Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Five Phases of Hacking:- The five phases of Hacking are as follow:

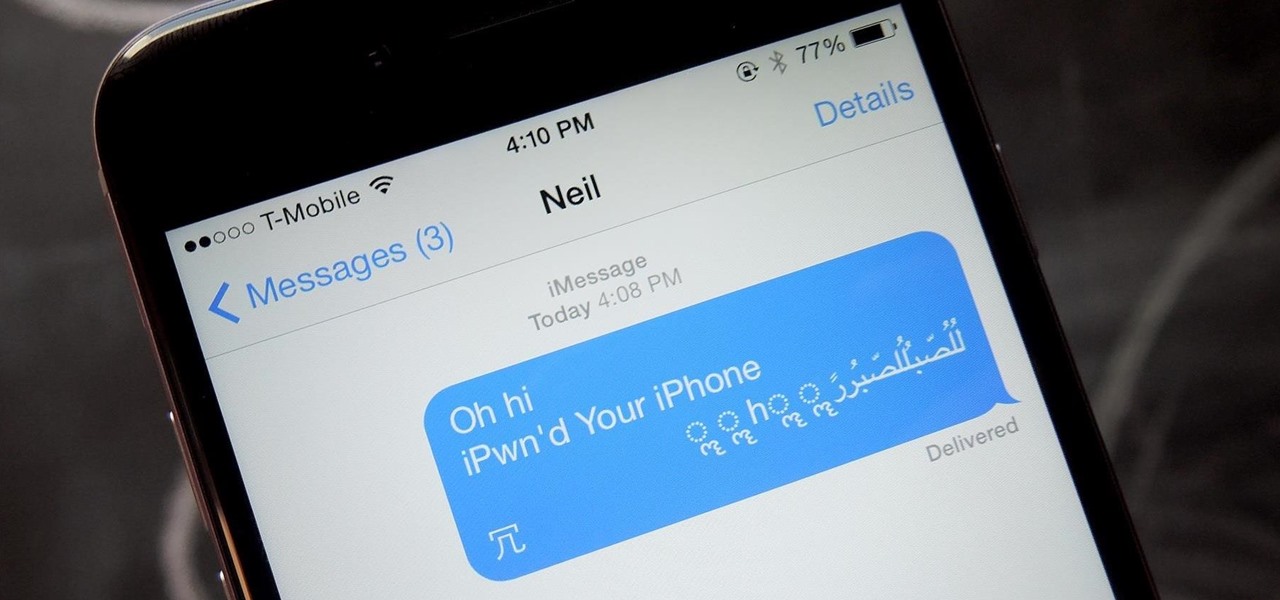
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

Worried about the MAC Defender that's been going around? Don't let your Mac get infected, watch this informative video to learn how to keep it virus free. If you are concerned with malware attacking your OS X Mac, you should watch this video.

Most people can barely be bothered to carry their wallets all the time, let alone a survival kit. When they're all dead from a massive natural disaster or terrorist attack, you'll know you were right to watch this video and prepare an every day carry (EDC) kit that ensure you will have the tools you need to survive with you at all times.

Becoming better at boffer combat is not a matter of mastering fancy sword moves, it's about being able to force an opening in your opponent's defenses and taking advantage of it without leaving yourself open for a counter-attack. This tutorial shows you precisely how to create these situations and take the most advantage of them.

Watch this 8 part series to learn all about fake UGGs and the 7 deadly signs of UGG boots. You'll be surprised at how easily people can be fooled with fake products. Make sure your UGG Australia boots are the real deal!

Whether you're interested in trying out for the lacrosse team for your school or would like to brush up on basic positions and responsibilities, this video offers a great run through of the most basic elements of lacrosse. The four lacrosse positions will be covered: Midfielders, attack men, goalies, and defensemen.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

This tutorial teaches you how to manipulate character stats in Mugen - the custom PC game engine - including how to adjust a character's health, defense, attack, and change their name.

Shaun of the Dead's Nick Frost faces an ornery alligator and learns a few useful tricks in the process.

Learn to perform a Jiu Jitsu Banana Split leg submission. This is a submission for grappling not self defense. It attacks the groin by pulling the muscles apart.

A pinch harmonic is an overtone. This video is a demonstration of how to play a pinch harmonic on the electric guitar with a right hand technique. Distortion, attack, vibrato, pick selection and more are discussed in relation to this topic.

Working with friends is always fun in Shank, but if one person doesn't really know the strategy that you need to employ to wine a boss battle, well, you can just forget it every going any better than bad. But don't worry, in this video, you and your friends can work to succeed against the Bouncer boss in Co-Op mode! You will just need to employ a simple tactic of waiting for him to use his stomp attack, and then lining up a timed trigger pull from both of you to start a double attack against ...

You know you're in pain, but are you just feeling the aftershocks of that spaghetti dinner, or is it a heart attack?

The aim of CPR is to preserve life by maintaining an adequate supply of oxygen to the heart and brain. Effective CPR prolongs a person's chance of survival until either a defibrillator arrives and can be used to shock the heart back into its normal rhythm or advanced professional life support is available. This how-to video shows you how to use a portable CPR Ezy when someone you know is suffering from a heart attack. This medical device helps you perform CPR on a victim in a constant rhythm.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

The evidence is mounting and is becoming indisputable: Gut bacteria play a role in strokes and heart attacks. The link may seem a little far-fetched, but cardiovascular disease may have less to do with what we eat and more to do with what chemicals gut bacteria make from the food we eat.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Dragon Age 2 is the latest fantasy RPG from the folks at Bioware, and if you're watching this video you've probably either just gotten it or are thinking about it. Check out the vid for a walkthrough of the prologue quest, Destruction of Lothering.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.