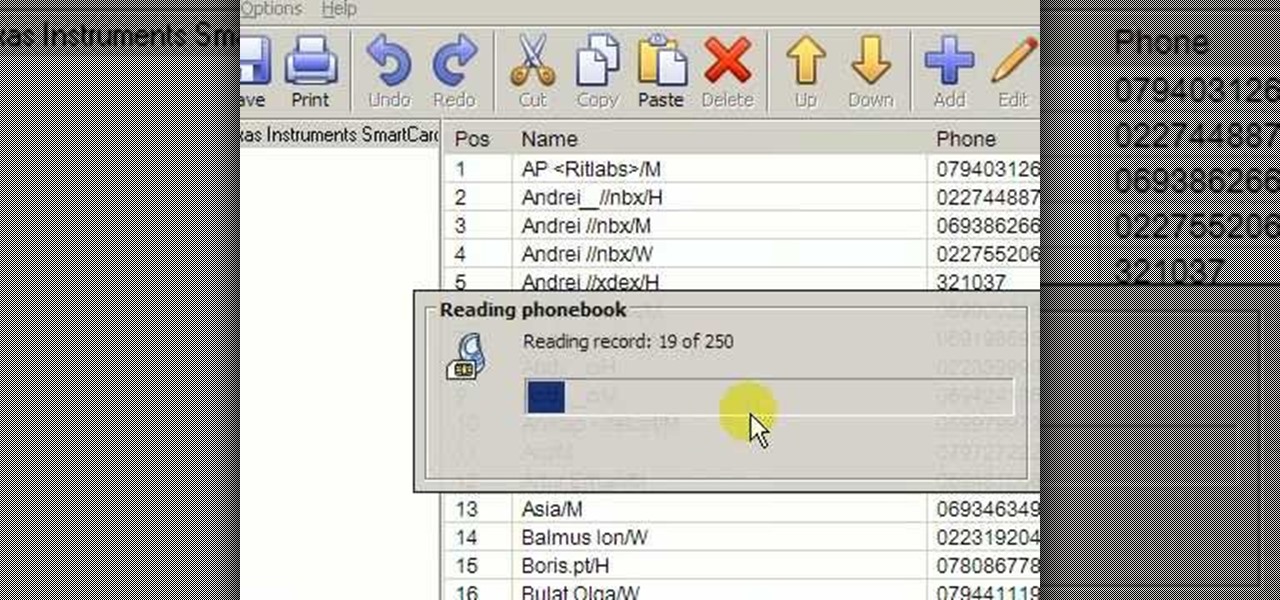
Accidentally deleted your address book? Got some sneaking suspicions you want to clear up? Got something to hide - permanently? In this video you'll learn what hardware and software you need and how to use it to recover deleted text messages, or, conversely, how to delete data permanently from your SIM card. Don't worry - we won't judge.
