How To: Stabilize shaky video in iMovie '09
Check out this informative video tutorial from Apple on how to stabilize shaky video in iMovie '09.


Check out this informative video tutorial from Apple on how to stabilize shaky video in iMovie '09.
Check out this informative video tutorial from Apple on how to trim edits between video clips in iMovie '09.

Check out this informative video tutorial from Apple on how to add photos to videos in iMovie '09.
Check out this informative video tutorial from Apple on how to add background music to videos in iMovie '09.
Check out this informative video tutorial from Apple on how to add titles to videos in iMovie '09.
Check out this informative video tutorial from Apple on how to crop and rotate videos in iMovie '09.
Check out this informative video tutorial from Apple on how to add theme titles and transitions to movies in iMovie '09.

Check out this informative video tutorial from Apple on how to add sound effects to movies in iMovie '09.

Check out this informative video tutorial from Apple on how to add video effects to movies in iMovie '09.

Check out this informative video tutorial from Apple on how to add voiceovers to videos in iMovie '09.

Check out this informative video tutorial from Apple on how to slow down, speed up, and reverse video in iMovie '09.

Check out this informative video tutorial from Apple on how to create picture-in-picture effects in iMovie '09.

Check out this informative video tutorial from Apple on how to add animated travel maps in iMovie '09.

Check out this informative video tutorial from Apple on how to record video with the built-in iSight camera in iMovie '09.
Check out this informative video tutorial from Apple on how to publish videos to YouTube in iMovie '09.

Check out this informative video tutorial from Apple on how to make a Magic DVD in iDVD '09.
Check out this informative video tutorial from Apple on how to make a OneStep DVD in iDVD '09.

Check out this informative video tutorial from Apple on how to create a custom DVD in iDVD '09.
Check out this informative video tutorial from Apple on how to burn a project to DVD in iDVD '09.

Check out this informative video tutorial from Apple on how to play guitar with GarageBand '09 guitar lessons.

Check out this informative video tutorial from Apple on how to play piano with GarageBand '09 piano lessons.

Check out this informative video tutorial from Apple on how to record an electric guitar in GarageBand '09.

Check out this informative video tutorial from Apple on how to record acoustic instruments in GarageBand '09.
Check out this informative video tutorial from Apple on how to use built-in software instruments in GarageBand '09.

Check out this informative video tutorial from Apple on how to edit and arrange songs in GarageBand '09.
Check out this informative video tutorial from Apple on how to send songs to your iTunes library in GarageBand '09.

Check out this informative video tutorial from Apple on how to create an iPhone ringtone in GarageBand '09.
Check out this informative video tutorial from Apple on how to create a podcast in GarageBand '09.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to record voice memos on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

