Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

Hello! I want to share a few thoughts about affection with you. This post is for all who wonder what is or could be the best way to communicate with the person you like. There are many ways of expressing. When Two Worlds, Mars and Venus Collide.
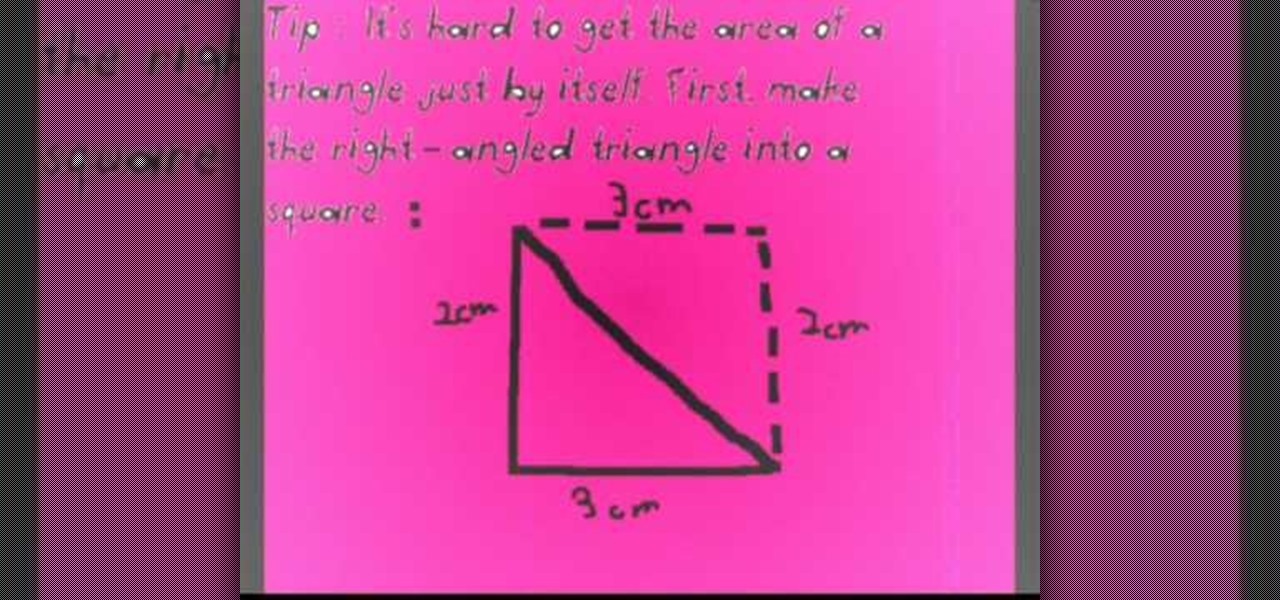
Before you can find the area of any geometrical figure, recall what you are finding when you solve for the area. The area is the surface of a 2-dimensional shape. When trying to find the area of a right triangle, the easiest way is to first double the triangle so that it resembles a square. This is particularly important if you don't know the length of the hypotenuse. Using the knowledge that the area of a square is the length multiplied by the height, calculate the area of the square you cre...

Ever thought about writing your own poems? You can learn how to in minutes by watching this adorable video. In it, you will discover how to create your own Limerick and haiku poems. A limerick is a rhyming poem that contains 5 lines and a haiku is a Japanese style poem containing 3 lines. This tutorial will teach you all about the amount of syllables you will need in each of the poems as well as several example poems for you to use for reference. Also, don't forget to take notes!

In this art video series, learn how to make wheel thrown clay pottery. Our expert will give you step-by-step instructions to make your own pottery, including basic wheel techniques like mounting the clay, shaping it and creating the opening, an explanation of the greenware and bisqueware stages, painting, and final firing of your piece in a kiln. These beginner pottery videos will help you discover the art that people have been practicing since time immemorial.

Crochet is the art of weaving with a hook. Usually crochet uses yarn, and the hook can range in size from .75 to 3.5 millimeters. In this craft video lesson, learn to crochet and discover free tips & techniques on the art of crocheting, including free patterns for doilies and dolls and instructions on how to change thread and complete a chain stitch.

