We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

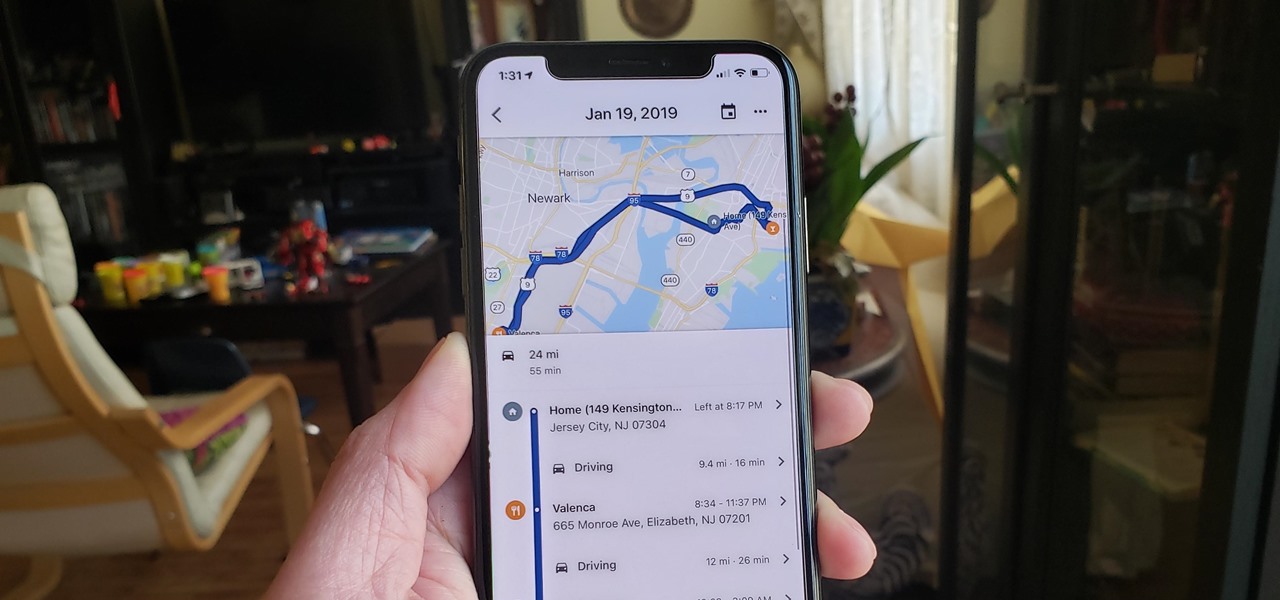
With so much stimuli in today's world, it can be hard to keep track of all the places we've visited and the events we've attended. Thankfully, a great feature in Google Maps lets you view a detailed log of your phone's location history to help you remember where you were at almost any given point in time.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Take a close look at the image above. These bugs spread a deadly parasite that infects thousands of people each year. They also live in the US, and it's important to know where they are and whether you need to worry that they're carrying a dangerous infection.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

I get along with most of my friends just like anyone else. We chat on the phone, go out drinking, and play video games—and we choose who to hang out with and when. That same sort of freedom is hard to find on Facebook.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

So, the in-person conversations between you and your friends has slowed down to a near halt, thanks to everyone's obsession with texting, Facebook, and over-uploading pics to Instagram—socializing at its best. It could also be that you're just not interesting enough anymore in person.

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

Breathe new life into your Instagram profile picture with another layer of self-expression. It's the perfect way to show another side of your personality without sacrificing your current IG profile photo.

