
How To: Gathering Sensitive Information: Basics & Fundamentals of DoXing
I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.


I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.
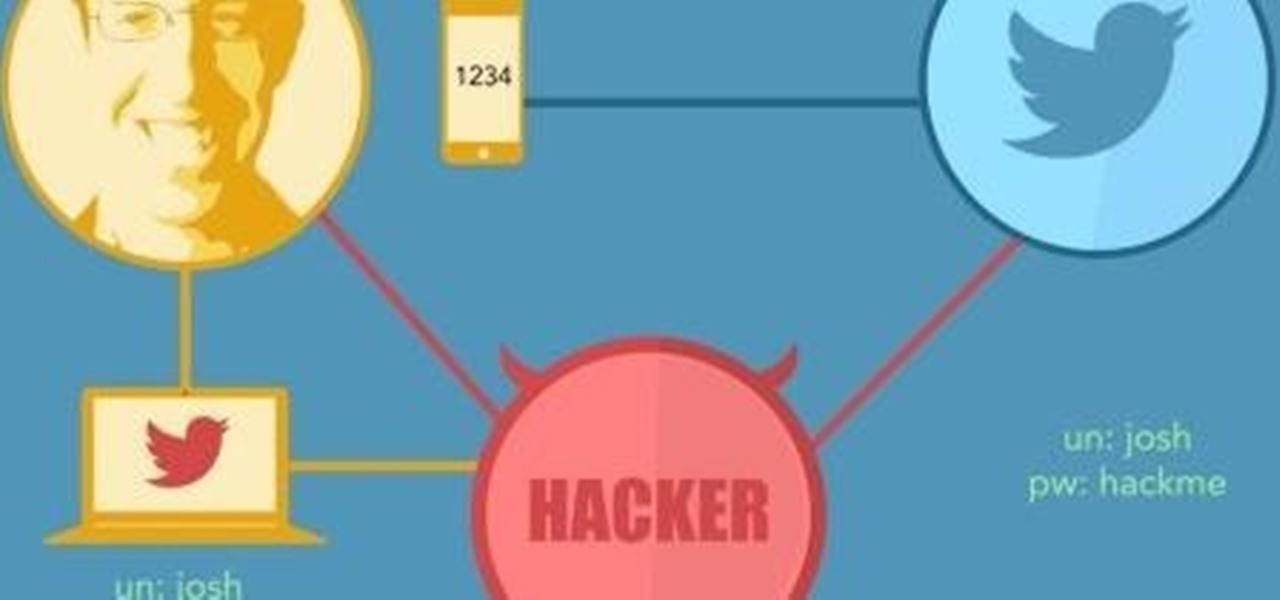
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.
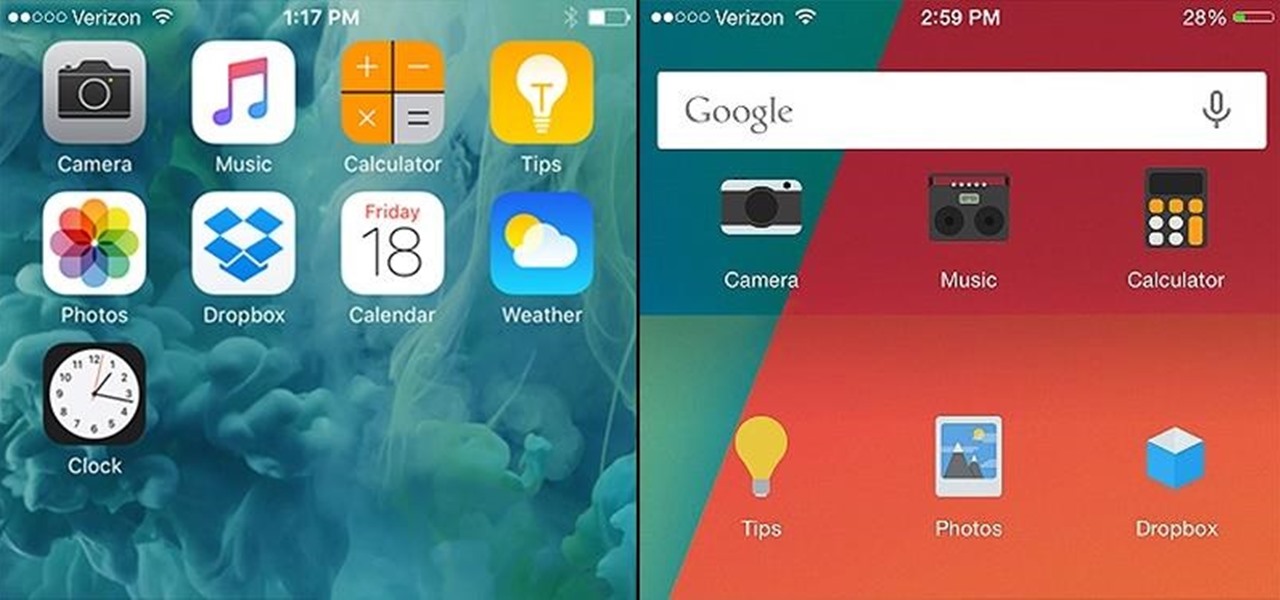
The competition between iOS and Android is fierce. Each operating system offers unique and powerful features, so it can be hard to choose which one you want. However, for iPhone users, a little tweaking and some themes can give your iPhone some of the key features and aesthetics of an Android.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.
Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.
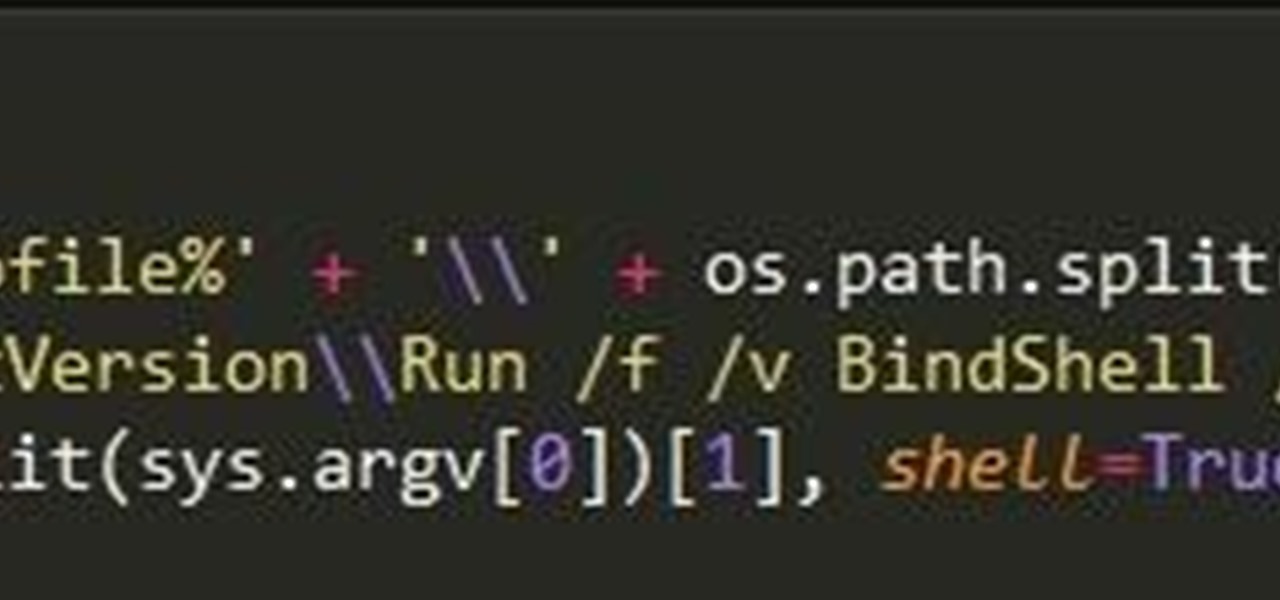
Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

