Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Malzahar's strength is being able to damage over time. With his silence ability, he is also good at harassing the other team. Here's a video which explains what Malzahar can do as a champion, and then a demonstration of him in action on the Fields of Justice.

Do you know where your blog's traffic is coming from? Everywhere. That's where. And they all want a warm welcome to your website. Every blog has multiple traffic sources. In order to welcome visitors from different traffic sources like Twitter, Facebook, Delicious, Digg, etc., with the welcome message, we can add our subscription link according to the traffic source. Also, we can use default welcome message for direct visitors with help of this plugin. See how.

There's a cool little plugin for your WordPress blog that will help you get more traffic from people searching the web on mobile devices. It's called MobilePress. Your visibility will become greater on mobile phones and other mobile devices when activating this plugin on your blog.
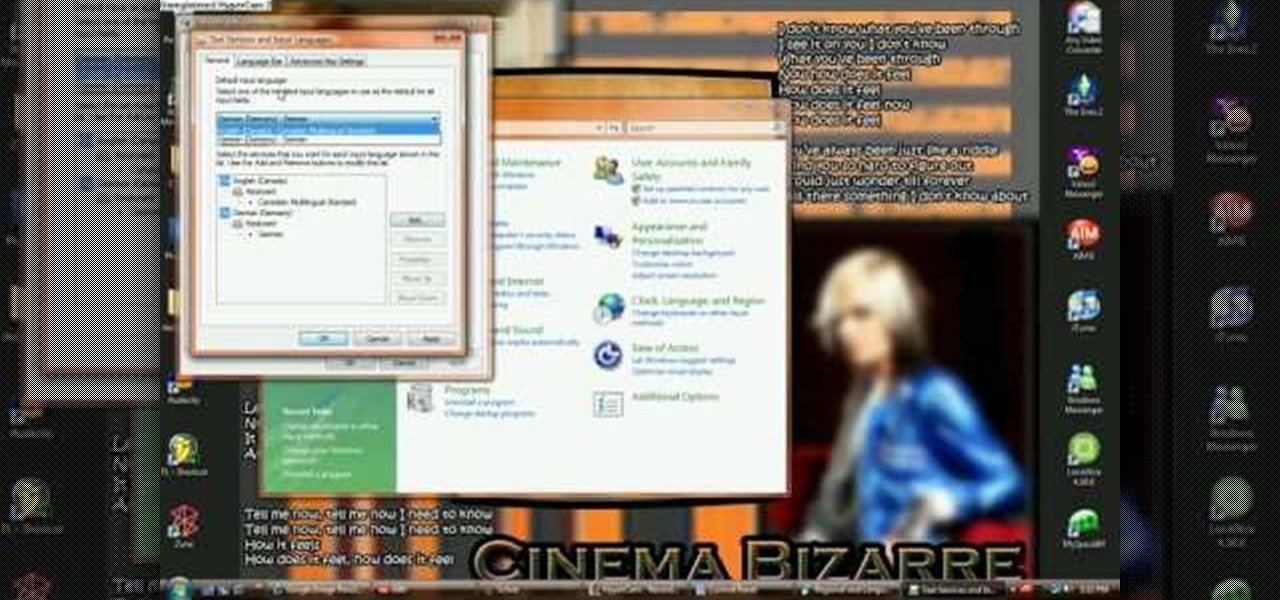
Mrs. Victoria explains us how to change the language on your Keyboard (Windows)1. Go to the control panel and select the option ‘Change keyboard or other input methods’ and a dialog box (regional and language options) pops up.2. Click on change Keyboard, and another dialog box pops up.a) In the new dialog box, click ADD Button, and select the input language you require and click OK.3. You have the feature to alter your language input whenever you want by coming to this (Change keyboard langua...

Peter Fiduccia from Field and Stream explains how to use the tending grunt sequence when hunting deer. The tending grunt is a grunt made by a buck when following a doe. The grunt is made in order to let the doe know that he wants to breed. The key to making the call is to be soft. Bucks don't make this call with aggression or loudly. The first step is to take the call and cup your hand around the end. Blow gently into the call. For more resonance in the call, grab the call with both hands at ...

With careful wording you can avoid lying and still avoid going to something that you just don’t want to attend. Even without a good excuse you can politely decline without hurting anyone’s feelings or ending up in an embarrassing situation.

This video explains how to train a Pit Bull terrier. Begin training at seven weeks, but formal obedience training should begin at 4 - 6 months. Be sure to use positive training methods that rely on praise and treats as motivators, rather than pain.

Doubling, grips, birls, and other bagpipe techniques are fully explained. Learn how to play bagpipes with free video lessons from a bagpipe teacher.

There are several types of chords including major, minor, suspended and dominant. Watch this experienced musician as he explains the basic essentials of music theory such as understanding notes and beats in this free online video series.

Free Tax Help! Learn how to prepare and complete a W-4 for singles, married couples, multiple jobs, and more in this free video on explaining the W-4 tax form.