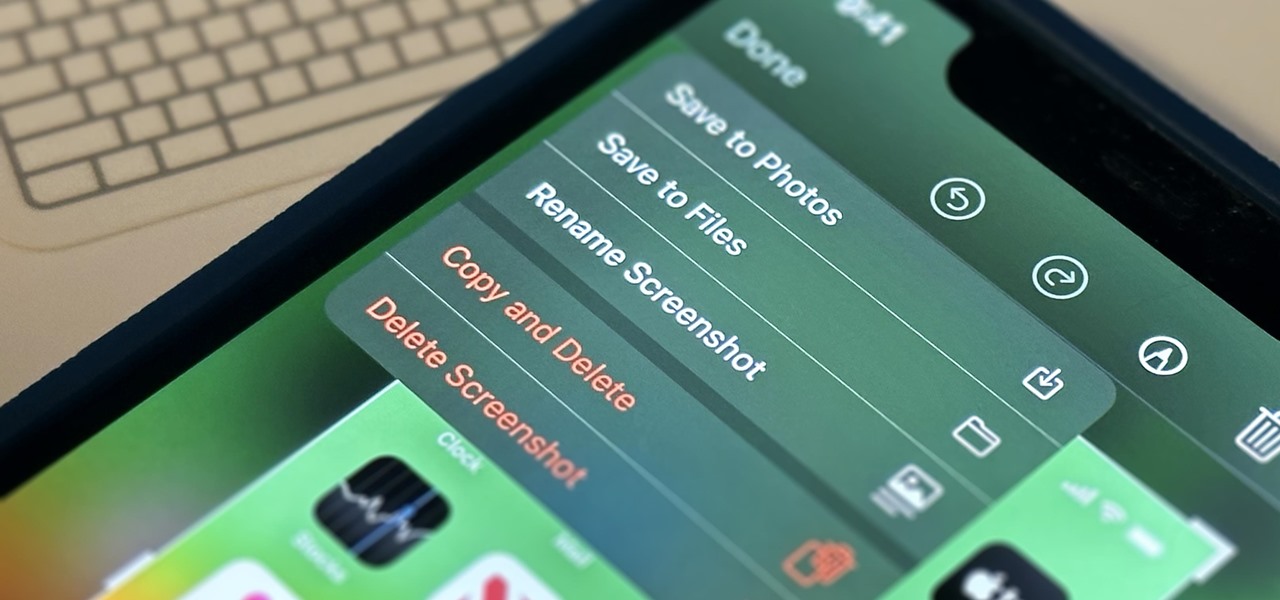
Apple's screenshot feature is a near-perfect tool for saving images of your iPhone's screen to keep for yourself or share with others. But iOS is missing one thing that would make it almost flawless: a way to rename your screenshots from their original IMG_1234.PNG file name.

Android 12L and Android 13 have a taskbar just for tablets that lets you quickly open recent, suggested, or pinned apps and drag and drop apps into split-screen mode. While the taskbar is meant just for tablets and foldable devices, you can unlock this new feature for your Android smartphone with a bit of tinkering.

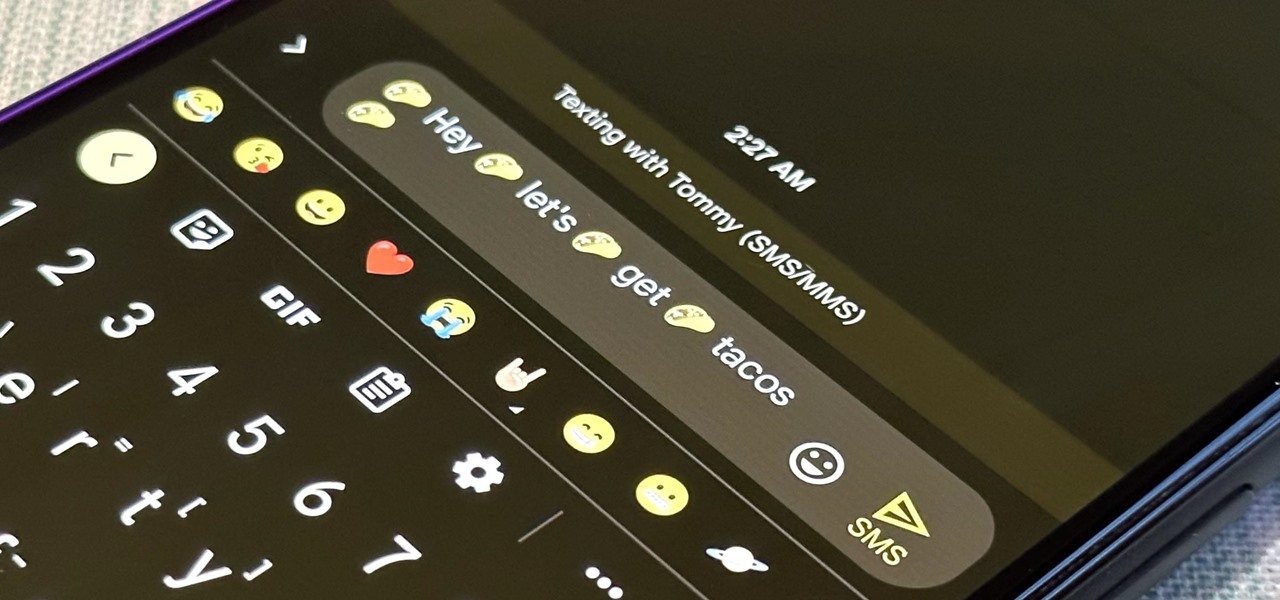
Emoji characters make messaging more fun, and Google has continuously added convenient and fun ways to insert playful symbols into your conversations using Gboard. After getting Emoji Kitchen in early 2020, we now have Emojify, a tool that automatically adds emoji to your message drafts.