There's a cool plugin for your WordPress blog called Capability Manager. The Capability Manager plugin is mainly used for the blog which has number of users, each having a different role. In order to manage the WordPress Admin access for each user role, this will help you. With the help of this plugin, you can enable the particular part of the Admin access to fit a particular user role.
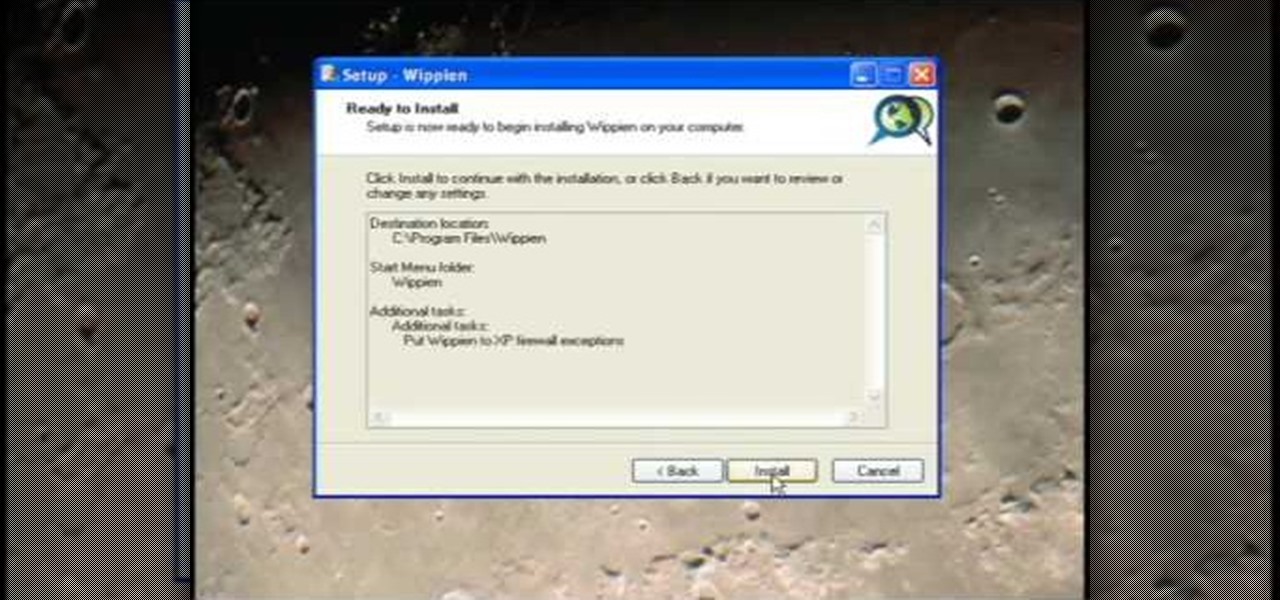
This video tutorial from ruralgeek shows how to set up and use Wippien VPN on Windows XP. First, download Wippien client from here: www.wippien.com.
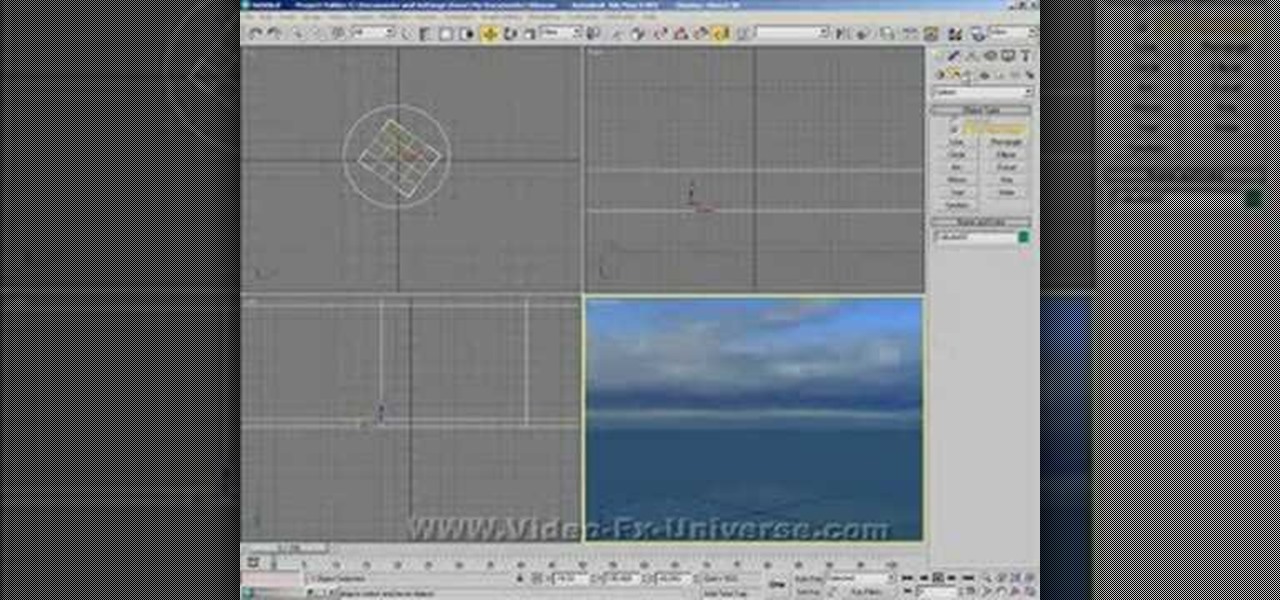
how to create an Ocean in 3DS Max

If you get looks of exasperation whenever you stammer out a drink order, take this crash course in bar-speak.

