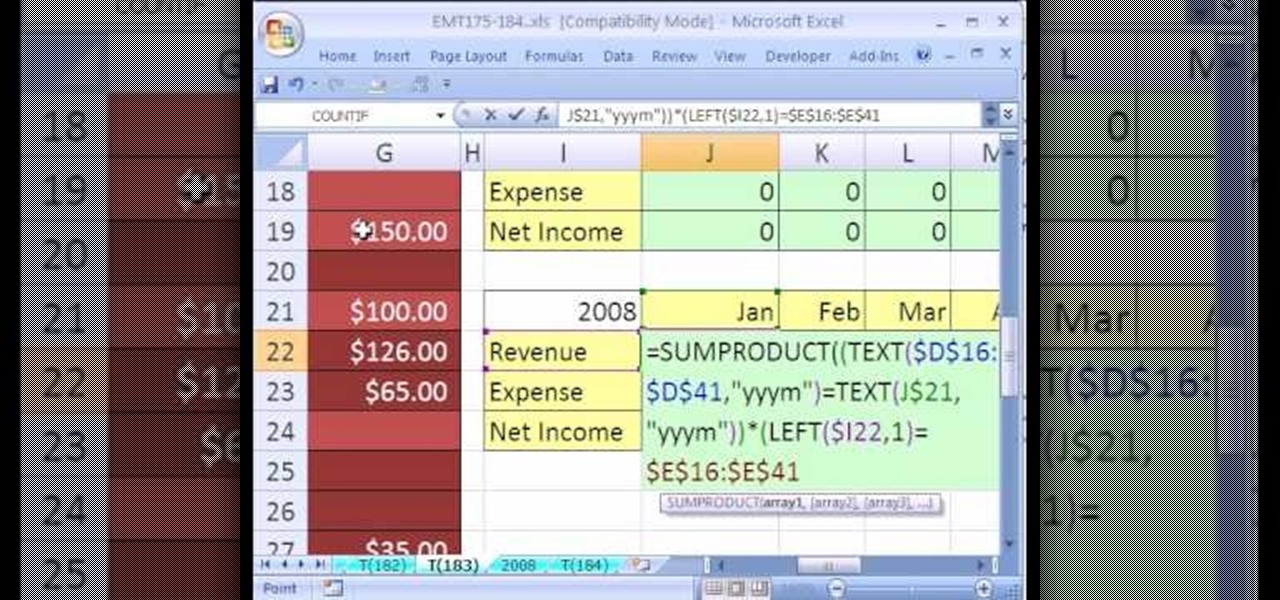
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 183rd installment in their series of digital spreadsheet magic tricks, you'll learn how to sum revenue from a table of data by year and month using the SUMPRODUCT, TEXT, SUM, IF & LEFT functions in an array formula.
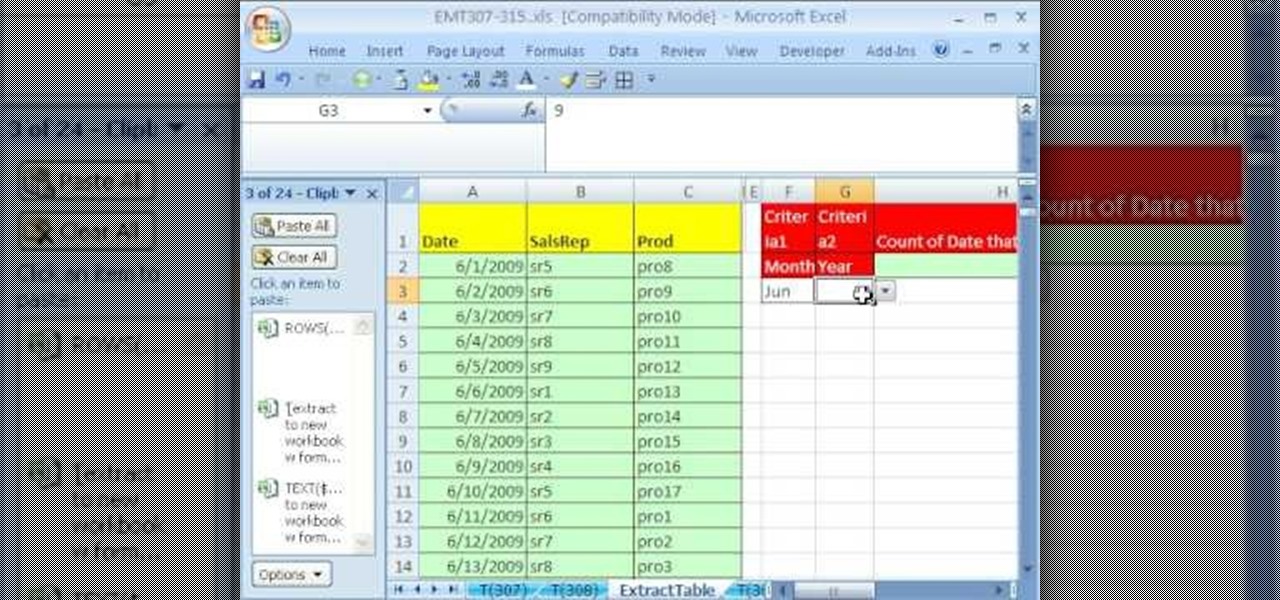
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. With this video tutorial from ExcelIsFun, the 308th installment in their series of digital spreadsheet video tutorials, you'll learn how to extract data to a new workbook by array formula. Functions used include IF, ROWS, INDEX, TEXT, ROW and SUMPRODUCT.
In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