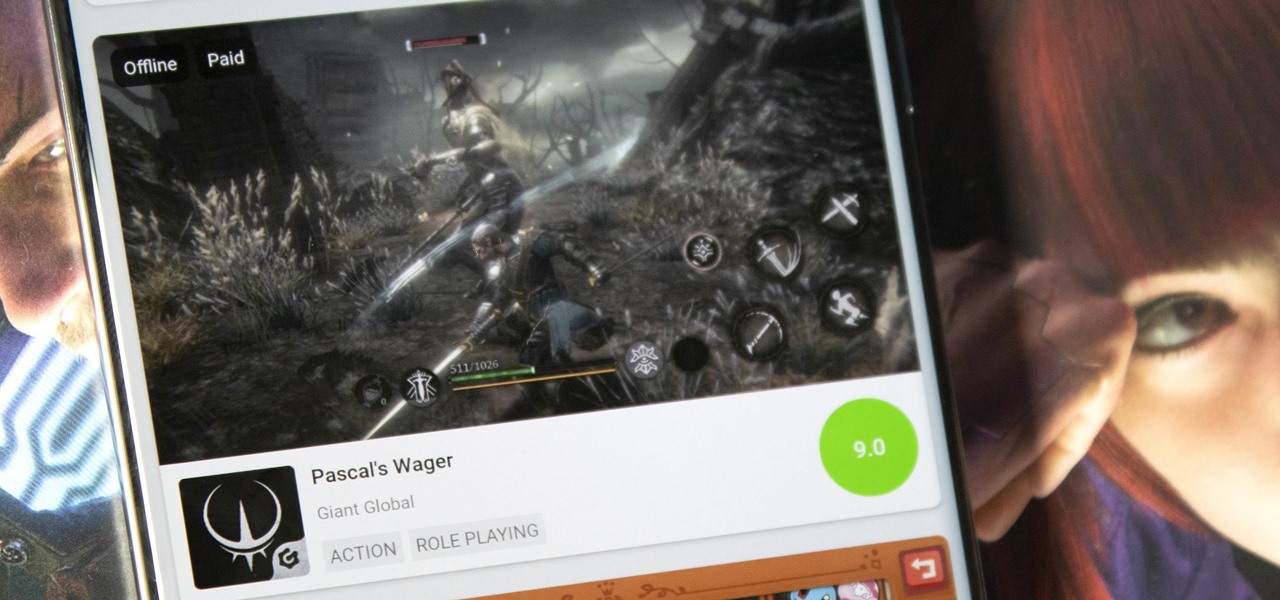
Discovering great mobile games is difficult. With over 300 thousand games on the Play Store — not including the hundreds more available by sideloading — finding the right one to invest your time and money in can be hard. The Play Store's rating system is helpful, but ratings are often skewed by external factors.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

Lock picking is a great skill that takes lots of practice and patience to master, but some locks simply can't be picked, like a Master Lock combination padlock. With a combination lock, you'll have to do it the old-fashioned way—cracking combinations.

Delve into the world of Singularity from Raven Software and Activision. This popular first-person shooter is available for play on the PlayStation 3 and Windows, but this complete walkthrough covers the entire gameplay for the Xbox 360. You'll even see some alternate endings!

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.

With the LG KU990 Viewty, you can take and view a crystal clear photo. Packed with high-quality camera features, this camera phone enables you to capture a high-definition image using a 5 MP camera lens certified by Schneider-Kreuznach and edit your photo on a large, clear, 3-inch display just like a professional photographer.

Discover upright bass scales and patterns, as well as how to move between chords. Learn about playing the upright or double bass in this free video series from a music teacher.

Looking for a fascinating new instrument to play? Discover the Native American flute with instruction from a professional musician in this free music video series.

The worst thing is when you go to bite into an apple and you find a grub or a worm. This tutorial teaches you how to get rid of pests in your apple trees. One of the main pests on apple trees is Codling moth, or the caterpillars of the moth which tunnel into the fruits as they grow. The damage caused by the burrowing is normally discovered in the summer or when the fruits are picked in autumn, but now is the time to prevent damage this summer.

In this expert video series, learn simple magic tricks to do at work. Greg Trevors will show you simple supply closet items that can mysteriously transform into magical objects. He will teach you a simple magic show routine, and various magic tricks using pens, rubber bands, paper clips, and coins. So, don't waste time at the office anymore; discover your inner magician today!

The last time the English language for Siri received new voices was in iOS 14.5, and there was one new male and one new female selection, bringing the total to four available options. In the iOS 15.4 update, there's a fifth one, and it may work better as a gender-neutral middle ground between the low-pitched male voices and high-pitched female ones.

Have you ever had a great meal at your local restaurant and wondered how to make it yourself? Or perhaps you've found yourself stumped at what to make for dinner based on the random provisions in your kitchen? Now, you can discover solutions to these food-based problems via Snapchat's computer vision wizardry.

Did you know there's a way to make animating your own cartoons that's way easier than it looks — and that you can learn all the skills you need from home? Whether you want to pick up a fun, creative hobby over the holiday season or learn the skills to start working in animation, The Ultimate Cartoon Animator 4 Pro Mac Bundle will have you quickly making your own cartoons. Right now, it's on sale for 74% off, at just $49.99 (regular price $196).