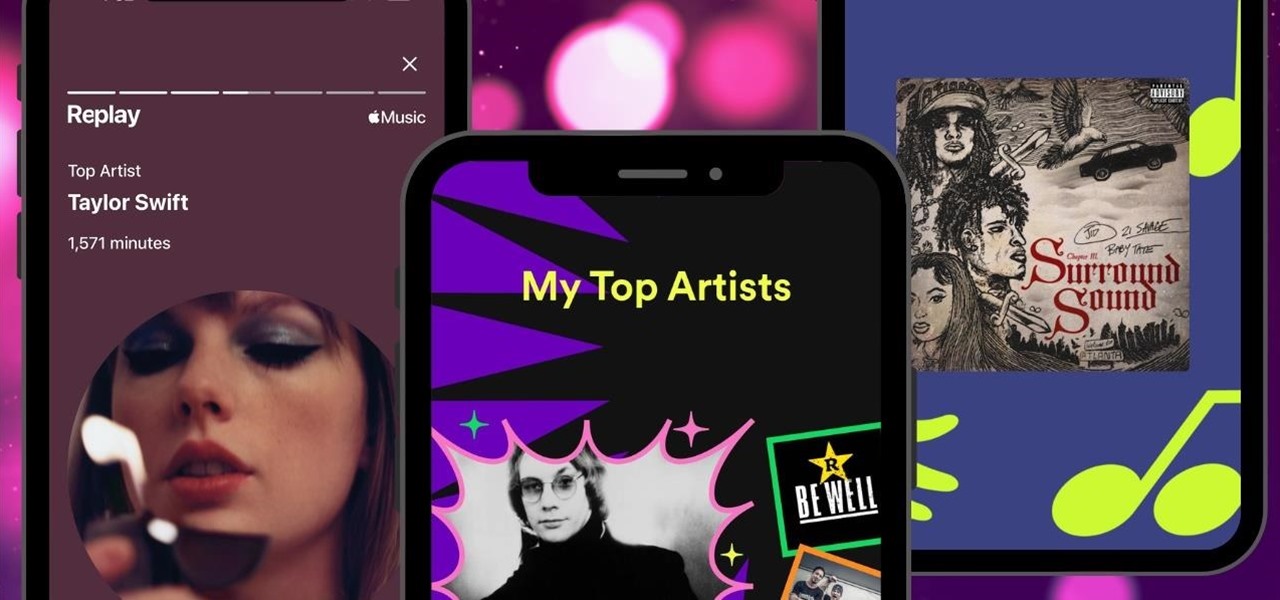
It's that time of year again. No, not the holiday season … the "share your year in music listening" season. And no matter which music streaming service you use, there's a way to find and share (or not share) your activity from 2022.

While you can use Google Assistant on your Android phone to identify songs playing around you, you may still prefer Shazam's music recognition service, which has been available on Android since 2008 — a full nine years before Google Assistant's audio-fingerprinting technology. If that's the case, it's even easier now to Shazam songs in seconds, no matter what screen you're on.

