
How To: Detect a pulse with two toothpicks
Check out the Pulse Trick illusion from Brian Brushwood and Scam School. As a conversation starter, Brian shows you how to use two toothpicks to detect a pulse.


Check out the Pulse Trick illusion from Brian Brushwood and Scam School. As a conversation starter, Brian shows you how to use two toothpicks to detect a pulse.

For many of us, being the interviewer is as nerve-racking as being the interviewee. You can keep your cool and quickly weed out unqualified applicants.

Just remember, for all powermoves, you have to get used to it. Train holding your body weight on the hand that you lift off with right hand for clockwise. You do not have to be able to balance a 1 handed handstand, just hold an L-kick or pike on that hand. This will strengthen the triceps. Also do not train flexibility by splits, you need all the muscles around ur legs and hands to be flexible. Just do flares and mills for flexibility.

This how-to video series is a step-by-step guide to molding fiberglass. These videos give a simple introduction to fiberglass mold construction, explained using a model aircraft cowling but the same technique applies to any fiberglass sculpture. The entire process is detailed from plug, to mold, to finished fiberglass part. Follow along with the eight steps: develop the plug, construct the parting board, lay up the mold, release the mold from the plug, prepare the mold for fabrication, lay up...

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how to mix a Reggaeton beat. Reggaeton is a genre of Latin dance music which mixes rap, hip-hop, reggae, and ragga. Salsa and merengue influences can also be heard in some songs. After becoming very popular in Puerto Rican clubs, it began spreading through parts ...

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video sequence explains how to use the wide feature on a DJ mixer.

Scam School presents four silly beer gags in this how-to video.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Basic drumming techniques and beginner drum lessons are explained in this free beginner's drum tutorial video series from our expert drummer, covering drum sticks, drum beats and fills.

Learn the basics of playing a tuba, from how sound is made to using pedal tones and controlling the tuba's volume, as our expert tuba player and teacher explains in this free tuba music education video series.

The California Department of Motor Vehicles (DMV) created this "The California Driver License" video series specifically to help new drivers understand the requirements and responsibilities of obtaining and keeping a license to drive. CA DMV examiners explain the application process, restrictions for provisional drivers, the behind the wheel test, insurance requirements, actions that can be taken against provisional drivers and driving under the influence.

This chess tutorial from Grandmaster Alexandra Kosteniuk is a perfect example of Retrograde Analysis.

This Photoshop video series is going to explain how to create a chiaroscuro lighting effect on an image. This art form was made famous by the Italian artist Rembrandt. Part one covers the origin of terms and how to create chiaroscuro dramatic lighting. Part two has instructions for downloading the image, and some very basic workspace and preferences instructions for beginners. Part three covers Duplicate Image, File Info, File Size, Eyedropper Sample, Doc Status Bar, Panels/Palettes. Part fou...

This detailed video series shows you everything you need to do to install an LED lighting gauge cluster in your Volkswagen MK4 (Jetta, Gulf, or GTI). Part 1 starts with disconnecting the battery, Part 2 has you remove the interior cluster, Part 3 you disassemble the instrument cluster, Part 4 covers LED ring installations, Part 5 goes over the interface removal, Part 6 covers the gauge face installation, Part 7 is 6 videos long (video 7 to 12) covering preparation for installing the cluster, ...

This video series shows you everything you need to know about completing a model from photographs in SketchUp. It follows Chapter 7 of the book Google SketchUp for Dummies. PART 1 shows you how to add photos to faces. PART 2 explains how to move, scale, rotate, shear and distort your texture. PART 3 shows you how to stretch a photo over a face (of your object that is)! PART 4 shows you how to stretch or scale the model until the photo texture looks right. PART 5 covers how to map photos to fa...