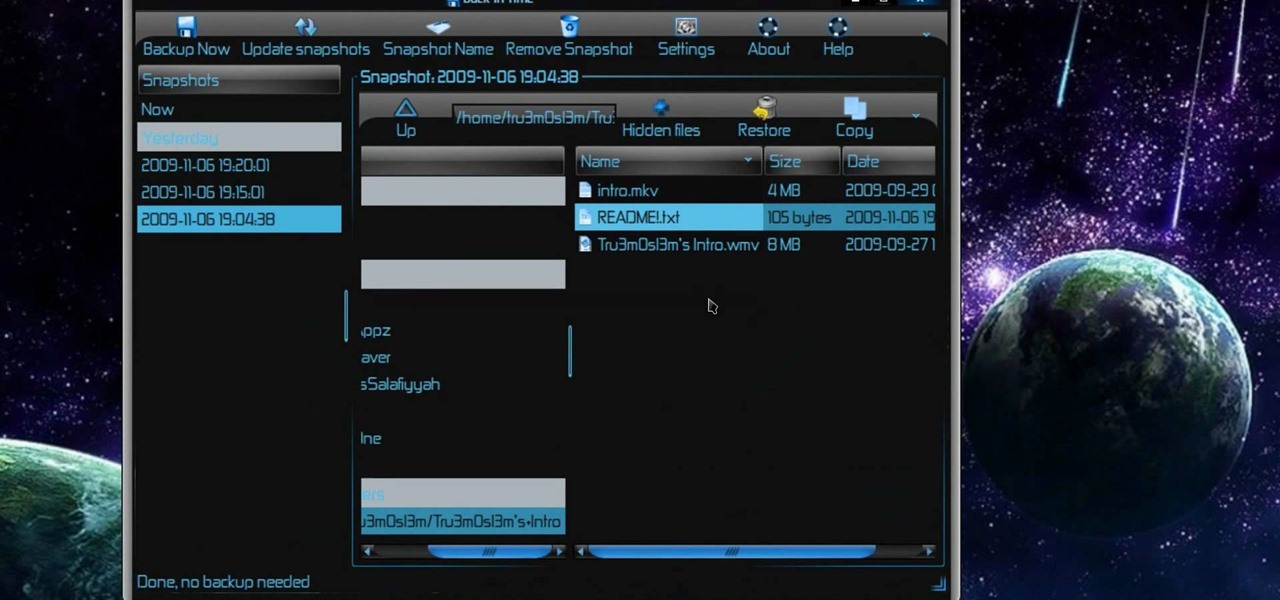
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

This shows a step by step method for using the Wii controller to output MIDI control to Apple Logic Pro and "conduct" MIDI with the Wii stick! This is a way cool Wii hack that makes the bluetooth controller work with Logic. You need to install another program to receive and control the data.

Here's a demo which shows a way to produce WAV sound files with TEXT using Photoshop or any photo editing software.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Using morphs to pre-process UVs is a great trick for any version of modo. You can leverage the embedded morph data to massage a model in 3D prior to UV projection. If that doesn't make sense, watch the video and learn how to pre-process UVs using morphs in modo.

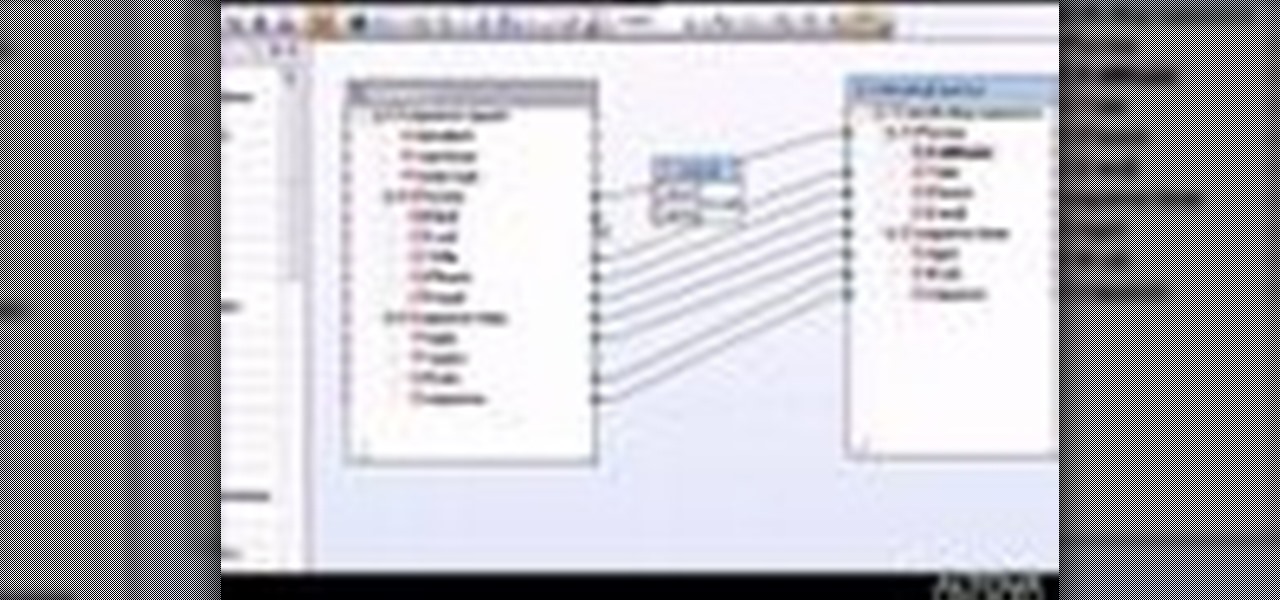
Learn how to use MapForce to map or transform XML data in a visual way, creating XSLT 1.0 or 2.0 transformation stylesheets, XQuery 1.0 documents, or program-code in Java or C# in this tutorial, which demonstrates a simple mapping from one XML schema to another. Take a look!