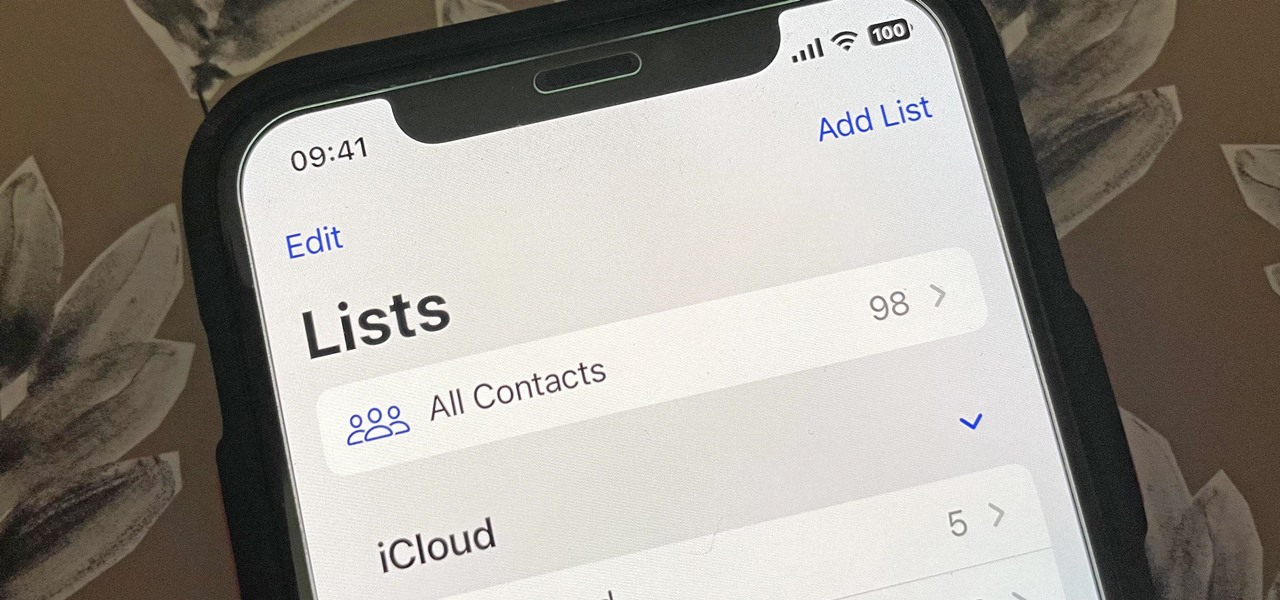
Apple's Contacts app just got its biggest update ever. Since the first iPhone in 2008, there have only been minor upgrades here and there to how you manage and interact with contacts. That changes with iOS 16.

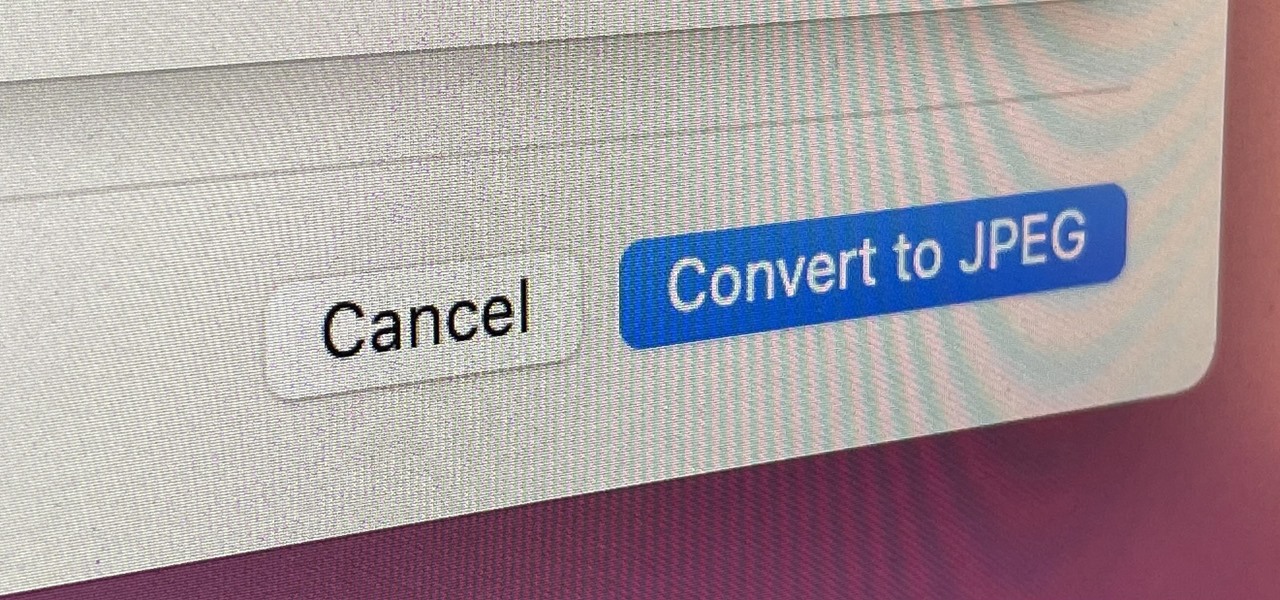
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.