In this video series, Malik the magic guy explains how to do the 21 card trick then enhance it, how to do the clock trick, the paired court cards magic trick, the two pile separation card trick, the 4 Apartment card trick and the Speller trick.
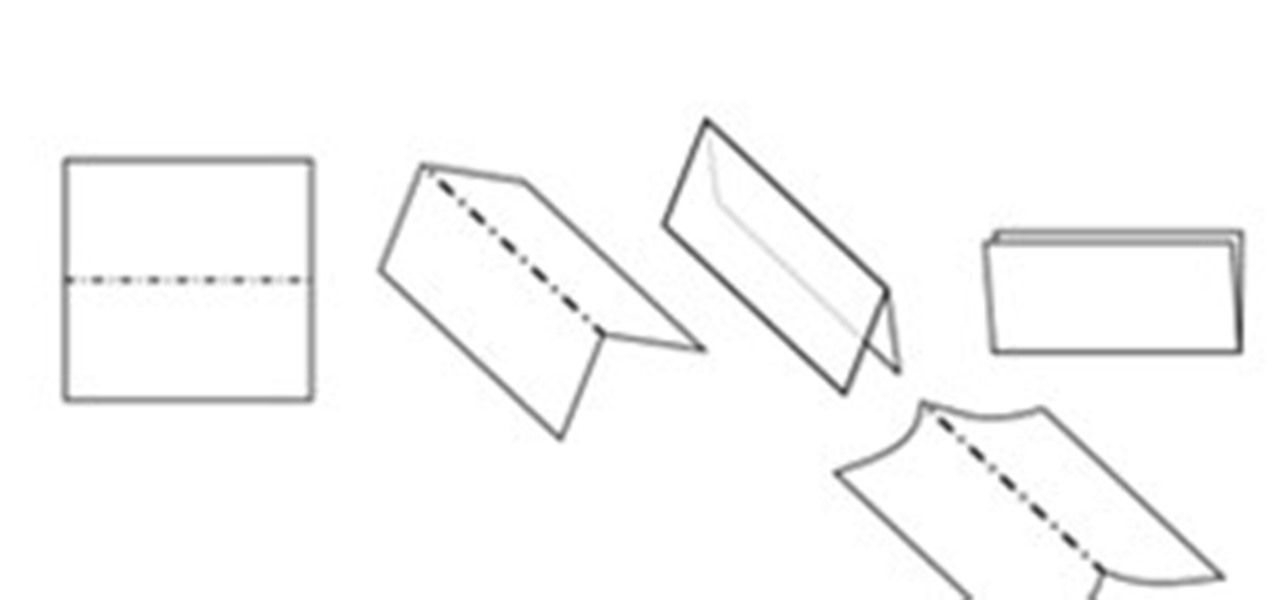
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

Ten days after Magic Leap declared that it had selected the winners of its Independent Creators Program, the company has officially released an almost full list of grant recipients.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Magic Leap CEO Rony Abovitz doesn't engage in tweetstorms often, but when he does, those tweets are bold, exceedingly confident, and there's usually a strong takeaway regarding what the company is or isn't doing. But on Thursday, Abovitz's latest tweetstorm sent an unusually flustered message: We promise, the magic we're telling you about it better than anything you've seen on video.
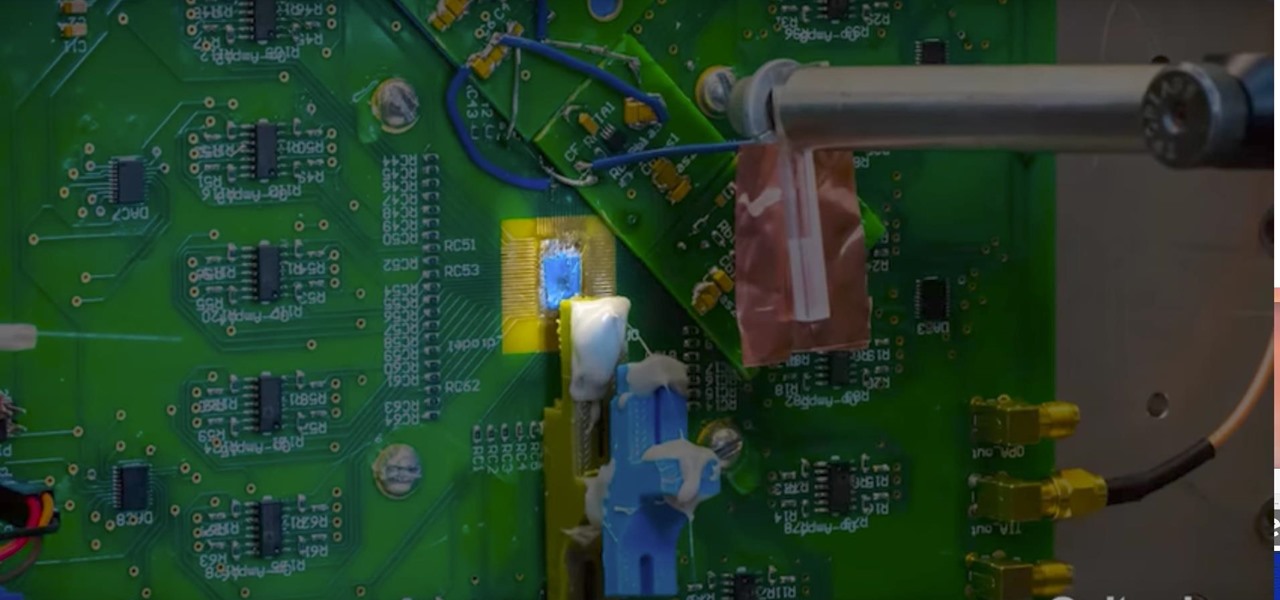
Researchers have created a possible replacement for traditional camera lenses, using an "optical phased array" to function as both a lens and sensor of a camera.