Learn how to setup the Verizon FiOS Router for multiplayer gaming. Most games and gaming consoles only require that UPnP (Universal Plug-n-Play) be turned on. The MI424WR Verizon FiOS Router that is manufactured by Actiontec ships with UPnP ON, as the default.
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.
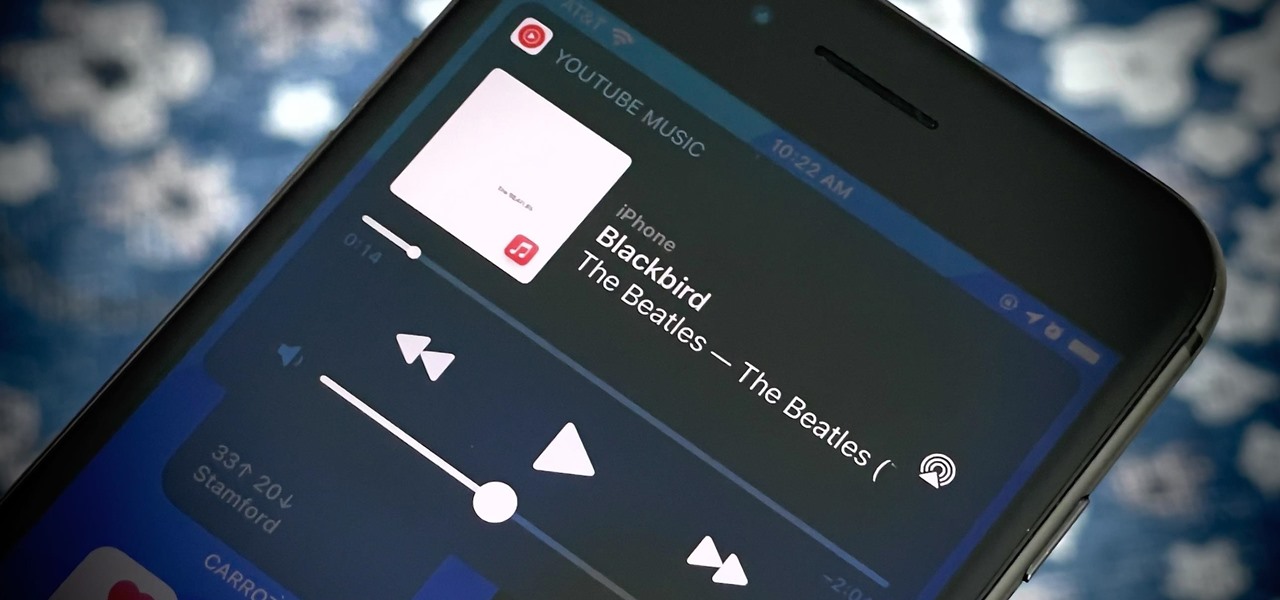
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.
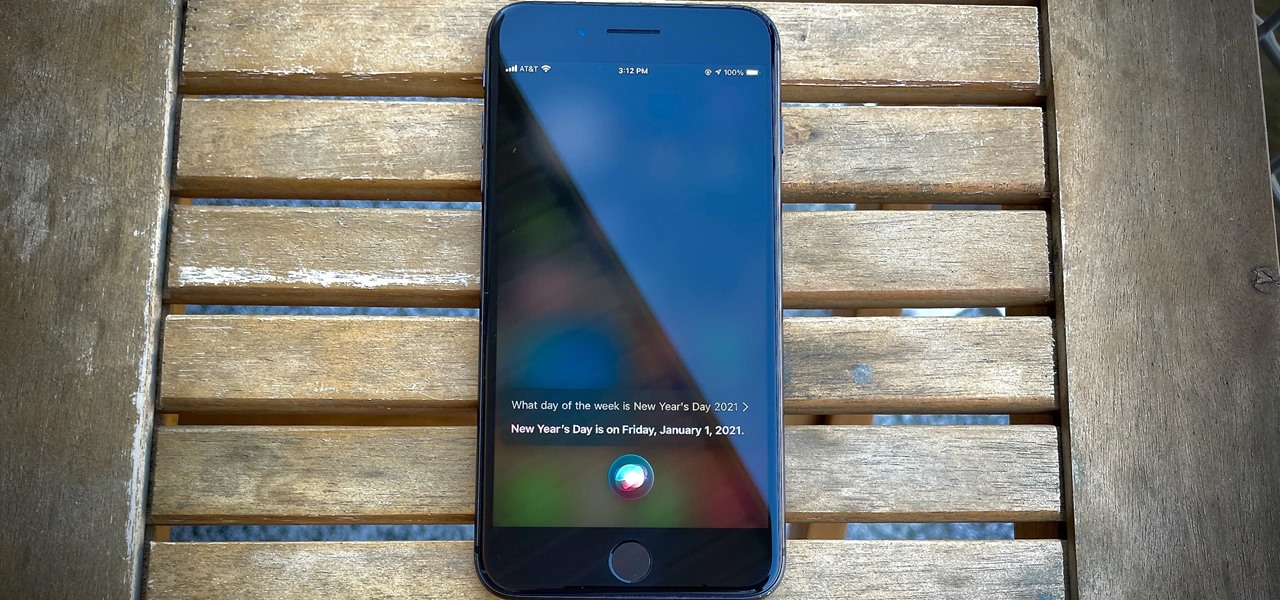
Full-page interfaces are so iOS 13. With Apple's iOS 14, alerts such incoming phone and FaceTime calls now appear as small banners instead. The same goes for Siri. Instead of using your iPhone's full display, Siri now exists in an unobtrusive overlay. But if you miss the focus that full-screen Siri used to bring, you're in luck because the feature still exists — it's just hidden.