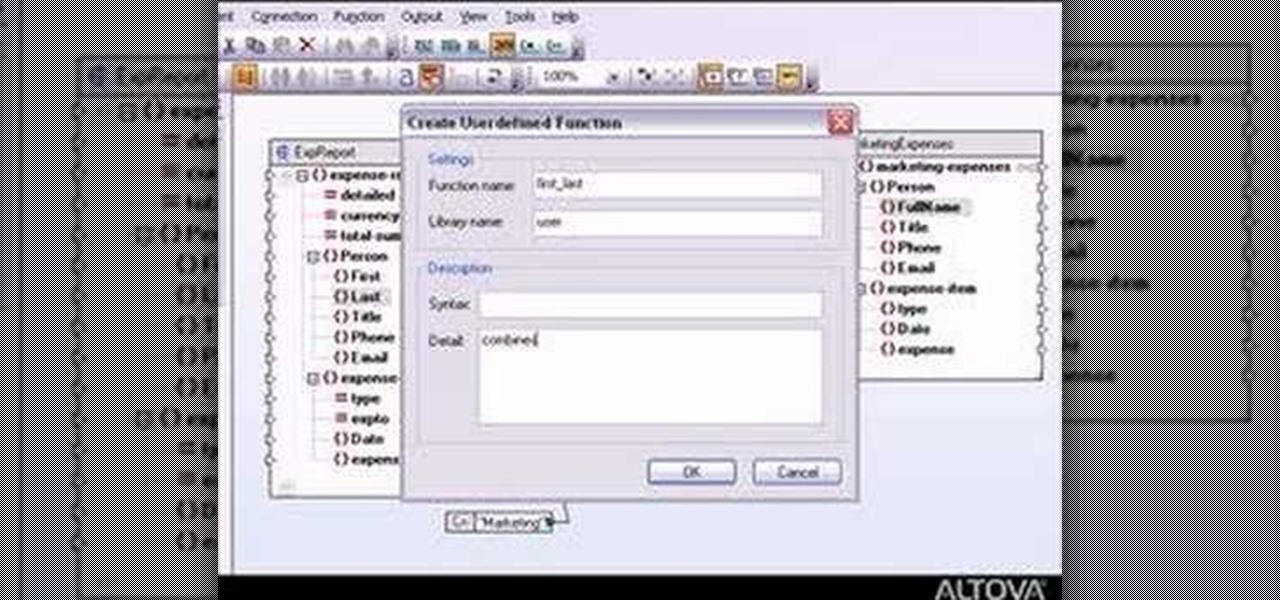
MapForce includes a powerful visual function builder that lets you create new data processing functions in a graphical way using existing functions and libraries. Learn how to combine multiple separate functions that returns a single result with this tutorial.

In this ASP.Net video lesson, you will learn how to display data in your ASP.NET 2.0 Web applications through some of the new databound controls.

