Windows Powershell is a powerful but unwieldy tool for web developers, with which the PowerGUI interface is a great means on interacting. This video will show you how to use SnippetManager, recently declared "Best Add-On" in "PowerGUI Challenge 2010", to create and manage code snippets to use in your projects.

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.

Looking for a party game for your child's next birthday party? Follow these directions to have your party participants skipping around the room, playing "Musical Pillows".

Sharpen your listening skills and coordination by playing a round of Mother May I. You Will Need

Watch this video tutorial to learn how to play war. Not only is War a great way to pass the time with a friend, but it's so easy to learn that both children and adults can play.

Get out your army pants and prepare to conquer your backyard. Learn how to play Capture the Flag with this video

Bridge is one of the most popular games in the world. The rules may seem overwhelming, but all you need are a few easy steps to learn the basics.

Doing a shot is more art than science. Here's one way to hone your barroom style. You Will Need

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Selfies' reign on social media and pop culture has not really lost any steam since it was declared the word of the year back in 2013. We've had the much-mocked selfie stick, and even an ill-fated TV show named after the term. So what's next? Well, if you're phone maker Oppo, you're banking on the next big selfie-thing being the dual selfie camera.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

The rite of passage for every tech product, formally known as Federal Communications Commission (FCC) certification, has come for the Magic Leap One: Creator Edition.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

A new survey shows that the majority of companies have an interest in using augmented reality, though adoption remains low. Meanwhile, two companies with support roles in the augmented reality industry are seeing positive financial results.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

What's up guys! It's time to discuss strings in more detail. Review

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

Those of you who have attended a Steampunk convention in the last year or two may have heard of something called "Tea Duelling" and been intrigued.

Ten days after Magic Leap declared that it had selected the winners of its Independent Creators Program, the company has officially released an almost full list of grant recipients.

A state of emergency has been declared in Malaysia's northeastern Kelantan state after an outbreak of avian influenza virus H5N1.

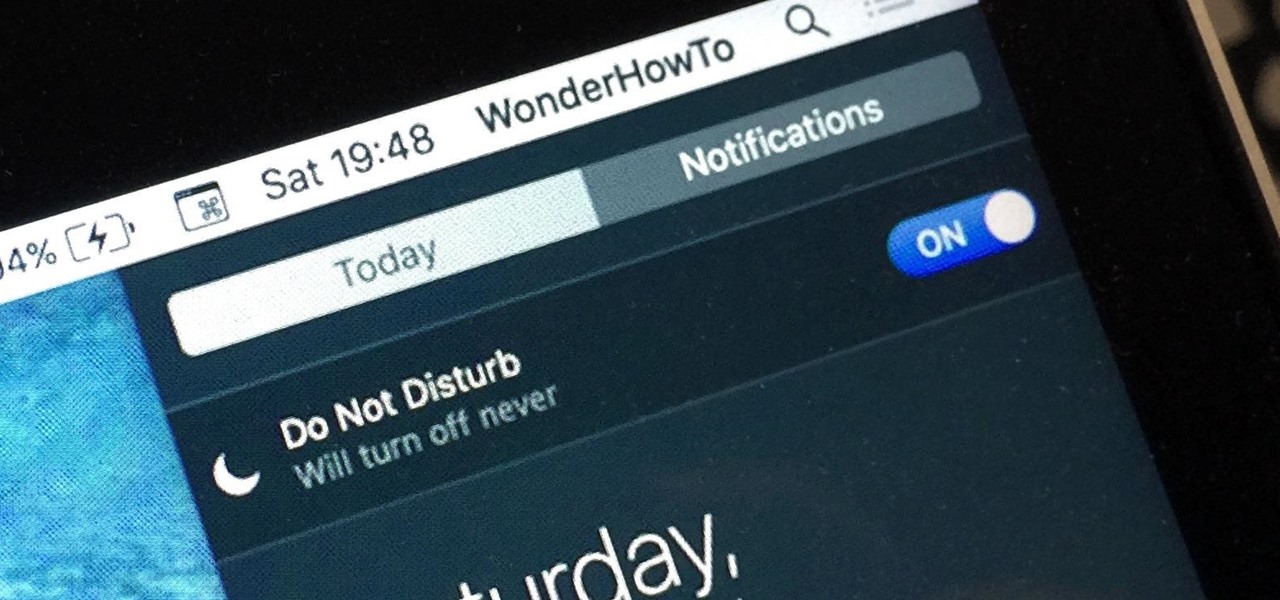
When Apple wanted to bring their Notification Center to Mac OS X, I loved the idea. But after using it since its integration in Mountain Lion, it's been more annoying and distracting than anything. More and more apps incorporate notifications, so I'm constantly getting sound alerts and banners in the top right corner that I don't want.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

