Google's been using their "Material Design" look in Android for years now, but a change is coming up with "Material Design 2," their updated version focusing on new colors, icons, and spacing. Whether it'll be called "Material Design 2" or not remains to be seen, but you can try it out right now in Google Chrome on your Android device right now.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

One odd change found in the Android Pie update is that the "Battery" menu no longer lets you see apps that are draining your battery, nor gives access to usage details. However, one quick menu tweak will bring the Battery menu back in line with Android Oreo's, only there's a hidden setting you have to unlock first.

Google just released Android 9.0 Pie, but the Android community is already working its magic. Developer Quinny899 quickly ported the updated Pixel Launcher from the new build, so you can try it out on other phones right now.

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

We've had a lot of fun digging into the Oreo update for the Galaxy S8. Thus far, we compiled a full list of the biggest changes and ran down some of our favorites. One of the most user-facing components on a smartphone is the camera. Samsung made sure to add some nice tweaks to the camera UI in Oreo too, bringing it more in-line with the camera on the Galaxy Note 8.

One of the best new features in Android Oreo is the new Adaptive Icons system. Starting now, developers can create a single icon for their apps, then your launcher can stylize those icons in a broad range of shapes to match your system theme. Most home screen apps haven't added support for this feature yet, but Nova Launcher just threw its hat into the ring.

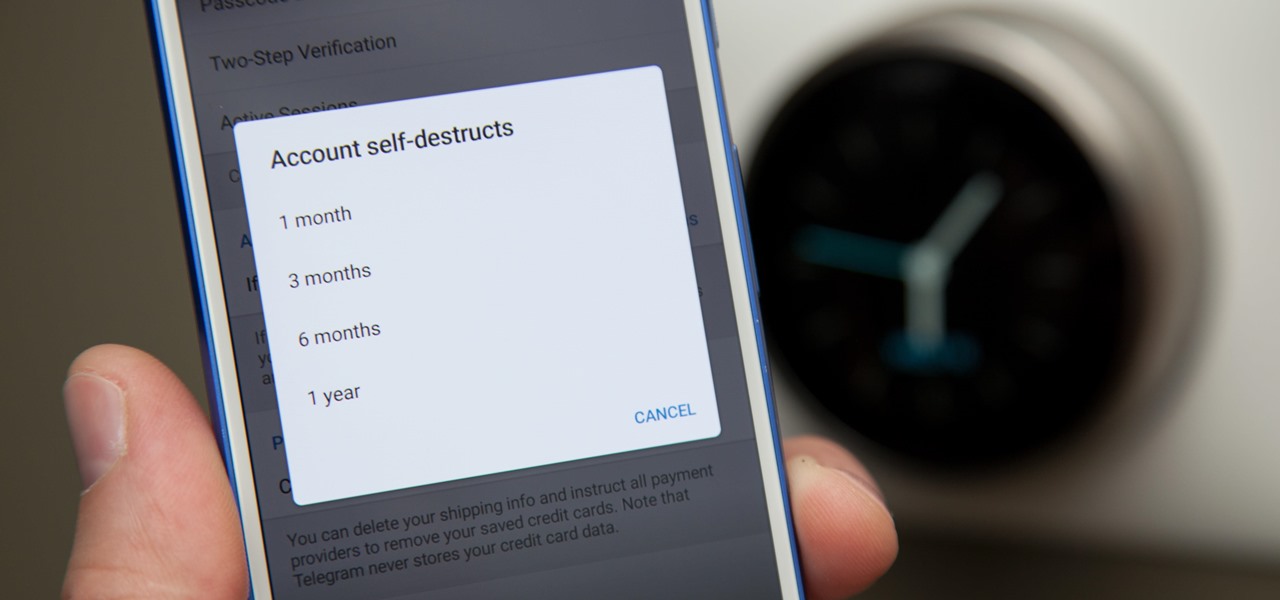
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

One major iOS 11 improvement that Apple skimped out on during its WWDC presentation was the redesigned storage management system, which makes it easy to view storage consumption in greater detail on your iPhone — and even easier to free up storage space with surgical precision.