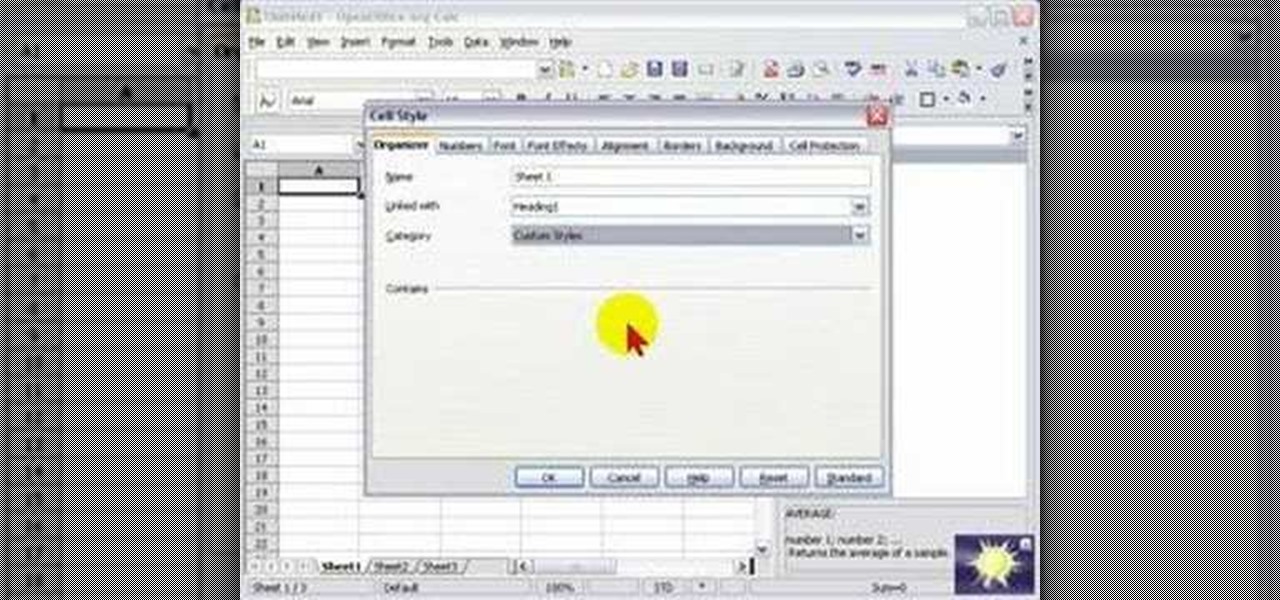
In this screencast, we look at how changing the page style of each sheet in your spreadsheet can enable you to apply different formatting settings for each one.

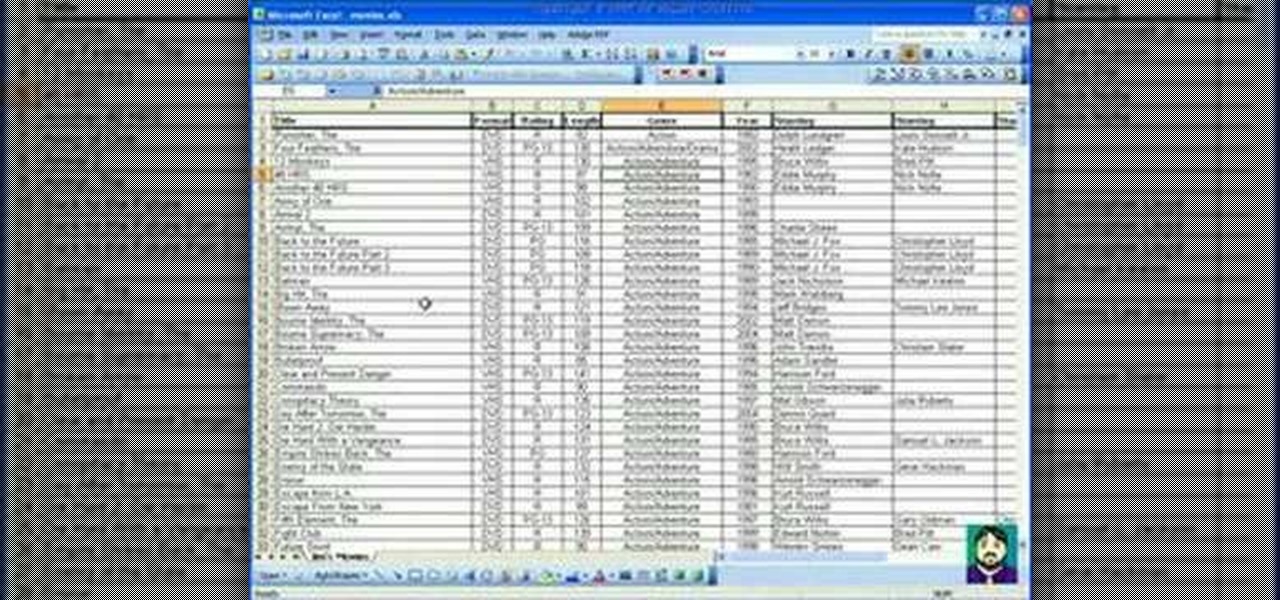
How to use Microsoft Excel as a simple database and how to organize and sort data on the fly.