We're living in the age of Big Data. As the primary force behind everything from targeted marketing campaigns and online search algorithms to self-driving cars and even space exploration, massive sets of complex data stand at the heart of today's most exciting and important innovations.
If you have a limited mobile data plan on your iPhone, you know how tricky it can be to stay within your given allotment. Large app installs and updates, 4K resolution videos, and photo backups can waste precious data resources in no time. And apps like Apple News, Facebook, Mail, and Netflix eat data like it's candy. But you can nip the problem in the bud by restricting data hogs from your cellular network.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

The photos and videos you take with your iPhone contain bits of information, known as metadata, including the location where they were taken. This metadata makes it easier for Photos to organize your media, but put these photos and videos in the wrong hands and anyone can find out where you live or work. Luckily, iOS 13 makes it easy to wipe the geotag from images and videos before sharing.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

While having no internet connection is definitely a bad thing when you need it, you can at least bide your time until you're back online with a hidden Easter egg inside of the Google Chrome browser. This gem unlocks a secret side-scrolling game that can keep you busy during your downtime.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

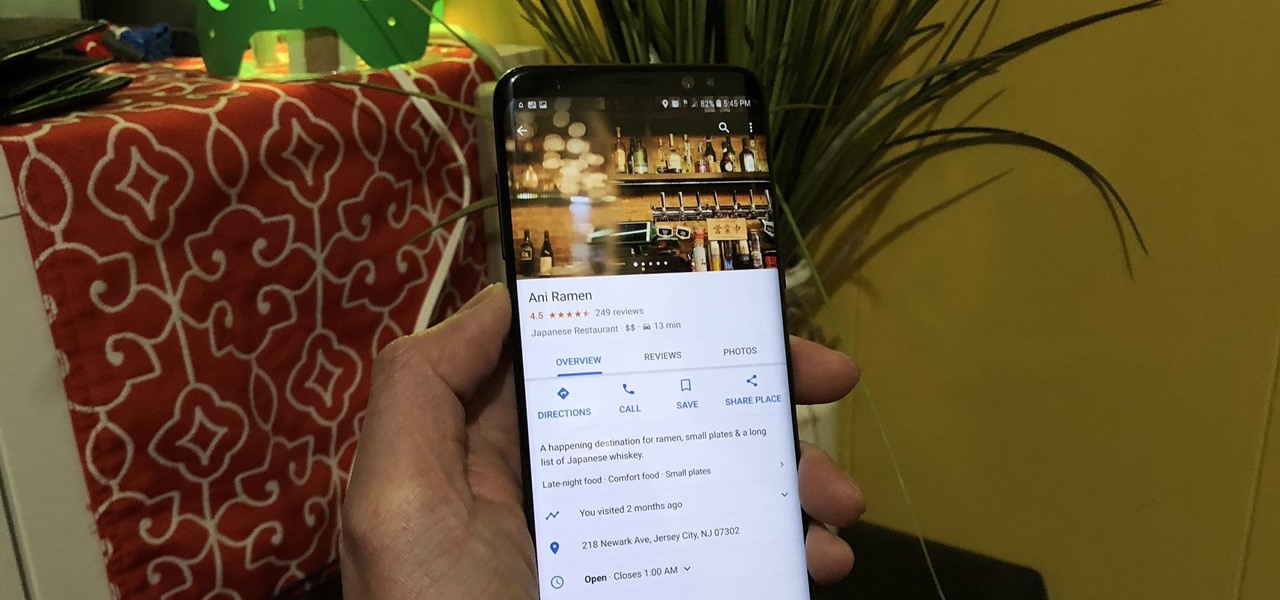
Going out to dinner on a Saturday night can be more trouble than it's worth when you find yourself waiting for hours on end just to be seated. Thankfully, Google Maps has some very useful data that can save you from a headache the next time you head out to your favorite restaurant.

This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

As if being pregnant did not come with enough worry, a new study found that certain antibiotics are linked to an increased risk of spontaneous abortion, or miscarriage — a terrifying finding for any expectant mother.

Today at Microsoft Build 2017 in Seattle, Washington, ScopeAR announced that their mixed reality smart instruction development platform, Worklink, will now work with the Microsoft HoloLens in addition to the mobile devices that are currently supported.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

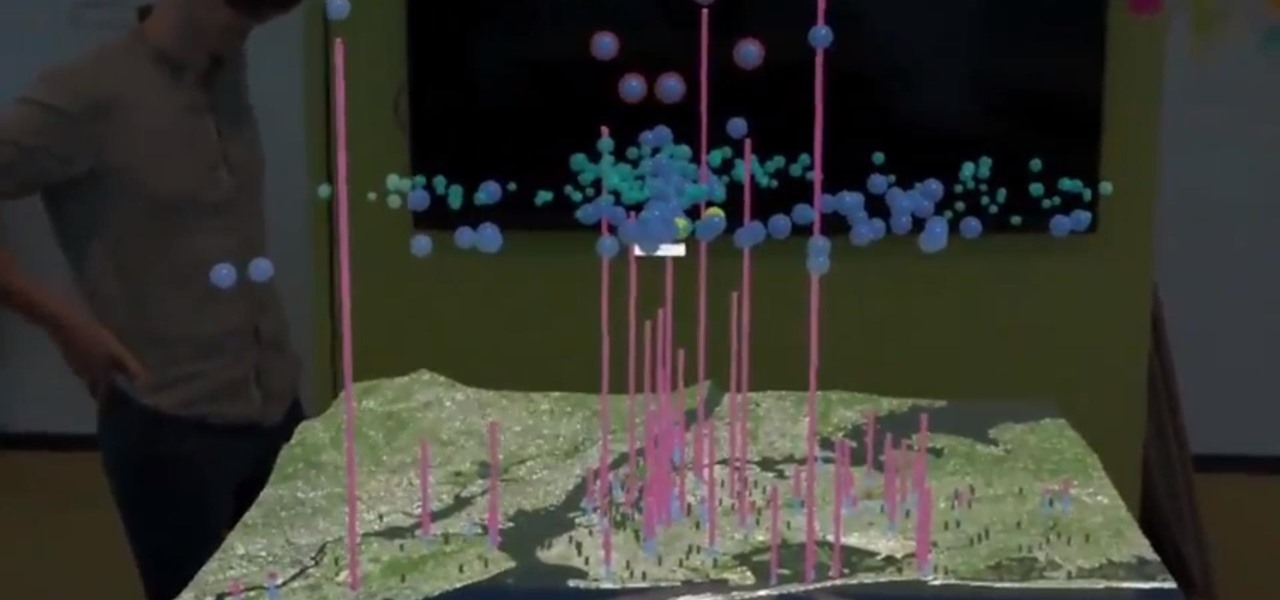
Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our head, sometimes it is what we say. In the case highlighted below, it's where we walk.