The Google Nexus 6P, manufactured by Huawei and released a little more than a year ago, has been a well-received smartphone in general. It sports front-facing stereo speakers, an awesome camera, a massive screen, supports all US carriers, and doesn't allow the infamous Qualcomm Snapdragon 810 to hamper its performance in the slightest.
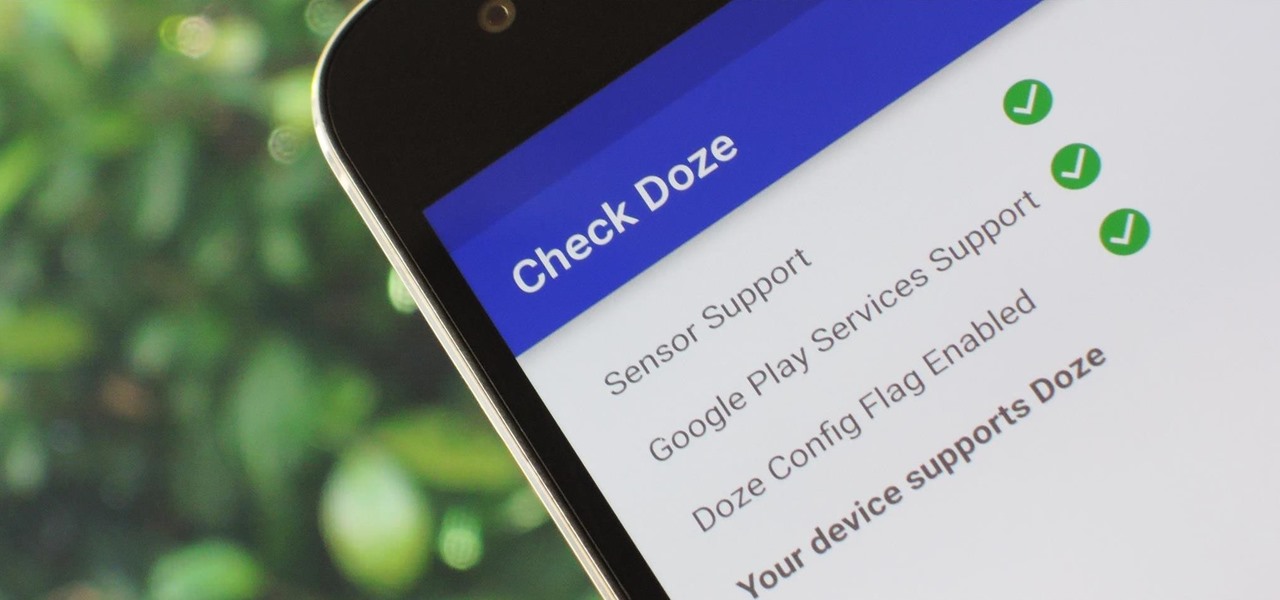
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Hello NullByte! This will be my first How To series.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

This tutorial is for everyone who is trying to learn how to windsurf. If you already know how to windsurf and just want to freshen up on the theory or if you have never tried it and want to give it a go, this is the series to check out.

2011's The Artist was the first silent film to win an Academy Award since 1927. It was old school versus new school, and it won in unprecedented fashion.

Kevin Battersby of Battersbygold explains the proper way of cleaning rubber or leather golf club grip, important for having a having more control of the club.