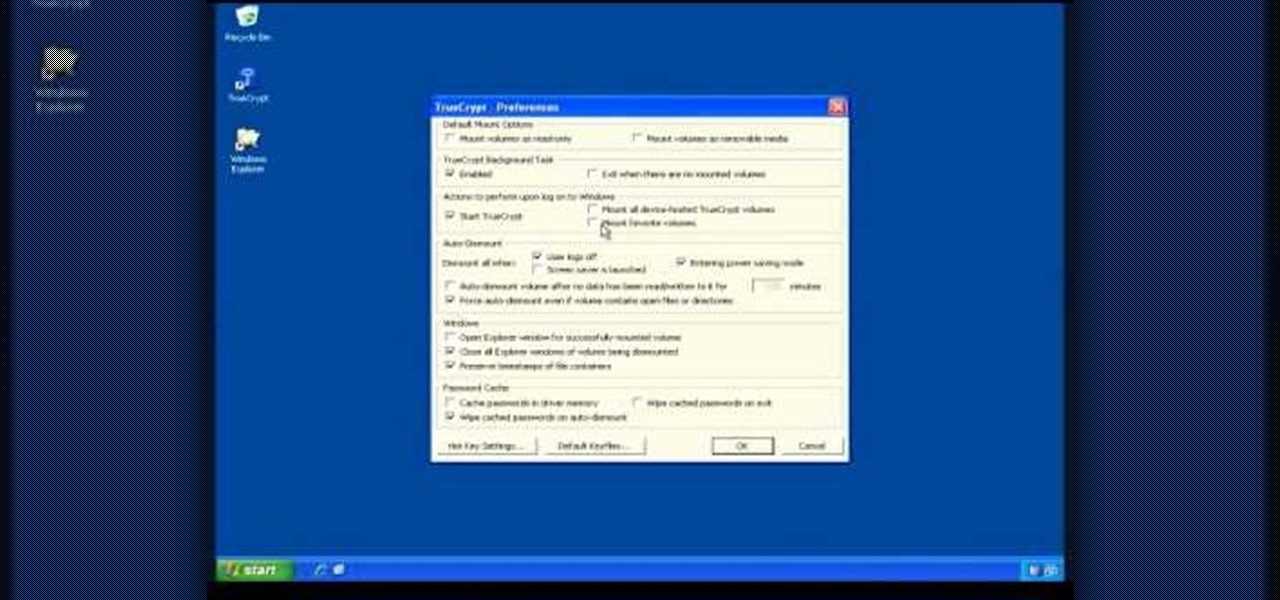
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

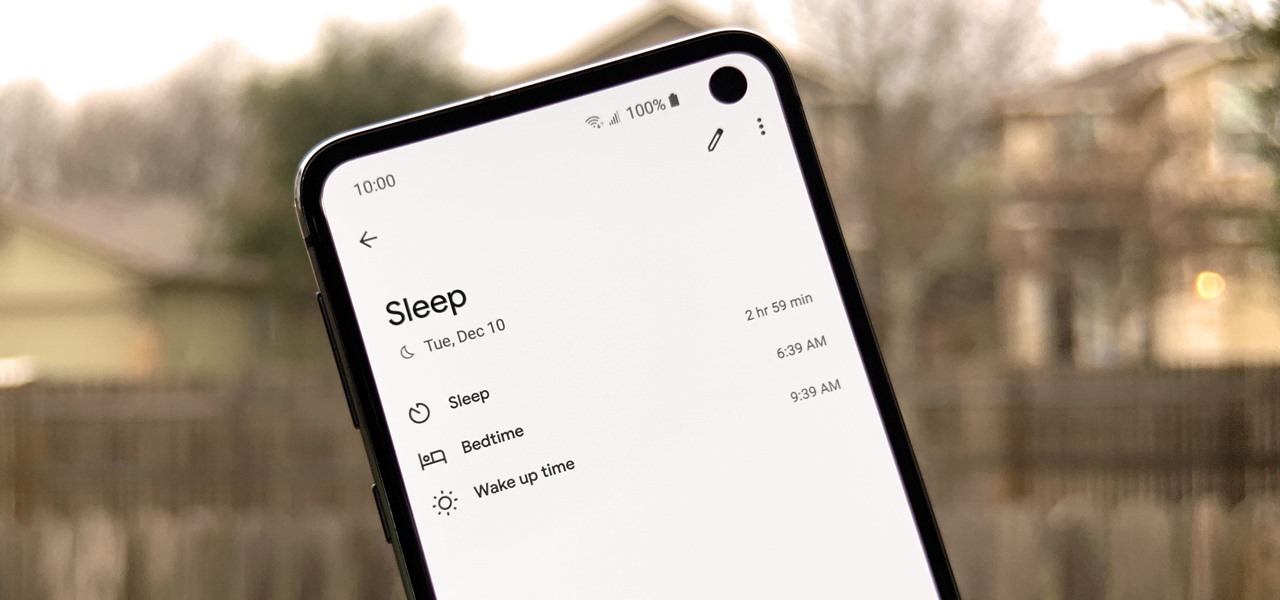
When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Many midrange phones are being manufactured without a gyroscope sensor—the Moto X Play, third-generation Moto G, and several of Samsung's Galaxy Grand