Learn how to install a custom air intake on your car or truck, from removing hoses to installing the silicone coupling, as our expert mechanic explains in this free auto-maintenance video series.

In this video series you will learn tips and techniques that will give you an edge on the house the next time you are at the tables. It will explain in detail all the basics of the game and show you that anyone can win.

In this video series, professional guitar player and technician Bill MacPherson shows how to adjust the intonation of a guitar. With his expertise he explains what guitar intonation is, what the different factors that affect guitar intonation are, different tuning methods, different guitar bridges, and finally how to adjust and setup the intonation of the guitar string by string. Stop fighting your guitar when you play and learn how to make your guitar work for you?

In this video series you will learn rules and information on how to play backgammon or how to improve your game if you already know how to play. There are several strategies explained in detail throughout the series that will expand your view of the game and help you identify possible weaknesses in your opponents that you might otherwise miss. Use these videos, tips and techniques to either learn the basics of how to play or to improve but keep playing.

We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Just like Apple and Google, Facebook has been working to develop computer vision shortcuts designed to give mobile apps augmented reality superpowers.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

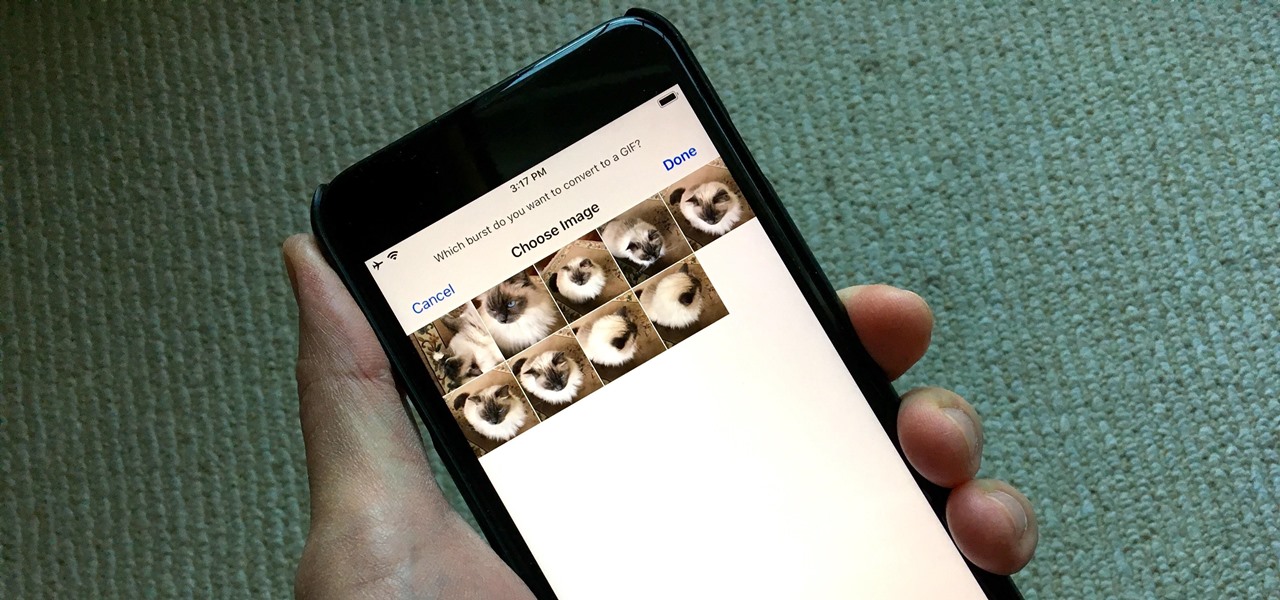
Creating GIFs of your own burst images has been possible for a while with third-party iOS apps, some of which cost money or include in-app purchases to utilize the full potential. Fortunately, with Shortcuts, Apple's automation workflow app, there's finally a native way to achieve this without spending any cash.

AMC Theatres was never a fan of MoviePass and even predicted its unsustainability. After the struggling MoviePass turned off diehard fans with too many new restrictions to combat its cash problems, AMC stepped in to save the day with its AMC Stubs A-List subscription for cheaper movie tickets.

With would-be unicorns Magic Leap and Niantic among its investments, Google is an active investor in augmented reality technology. This week, the search giant experienced both ends of the investment cycle, with an exit via Lyft's acquisition of Blue Vision Labs, and a funding round for Resolution Games.

