Make your nose look smaller and accentuate your brow bone by applying concealer on the bridge of nose. Discover more about how to make your nose look smaller and narrower with this free video from a professional makeup artist.

Watch this how to video and discover why induction cooktops are the hottest trend in the kitchen. These Home & Garden tips will help you decide on an induction stove that is right for you kitchen.

Discover what happens when you hit a ball with your tennis racquet by instrumenting it with I-CubeX sensor technology! If you ever wanted to improve your game, this is the way to do it.

Pharmacist Sherry Torkos shares the story on how L-theanine was discovered to be a calming and relaxing supplement.

Super Smash Bros. Brawl smashed its way into the US market this weekend, and the Mahalo video games team has been all it, uncovering the unlockable characters and discovering gameplay tricks. We took a gander by the line at the midnight launch, and spoke to Mark about what makes this game so special. Game!

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

Cultivating a strong online presence can have a huge impact on your employment prospects or help you get that dream store up and running in no time. Whether you're looking for work or building a brand, being able to create and maintain a professional website is essential in the modern workforce.

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

With Zoom and Google Meet, you can zoom in using your rear camera on a video call to focus on something far away or to get a closeup view. But in Messenger, Snapchat, WhatsApp, Skype, Instagram, and most other video chat apps, zoom functionality is disabled. And it may appear to be blocked in FaceTime too, but that's not the case — the feature is just hiding in plain sight.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

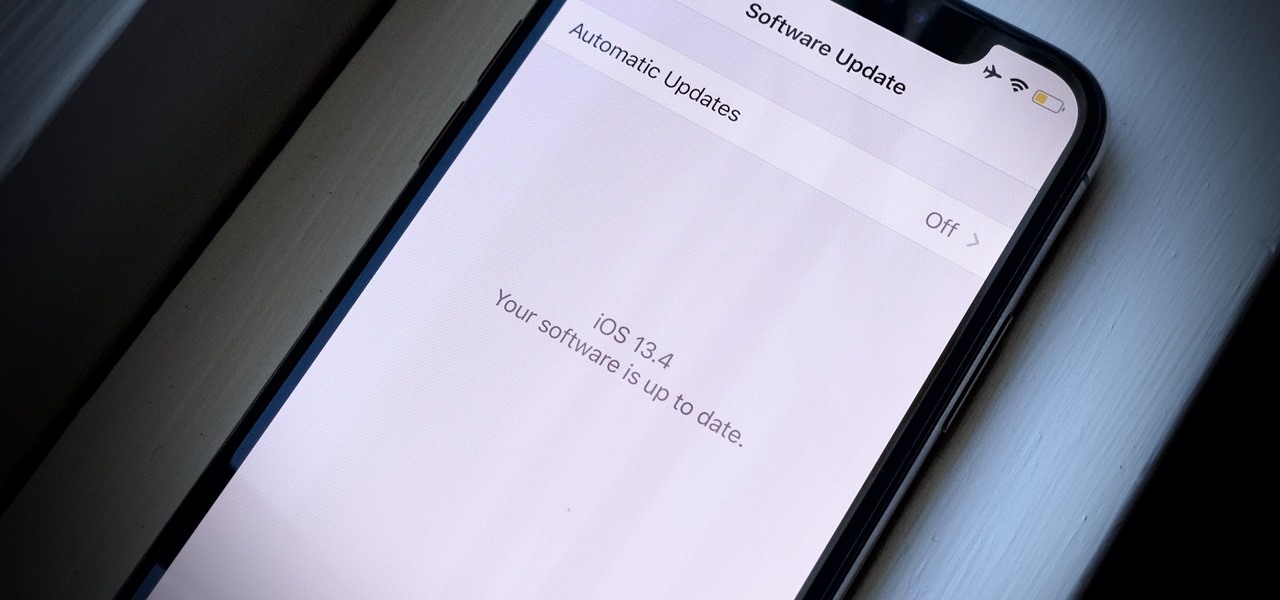
Apple hasn't released a major iOS 13 update in 15 weeks. Sure, iOS 13.3.1's release was eight weeks ago, but that minor update only included bug fixes, lacking any significant new features and changes. If you've been waiting for Apple to add some excitement to your iPhone, you're in for a treat, as Apple just released on March 24.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

The developer who gained notoriety for his What Disney Are You? augmented reality filter on Instagram is striking again while the iron is hot.

