
How To: Play defense in volleyball
This video discusses basic techniques for diving and defensive volleyball positioning when being attacked by the left, right, and middle hitter of the opposing team.


This video discusses basic techniques for diving and defensive volleyball positioning when being attacked by the left, right, and middle hitter of the opposing team.

This week, the thread heads teach us how to make our t-shirts cooler, by cutting slits all over them. Not only are they stylish, but they make you look like Wolverine just attacked you. Awesome!

It doesn't matter what type of cuisine you're cooking - more likely than not, you're tossing the ingredients in a pan and smearing oil all over it for extra succulence (as well as to coat the pan). While a healthy dose of oil every day is vital for absorbing vitamins and nutrients, getting too much oil will land you in heart attack town.

Besides being useful, mousetraps can be pretty loud, which makes them perfect for the prankster at heart. They can scare the crap out of your intended victim, but for some, giving them the heebie-jeebies can be more difficult than just a normal trap. They might not scare as easily with a short burst of sound. But they will if you add a few mods to that everyday mouse trap!
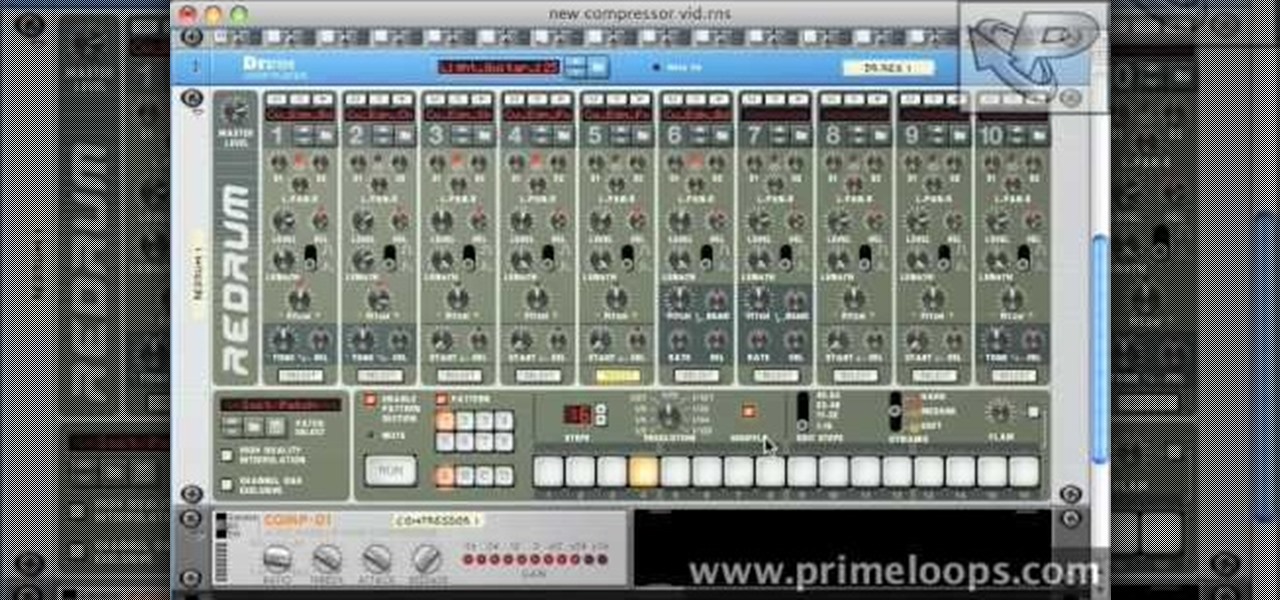
This tutorial video will show you what the purpose of compression is and how compression works through its parameters. Your instructor illustrates a drum beat and a plucked guitar line. Beginning with how to compress the drum beat, take (download) a drum sound pack without compression and to add compression using the software right click on the drum machine, choose create, and then choose combo on compressor. The virtual compressor has all the dials and adjusters found on any basic compressor...