If you've ever wanted to live in the Matrix—or at least the iconic digital rain data visualization that Neo saw when realizing he was, indeed, the "one"—you can now do that with the Microsoft HoloLens. Just download The Red Pill.

New technologies in current-generations smartphones allow for much faster charging—Qualcomm Quick Charge 3.0, VOOC Flash Charge, and USB Type-C, for instance, can charge a phone up to 4 times faster than traditional methods. However, the majority of phones on the market still don't support these standards. So for the rest of us, I'll go over an easy tip that can charge any smartphone as much as 25% faster.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

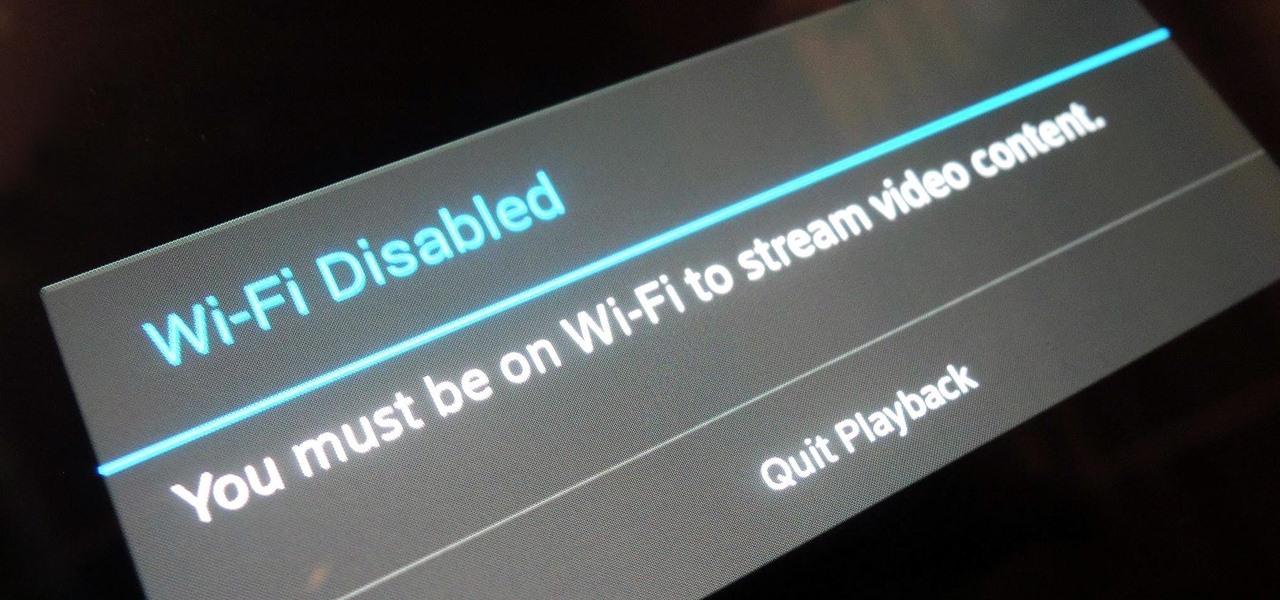
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.

The sensors in your mobile device are integral for gaming (try to beat my Temple Run 2 score), as well as many of the basic Galaxy S3 features like Smart Stay and other fancy additions. But sometimes those sensors can become overly sensitive or just downright unusable.

