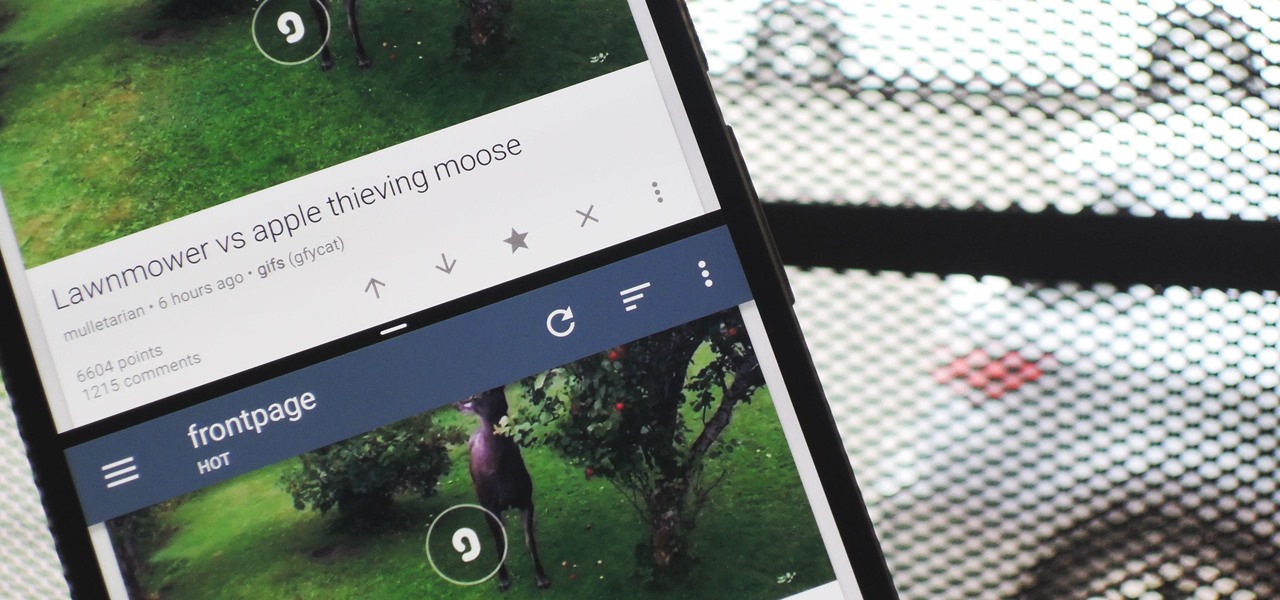
If you were a particularly good little girl or boy this year, Santa might have finally brought you that cool new smartphone you've been wanting. Or perhaps you just took advantage of a great sale and treated yourself to a new gadget this holiday season—totally justifiable, and surely a well-deserved gift.

If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster and some paint.
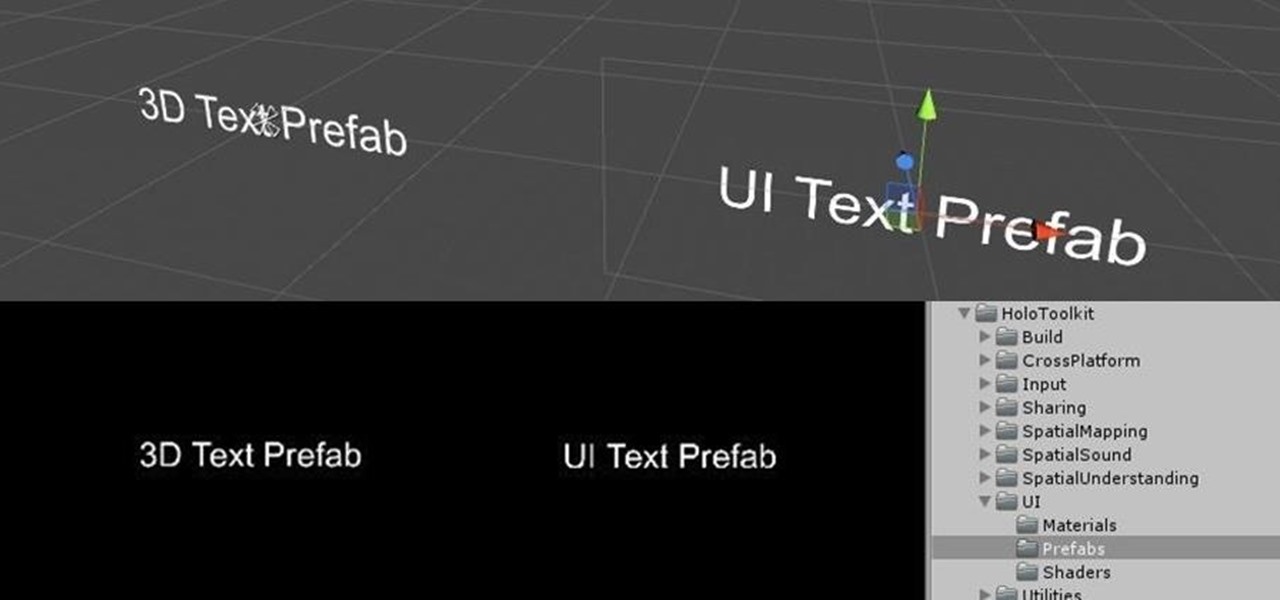
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Well, we have some potentially good news for those wanting to experience Magic Leap. The ultra-secretive company seems to be planning a big year in 2017.