When summer rolls around, I think of two things: grilling and ice-cold beverages. To me, nothing beats loading up the grill with charcoal, letting the smell of smoke get stuck to your clothing, and imbibing the most refreshing drink you can find.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

There are three huge benefits to microwave popcorn: it's quick, it's delicious, and it's cheap. But there's a way to make popcorn that's better, more delicious, and cheaper than the microwave variety. And oh yeah, quite a bit healthier.

Ice pops are like summer on a stick, with all the sweetness and stickiness of July and August. Store-bought popsicles, although refreshing, are never as good as homemade. So it's time to up your popsicle game with some of these beautiful creations, including some boozy pops (poptails) for adults.

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

For 365 days of the year, our mothers show their love for us by driving us places, cooking us food, doing our laundry, and being our number-one cheerleader. But for one day of the year, we all get up early in the morning and show our love for our favorite women. Often, that means cooking breakfast or making brunch, or running to the store to grab a pre-selected bouquet of flowers.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

It can be pretty tough to fall asleep when your brain is thinking nonstop or anxiety has gotten the best of you, and it seems to only get harder when you're lying in bed listening to yourself breathe. Yet paying attention to that breathing may be exactly what you need in order to find a calm, easy entry into a good night's rest.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Eye contact is key in conversations, job interviews, and honesty, and it can help you access others' thoughts and spot heavy drinkers. Locking eyes with someone can even help you fall in love, whether you know them or not.

