How To: Beginners x86 Linux Assembly
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

Whether you are vegan, lactose-intolerant, or cooking for someone who is, standing before the non-dairy milk shelf in the grocery store can be daunting. Instead of playing it safe with the two most common milk alternatives—soy and almond—perhaps you should explore a few other choices that tend to be overlooked.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.
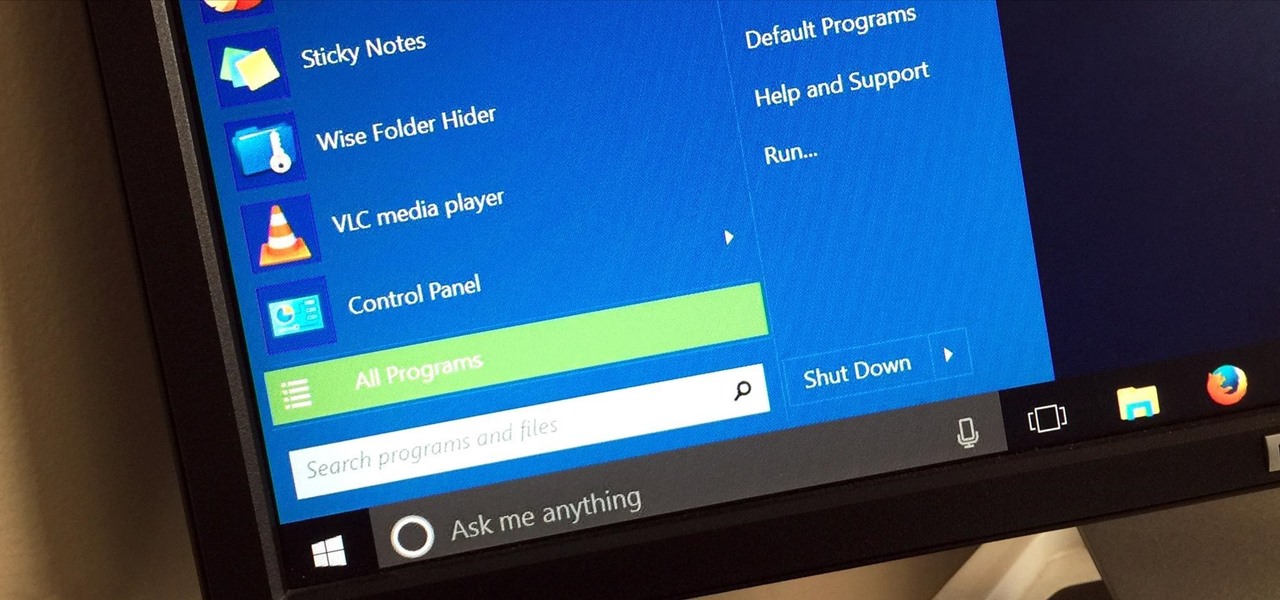
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Windows 10 is due to be released on July 29th, and the majority of existing Windows users should be eligible to upgrade to the newer version for free.

Video: . Project Overview

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Getting a new phone is exciting, but having access to its exclusive apps ahead of its release is what we're all about here on Gadget Hacks.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

Journals are a great source of hilarity and embarrassment, detailing everything from your elementary school crushes to those super awkward middle school dances. While rereading your old hand-scrawled entries might make you cringe, that old journaling habit could benefit you as an adult.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

This video shows how to easily record your voice and insert a sound podcast to your WebQuest or webpage using Dreamweaver. It shows how to have the sound play on the same page without auto starting. The tutor initially goes to the Start button and in All programs selects Accessories. Next he selects Sound Recorder from the Entertainment option and records his voice reading out the content of the page. He then saves the file in the folder called websites creating a subfolder in the name of ‘so...
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

This video will teach you how to increase your PC's virtual memory. Or in other terms, the Random Access Memory space to be used when doing something with your computer. 1. Press CTRL+ALT+DEL. Go to Performance tab. 2. Check the Commit Charge which is also the amount of virtual memory used. 3. Right-click the My Computer shortcut on your desktop. 4. Go to Advanced tab. 5. On the Performance box, click Settings button. 6. Click the Advanced tab. 7. At Virtual Memory box, click Change button. 8...