models, among others. It's not exactly an essential smartphone sensor, and leaving this out keeps the phone's price point down, so it's an understandable omission.

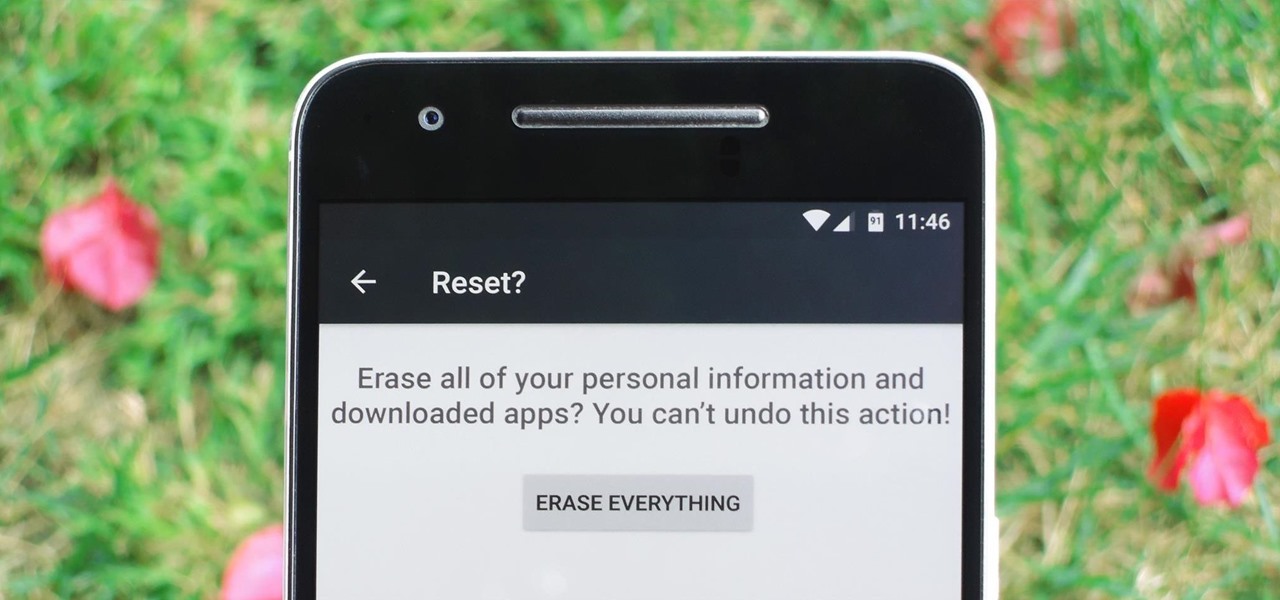
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Much like the Chromecast, Android TV devices such as the Nexus Player and Nvidia Shield TV