In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

We've all been there—you're away from home, your phone's battery is quickly nearing zero, and you forgot to bring your charger. "Hey, does anybody have an iPhone charger?" you ask. Crickets. If you could understand cricket-speak, you'd know that they too were saying "Sorry, bud. We're all on Android."

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

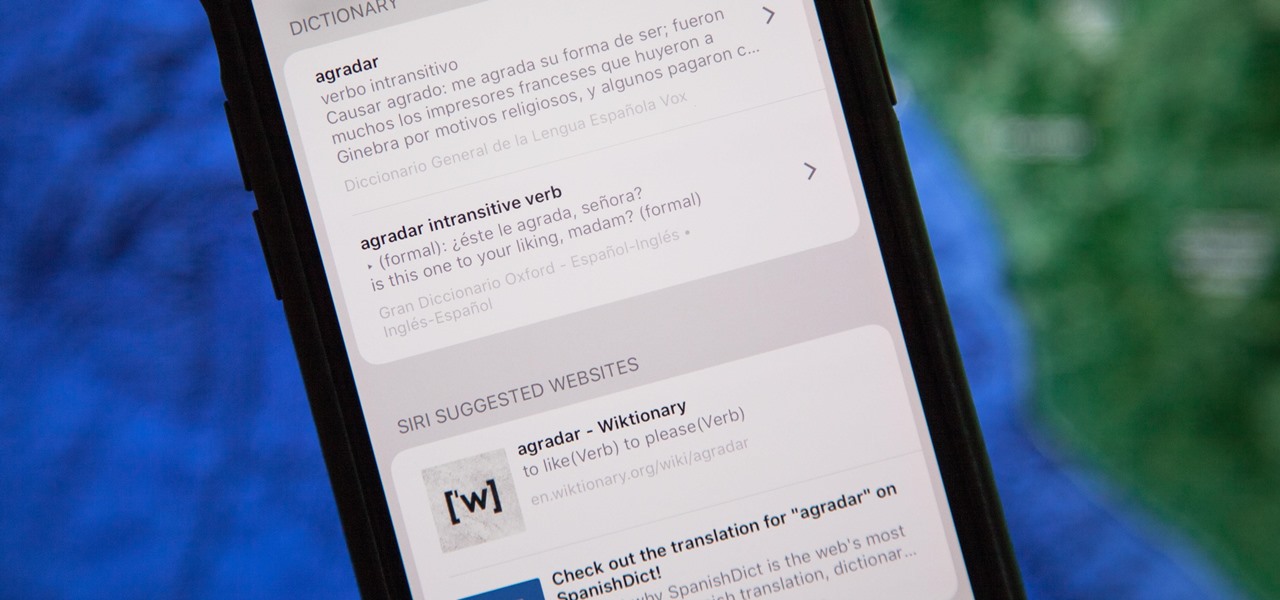
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

I think it was 1986 when I first discovered my love for making computers say stupid things out loud. My older brother got a Commodore 64 for his birthday, which came bundled with software that would speak out any term you typed in—and boy, that computer sure made a fool of itself after my five-year-old imagination got a hold of the keyboard.

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the interface of their device, a new hidden menu might be the most exciting addition of them all.

One of the most exciting things about a major iOS update is the discovery of new glitches, or even just finding ways to replicated the old ones that we've come to love so much. One of these is the glitch that lets you nest folders within folders on the home screen, which can save some major screen real estate. While this glitch was available in both iOS 7 and iOS 8, the process is slightly different in iOS 9, but you still have a couple options to choose from.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

Many of us were required to take a foreign language in school, but sadly, many of us are far from fluent in said language. To be a better citizen of the world, learning popular and rare languages would be dope, but in reality, that's probably never going to happen. If you ever do find yourself in a situation where you're messaging people who don't speak your language, there's an app that can help you.

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

For those of you who have been taking full advantage of the jailbreak for iOS 8 that's available, you can understand and appreciate what this really offers iPhone users—sovereignty.

Believe it or not, you can put your money to use very efficiently in a new way: your credit or debit card can serve as a blade in desperate situations. (It might even be handier than dental floss as a brilliant substitution for specialized kitchen tools.) While I wouldn't take bets on it slicing a New York strip steak, there are definitely many other foods it will easily slice through. What Is It Made Of?

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

With Nexus devices already enjoying Android 5.0 Lollipop, most other manufacturers are scrambling to get their flagships updated to Google's latest operating system. While HTC has promised Lollipop by the end of 2015, OEMs such as Motorola and Sony have already issued updates to their latest models. Then there's Samsung.

With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker.

When exercising at a high intensity, you know to expect some level of pain. That can make it difficult to identify when your body gives you a warning sign of injury. If you pay close attention, however, you can tell the good hurt from the bad. I talked to Dr. Brian Parr again, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained which symptoms of exercise are normal and which are bad:

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

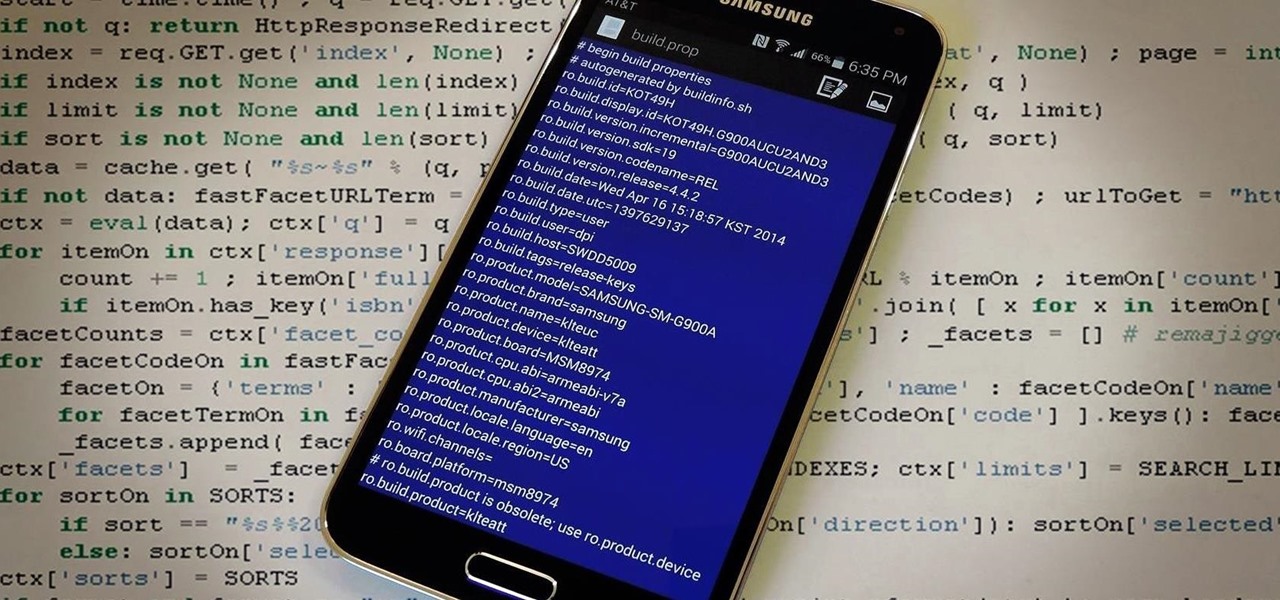
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.

Trying to explain something difficult over the phone can be pretty frustrating if the other person doesn't understand you. Using text messages can be useless for auditory learners, and a phone call won't do much good for a reading or visual learner.