The standard way to sort your notes and to-dos in Reminders has always relied on you putting them in the correct list and group. Then came smart lists for flagged and scheduled tasks, followed shortly by a smart list for tasks assigned to you. In iOS 15, Apple brings yet another way to find your reminders more easily — tags.
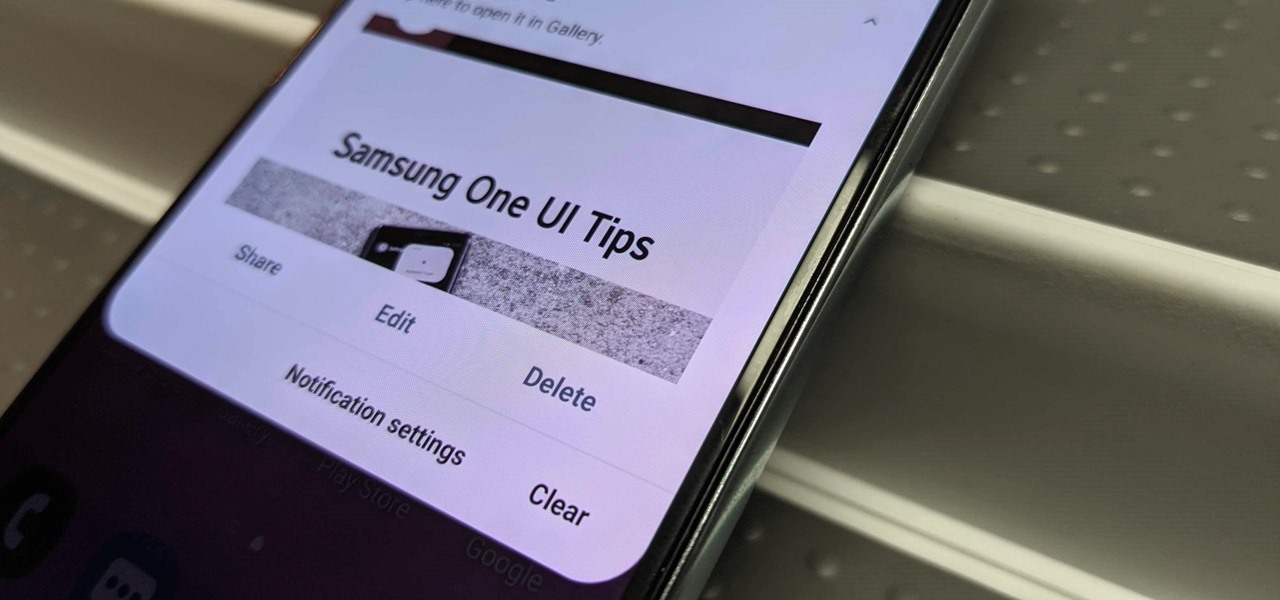
An unfortunate byproduct of Samsung's One UI version of Android is redundancy, where you have the Google/AOSP way of doing things mixed with Samsung's methods at the same time.

Bus stops can provide shelter in the event of rain, and now they also protect you from augmented reality squid.

We've got almost a full year until the next installment of Ghostbusters arrives, but in the meantime, it turns out that Sony is about to launch an augmented reality experience that will let fans use immersive computing to combat the franchise's whimsical apparitions.

Parkinson's disease, a condition that can impair movement and coordination, affects over 10 million people worldwide. And with around 60,000 Americans being diagnosed every year, we're on track to see almost one million Parkinson's afflicted Americans by 2020.

Samsung removed the Bixby key on the Galaxy Note 10 and Note 10+ and gave the power button dual functionality. In the process, they changed the way you power off the phone and made taking screenshots a bit tricky. Fortunately, it's not too hard once you get used to things.

While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or Android.

