If you like homemade light shows, this is one hell of a way to do it. AP Digital light shows you how you can hack a small fan into a special mirror used to create a poor man's PIC-based laser show. It's an experimental method of balancing a fan-mounted acrylic mirror for spirograph project.

There are many different ways to connect an iPod to an in-car stereo, however, some work significantly better than others. In this tutorial, learn how to use an FM modulator to listen to your favorite tunes. This is different than an FM transmitter which is much less reliable. The modulator is the best method of connecting an MP3 player to a car stereo without an AUX input jack. Check out this clip to get started.
In this video about choosing a web hosting company. The narrator begins by saying that web pages are hosted on servers; the files that make up a web site are hosted or stored on a server. The narrator recommends a service called Host Gator. He indicated they are reliable and provide reasonably priced web hosting services. He briefly discusses the process they charge for their different levels of hosting services. Next he shows the steps to hook your domain name to the host account. He demonst...

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

Being an aircraft pilot can be frightening, but as long as you have the proper spin awareness training, you should be good. Most pilots out in the general aviation public that have never conducted spins in an approved aircraft for the purpose of developing their spin recognition and recovery techniques to become a more safe and reliable pilot.
If you've programmed a few Windows Mobile applications, you might need to perform some troubleshooting and debug the program to weed out all the problems. You can do this with AppVerifier. Marty Larson demonstrates installing, configuring and using the "AppVerifier" Application Verifier tool to debug Windows Mobile applications.

Ever wanted to build a backyard teepee? Here's your chance! In this two-part tutorial, learn how to contruct an inexpensive teepee out of a tarp. Easy to set-up, this teepee is roomy and fun to play in no matter what age you are! If in the wilderness, use this teepee for reliable shelter from cold or warm weather.

The Double Overhand Loop is a very quick and easy way to tie a loop at the end of the line. It is not a very strong knot but it is fine for attaching a sinker. For most other applications other stronger knots are better options. The double overhand loop retains around 55 percent of the line original breaking strength. A simple and yet reliable fishing knot. Watch this video knot-tying tutorial and learn how to tie a double overhand loop fishing knot.

A lot of you are enjoying a nice winter snowfall right now. Some of you aren't enjoying the snow at all, especially if your car's stuck in it or you have to grab the snow shovel, yet again. But perhaps you'll change your distaste for snow when you try out some tasty homemade snow cream!

Watch this video to learn how to cap off a water pipe with a push fit fitting within seconds. Useful for when you absolutely have to cut a pipe.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

If you want to know the best way to get an accurate pH measurement, this shows the lab equipment needed and the processes used. When doing chemical reactions, sometimes the acidity or the basicity is important. This is usually defined as pH and measuring it can be very useful for getting the reaction right. There are a few ways to measure pH, and the simplest, cheapest, most reliable method is paper. But that's not all. See a whole lot of ways in this two-part video.

This is a two-part video tutorial on cold smoking country style pork sausage. IN part one, the recipe for this sausage is provided. Most of this video's concentration lies on ways the residential sausage maker can reduce his or her hazard exposure. From the video maker: "It is not meant to be taken as more than an introduction to the concepts of where some pathogens may come from and how they might be limited." Part two investigates these hazards, but is deemed: "not a substitution for a HACC...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Any parent with a rambunctious child who may have at one point racked up a hefty bill on their Kindle or Android device can now breathe a sigh of relief. One, Jack Black has had it happen to him too, and two, Amazon will be refunding up to $70 million of in-app purchases made by children after downloading apps from the Amazon AppStore.

Apple announced their new iPhones today, and the 7 Plus features two camera lenses on its backside. That could push smartphone photography ahead in a major way. It may also serve as the basis for their foray into virtual, augmented, and mixed reality.

Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

YouTube is home to some of the most vile commenters on the internet—completely void of literacy, accuracy of facts, respect, and goodness in general. Known to many as the cesspool of the internet, the YouTube comment board can be a tough place for a person who's not accustomed to hostility on the web. "Tracking my cookies? They will never get my recipe!"