Repetitive use of apps over time will eat up your storage space with by caching data on your device. This can be useful at first, speeding up your apps by not requiring them to re-download frequently used data, but as a cache grows, even the initial performance improvements can be outweighed by the unwelcomed loss of storage space. And if a cache grows too large, the time it takes an app to access the cached data can be even slower than the time it would've taken to re-download the data in th...

Whether you're pressed against your bedroom window, hidden deep inside your linen closet, or lounging on the rooftop, finding that area of maximum Internet speed around your house is usually just trial and error. And when you finally find the sweet spot, apps like Speedtest.net can help you determine how fast your Wi-Fi or cellular connection is overall on your computer or smartphone, so you know your full capabilities. But, if you want to know exactly how fast your Samsung Galaxy Note 2 is u...

We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated.

While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.

We depend on our hard drives for our data storage and if they stop working, our important data can be lost, this could cause many problems like losing school projects making us to do them again, losing jobs and other problems . So here is a tutorial, on how to make a dead hard drive work again.

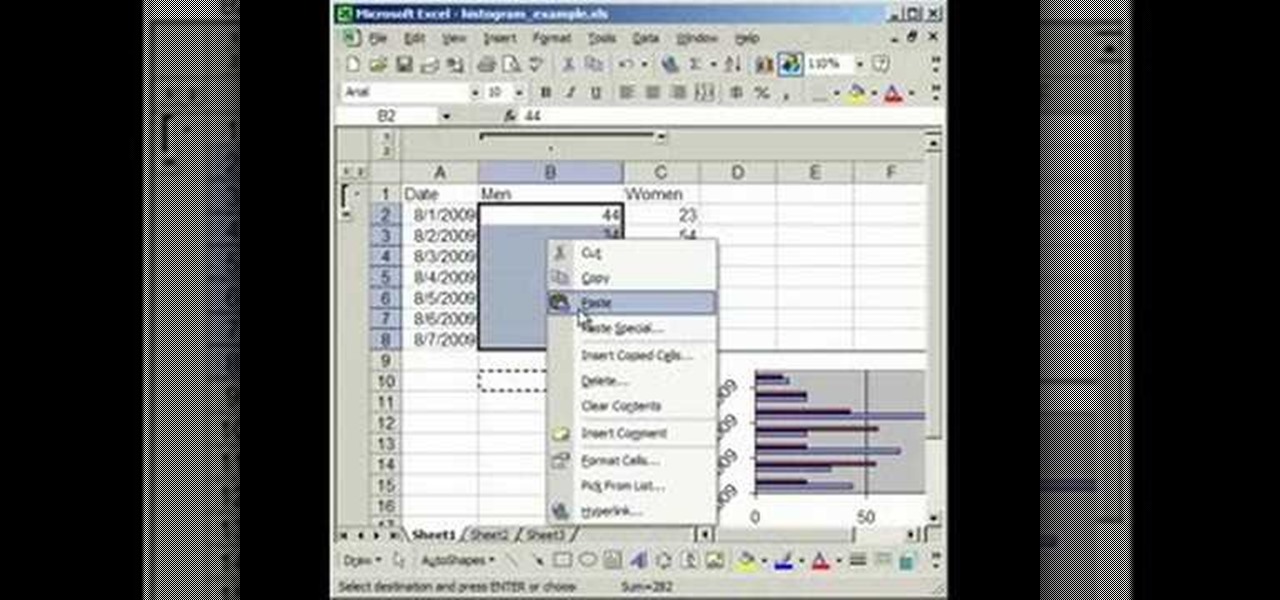
In this tutorial, we learn how to make a histogram chart in Excel. To create a vertical histogram, you will enter in data to the chart. Then, highlight all of the data and go to "insert", "chart", then choose a regular column chart. Grab a regular 2D column and then make sure your values are correct. Then, right click and go to "chart options", then take the legend off. Now, make these columns all touch each other by right clicking over the columns and formatting them. Go to "options" then ch...