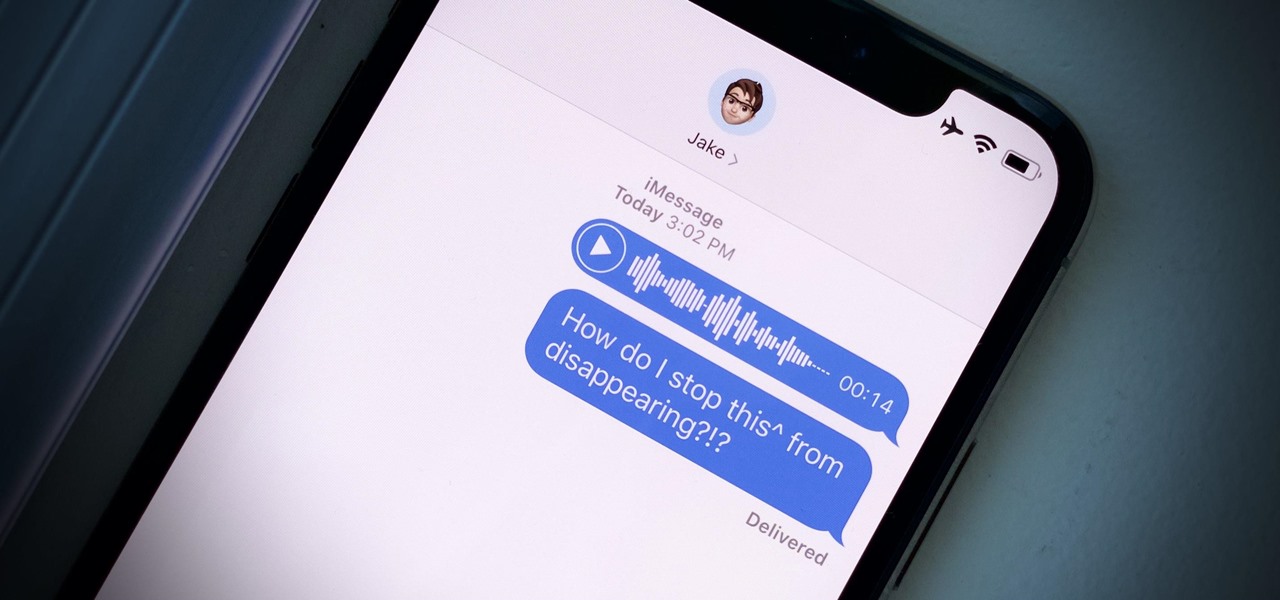
Introduced in the Messages app back in iOS 8, audio messages are a fun way to spice up an iMessage thread when you're bored with text, emoji, and GIFs. However, it can be frustrating to lose an important, funny, or otherwise-interesting sound clip because iOS auto-deletes it two minutes after you send or listen to it. Thankfully, there is a way to stop this from happening.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Ever since Microsoft sunset Windows Phone, they've been working with Android to tap into the growing mobile device market. The tech giant has uploaded over 80 apps to the Play Store for any Android user to download, but some features Samsung has hoarded for themselves.