While Gucci is among the most recognizable brands in fashion, you would be excused for not realizing that the company makes sneakers as well.
If you don't want the large and permission-hungry Facebook app on your phone, the perfect solution is to create an app icon for the Facebook mobile site on your home screen. The website version of Facebook doesn't run background tasks, has no distracting notifications by default, you won't be giving Facebook as much data, and your phone's battery life will be improved.
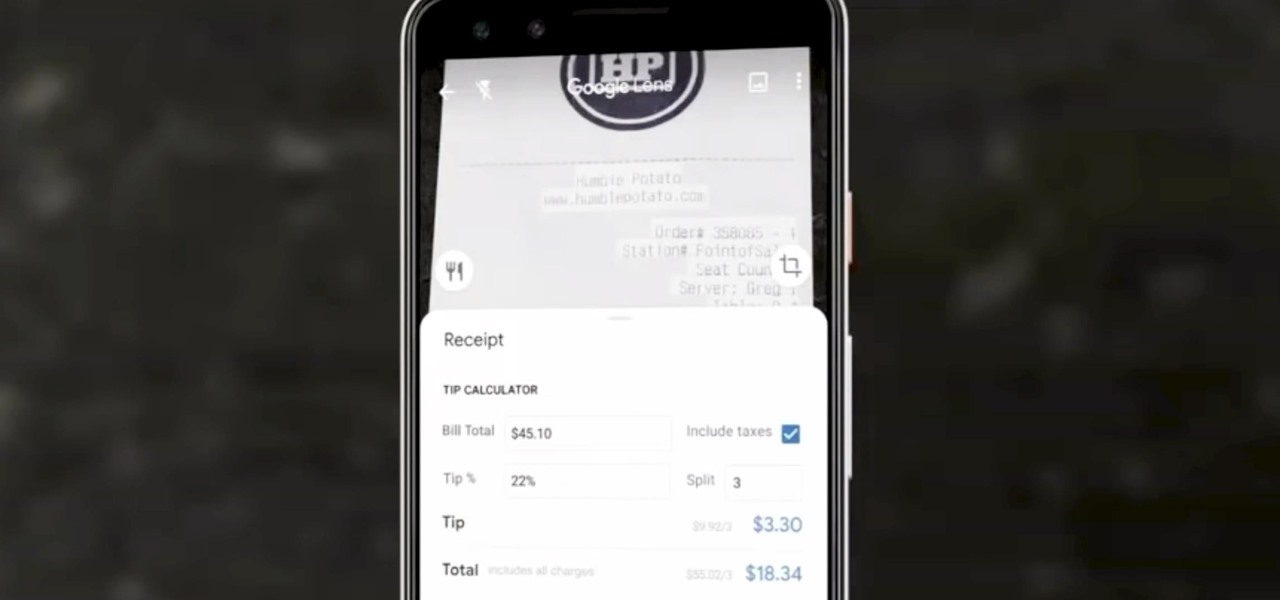
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have another cool Lens feature to look forward to — receipt calculations.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.
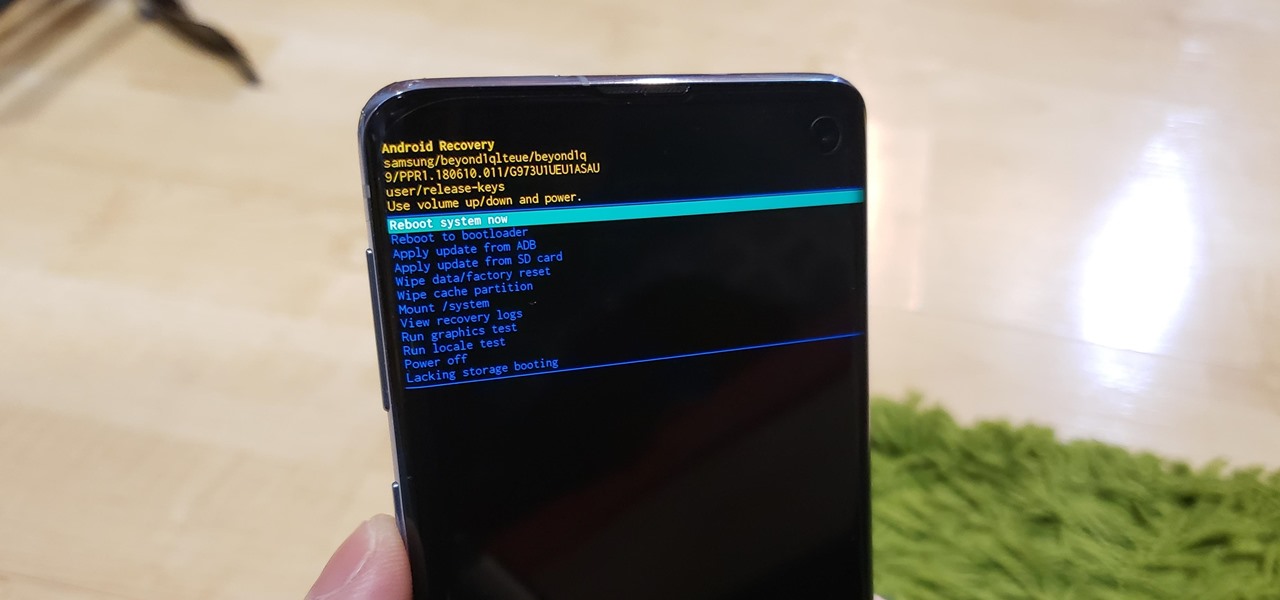
You don't need to be a hardcore modder to know the importance of booting your S10 into either recovery mode or download mode. In fact, these pre-boot menus are something everyone should be familiar with. The former can help you get out of soft bricks, while the latter lets you use utilities like Odin and Smart Switch to flash firmware files and fix your phone when all other solutions fail.
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

It turns out that Dr. Grordbort's Invaders is not the only Magic Leap demo to become a reality for the Magic Leap One.