Cast-iron cookware breeds a strange kind of obsession. When I got my first pan, I spent untold hours seasoning, cooking, researching the best non-soap methods to use for cleaning, and re-seasoning that thing. Finally, I became exhausted by the whole process and realized that you can skip seasoning a cast-iron pan as long as you use it regularly and clean and oil it properly in-between uses.

Google Play Music is one of the best streaming services out there. It allows users to upload as many as 20,000 of their own songs for free, then stream them all to any device without ever paying a dime. If you upgrade to their All Access subscription, you get these features in addition to an expansive on-demand library of songs (and beta-access to YouTube Music Key).

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!
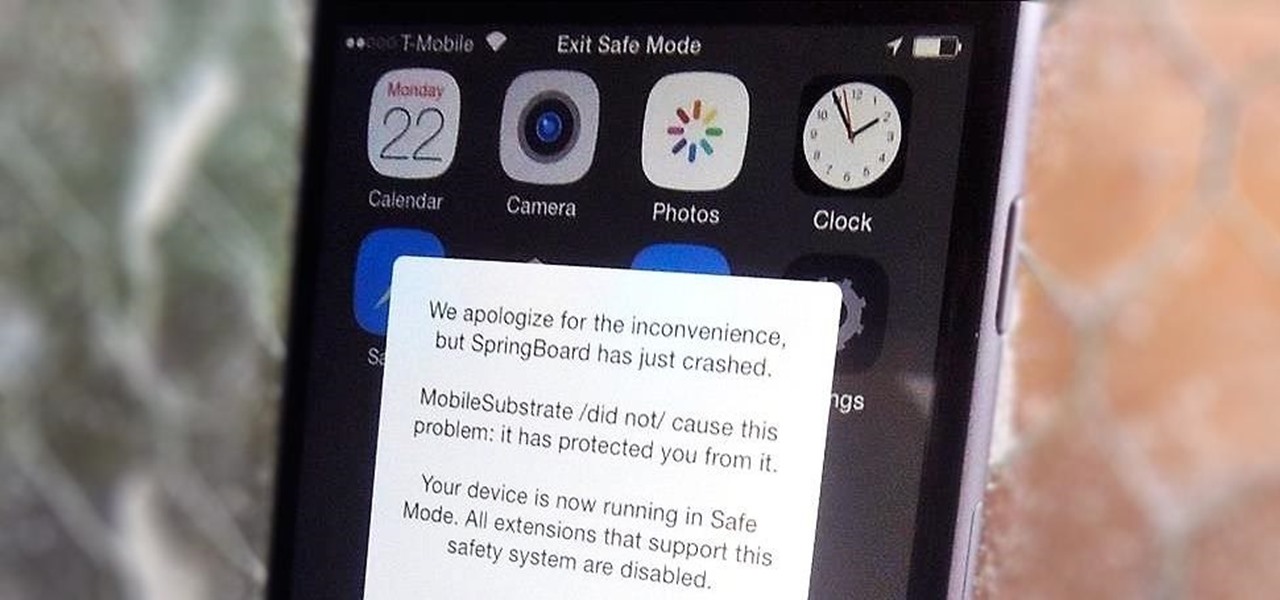
Installing tweaks or themes onto your jailbroken iOS device is a pretty fun and exciting experience, but if you do it for long enough, you're bound to come across a bug that will cause your operating system to crash.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

Cold pizza is the holy grail of leftovers. That's a statement that elicits a slew of impassioned feelings. Either you love the idea of biting into soft crust and cold, fatty cheese, or scowl at the idea of pizza that isn't hot, crisp, and melty. Yet if we were to stand by the former sentiment, how would we argue on its behalf? Food Science Explains Why Cold Pizza Rules

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

One of the best ways to reduce clutter and enjoy the new iOS 8 wallpapers on your iPhone is to use the little-known trick of hiding all of your main home screen apps. This trick effectively moves your apps off the main home screen and over to additional home screen pages, or in your dock, making your main home screen beautifully clutter-free.

Salad greens are a staple in my house and for good reason: they're cheap, nutritious, and work as a base or an accompaniment for almost all meals. However, it's all too easy to forget about them and then pull out a bag filled with sludgy dark goo or yellow, inedible leaves.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Google Now is a wonderfully powerful service—with its predictive cards and voice search, it serves as a great starting point for any searches you need done. In fact, Samsung liked it so much that they decided to build the "Okay, Google" hotword detection right into the Galaxy S5's stock launcher.