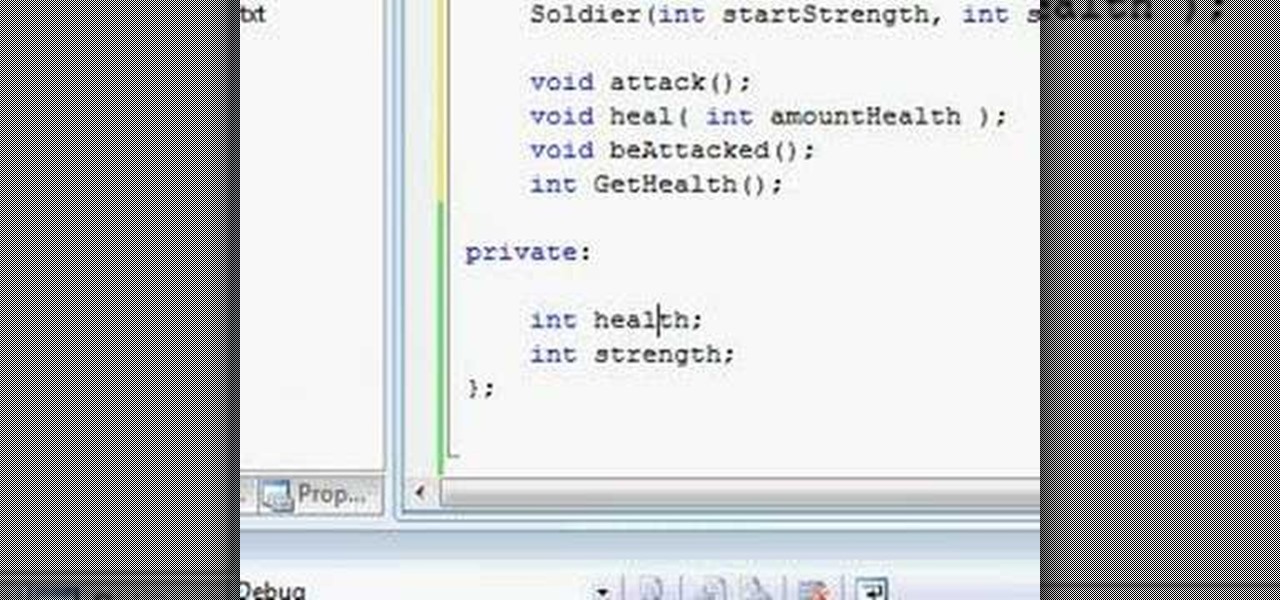
How To: Use object oriented programming encapsulation in C++
Watch this video to learn how to use OOP encapsulation in C++. Other topics included in the video include class declaration/definition.


Watch this video to learn how to use OOP encapsulation in C++. Other topics included in the video include class declaration/definition.
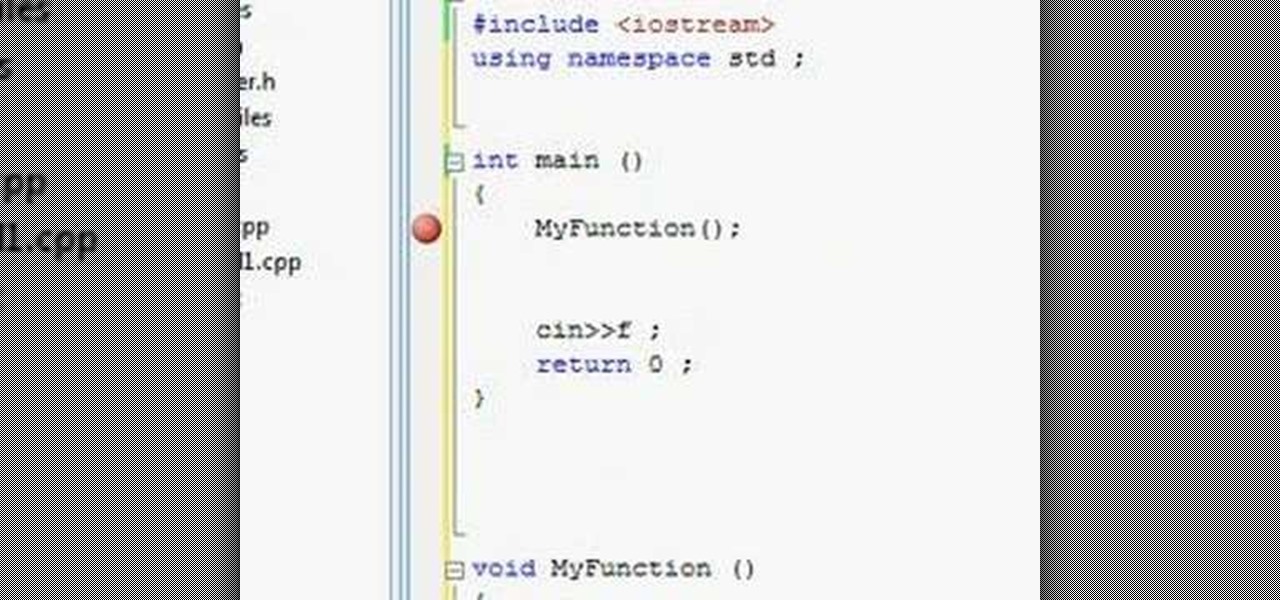
Watch this video to learn how to use function definitions in C++. The topics of declaration order and calling/returning are also covered.