Nowadays, it feels like you can't talk about eating healthy without bringing up quinoa. Quinoa (KEEN-wah) has been the "superstar" of the health movement for a while; 2013 was declared the International Year of Quinoa by the United Nations, and has only continued to grow in popularity with both health nuts and culinary experts alike through the past few years. The true testament to quinoa's success has been its eventual integration into our everyday lives. Quinoa is now very accessible to fol...

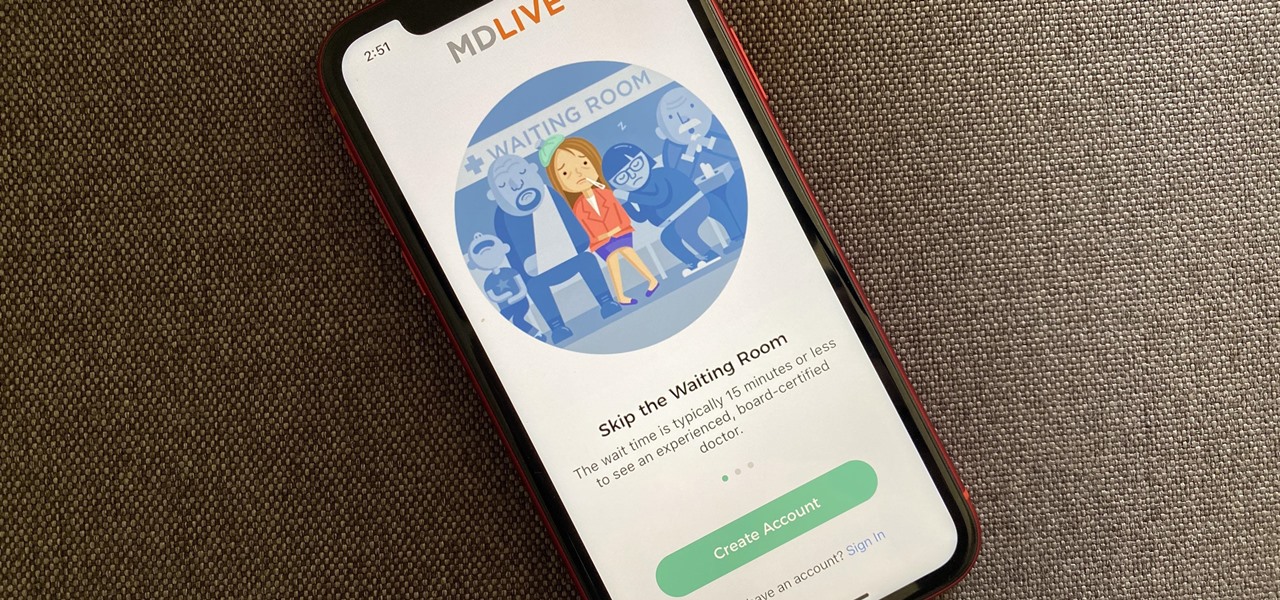
The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

There could be a fresh outbreak of the Zika virus in the Americas as the weather heats up and the mosquito population blooms.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Religion is one of the most-ignored topics when it comes to Steampunk, which is surprising given how important religion was in Victorian England. Even the hot-button issues of race and gender are confronted with a greater awareness than religion.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?