If you can't beat Silitha in the Xbox 360 video game Darksiders, then perhaps you should check out this video on accomplishing just that. Silitha is a gigantic and ugly spider-like creature that dwarfs War. She can teleport around the arena and likes to appear directly above War and attempt to crush him beneath her. Silitha will appear around the edge of the room and taunt War. Get just about past the middle of the room towards her then use your Abyssal Chain to pull yourself directly at her ...
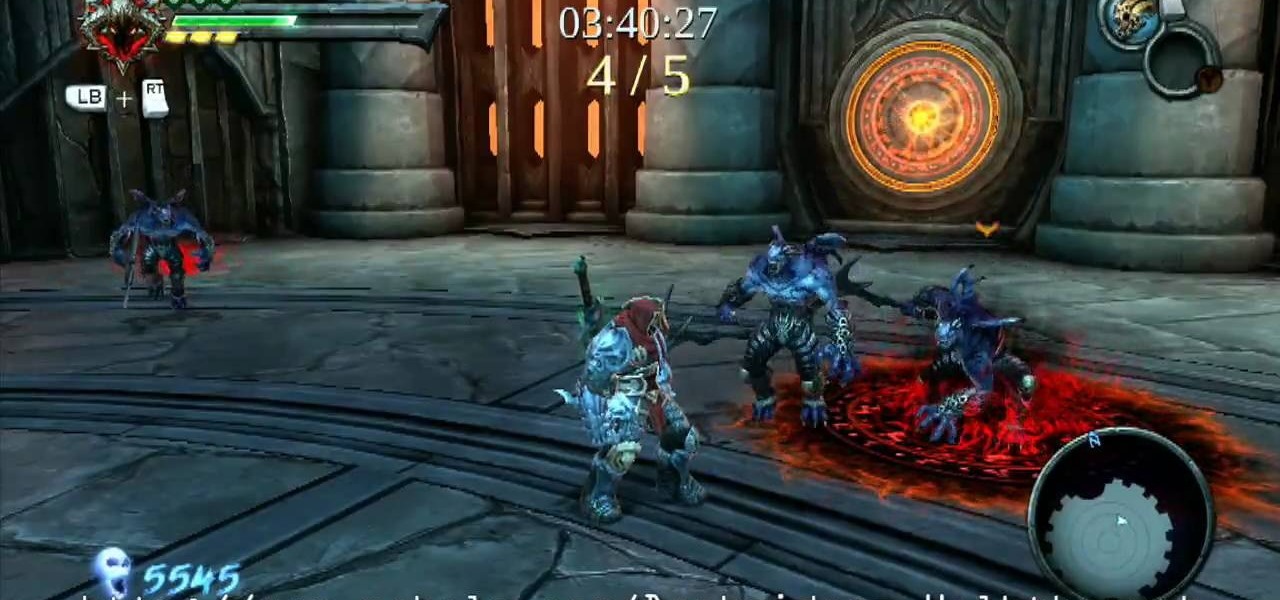
Get ready for one heck of a battle in the Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

Get ready for this Shadow Arena Challenge in the Choking Ground on the Xbox 360 game Darksiders. Meet the requirements of each portal to free the Tormented Gate so that you may proceed.

Luka will need to fend for himself in this level on the Xbox 360 game Bayonetta. In Chapter 15 - A Tower to Truth, stay close. In verse one, when you start you'll see two statues of Fearlesses (dog-like creatures). Attack these statues and they'll come alive and attack you. For more info, watch the whole gameplay.

Complete 10 verses in this level for the Xbox 360 game Bayonetta. In Chapter 12 - The Broken Sky, attack the tongue. In the verse 1 fight, there are a few minor enemies to kill. There is also a creature that looks like a wind-dragon, but you can't attack him. To end the fight, just head for the exit. Before you go through, look at the cage at the bottom of the stairs. Inside you'll find an Umbran Tear of Blood. For more info, watch the whole gameplay.

Wolves in Sheep's Clothing: So, yes, that means there are more than one wolf in sheep's clothing. Hit the map marker and this mission will immediately kick off. You need to check the nearby street in front of a large, regal building to find a certain somebody. The area is marked green on your map, so don't waste time anywhere else. Just turn on eagle vision and, once you've spotted the target, a cut scene will take over.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

Boys Will Be Boys: This is the very first problem for you to solve in the video game. You're dropped into your first mission, which requires you beat up a lot of dudes. Be sure to lock onto an enemy, which allows you to throw up your guard and block incoming attacks. You've got access to a counter move that's incredibly useful if you can get the timing down. Just hold up your guard and press the attack button as an enemy swings on you to put him down instantly. For more info, watch the whole ...