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

I truly don't understand why anyone would pay $10.99 for a case of carbonated water just to feel like a Midwest mom on a diet. Every time I talk about LaCroix, pronounced La-CROY (rhymes with enjoy), it's like I take all the money I spent on my French major and light it on fire.

Some manufacturers, like Samsung and LG, have had split-screen multitasking on their custom versions of Android for years. But starting with Android Nougat, Google added this functionality to AOSP, which means that all phones and tablets running Android 7.0 or higher will now have a new multi-window mode.

Ah, butter—the (literally) heart-stopping star of the dairy world. Everything tastes better with it, from pie crusts and cookies to veggies and steaks. Hell, you can even fry things in butter if you want the best-tasting fried foods of your (short) life.

The future for the Meta 2 augmented reality headset will have to wait. While shipments were supposedly on their way out back in June, Meta revealed today that they need a bit more time to provide the best possible experience—and that's really for the best.

If you've seen, heard, or even tried the latest virtual reality headsets, you've probably heard about something called "room scale." It's why the HTC Vive suddenly usurped the reign of the Oculus Rift while no one was looking, and it's exactly where Oculus hopes to catch up. Here's what it is and why it matters.

There seems to be a nearly cult-like craze surrounding those glasses filled with summery, pink-hued rosé wine. From picnics in the park to long days spent on the beach, rosé wine offers light, warm-weather refreshment to its lucky imbiber.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

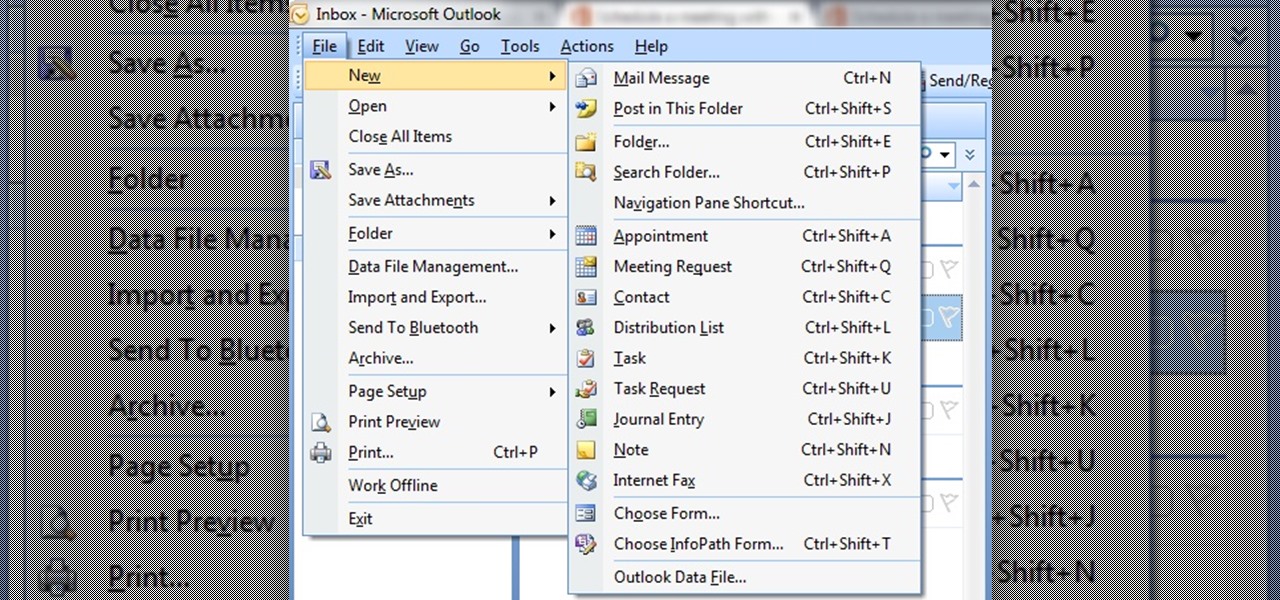
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