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

After recently renewed enthusiasm for the arrival of Apple's long-awaited AR wearables -- the subject of multiple reports and rumors over the past few years -- some of that excitement may now be dampened a bit.

Scanning pictures and uploading them to Google Photos is a great way to digitize your collection. With unlimited high-quality storage and text recognition capabilities, it's hard to pass up. And for your older family pictures, Google Photos will soon even colorize black and white images.

The growing stock of augmented reality apps filling up the Magic Leap store seems to be picking up pace in recent months.

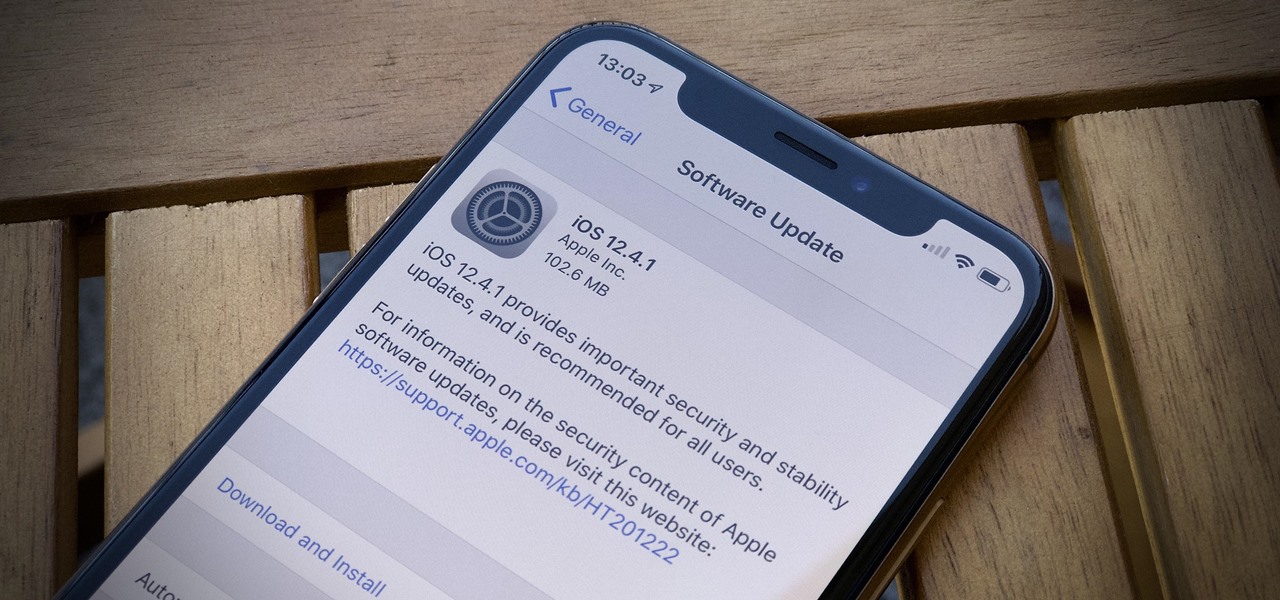
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

With Snapchat making the leap into the smartglasses realm, Facebook had to find a way to try and steal its competitor's augmented reality thunder.

Right now, Apple is testing two versions of iOS. On the one hand, you have iOS 13, buggy but feature-filled. On the other, iOS 12.4. The latter just got an update to the fifth developer and public beta versions, 13 days after the release of iOS 12.4 developer beta 4.