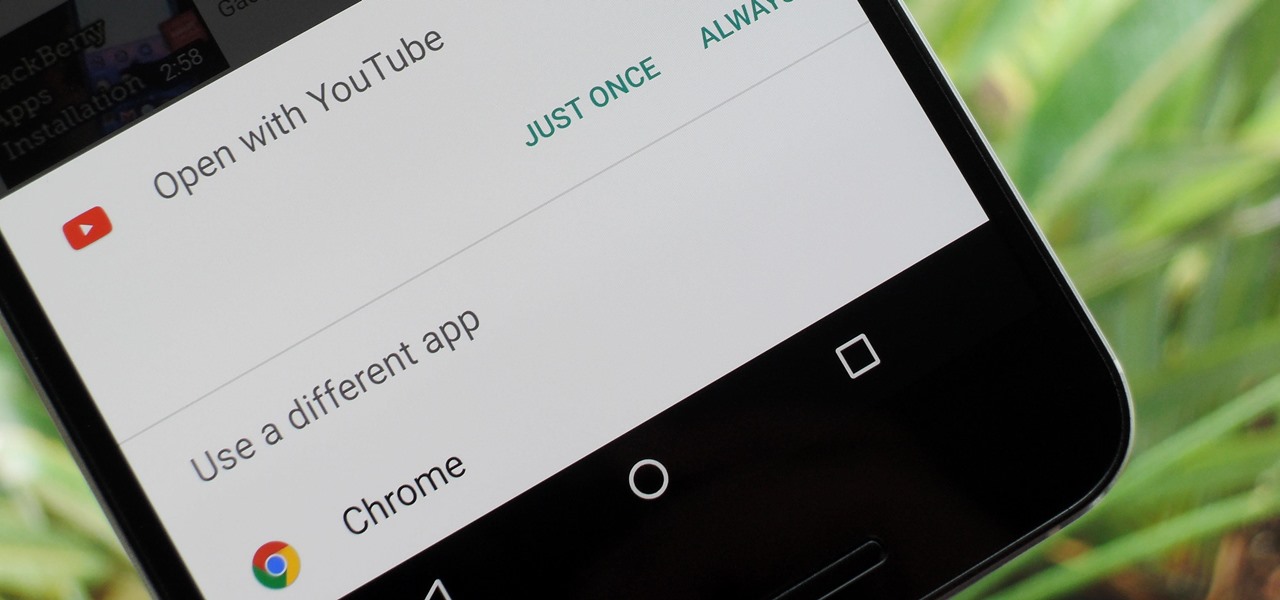
One of Android's biggest strengths relative to iOS is the fact that you can use any app to open compatible links, not just the stock ones that come preloaded on your device. When you tap a link that two or more of your apps are capable of opening, you'll see a message asking which app to launch it with—and from there, the choices are "Just Once" or "Always."

Over the course of the past year, a lot of Android apps have added pull-to-refresh functionality. It's a very useful and intuitive gesture, because all you have to do to refresh the page you're viewing is scroll to the top of the screen, then slide your finger down one more time.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Out of the box, your iPhone will not shoot 4K videos. If you want to up your video quality to go beyond 720p or 1080p HD, you'll have to do it manually. However, not all iPhone models can actually film in 4K resolution. If you have an iPhone 6 or below, you're out of luck, but if it's the iPhone 6S or newer, you can rock the 4K no problem.

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

The lack of Xposed support on Android Lollipop has left modules like GEL Settings incompatible with my Google Play Edition HTC One, so I've had to find a new launcher to meet all of my needs. While I can safely say I will never find the perfect launcher for me, Blinq comes pretty damn close.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

Big bad Apple recently announced its next iterations of iPhones and the world went crazy—as usual. Displaying an array of cool colors and futuristic features, the new iPhone 5S and 5C will both be rocking iOS 7, a sleek, modern operating system that gets rid of the old icons and glossy finish for a more flat and contemporary design.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Liked out? It is possible to "Like" too much. If you've gone too far expressing your enthusiasm for Facebook fan pages, watch this video to learn how to delete, or unlike, Facebook pages. Manage your Facebook profile like a pro.

If you are concerned about your electric bill, you might want to take control by installing a programmable thermostat. This will allow you to manage the temperature- and amount of electricity being used- in your home. The installation is simple and requires almost no tools.

For girls, short hair is a lot easier to manage than longer strands, with one caveat: You're much more limited in terms of what hairstyles you can do. But fret not. If your hair doesn't quite skim your shoulders yet, check out this hairstyling video to learn two super cute, feminine looks for girls with shorter strands.