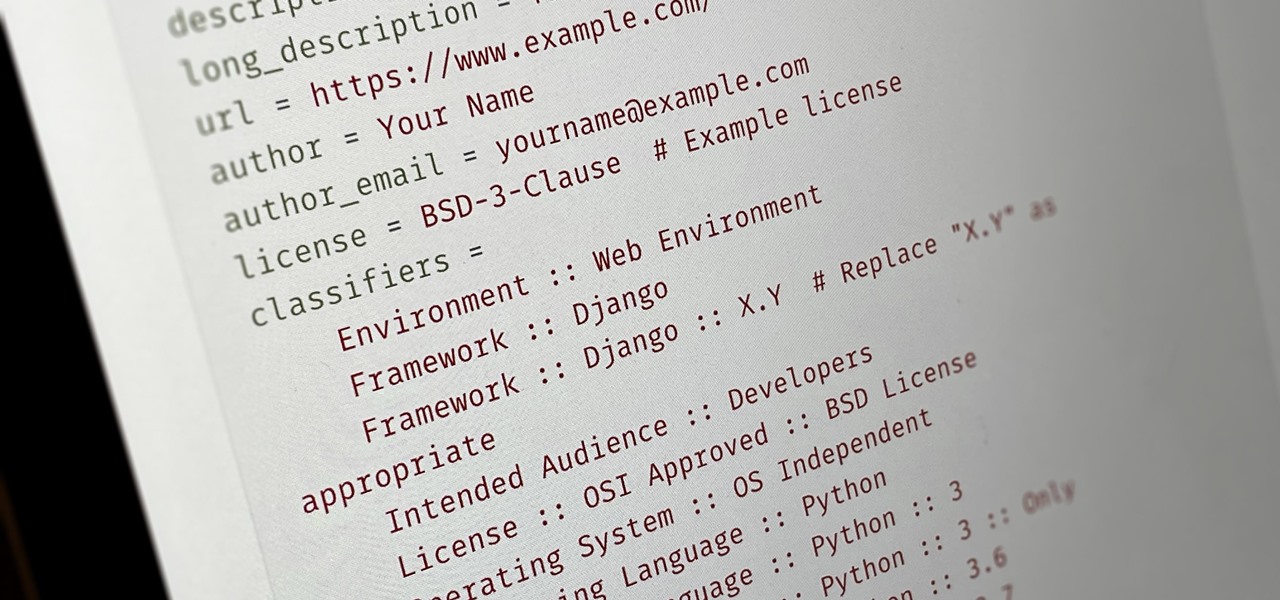
Everybody wants to build an app, but no one wants to start it from scratch. Building a full-blown application — or any other digital product for that matter — from the ground up entails some tedious work, which is why frameworks exist. Django, a Python-based framework, happens to be one of the best

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

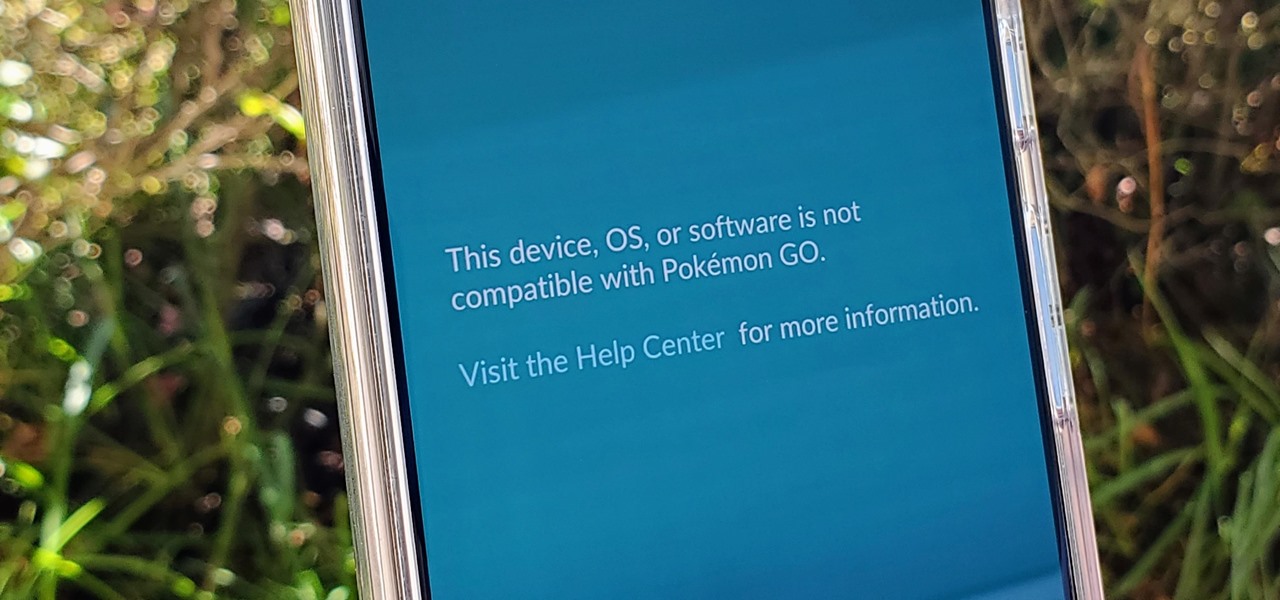
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.

In a welcomed Wednesday twist, iOS 13.4 public beta 3 follows the release of developer beta 3 by just three hours. While that isn't super uncommon for most beta cycles, it is for this one. Apple waited 24 hours between dev beta 2 and public beta 2, and five full days between dev beta 1 and public beta 1. It's nice to see these betas coming out on the same day again.

So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.