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Sulfuric acid is mixed with sugar, which is attacked by the acid. The final products are carbon, water vapor, and sulfur dioxide gas.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

In this tutorial, we will teach you how to defend yourself against an attacker with a knife. It's the best MMA for self-defense, especially for teenagers.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

When the castle has been attacked there are only ruins left. Here is the drawing video by which i go over drawing medieval ruins. Goes with other how to draw fantasy , art videos, and art tutorials. I go through my thought process in detail at :
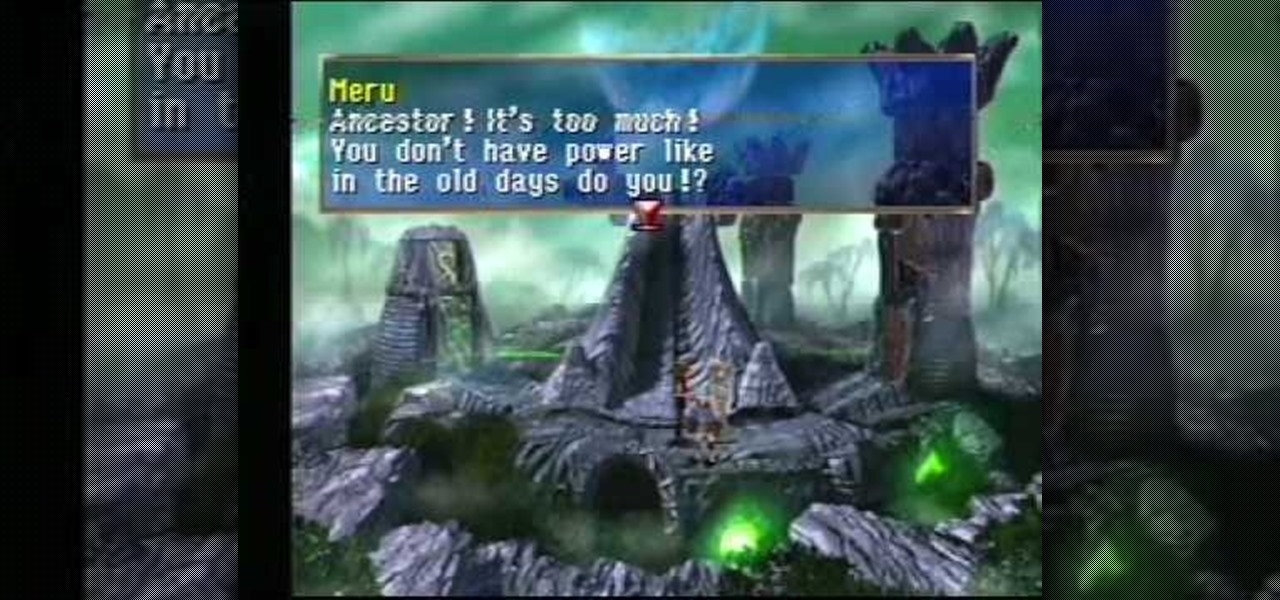
You'll find yourself in Kadessa and Deningrad in this installment of The Legend of Dragoon for PlayStation. This video walkthrough takes you from where Dart and company are exploring Kadessa, they fight and defeat the Grand Jewel for possession over the Dragon Block Staff, the party leaves Kadessa just as the Divine Dragon is launching an attack upon Deningrad, the Winglies try to teleport the party to Deningrad but they are too late to stop the attack, the party rush to the castle and make s...

Africanized honeybees, also called killer bees, can be far more aggressive than other types. Here's how to survive when they're on the rampage.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

The newest trend in couture? It's called 'trashion' - high fashion using trashy things. And we mean trashy! This tutorial shows you how to make a ball gown using trash bags, duct tape and newspapers. You'll also want a dressmaker's dummy to construct your dress around - or at least a model who's okay with standing still for a long period of time. Use the trash bags to form the dress, and then attack the newspapers over it layer by layer. You're ready for your debut!