This video shows you the basics of how to manage the General Umbriss heroic in World of Warcraft: Cataclysm. Then, you're shown how to earn the special achievement, Umbrage for Umbriss. The fight is easy, but the achievement is a bit tricky.

We think curly hair is awesome, and we're totally jealous of Taylor Swift's natural mane of beautiful blonde curls. But if you have curly hair then you know that oftentimes it can be difficult to manage, and that frizzies pop up at the first sign of humidity.

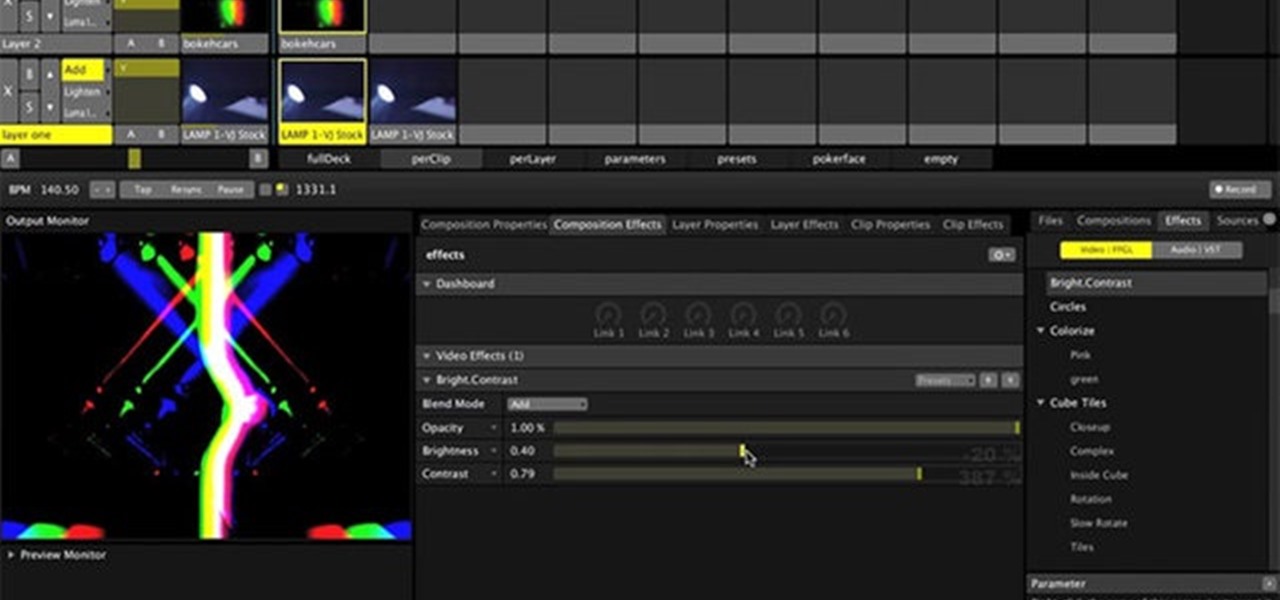
Resolume 3 is a powerful program which allows you to edit both audio and video effects. This quick tutorial gives you a brief overview of the general effects feature, how you can apply effects and how you can eliminate effects altogether.

When you use Gmail, Google Maps, Google Documents or any of the other Google products, you send trackable information about yourself to Google. By going in and configuring your account settings in Google Dashboard, it's possible to manage the information about yourself that you send them. This informative video shows how.

This tutorial shows you a few good tips on how you can manage your multiplayer Minecraft game. There's a special focus on how you can mine for diamonds and other rare commodities when you've logged on to a multiplayer server.

Your little robot has been thrown in jail and managed to break out! But what happens next? This tutorial shows you how to thwart one of your black-hatted enemies and sneak past him to continue on through the robot castle in Machinarium.

We've all been there, where we're trying to find that one thing in our cache but it's just eluding us. There's an easy and free solution to this pressing issue. Just use this Firefox add-on CacheViewer to manage and navigate your cache.

This is a fairly easy emblem to make, and manages to show your love for two different video games at once - Call of Duty: Black Ops and Minecraft. Turn the pixelated face of the creeper into your new multiplayer emblem!

Manage and read your alerts with the Desire HD's Notification's panel. Learn how to use it with this quick, official tutorial from HTC.