Check out this mission on The Saboteur for the Xbox 360. The third mission in Act 2: A Whisper or a Roar is where Santos is looking for help again. When you get to the convoy, Sean points out that there are two very different ways to complete this mission. You can get a disguise, sneak up close to the convoy, and plant some dynamite, which would be the conventional route.

The video presents "How to start your own Clothing Line Business". The steps include getting the financing, designing the prototype outfit/s, producing the line of clothing, promotion and sales. A good way of financing for a small business such as this is to sell your idea to family, friends and even colleagues. Research and prepare the business plan for your clothing line and be passionate about it in your presentation to convince them to fund your business. The next step is to get the produ...

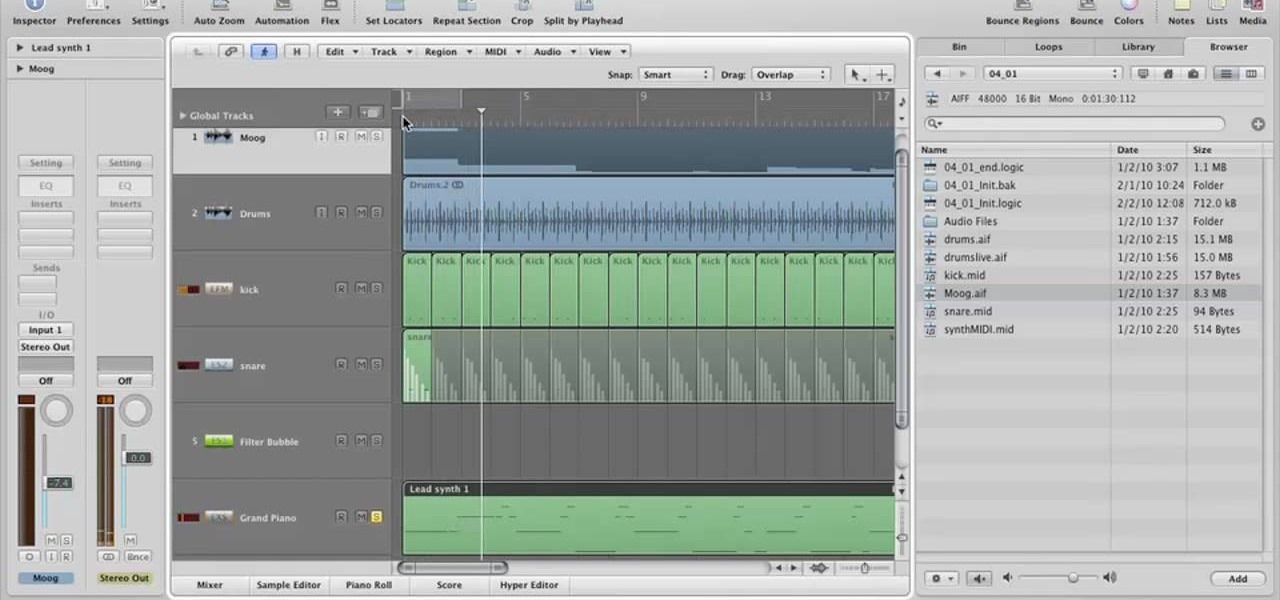
This Lynda tutorial teaches how to use the Logic pro, a songwriting application. Midi sequencing and quantizing is the main focus of this video. Midi is a short name for Musical instrumental digital interface. Midi is not sound. It is a low resolution computer protocol, developed in early 80’s to enable computer to communicate each other. Midi is fast, simple and reliable. It has a intensity stream. In this project, Scot Hirsch explained how a midi file is manipulated in Logic pro. Midi file ...

First thing you should do is invest in a reliable good quality digital camera. No, you do not have to spend big bucks on one. Kodak, Sony and Nikon make inexpensive digital cameras that are ready to be bought everyday. Make sure you find a camera that fits your needs.