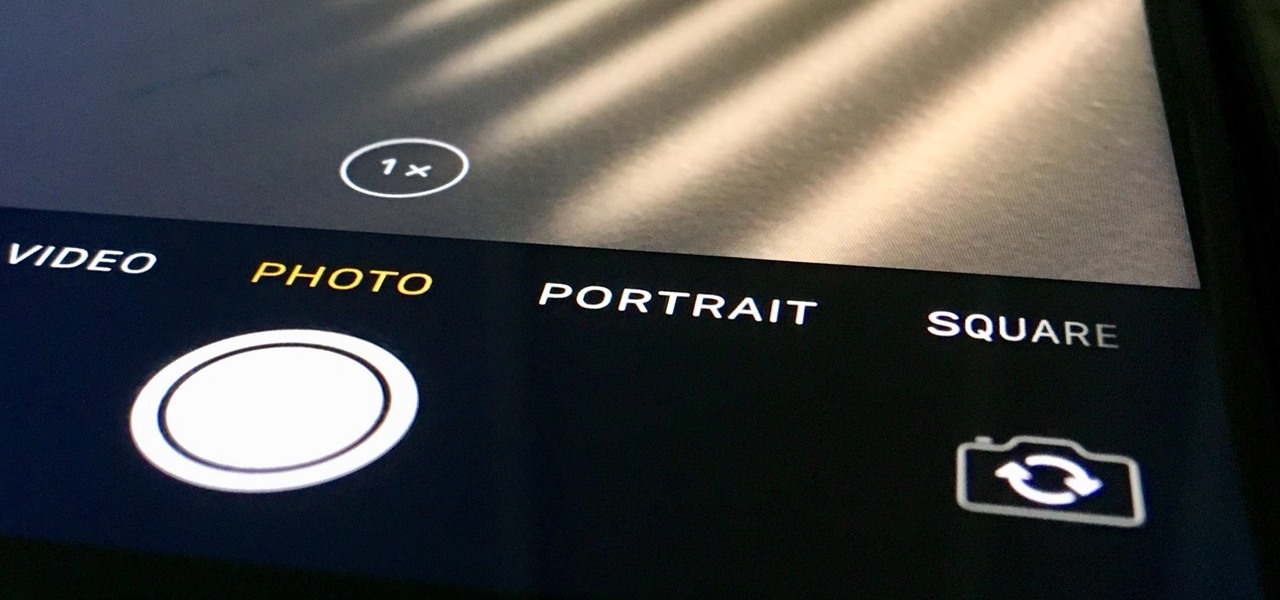
Even though your iPhone's Camera app is fast and easy to use, its default settings prevent you from immediately accessing any other shooting mode aside from "Photo" with "Live Photo" on and no filter applied. But there is a way to make the Camera app remember what you prefer the next time you open it up.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

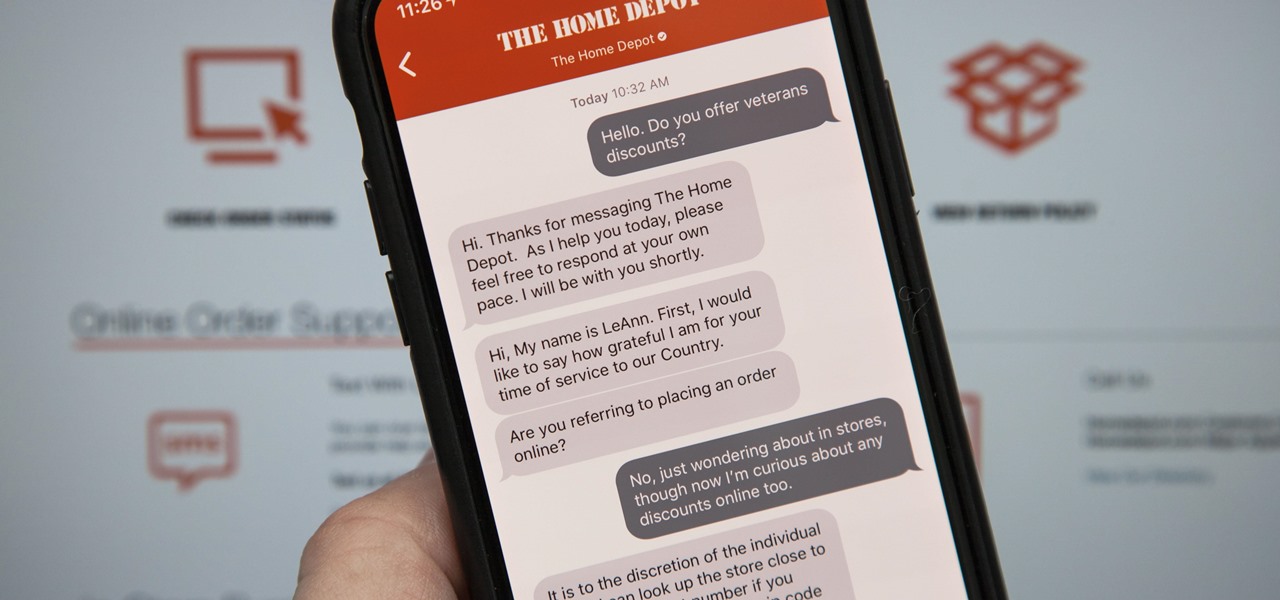
Apple first announced Business Chat, a new way for customers to communicate with companies, at WWDC 2017. While Business Chat did not arrive with the initial release of iOS 11, Apple pushed it out in iOS 11.3 so companies can offer customer service in a whole new way, and it works pretty much the same in iOS 12 and higher as it did back then.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.