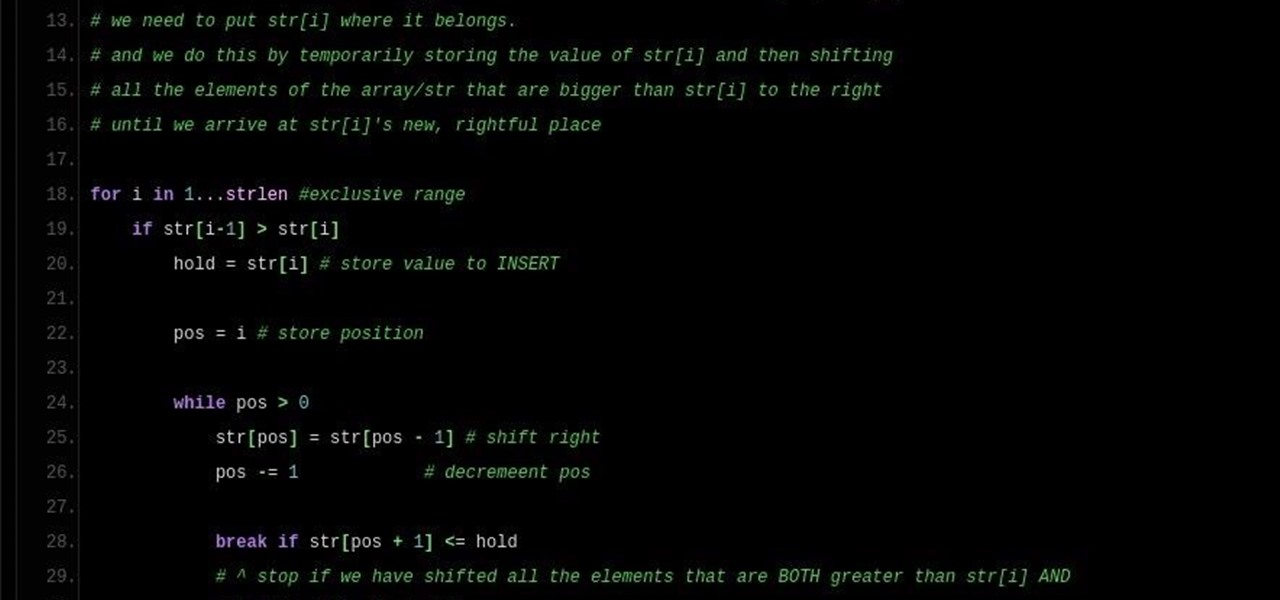
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

A classic French omelet is supposed to be completely cooked through with no brown edges. This is a delicate balance to strike, though. I always find that the moment I flip an omelet, it completely falls apart—unless it's so well-done it's rubbery, of course.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Lemons, limes, and even oranges compliment a wide variety of both food and drink: gin and tonic, poached salmon, shrimp cocktails, fajitas, and so on. And you can easily step up your hosting game by making citrus garnishes: a presentation that is both elegant and interesting.