The witch is the blue-chip stock of Halloween costumes — reliable return, low risk. You Will Need

This how-to video quickly outlines exercises to get your dog walking on a loose leash by your side. Put very basically, teach the dog what you want them to do! And secondly, stop reinforcing them when they pull! A clicker training method is used, but if you do not have one, you can always use a verbal marker like yes. However you will get much faster and reliable results by using the clicker. If you hold the clicker in the same hand as the leash, and keep the treats in the other hand, you wil...

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

Tired of walking everywhere? Does your only ride have two wheels and a bell? Check out this video and learn tips and tricks for convincing your parental units to buy you a car. Pretty soon you will be cruising through town and the envy of all your friends.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

Rumors are what Apple dreams are made, so most of the time it's best to ignore the juicy ones -- but some Apple rumors demand a least a little attention.

The iPhone 11, 11 Pro, and 11 Pro Max are the most advanced flagships Apple has to offer, but that doesn't mean they're immune to occasional bugs. Anything from an app plagued with issues to a faulty software update still can cause your device to freeze up, so having the ability to force a restart can come in very handy.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

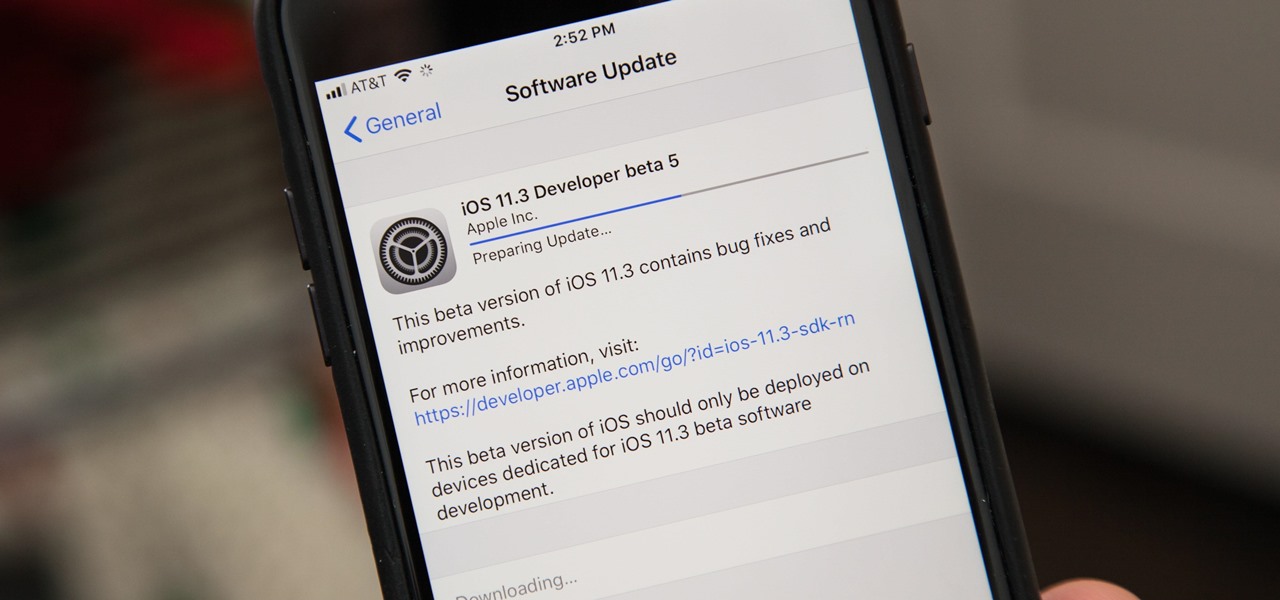
Apple released the fifth build of the iOS 11.3 developer and public beta on Monday, March 12. The update comes exactly one week after the March 5 release of beta 4, which mostly introduced bug and stability patches. At this time, this new beta appears to do much of the same.

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.