have always had those beautiful background images as their default screensaver. However, unlike the Chromecast, these "Backdrop" images, as they're called, weren't always customizable on Android TV.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

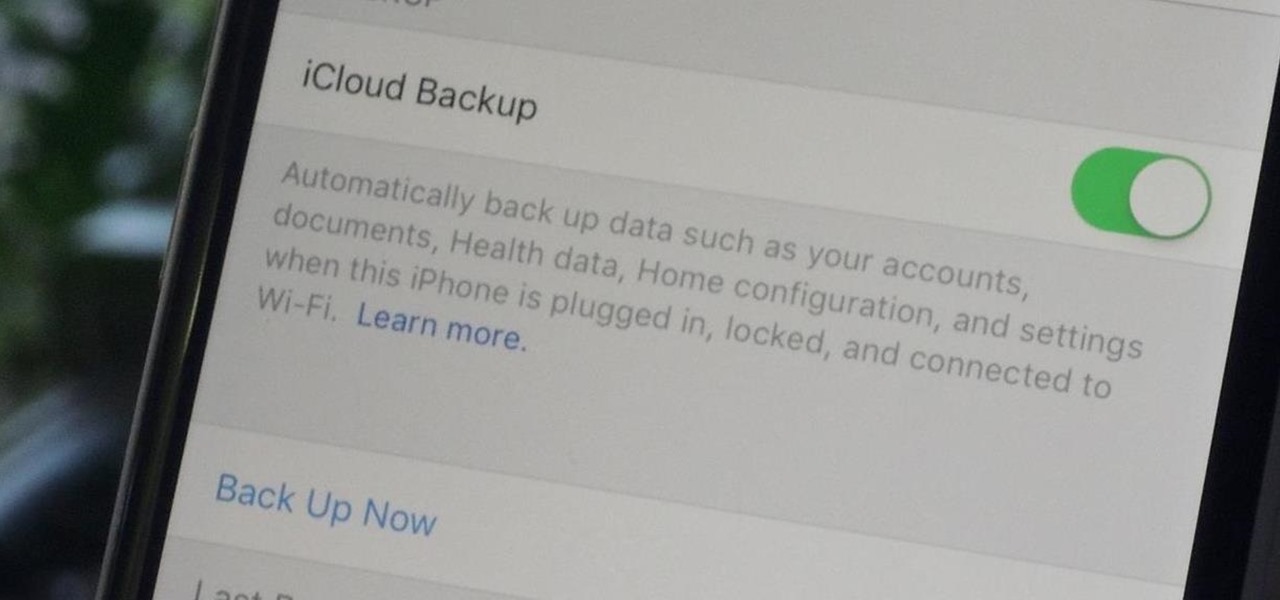
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.