What's the best way to celebrate your independence? Alcohol. There's no a soul out there that can't enjoy a few drinks during a nice celebration. So, why not go a step further with some crazy shots? Shots are the quickest and easiest way to get drunk fast. Do it for your country — but don’t overdo it. Mix up a batch of patriotic cocktails for your Independence Day party.

Welcome back my friends !! Today we'll go through the second part of this C# series

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.
We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.
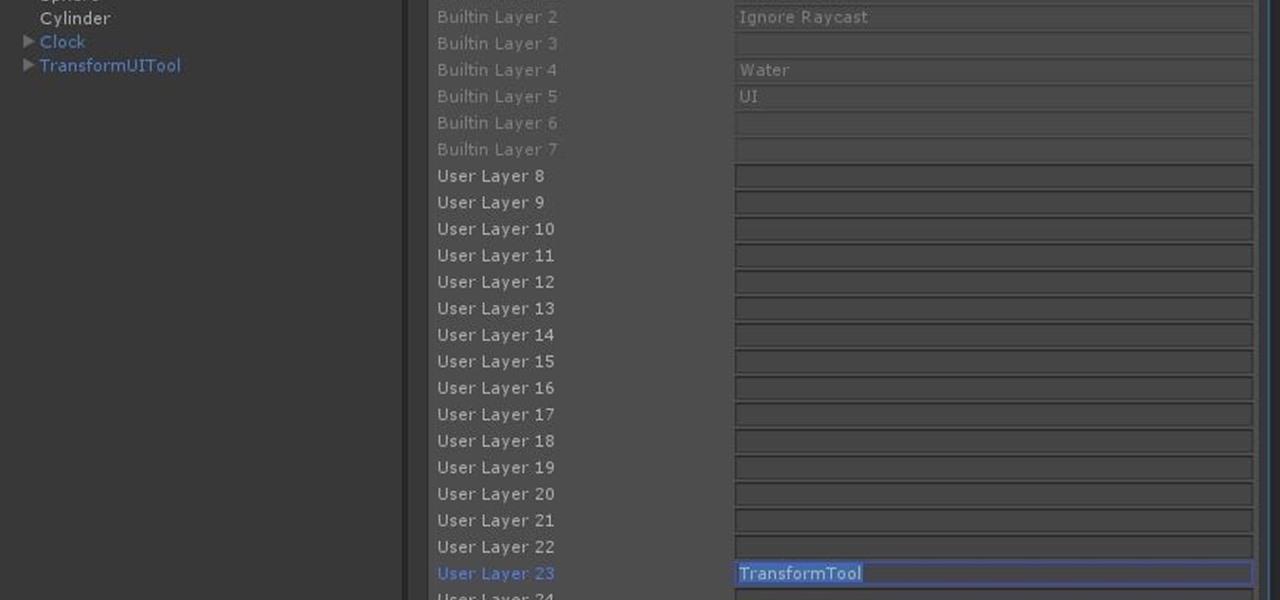
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.
Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.
Hey everyone. Only found the site a few days ago but really loving it. Been

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Basic Tips on Creating a Last Will and Testament To say that people do not like talking about composing their last will and testament documents is a reasonable assessment. But for preparing what lies ahead in the future, it is necessary to know what it contains and what it does once the owner of the will passes away.

You love the person you are with, but how do tell them "I love you" for the time? In this relationship how-to video Tracey Cox discusses the proper timing and methods for telling your partner that you love him/her for the first time. How do you know when the time is right to say "I love you" anyways? She even offers a few 'cheats' for sneaking that first declaration of "I love you" into a conversation. Say 'I love you' for the first time.

Yale University has opened up its museum archives to the public in digital form, providing free online access to high-resolution images from its cultural collections, making it the first Ivy League school to do so in this fashion. Currently, there's over 250,000 "open access" images available from their new online collective catalog, with the goal of providing scholars, artists, students and all other worldly citizens royalty-free, no-license access to images of public domain collections with...

Austrian composer Peter Ablinger has created a "speaking" piano. Ablinger digitized a child's voice reciting the Proclamation of the European Environmental Criminal Court to "play" on the piano via MIDI sequencer. Apparently, the computer is connected to the piano, which analyzes the human speech, and then converts it to key-tapping.

Politics(the Government) is built to accomplish a few things: maintaining order, providing necessities, operating businesses (stimulating the economy, trade), maintaining public relations and the most important of all, protecting the rights of the individuals it governs. It has a broad role, and as such, an array of bills, laws and rules to regulate itself and the country.

So far, I've talked a lot about what's going on in the world around us, but it's time I come back to politics for a bit. That said, the name of this world is somewhat misleading, in the sense that I talk about everything, not just politics! But I digress again.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing.

It's been five long years since Dead Island was first revealed to the public, but today the zombie game finally saw the light of day with its release on PC, PlayStation 3 and Xbox 360. When the first teaser trailer came out from developer Techland, Dead Island looked nothing more than a cheap Resident Evil ripoff—on an island.

The Tokyo Game Show (TGS) is the biggest video game expo in the most game crazy country on Earth. It is kind of a big deal. As such, their "indie" game showcase/contest Sense of Wonder Night (SOWN) is a major opportunity for developers of all shapes and sizes to showcase their work to important industry leaders and expo attendees. 2011 will be SOWN's fourth year, and it began accepting submissions yesterday.

Introduction I will not go into some time-waster of a story about how I came to build this app. It was a prerequisite in a bigger project I am still tinkering with from time to time.
Socket programming in Unix allows multiple computer programs to "talk" to each other in the form of open "pipes". This is used in many popular programs for the Linux system (see any distribution). This how-to is created to understand the simple creation of a socket and what the various parts of the call mean.